VPC Demystified: Key Facts about Virtual Private Clouds
 Jay Kasundra
Jay Kasundra
Amazon Virtual Private Cloud (Amazon VPC) enables you to launch AWS resources into a virtual network that you've defined.
A virtual private cloud (VPC) is a virtual network dedicated to your AWS account.
It is logically isolated from other virtual networks in the AWS Cloud.
You can launch your AWS resources, such as Amazon EC2 instances, into your VPC.
You can specify an IP address range for the VPC, add subnets, associate security groups, and configure route tables.
A VPC spans all the Availability Zones in the region.
After creating a VPC, you can add one or more subnets in each Availability Zone.
Each subnet must reside entirely within one Availability Zone and cannot span zones.
Default vs Custom VPC
If your account supports the EC2-VPC platform only, it comes with a default VPC that has a default subnet in each Availability Zone.
A default VPC has the benefits of the advanced features provided by EC2-VPC, and is ready for you to use. If you have a default VPC and don't specify a subnet when you launch an instance, the instance is launched into your default VPC. You can launch instances into your default VPC without needing to know anything about Amazon VPC.
Regardless of which platforms your account supports, you can create your own VPC, and configure it as you need. This is known as a non-default VPC. Subnets that you create in your non-default VPC and additional subnets that you create in your default VPC are called non-default subnets
Accessing the Internet
- Your default VPC includes an internet gateway, and each default subnet is a public subnet. Each instance that you launch into a default subnet has a private IPv4 address and a public IPv4 address. These instances can communicate with the internet through the internet gateway
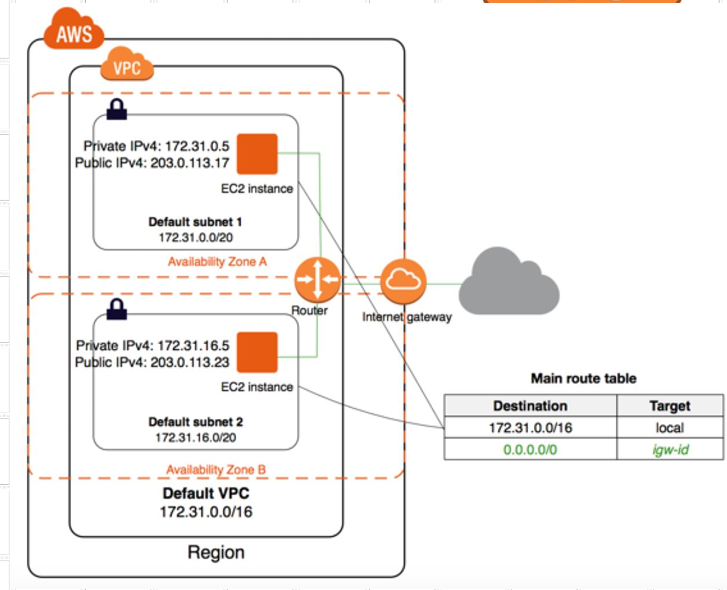
VPC and Subnet
en you create a VPC, you must specify an IPv4 CIDR block for the VPC
The allowed block size is between a /16 netmask (65,536 IP addresses) and /28 netmask (16 IP addresses)
The CIDR block of a subnet can be the same as the CIDR block for the VPC, or a subset of the CIDR block for the VPC (for multiple subnets)
The allowed block size for a subnet is between a /28 netmask and /16 netmask. If you create more than one subnet in a VPC, the CIDR blocks of the subnets cannot overlap.
Reserved IPs
The first four IP addresses and the last IP address in each subnet CIDR block are not available for you to use, and cannot be assigned to an instance.
For example, in a subnet with CIDR block 10.0.0.0/24, the following five IP addresses are reserved:
10.0.0.0: Network address.
10.0.0.1: Reserved by AWS for the VPC router.
10.0.0.2: Reserved by AWS for the IP address of the DNS server
10.0.0.3: Reserved by AWS for future use.
10.0.0.255: Network broadcast address. We do not support broadcast in a VPC
Public & Private Subnet
The instances in the public subnet can send outbound traffic directly to the Internet, whereas the instances in the private subnet can't.
Instead, the instances in the private subnet can access the Internet by using a network address translation (NAT) gateway that resides in the public subnet
NAT
You can use a NAT device to enable instances in a private subnet to connect to the internet (for example, for software updates) or other AWS services, but prevent the internet from initiating connections with the instances. A NAT device forwards traffic from the instances in the private subnet to the internet or other AWS services, and then sends the response back to the instances.
