How to Configure a Firewall Using UFW on Ubuntu
 Joseph Chisom Ofonagoro
Joseph Chisom Ofonagoro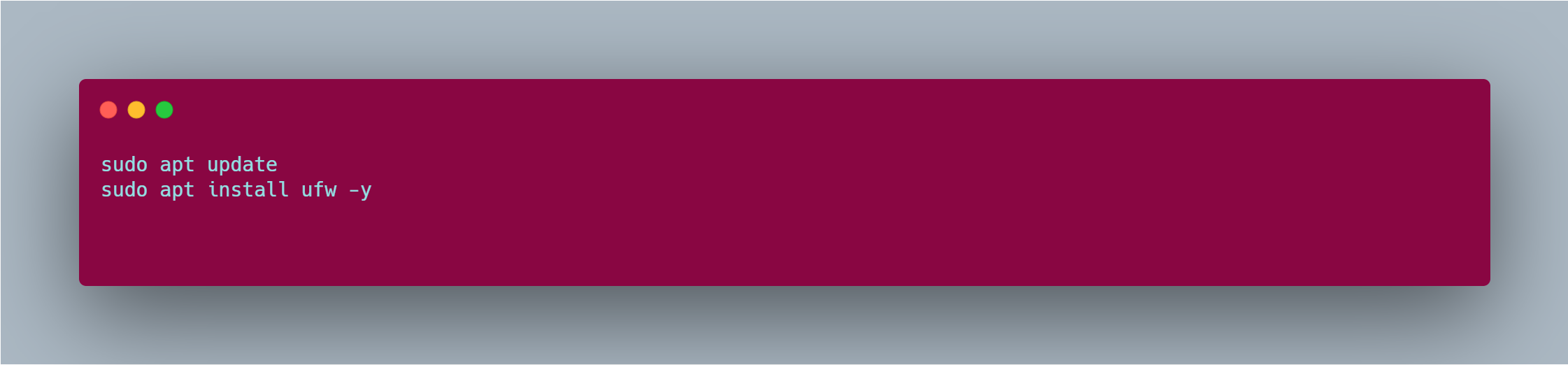
Linux is favored by security professionals for many reasons, but among all of these reasons, the fact that it has flexibility in the number of things it can be used for is enough reason it has lots of fans. Ubuntu, a very popular linux flavor shares this flexible nature of linux and one of its many uses is in configuring a firewall using the UFW package.
In this guide, I am going to be explaining how you can configure your firewall using UFW, advantages of doing so and potential cons of it.
Now let’s move in.
What’s UFW?
UFW stands for Uncomplicated FIrewall. It is a simple linux firewall package that’s used to work with Firewall operations in Linux Command Line especially for beginners that may find other methods very complicated.
Getting Started
To get started with using UFW, you should be sure to have the following set:
A Ubuntu with version 17 or later: This is necessary because you’d need some other additional things enabled, like IPV4 & IPV6. Having a later version of Ubuntu ensures that these additional requirements are already installed by default.
Sudo access: This requires no emphasis, right?
UFW should be installed.
UFW usually comes preinstalled, but if it is not, you can install it by doing:
If it is not installed, you will get an inactive response.
To install it, you do the normal installation procedure;
If you are familiar with Ubuntu installations, you should proceed with this command snippets,
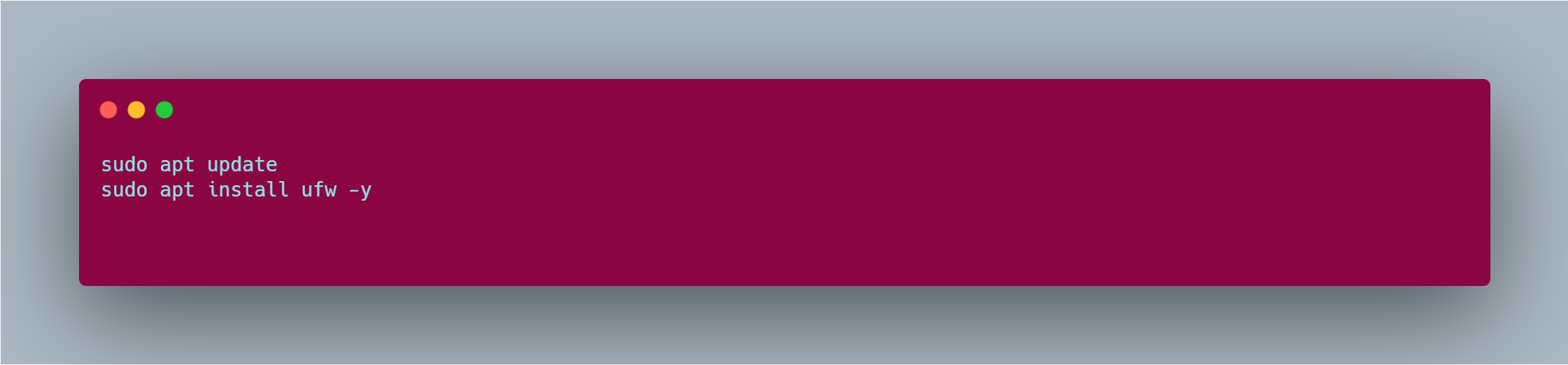
but if you are not familiar with it, you should remove the ‘-y’, but that means you will have to periodically type in Yes or No when prompted to.
