Create site-to-site connectivity from on-premises to Azure Cloud using Azure VPN.
 Elinathan Olotu
Elinathan Olotu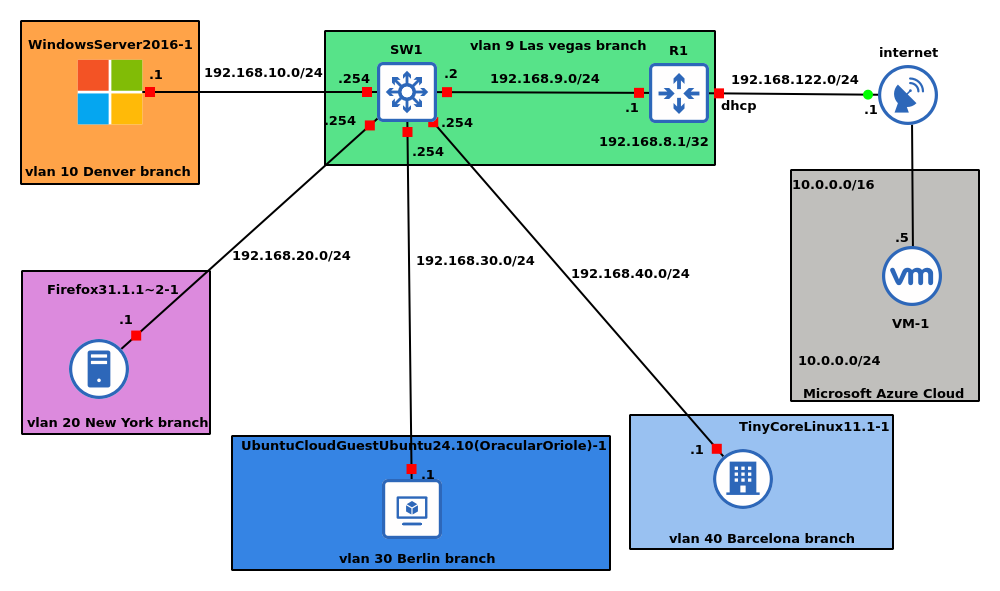
In this article, I will demonstrate how to connect on-premises infrastructure to Azure cloud via VPN and using the BGP routing protocol.
BGP is an optional feature for Azure Route-Based VPN gateways. It allows you to connect new office sites, thereby enabling scalability dynamically.
In the article, I am connecting only the Las Vegas site to my resources in Azure, while the other sites are connecting to my Las Vegas site to get access to the resources in Azure.
Prerequisites
You need to have these things to emulate this configuration, which I will list below.
You need an account with Azure.
You also need to download the emulator I used for this demonstration, GNS3.
You also need to have images to emulate software on the switch, router, and the 4 servers I used. For the router and switch, I used a Cisco IOL that emulates Cisco iOS 15.x, and for the servers, I used Windows Server 2016 and different variants of Linux servers.
There are multiple ways your on-premises infrastructure can connect securely with your infrastructure in the cloud. In this blog, we will be exploring the VPN method, as it is arguably the most affordable method depending on certain factors and usage.
Introduction
There are two methods of using Azure Route-Based VPN gateways.
The first method is a case where the network engineer manually configures the sites using static routing, and the second method uses the routing protocol BGP, which enables the sites to be added dynamically.
I will be creating a virtual network in Azure and then also creating a Windows Server 2022 server virtual machine, then using Azure VPN to connect it to my on-premises sites that I have already created in GNS3 as shown in the diagram below.
The VPN connection is going to take place between the router R1 and the VPN Gateway.