AWS offers two kinds of NAT devices
NAT Gateway : You are charged for creating and using a NAT gateway in your account. NAT gateway hourly usage and data processing rates apply.- NAT Instance
A NAT instance is launched from a NAT AMI
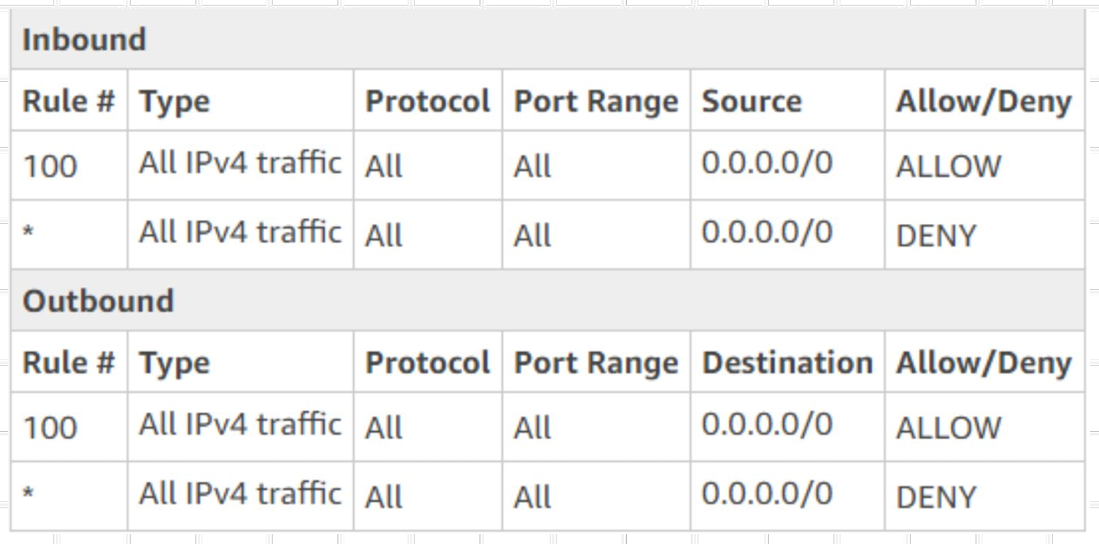
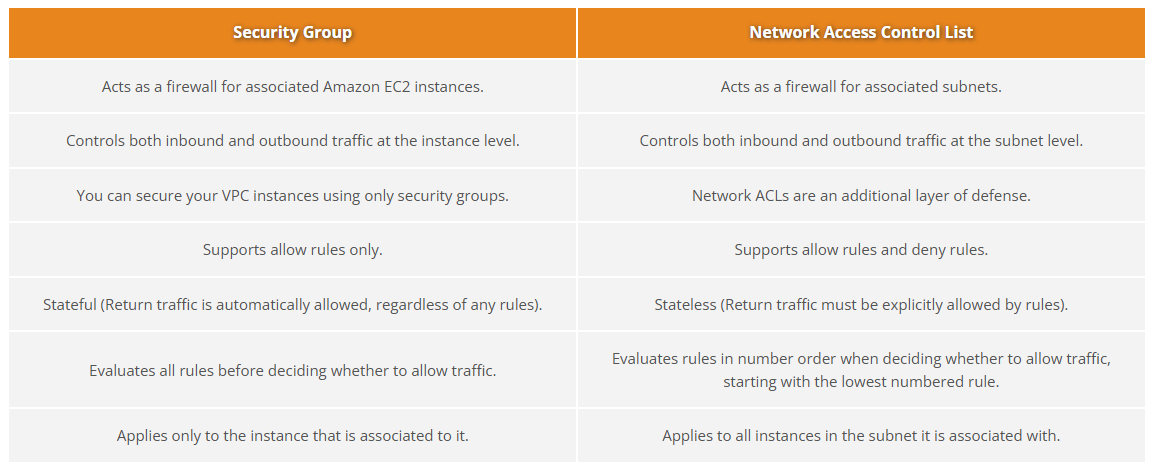
NACL
A network access control list (ACL) is an optional layer of security for your VPC that acts as a firewall for controlling traffic in and out of one or more subnets
Each subnet in your VPC must be associated with a network ACL
You can associate a network ACL with multiple subnets
A subnet can be associated with only one network ACL at a time
A network ACL has separate inbound and outbound rules, and each rule can either allow or deny traffic
Network ACLs are stateless
NACL vs Security group
Route Tables
A route table contains a set of rules, called routes, that are used to determine where network traffic from your subnet or gateway is directed.