Enabling UFW and Policies
After installing UFW, you will need to enable it using this command:
sudo ufw enable
Enabling UFW will automatically set the default policies. These default policies deny any incoming traffic and permits traffic going out of the firewall.
But in situations where you might want to configure it to do the opposite of its default policies, you can do so by writing some commands.
Well, you should do that to see how it works, but ideally, the default should be left the way it is.
Now, suppose you also want this firewall to filter traffic from select ports, you can do so at this stage. Here are some practical examples.
Setting Rules
Permitting from select legitimate incoming ports
sudo ufw allow 443
Port 443 is used for https requests, and typing in this command permits all traffic coming in from port 443 to pass your custom firewall.
Denying From Select Ports.
Just as we permitted from a specific port, we can also deny traffic from any specific port of our choosing. All you need to do is modify the command to deny traffic coming from these ports.
sudo ufw deny 80
Ths denies any traffic coming from an http resource which we indicated by its port number; 80. Alternatively, you can also use http if you forgot the port number and this rule applies to other ports too.
Note: denying incoming ports is necessary if you feel you may accidentally permit all incoming connections in the future. So by explicitly denying a particular connection, even when you make this mistake, that port will remain blocked. Aside from this, there is no other reason to write a separate command denying incoming traffic.
Permitting From IP Addresses.
One cool and quite common use of firewalls is in filtering ip addresses. So, it is quite normal to find people using firewalls to block and permit IP addresses. Here is how to get this done using ufw:
sudo ufw allow 198.5.77.1
This permits only this specified IP address to establish a connection passing through the wirewal.
You can also specify from a particular IP address using this command:
sudo ufw allow from 198.5.77.1
By adding the from params, you have instructed the firewall to permit all connections from that IP going forward.
Things can get more tricky if you want to restrict an IP address to only communicate with just a specific port. Here is an example of that:
sudo ufw allow from 198.5.77.1 to any port 443
Denying IP Addresses:
To deny a specific IP address from accessing connection, you can twerk its permission command to be:
sudo ufw deny 198.5.77.1
To deny an unspecified range of IP addresses, you can use:
sudo ufw deny from 198.5.77.1
Permitting From Select Port Ranges
Instead of specifying different ports individually, you can simply specify them as a range, from a start to a stop. This permits any traffic coming in from any ports within that range.
An example will be: sudo ufw allow 5000:6000/tcp
One thing you must know when writing commands that filter our traffic from port ranges is that the protocol must be specified as this tells the firewall what protocol it should focus on. As you can see, in my example, I specified the Transmission Control Protocol.
Denying From Select Port Range
To reverse the allow command for port range, you can use the deny command also in this format:
sudo ufw deny 5000:6000/udp
Logging
After adding your custom rules, you might want to specify that your firewall logs activities at a frequency. Normally, to do this, you should have to type in sudo ufw logging on but after doing this, you might also specify the log intensity in a separate command. sudo ufw logging high, sudo ufw logging medium or sudo ufw logging low.
Instead, you can do all of these in a single command; turning on logging and selecting its intensity. Just type in sudo ufw logging high. You can add either low or medium or high, whatever you want.
Apply Your Changes
To apply any rules you have set, you should use the reload parameter by typing; sudo ufw reload.
Once you do, the next step is to test your connection to ensure that the rules you set are working properly.
You can use telnet to ping your ports to check if the traffic is coming or going out. Here is an example; telnet your-server-ip 443
Where telnet is the tool you use to ping network connectivity. Your-server-ip is your server’s IP address 443 is the port you are testing.
