AWS Certified Solutions Architect - Associate
 Rohit Pagote
Rohit PagoteTable of contents
AWS Global Infrastructure
AWS Regions
AWS Availability Zones
AWS Data Centers
AWS Edge Locations / Points of Presence
AWS Regions
A region is a cluster or collection of data centers.
AWS has regions all around the world.
Most AWS services are region-scoped.
How to choose AWS Region
Compliance with data governance and legal requirements: data never leaves a region without your explicit permission.
Proximity to customers: reduced latency.
Available Services within a Region: new services and new features are not always available in every region.
Pricing: Pricing varies region to region.
AWS Availability Zones
Each Region can has many Availability Zones (usually 3, min 3, max 6).
Each AZ is one or more discrete data centers with redundant power, networking and connectivity.
They are separate from each other, so that they are isolated from disasters.
They are connected with high bandwidth, ultra-low latency networking.
AWS Points of Presence (Edge Locations)
Content is delivered to end users with lower latency.
AWS has 400+ POP (400+ Edge Locations & 10+ Regional Caches) in 90+ cities across 40+ countries.
IAM
IAM stands for Identity and Access Management.
It is a Global Service.
IAM: Users and Groups
Root account is created by default when we create AWS account. It is not recommended to use or share the root account.
User is an entity that you can create in AWS.
The IAM user represents the human user or workload who uses the IAM user to interact with AWS.
Group is a collection of users. It can only contain users, not other groups.
Users don't necessary have to belong to a Group, and Users can also belong to multiple Groups.
IAM: Permissions
Users or Groups can be assigned JSON documents called as Policies.
These policies defines the permissions to the users or groups.
In AWS, you apply the least privilege principle: don't give more permissions than a user needs.
IAM: Policy Structure
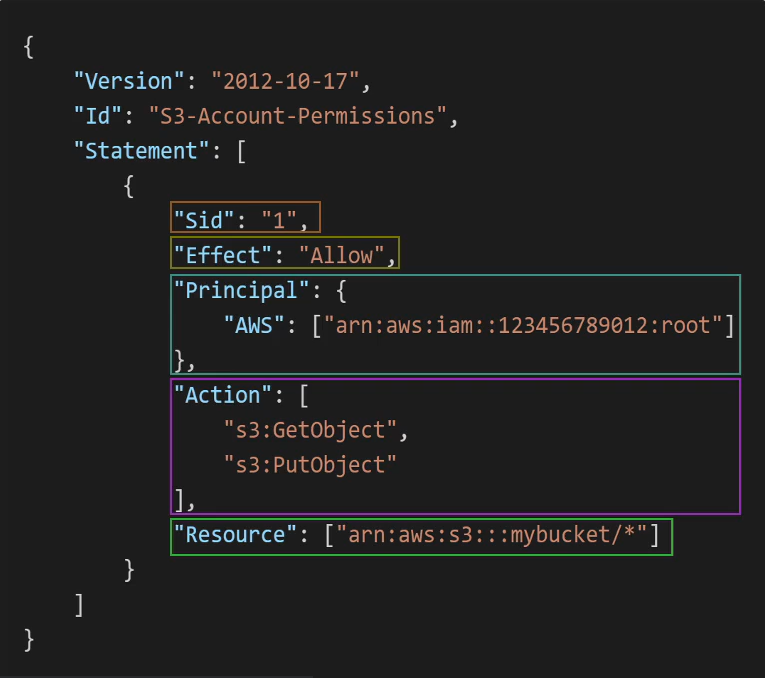
Version: policy language version, always include "20112-10-17"
Id: identifier for the policy (optional)
Statement: one or more individual statements (required)
Statement Consists of:
Sid: identifier for the statement (optional)
Effect: whether the statement allows or denies access (Allow, Deny)
Principal: account/user/role to which this policy applied to
Action: list of actions this policy allows or denies
Resource: list of resources to which the actions applied to
Condition: conditions for when this policy is in effect (optional)
IAM: Roles for Services
Some AWS service will need to perform actions on your behalf.
To do so, we will assign permissions to AWS services with IAM Roles.
IAM Role is just like a user, but they are intended to be used not by physical people, but instead they will be used by AWS services.
IAM: Security Tools
IAM Credentials Report (account-level)
- A report that lists all your account's user and the status of their various credentials.
IAM Access Advisor (user-level)
Access advisor shows the service permissions granted to a user and when those services were last accessed.
You can use this information to revise your policies.
IAM: Guidelines & Best Practices
Do not use root account except for AWS account setup.
One physical user = One AWS user
Assign users to groups and assign permissions to groups.
Create a strong password policy.
Use and enforce the use of MFA.
Create and use Roles for giving permission to AWS services.
Use Access Keys for programmatic access (CLI/SDK).
Audit permissions of your account using IAM Credentials Report & IAM Access Advisor.
IAM: Summary
Users: mapped to a physical user, has a password for AWS console.
Groups: contains users only.
Policies: JSON document that outlines permissions for users or groups.
Roles: for AWS services.
Security: MFA + Password policy
AWS CLI: manage your AWS services using command-line.
AWS SDK: manage your AWS services using a programming language.
Access Keys: access AWS using CLI or SDK.
Audit: IAM Credentials Reports & IAM Access Advisor.
AWS Access Keys, CLI and SDK
How can users access AWS?
