Demystifying ARP and NAT: The Backbone of Internet Traffic
 Siddhartha S
Siddhartha S
Introduction
In the first article of this series, Navigating Networking Layers: The Journey of Data Through TCP we explored how data flows through various layers of the network, transitioning from segments to packets to data frames.
In this article, we will delve into two essential concepts: Address Resolution Protocol (ARP) and Network Address Translation (NAT). These play crucial roles in facilitating communication between hosts within a private network and across the internet, respectively.
While this article stands on its own, readers who choose not to refer to the previous installment will still find valuable insights here. We aim to provide a clear understanding of how computers communicate with one another, whether they are situated within the same premises or on opposite sides of the globe.
ARP (Address Routing Protocol)
To begin, let's start with something relatable—our home internet setup.
The following diagram illustrates this setup:
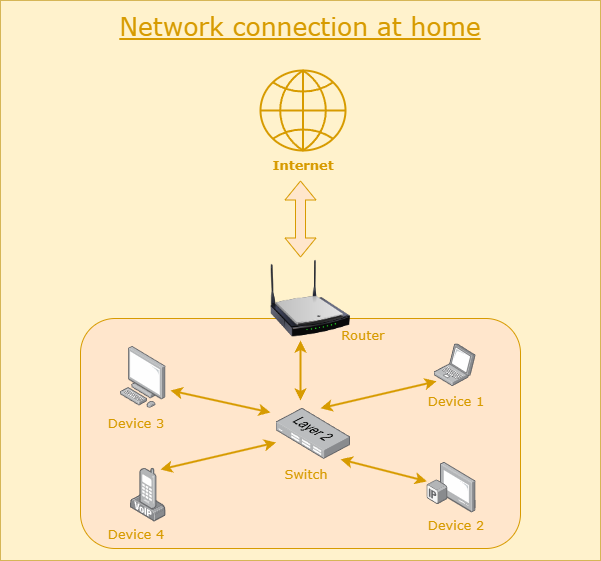
Many of us may not have encountered a switch, as most Wi-Fi routers also function as switches. However, in the past, when internet connections were primarily provided via cables, all devices had to connect to a switch, which, in turn, connected to a router.
This setup constitutes a private network. As soon as you connect your device to the network, it is assigned an IP address. The CIDR ranges for private networks, as outlined in the RFC 1918 Address Allocation guideline, are as follows:
192.168.0.0/16
172.16.0.0/12
10.0.0.0/8
For most home users, the first CIDR range is the most common choice, as it provides a sufficient number of IP addresses for typical household usage. The IP address displayed on your device is not inherent to the machine itself; rather, it is an attribute of the Network Interface Card (NIC) connected to your device. The NIC also has a unique MAC address, assigned upon manufacture, which follows the format aa:bb:cc:dd:ee:ff. This means a MAC address is made up of six octets.
Both the MAC address of your NIC and the IP address assigned to your NIC serve as identifiers within a private network. It is essential to note that no two devices can share the same IP address or MAC address within the same private network (subnet).
Now, let’s visualize a scenario in which two hosts within a given subnet want to communicate.
Communication occurs using IP addresses; however, within a subnet, MAC addresses are used. This process is facilitated through an Address Resolution Protocol (ARP) table maintained by all hosts. The ARP table acts as a mapping device, linking IP addresses to MAC addresses.