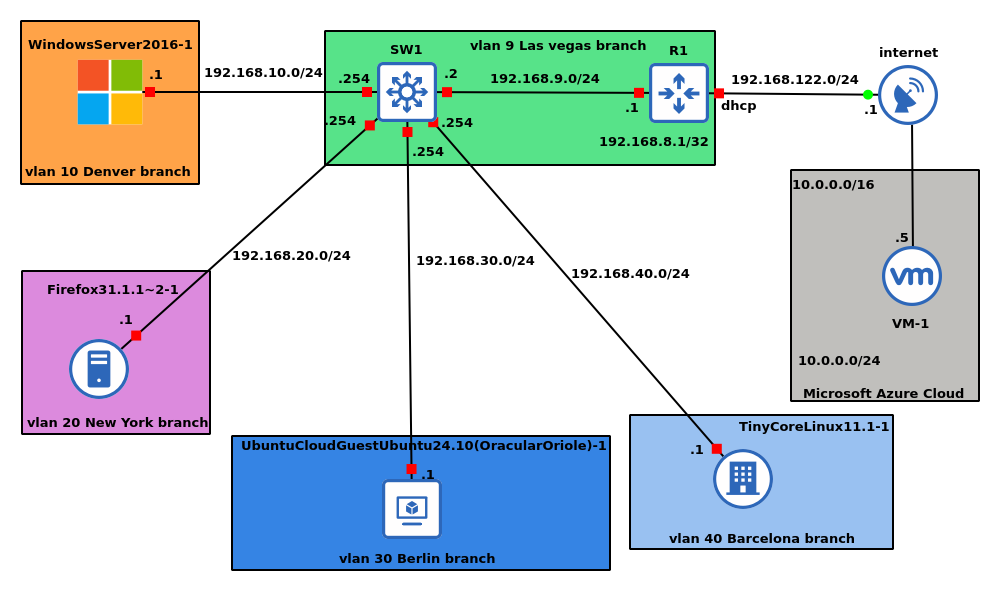
The diagram above is called a topology. A topology is how everything in the network is connected. Think of it as the layout or the map of how devices talk to each other; an example is the diagram above.
Setting up the Azure cloud infrastructure
Setup VNET in Azure cloud
I created a resource group named reggierg.
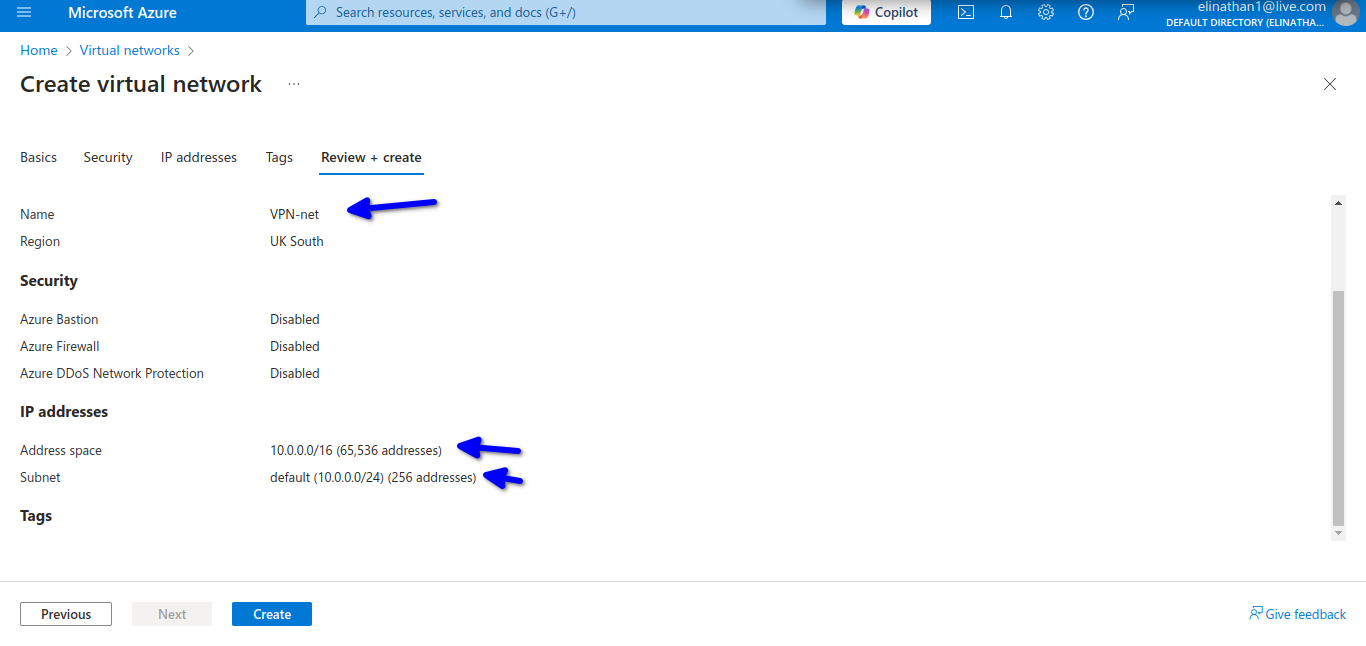
In the above diagram, I named the virtual network VM-net, and we will be using the 10.0.0.0/24 subnets and assigning them to our devices in the Azure cloud. Then I click on create to create the virtual network.