Main route table - The route table that automatically comes with your VPC. It controls the routing for all subnets that are not explicitly associated with any other route table.
Custom route table - A route table that you create for your VPC.
Each subnet in your VPC must be associated with a route table
A subnet can only be associated with one route table at a time, but you can associate multiple subnets with the same subnet route table
Internet Gateway
An internet gateway is a horizontally scaled, redundant, and highly available VPC component that allows communication between instances in your VPC and the internet.
It therefore imposes no availability risks or bandwidth constraints on your network traffic
Creation VPC in AWS
To access VPC, type "VPC" in the search bar and click on the first result. Click on Create VPC.
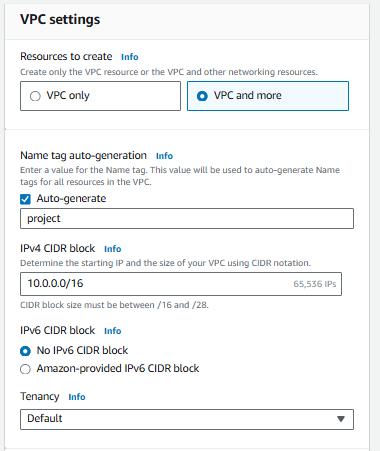
Select "VPC and more" and then choose the CIDR range.
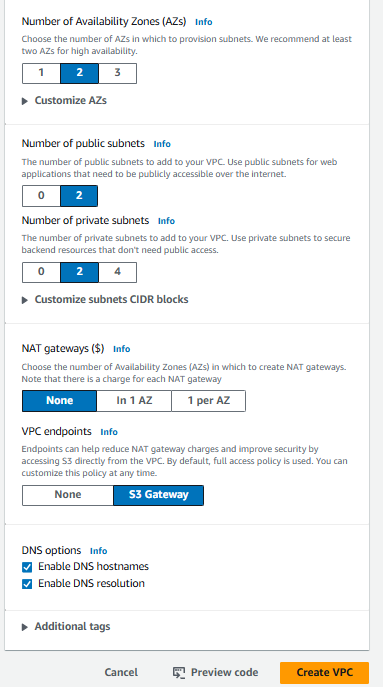
Choose the number of Availability Zones (AZs), the number of public and private subnets, and the number of NAT gateways. Then, click on Create VPC.
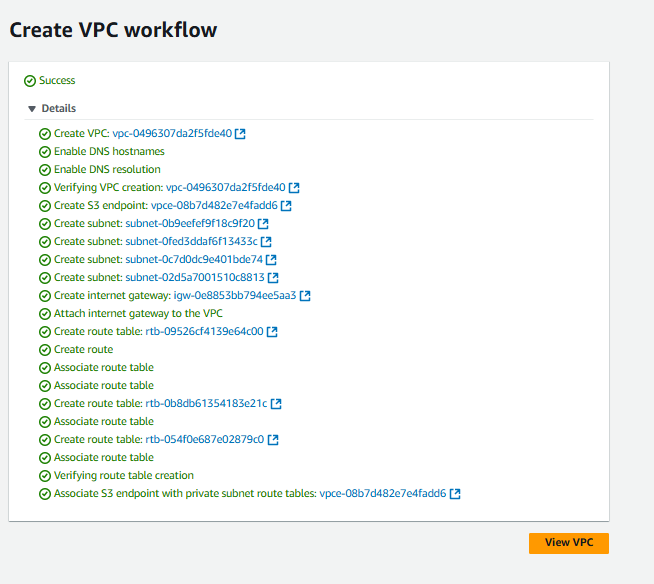
Wait for all the checks to turn green. Then, click on View VPC.
How to select non-default VPC while creating EC2 instance.
When launching an EC2 instance, click on Edit in the Network settings.