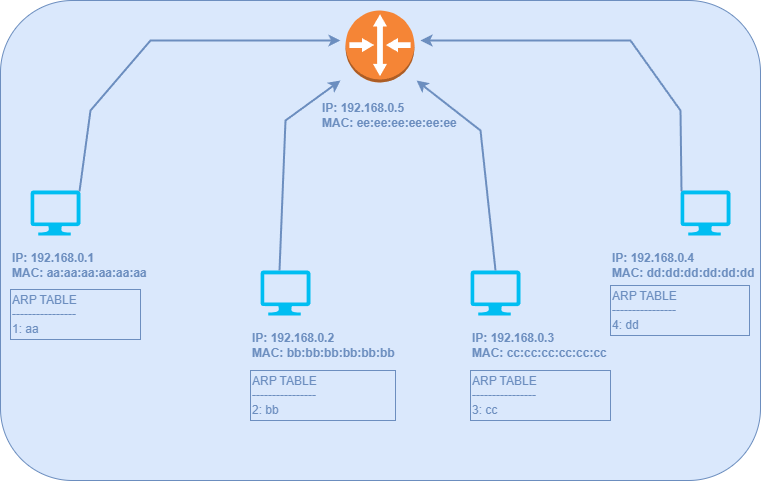
Note that the IP and MAC addresses in the ARP tables have been abbreviated for brevity. For instance, '1' represents 192.168.0.1 and 'aa' denotes aa:aa:aa:aa:aa:aa.
There are two potential scenarios:
A host wishes to connect to another host within the subnet.
A host aims to connect to a host outside the subnet, residing elsewhere on the internet.
We will explore both scenarios in detail.
Scenario 1: Host Wants to Connect to Another Host within the Subnet
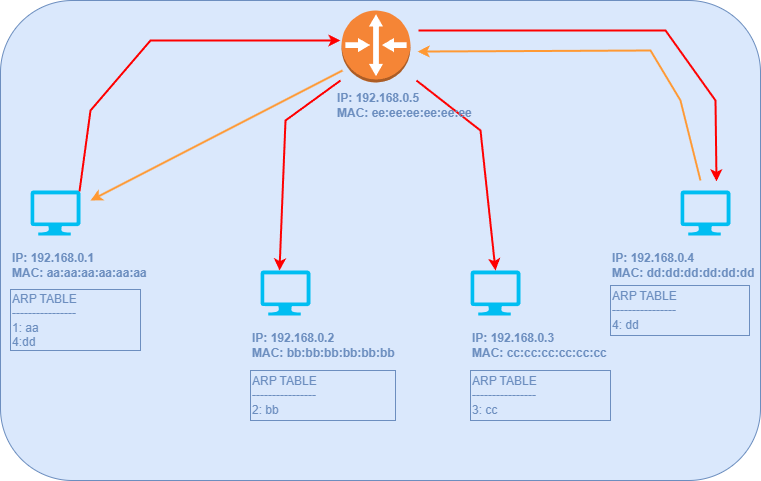
Starting with a fresh slate, the ARP tables of all hosts will initially contain only their own IP-MAC mappings. Let’s assume Host 1 wants to connect to Host 4. All Host 1 knows is the IP address of Host 4, which is 192.168.0.4. The following steps occur:
Determine Subnet Membership: Host 1 checks whether the target IP address (192.168.0.4) belongs to the same subnet (the method for this determination will be discussed in a later section).
ARP Table Lookup: Host 1 consults its ARP table but does not find an entry for Host 4.
Broadcast ARP Request: To locate Host 4's MAC address, Host 1 broadcasts an ARP request to all hosts within the subnet connected via the router/switch. For simplicity, we assume that the router functions as a switch in this scenario.
From the broadcast message, Host 4 learns the MAC address of Host 1. All hosts receive the broadcast, but only Host 4 will respond.
Host 1 then updates its ARP table and uses Host 4's MAC address to send messages.
How does a host determine if another host is within the same subnet?
A host determines if another host's IP address is within the same subnet by performing the following steps:
Obtain the Subnet Mask: The host uses its configured subnet mask to identify the network portion and the host portion of its own IP address.
Perform a Bitwise AND Operation: The host executes a bitwise AND operation between its own IP address and its subnet mask, and then does the same for the target IP address.
Example:
Host's IP:
192.168.0.10Subnet Mask:
255.255.0.0Target IP:
192.168.0.5
Convert to binary:
Host IP:
11000000.10101000.00000000.00000001Subnet Mask:
11111111.11111111.00000000.00000000Target IP:
11000000.10101000.00000000.00000101
Perform bitwise AND:
Host:
11000000.10101000.00000000.00000000(result:192.168.0.0)Target:
11000000.10101000.00000000.00000101(result:192.168.0.0)
Compare Results: If the results of the AND operation for both IP addresses are identical, then both hosts are in the same subnet. In the above example, since both results are
192.168.0.0, the host determines that192.168.0.5is in the same subnet.
