Brute Force attacks using Hashcat
 Peter Gari
Peter Gari
I’m in the final year of my electronic and computer engineering course, and one of my favorite topics this semester has been Cryptography and Network Security. Recently, we explored password cracking and brute force attacks, including a class assignment to crack the password of a protected Excel file. This made me more curious about the topic and led me to a rabbit hole , leading me to dive deeper into brute force attacks and tools like Hashcat. In this article, I’ll share what I’ve learned so far through an introduction to bruteforce attacks with Hashcat.
What Are Brute Force Attacks?
A brute force attack is a method used to guess a password or encryption key by systematically trying every possible combination until the correct one is found. This attack relies on the sheer processing power of modern systems to crack weak or predictable passwords. While it can be time-consuming, brute force remains effective, especially against poorly secured files or accounts.
What Is Hashcat?
Hashcat is a powerful, open-source password recovery tool that leverages the processing power of CPUs and GPUs to perform attacks like brute force, dictionary attacks, and more. It supports numerous hashing algorithms and is highly efficient for cracking password-protected files and systems.
Setting Up Hashcat on a MacBook Pro
In this article, I will be setting up hashcat on a macbook pro. (Look out for my next article which will do the same in Ubuntu) . The following command can be used to install: brew install hashcat

This command will install the latest version of hashcat
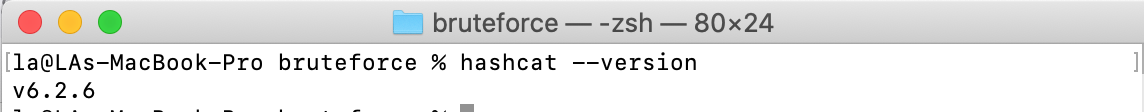
You can confirm the installation of hashcat using hashcat --version
Here are other commands you can run on the terminal to familiarize with the hashcat.
hashcat -I : Displays detailed information about the devices available for processing, such as your CPU or GPU.
hashcat --help : Lists all available options and parameters in Hashcat.
hashcat -b: Tests the performance of your hardware across different hashing algorithms.
hashcat --example-hashes: Displays a list of supported hash types along with examples.
hashcat --restore: Resumes a previously paused or interrupted cracking session.
hashcat --stdout: Simulates the attack without performing any cracking to check if your parameters are correct.
If you’re using hashcat for the first time, I encourage you to run the above commands and observe the output in order to familiarize with it. These commands are helpful for exploring and mastering Hashcat beyond just password cracking.
Basic Brute Force Commands in Hashcat
Hashcat works by targeting hashed passwords. To brute force a hash, you’ll first need to know the hash type of the password. Here’s a basic rundown of commands:
Generate a Hash File
Extract the hash from your target file (for my class assignment, an Excel file) using a tool like John the Ripper or a similar utility. Save the hash to a file, e.g.,hash.txt.Run a Basic Brute Force Attack
Use the following command:hashcat -m [hash_type] -a 3 hash.txt ?a?a?a?a
-m: Specifies the hash type (e.g.,9600for Excel 2013+).-a 3: Indicates a brute force attack.?a?a?a?a: Specifies the keyspace (four characters in this case).
Adjust the?apattern based on the complexity and length of the password.
Brute Forcing an Excel File
Extract the Hash
For Excel files we need to first extract the hash. This is done by using a tool like office2john (available in theJohn the Rippersuite) to extract the hash, In this case, my excel file was named “Finance Sample.xlsx”:python office2john.py Finance Sample.xlsx > hash.txt
Identify the Hash Type
It is important to know the exact hash type, this will be part of the command used to perform the bruteforce. The hash mode for different types of hashes can be obtained from the hashcat website (https://hashcat.net/wiki/doku.php?id=example_hashes) or using the command, hashcat —example-hashesExcel files use specific hash modes:
Excel 2010:
9400Excel 2013+:
9600
Run Hashcat
Using the extracted hash, run:
hashcat -m 9600 -a 3 hash.txt ?a?a?a?a?a
This attempts passwords of up to 5 characters. Increase ?a repetitions for longer passwords.
Resume Interrupted Cracks
If the attack stops or you need to pause, use:
hashcat --restore
Final Thoughts
While brute force attacks are educational and showcase the importance of strong passwords, they highlight the need for robust security practices. Use these tools responsibly, ensuring that you only test on files you own or have explicit permission to analyze.
Note: Note: Brute force attacks are computationally intensive, and you may notice a significant slowdown on your computer during the process. Hashcat allows you to specify whether to use your CPU or GPU, which can help improve performance. I will cover this in an upcoming article.
Sources
Wikipedia contributors. (n.d.). Brute force attack. Wikipedia. Retrieved from https://en.wikipedia.org/wiki/Brute-force_attack
Hashcat. (n.d.). Hashcat Documentation. Retrieved from https://hashcat.net/wiki/
Subscribe to my newsletter
Read articles from Peter Gari directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