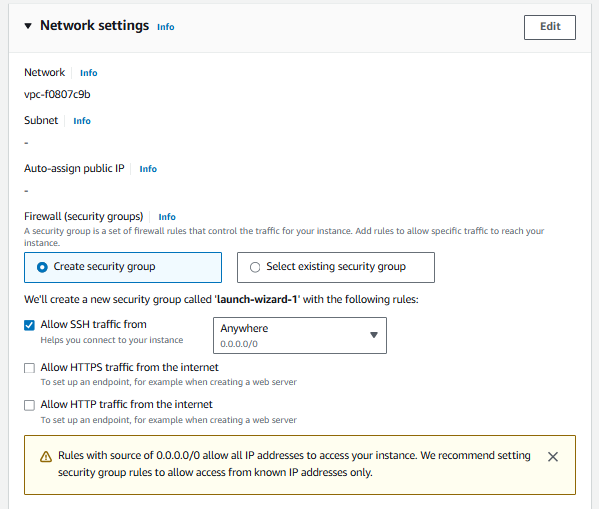
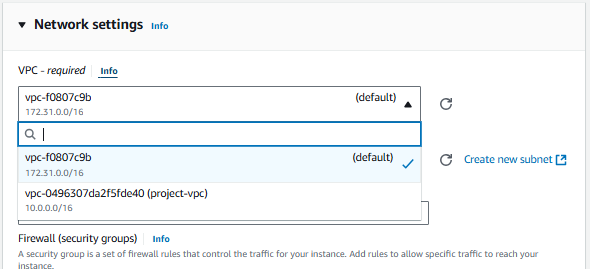
Select your non-default VPC from dropdown.
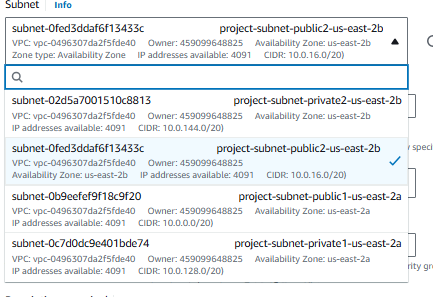
Select the required subnet for the instance. Then Launch instance
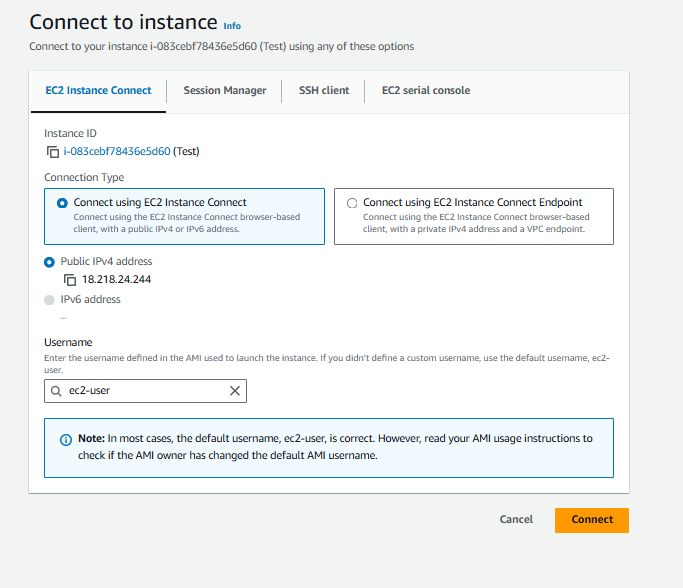
Accessing of EC2 server in private Subnet - Bastian Host/Jump Server
Create an EC2 server in a private subnet. Ensure the key pair is downloaded. Then connect to public EC2 instance
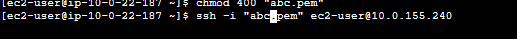
Create new .pem file using CLI command.
Open the key pair .pem file of the EC2 instance in the private subnet. Copy and paste the content into the CLI, then exit the file editor.
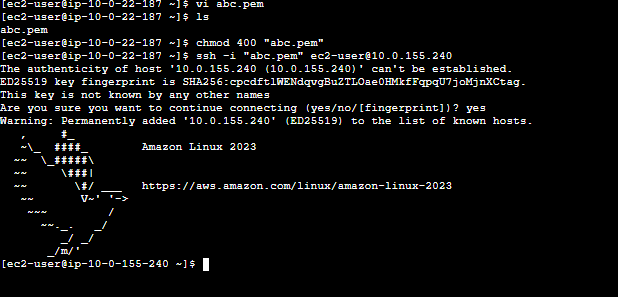
Now, use the SSH client connection option to connect to the EC2 server in the private subnet.
The user can now access the EC2 server located in the private subnet.
VPC Flow Logs
VPC Flow Logs is a feature that enables you to capture information about the IP traffic going to and from network interfaces in your VPC.