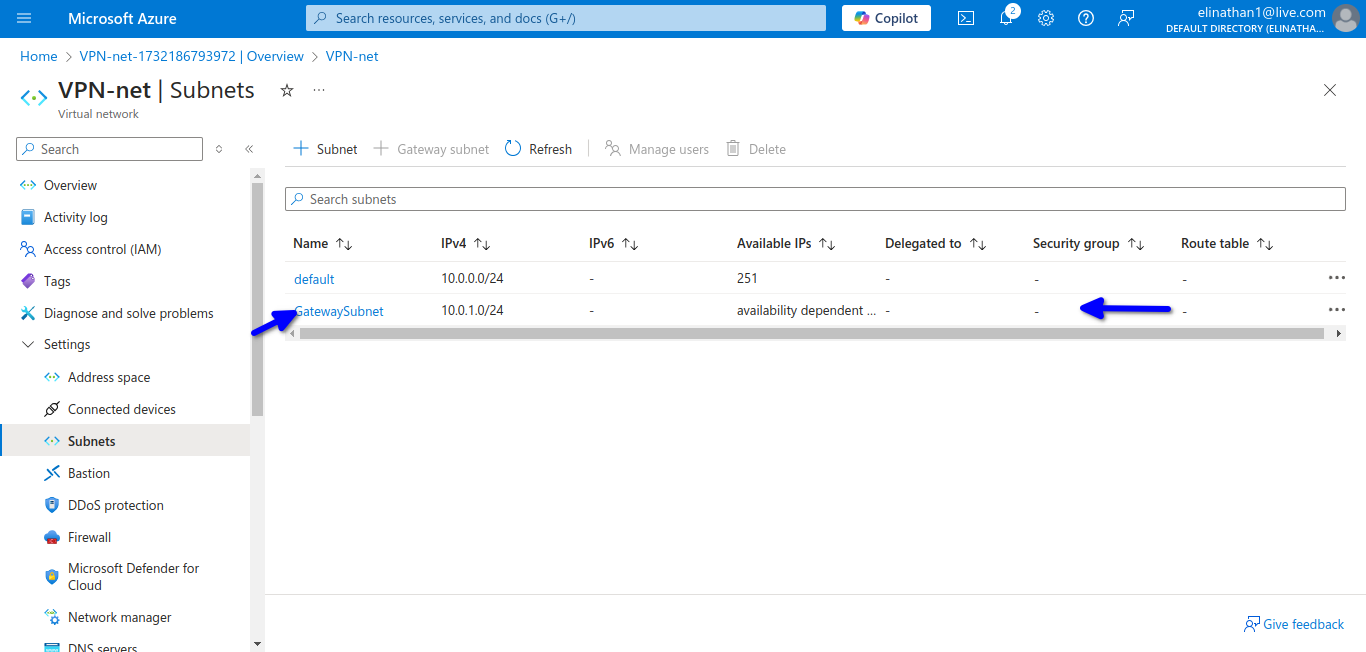
Setup Gateway Subnet
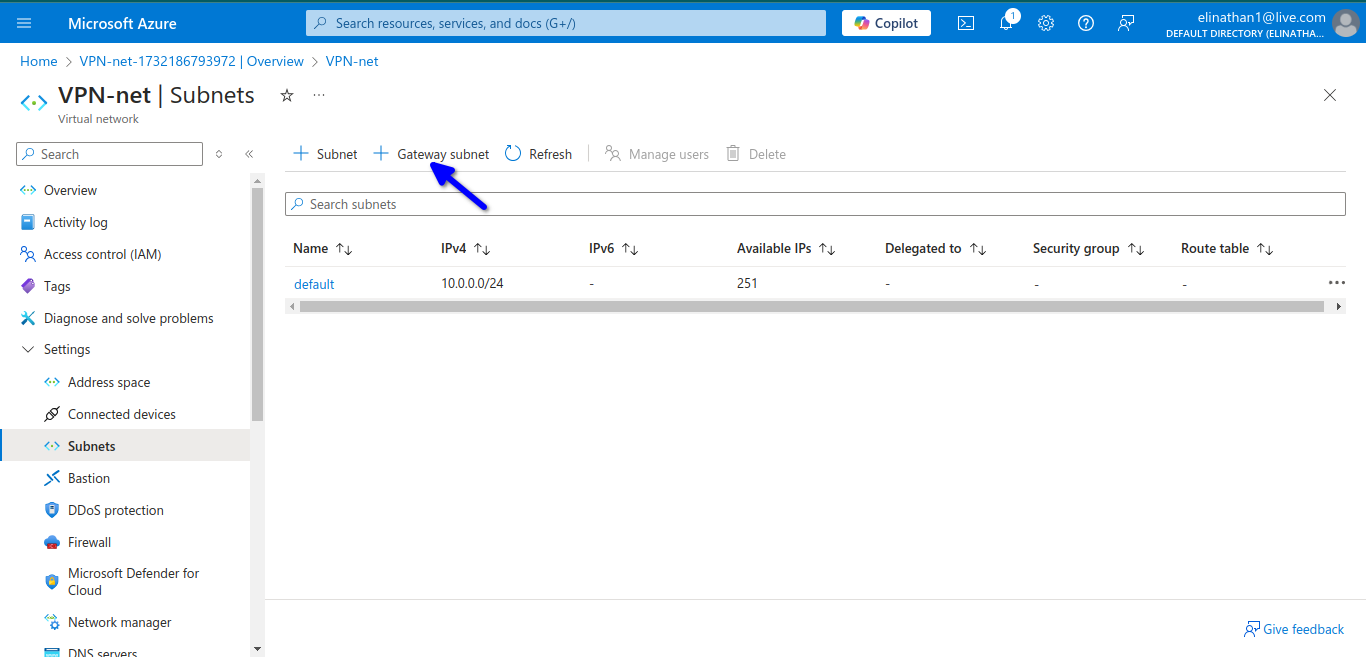
then add the gateway
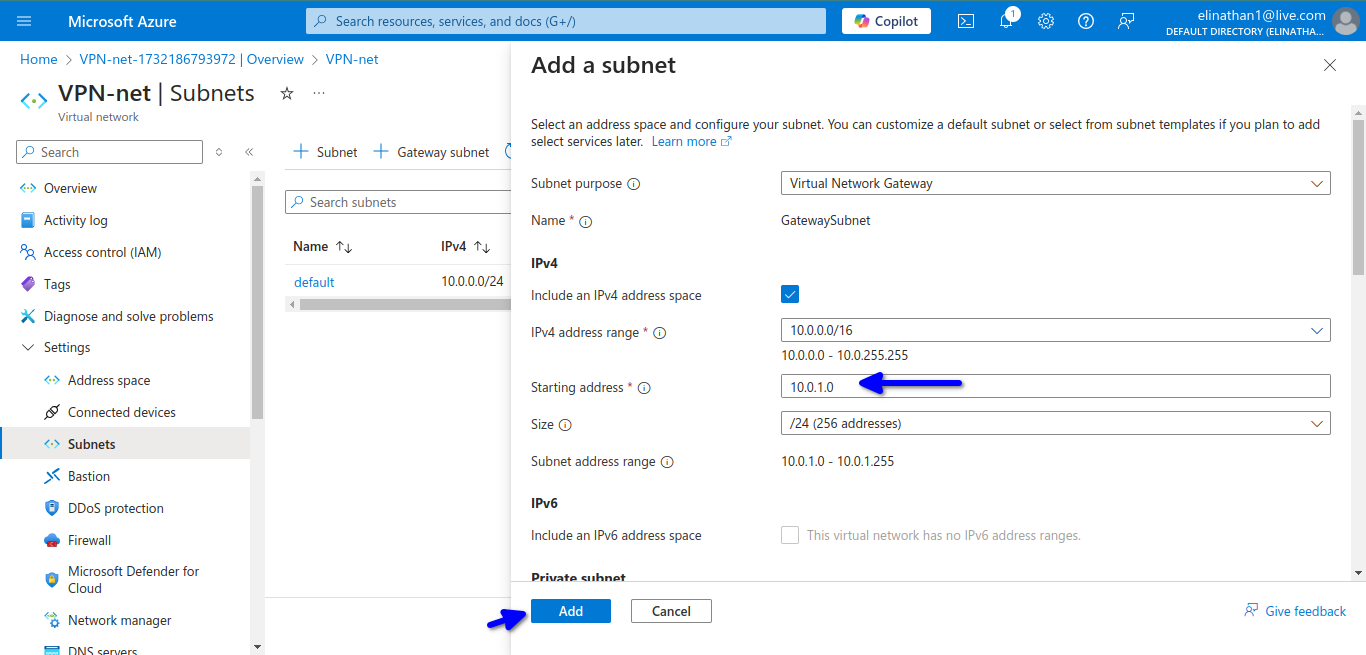