There are 3 options:
AWS Management Console: protected by password + MFA
AWS Command Line Interface (CLI): protected by access keys
AWS Software Development Kit (SDK)- for code: protected by access keys
Access keys are generated through AWS Console.
Access Key ~= username
Secret Access Key ~= password
AWS CLI
A tool that enables you to interact with AWS services using commands in your command-line shell.
Direct access to the public APIs of AWS services.
You can develop script to manage your resources.
It's open source: aws-cli
It's an alternative to using AWS Management Console.
AWS SDK
AWS SDK stands for Software Development Kit
Language specific APIs (set of libraries)
Enables you to access and manage AWS services programmatically.
Embedded within your application.
Supports: JS, Python, PHP, .NET, Ruby, Java, Go, Node.JS, C++.
Example: AWS CLI is build on AWS SDK for Python (boto3).
Amazon EC2
EC2 Basics
EC2 = Elastic Compute Cloud
Infrastructure as a Code (IaaS) service.
It mainly consists in the capability of:
Renting Virtual Machines (EC2)
Storing data on virtual drives (EBS)
Distributing load across machine (ELB)
Scaling the services using an auto-scaling group (ASG)
EC2 sizing & configuration options
OS: Linux, Windows & MacOS
How much compute power and cores (CPU)
How much random-access memory (RAM)
How much storage space:
Hardware (EC2 instance store)
Network-attached (EBS & EFS)
Public IP address
Firewall rules: Security Groups
Bootstrap script (configure at first launch only): EC2 user data
EC2 User Data
It is possible to bootstrap the instances using an EC2 User Data Script.
Bootstrapping means launching or running command when a machine starts.
This script is only run once at the instance first start.
EC2 user data can be used to automate boot tasks such as:
installing updates
installing softwares
downloading common files from the internet, etc.
EC2 user data script runs with the root user.
EC2 Instance Types
Will add aws skill builder link here to read for the ec2 instance types.
AWS has the following naming convention:
m5.2xlarge
m: instance class
5: generation (AWS improves them over time)
2xlarge: size within the instance class (CPU, Memory, etc.)
Below mentioned some of the most used instance types.
EC2 Instance Type - General Purpose
Great for a diversity of workloads such as web servers or code repositories.
Provide balance between:
Compute
Memory
Networking
EC2 Instance Type - Compute Optimized
Great for compute intensive tasks that require high performance processors.
Batch processing workloads
Media transcoding
High performance web severs
High performance computing (HPC)
Scientific modeling & machine learning
Dedicated gaming servers
EC2 Instance Type - Memory Optimized
Fast performance for workloads that process large data sets in memory (RAM).
High performance, relational/non-relational databases
Distributed web scale cache stores
In-memory databases optimized for BI (Business Intelligence)
Applications performing real-time processing of big unstructured data
EC2 Instance Type - Storage Optimized
Great for storage intensive tasks that require high, sequential read and write access to large data sets on local storage.
High frequency online transaction processing (OLTP) systems
Relational and NoSQL databases
Cache for in-memory databases (ex. Redis)
Data warehousing applications
Distributed file systems
Security Groups (SG)
Introduction
SG are the fundamental of network security in AWS.
They control how traffic is allowed into or out of EC2 instances.
SG only contain allow rules.
SG rules can reference by IP or by Security group.
Deeper Dive
SG acts as a firewall on EC2 instances.
They regulate:
Access to ports
Authorized IP ranges - IPv4 or IPv6
Control of inbound network (from other to the instance)
Control of outbound network (from the instance to other)
Good to know
SG can be attached to multiple instance
Locked down to a region/VPC combination. (if you switch a region or create a new VPC, you have to create new SG)
Does live outside the EC2 - if traffic is blocked, the EC2 instance won't see it.
It's good to maintain one separate SG for SSH access.
If your application is not accessible (time out), then its a SG issue.
If your application gives a "connection refused" error, then its probably an application issue.
All inbound traffic is blocked by default.
All outbound traffic is allowed by default.
Classic Ports to Know
22 = SSH (Secure Shell) - log into Linux instance
21 = FTP (File Transfer Protocol) - upload files into a file share
22 = SFTP (Secure File Transfer Protocol) - upload files using SSH
80 = HTTP - access unsecured websites
443 = HTTPS - access secured websites
3389 = RDP (Remote Desktop Protocol) - log into a Windows instance
EC2 Instance Purchasing Options
On-Demand Instances: short workload, predictable pricing, pay by second
Reserved (1 & 3 years):
Reserved Instance: long workloads
Convertible Reserved Instance: long workloads with flexible instances
Saving Plans (1 & 3 years): commitment to an amount of usage, long workload
Spot Instance: short workloads, cheap, can lose instances anytime (less reliable)
Dedicated Hosts: book an entire physical server, control instance placement
Dedicated Instances: no other customer will share your hardware
Capacity Reservations: reserve capacity in a specific AZ for any duration
Subscribe to my newsletter
Read articles from Rohit Pagote directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Rohit Pagote
Rohit Pagote
I am an aspiring DevOps Engineer proficient with containers and container orchestration tools like Docker, Kubernetes along with experienced in Infrastructure as code tools and Configuration as code tools, Terraform, Ansible. Well-versed in CICD tool - Jenkins. Have hands-on experience with various AWS and Azure services. I really enjoy learning new things and connecting with people across a range of industries, so don't hesitate to reach out if you'd like to get in touch.