Scenario 2: Host wants to connect to a host who is outside the subnet and is located somewhere on the internet
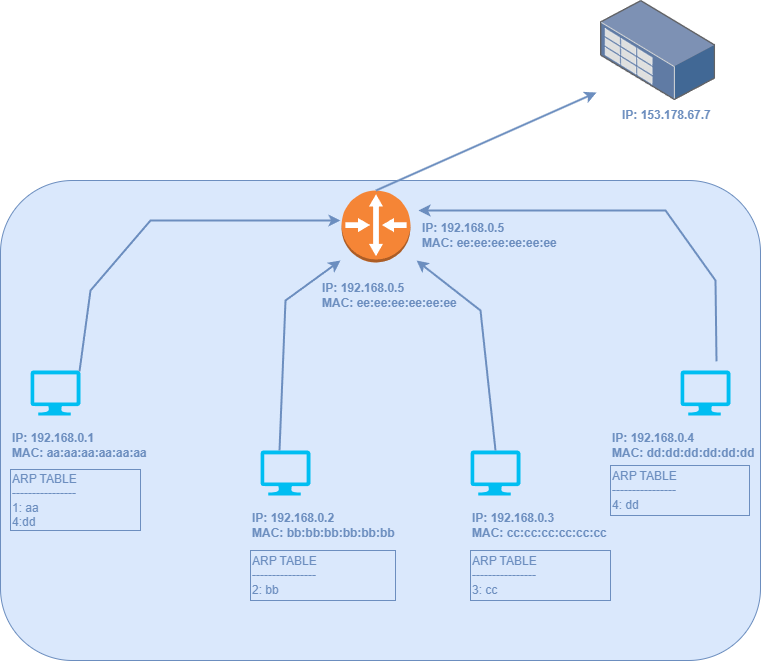
Now, let’s examine the scenario in which a host wants to connect to an IP address located somewhere on the internet.
Assuming Host 1 intends to connect to a server with the IP address 153.178.67.7, the following steps occur:
Determine Subnet Membership: Host 1 checks whether the target IP address (
153.178.67.7) is part of its subnet.Realize It’s Outside the Network: Upon realizing that the target IP is not within the same network, Host 1 prepares to send the message to the gateway.
Identify the Gateway: The gateway serves as a special host acting as a bridge to an external network. Host 1 will now consult its ARP table to find the MAC address of the gateway.
ARP Broadcast: In the previous diagram, the gateway is also represented by the router. Host 1 will issue an ARP broadcast to request the MAC address of the gateway (represented as
ee:ee:ee:ee:ee:ee). It is important to note that this step is where ARP poisoning can potentially occur, a topic we will cover shortly.Receive the Gateway’s MAC Address: The router replies with its MAC address, allowing Host 1 to send the message to the gateway.
At this juncture, you may be wondering why a request for an external IP address is sent to the gateway. We will explore this topic in detail in the upcoming NAT section.
ARP Poisoning
When a connected host broadcasts a message to the gateway, it is possible for a malicious host to respond to the broadcast, impersonating the gateway. If the reply from the malicious host reaches the requesting host before the legitimate gateway's response, the requesting host may mistakenly identify the malicious host as the gateway. Consequently, the requesting host will direct all internet requests to this impersonating host. This process is known as ARP poisoning.
NAT (Network Address Translation)
Internet gateways or routers that connect the Wide Area Network (WAN) and Local Area Network (LAN) possess two IP addresses: one internal IP and one public IP.
In the previous section, we observed that when a host needs to send a message to another host on the internet, it forwards the message to the internet gateway.
The Internet Gateway (IG) recognizes that the message must be routed to a remote server on the internet. It reads the From IP (192.168.0.1) and Port (6666) from the IP packet. Thus, internet gateways operate at Layer 3 of the networking model.