Flow log data can be published to Amazon CloudWatch Logs or Amazon S3
You can create a flow log for a VPC, a subnet
Creation of VPC flow logs
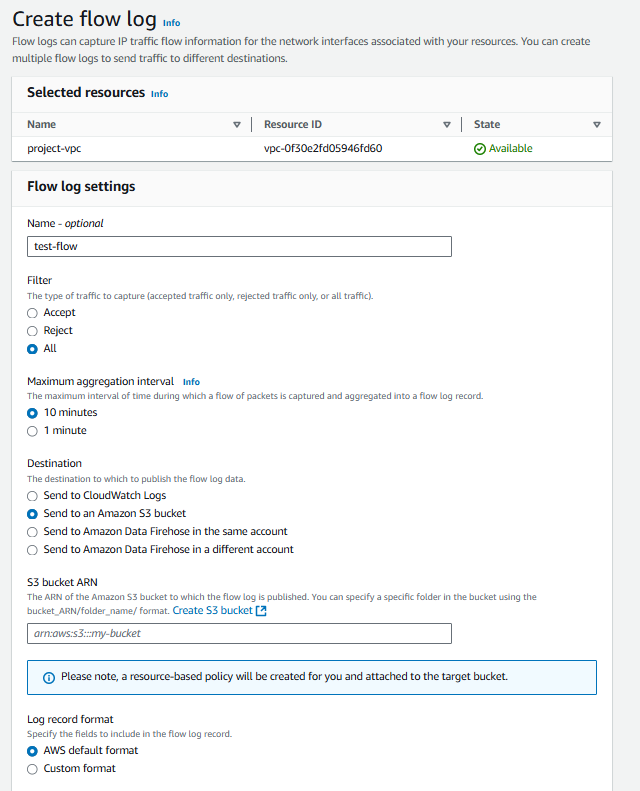
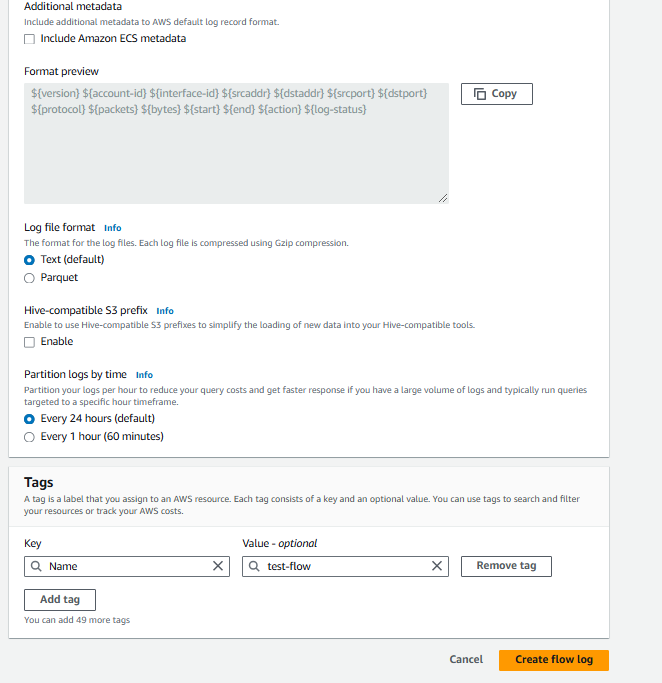
To generate VPC flow logs, open your VPC, click on Flow Logs, and then click on Create Flow Log.
Enter a name and choose any option you prefer from the provided choices. Then click on "Create flow log."
VPC Peering
A VPC peering connection is a networking connection between two VPCs that enables you to route traffic between them privately.
Instances in either VPC can communicate with each other as if they are within the same network.
You can create a VPC peering connection between your own VPCs, with a VPC in another AWS account, or with a VPC in a different AWS Region.
AWS uses the existing infrastructure of a VPC to create a VPC peering connection; it is neither a gateway nor an VPN connection, and does not rely on a separate piece of physical hardware.
There is no single point of failure for communication or a bandwidth bottleneck.
Working of VPC Peering
To create a VPC peering connection, open the peering connection from the left navigation menu and click on "Create peering connection."