With this, we can have a more practical example; telnet 8.8.8.8 443 If the connection goes through, you will see a successful connection message, but if you see something like ‘unable to contact, connection refused or timeout, that’s an indication that the connection isn’t going through and depending on your firewall rules, you could simply ignore it or troubleshoot it.
Check Status
To check your ufw status. You can do so with this command;
sudo ufw status verbose
This gives a more detailed status report of ufw.
Delete and Disable
Disable ufw
To temporarily disable ufw, on your terminal you can type in;
sudo ufw disable
Delete Rules by Numbers
Every rule is assigned a number at creation and can be referenced by this number if you know them. To find their numbers, use this command;
sudo ufw status numbered
The output will be something like this:
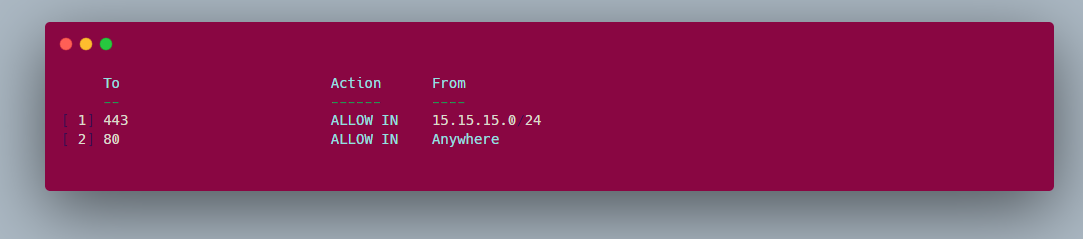
The number by the far left is the number that was assigned to a rule.
Now that you know the rules and their numbers, you can go ahead to write the command for deleting rules by their numbers.
sudo ufw delete 1 This deletes rule number 1 which was the allow rule I wrote for https. When prompted, input y for yes.
Delete With its Name
If you don't want to delete a rule by its assigned number, you can use its name: here is an example: sudo ufw delete allow https
This deletes a rule I wrote to allow https requests.
Resetting ufw
If perhaps you want to return to default settings which is allow all outgoing connections and deny all incoming, you can use the reset parameter
sudo ufw reset
This will reset all rules to pre-installed ones.
Pros and Cons of UFW
Pros
Easy to use:
Recall that at the beginning of this guide, I told you that ufw is easy to use and the ideal option for beginners or people who need simple tools unlike tools like iptables
Pre Installed on Ubuntu:
UFW is included with Ubuntu by default, so there’s no need to install additional software.
Quick Configuration:
Common tasks like enabling or disabling the firewall are just one command:
Integration with Applications:
Many applications, like OpenSSH, register profiles with UFW. You can enable them directly:
Supports IPv4 and IPv6:
UFW can manage both IPv4 and IPv6 traffic seamlessly.
Lightweight:
UFW is not resource-intensive, making it suitable even for low-powered servers or devices.
Logging Features:
UFW has logging to track blocked or allowed connections, helpful for troubleshooting:
Cons
Despite its good number of advantages, it still has other things one might consider before using it.
Limited Granularity:
UFW is not as flexible as iptables for very specific rules or complex configurations. For example, it’s harder to set up rules based on packet attributes. This also makes it unsuitable for large organizations.
No GUI:
UFW is command-line-based. Beginners who prefer graphical interfaces need to install additional tools like GUFW.
Less Suitable for Complex Networks:
For advanced network setups involving multiple interfaces, zones, or NAT, UFW might feel restrictive compared to firewalls.
Less Real-Time Feedback:
UFW doesn’t provide real-time insights during rule application. Debugging often relies on checking logs after applying rules.
Conclusion
Configuring a firewall using UFW on Ubuntu is a straightforward process, making it an excellent choice for beginners or those who need a quick and effective way to secure their systems. Its ease of use, lightweight nature, and integration with Ubuntu make it a valuable tool for managing basic firewall rules.
By following the steps outlined in this guide, you can set up and manage your firewall effectively, ensuring a balance between accessibility and security. With the pros and cons in mind, UFW can be a great addition to your toolkit, provided it suits the specific needs of your environment.
Subscribe to my newsletter
Read articles from Joseph Chisom Ofonagoro directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Joseph Chisom Ofonagoro
Joseph Chisom Ofonagoro
Hi there! I am a curious techie. My spare time is spent with books.