The IG makes an entry in its ARP table, which includes a public port that corresponds to the combination of the From IP and Port as well as the To IP and Port.
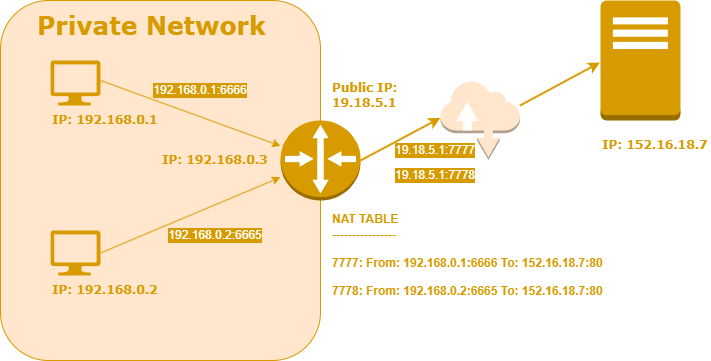
Referring to the diagram above, the ARP table of the router contains entries for two different hosts that communicate with the same application on the same server. The IG rewrites the headers of the IP packets, replacing the From IP and Port with its own public IP. As a result, the packets sent to the remote server now have a From IP and Port of 19.18.5.1:7777.
When the response from the remote server returns to the internet gateway, it arrives at port 7777. The IG checks its NAT table and recognizes that traffic on port 7777 should be redirected to the local machine at 192.168.0.1, port 6666.
Interestingly, API gateways, which serve as entry points to a microservices cluster, also perform NATing. They route requests to the appropriate microservice based on the incoming request, presenting only one gateway to the caller rather than multiple services.
Why Can’t All Machines Be Assigned a Public IP to Avoid Internet Gateways?
This limitation is precisely what will be addressed with IPv6. Currently, IPv4 has restrictions concerning the number of connected devices. NAT provides a solution, allowing many devices to connect to the internet while utilizing a limited number of public IP addresses.
Conclusion
In this article, we have explored two fundamental protocols—Address Resolution Protocol (ARP) and Network Address Translation (NAT)—that play critical roles in networking, facilitating seamless communication within private networks and between those networks and the internet.
We began with an overview of how ARP enables hosts within a subnet to resolve IP addresses into MAC addresses, thus allowing devices to identify and communicate with one another effectively. By maintaining an ARP table, each host can efficiently map IP addresses to their corresponding MAC addresses, ensuring reliable connectivity within a private network.
We then delved into NAT, which serves as a vital mechanism employed by internet gateways to allow multiple devices on a private network to share a single public IP address. This process not only conserves the limited number of IPv4 addresses available but also enhances security by hiding internal IP addresses from external networks. NAT enables the correct routing of data packets between local machines and remote servers, ensuring that responses from the internet are directed to the appropriate device within the private network.
Together, ARP and NAT form a foundation that underpins modern network communication. Understanding these protocols is essential for appreciating how data flows seamlessly across various layers of the network, whether between devices within the same premises or on opposite sides of the globe. As we continue to move toward an increasingly interconnected world, the importance of these protocols will only grow, paving the way for advancements in networking technology.
Subscribe to my newsletter
Read articles from Siddhartha S directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Siddhartha S
Siddhartha S
With over 18 years of experience in IT, I specialize in designing and building powerful, scalable solutions using a wide range of technologies like JavaScript, .NET, C#, React, Next.js, Golang, AWS, Networking, Databases, DevOps, Kubernetes, and Docker. My career has taken me through various industries, including Manufacturing and Media, but for the last 10 years, I’ve focused on delivering cutting-edge solutions in the Finance sector. As an application architect, I combine cloud expertise with a deep understanding of systems to create solutions that are not only built for today but prepared for tomorrow. My diverse technical background allows me to connect development and infrastructure seamlessly, ensuring businesses can innovate and scale effectively. I’m passionate about creating architectures that are secure, resilient, and efficient—solutions that help businesses turn ideas into reality while staying future-ready.