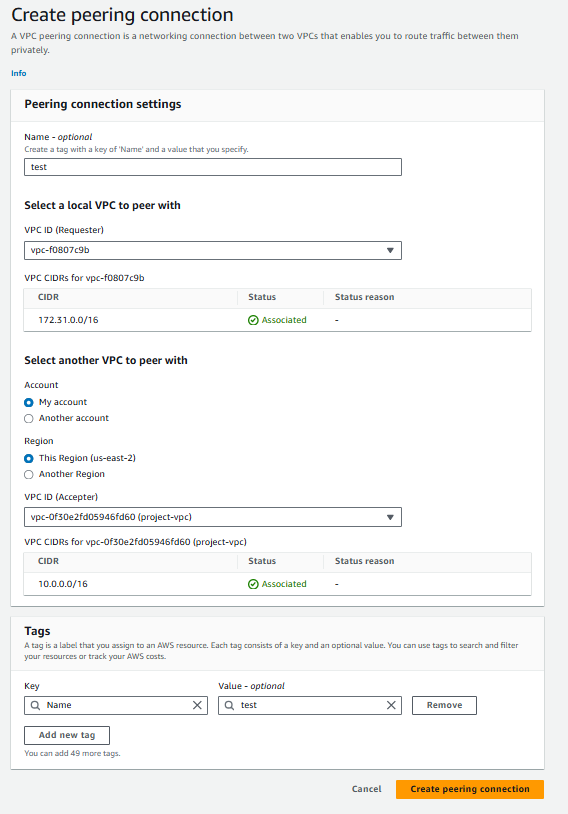
Select the local VPC and another VPC from the dropdown menu.
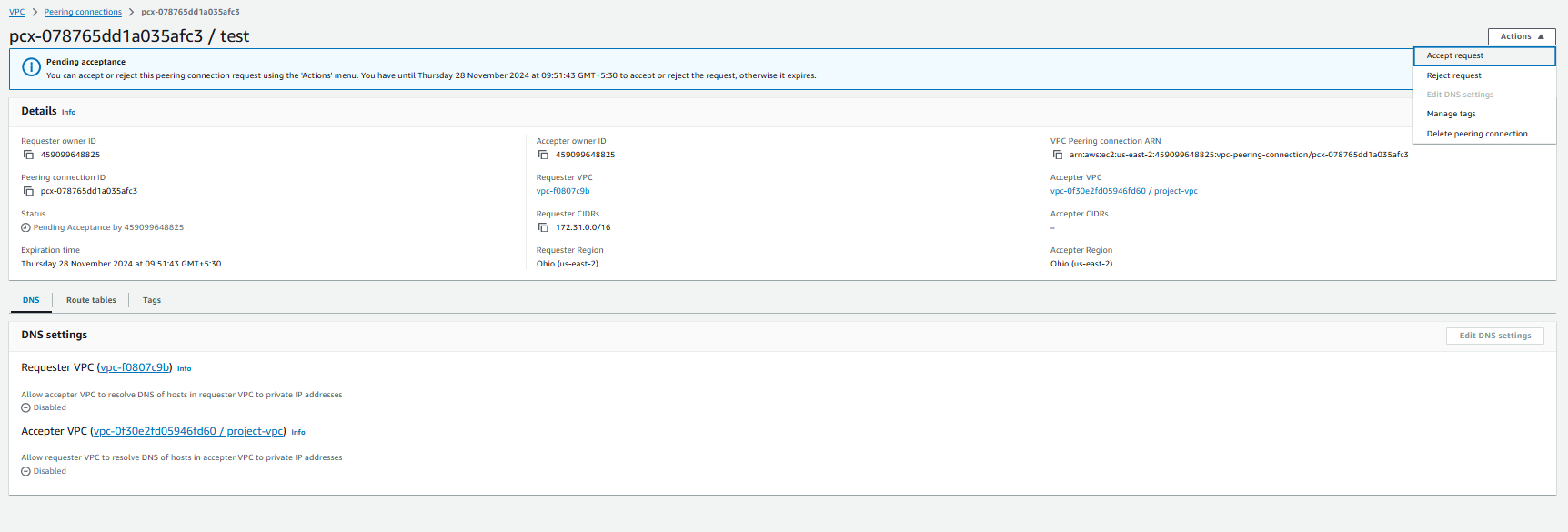
Click on the "Actions" option from the peering request. You will see two options: "Accept Request" and "Reject Request." Choose the one that fits your needs.
Direct Connect
AWS Direct Connect is a cloud service solution that makes it easy to establish a dedicated network connection from your premises to AWS.
Using AWS Direct Connect, you can establish private connectivity between AWS and your datacenter, which in many cases can reduce your network costs, increase bandwidth throughput, and provide a more consistent network experience than Internet-based connections.
Subscribe to my newsletter
Read articles from Jay Kasundra directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