The subnet for the gateway is 10.0.1.0/24. By default, Azure automatically assigns a private IP address from the GatewaySubnet prefix range as the Azure BGP IP address on the VPN gateway. The custom Azure APIPA BGP address is needed when your on-premises VPN devices use an APIPA address (169.254.0.1 to 169.254.255.254) as the BGP IP.
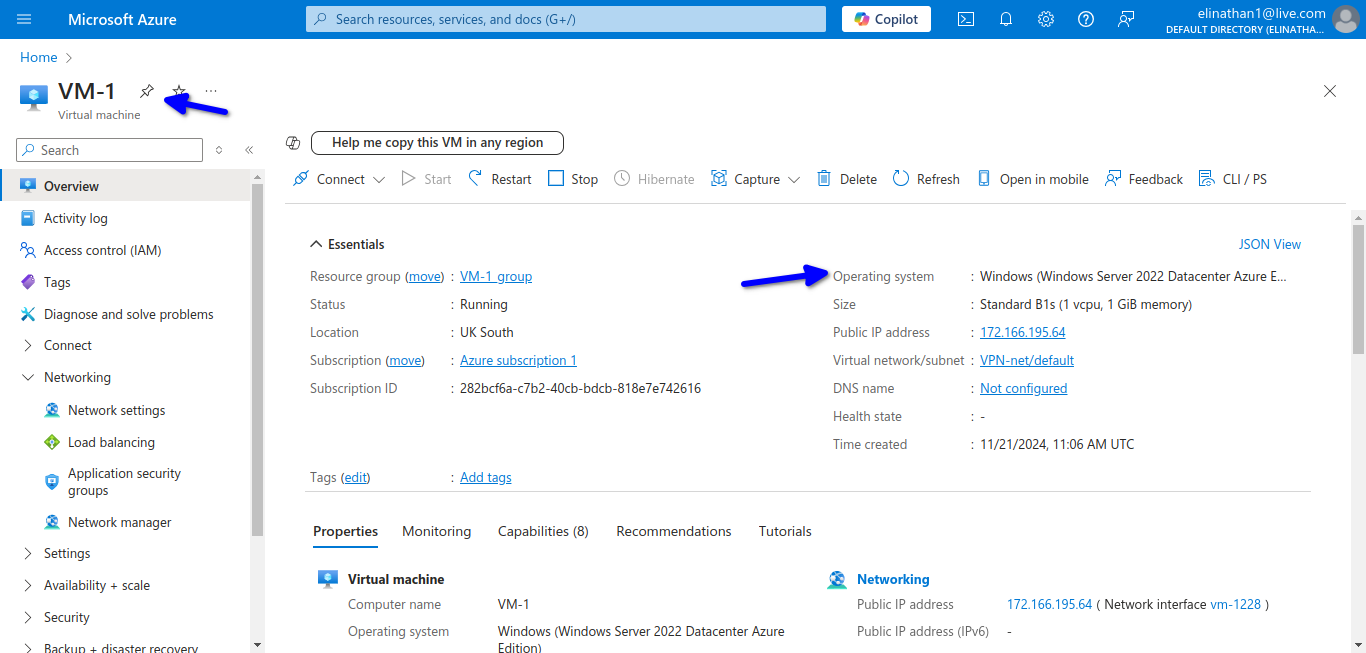
Now I created a virtual machine and named it VM-1
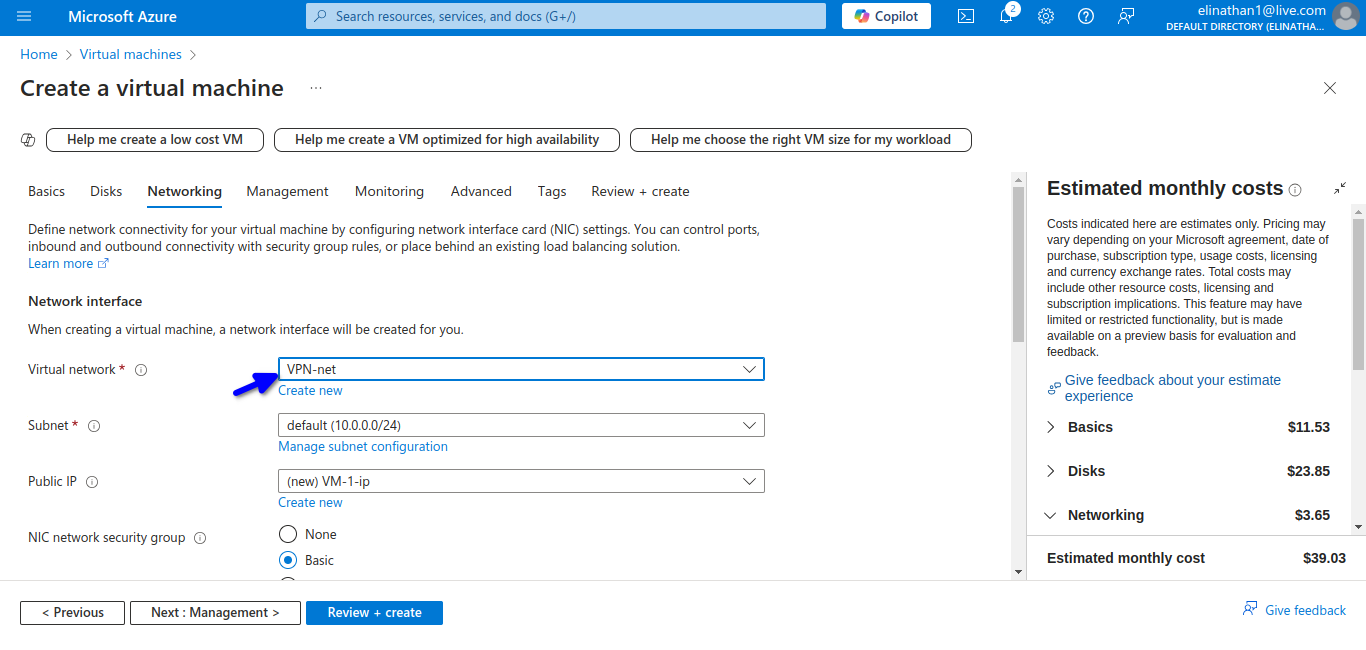
I added the virtual network earlier created to it.
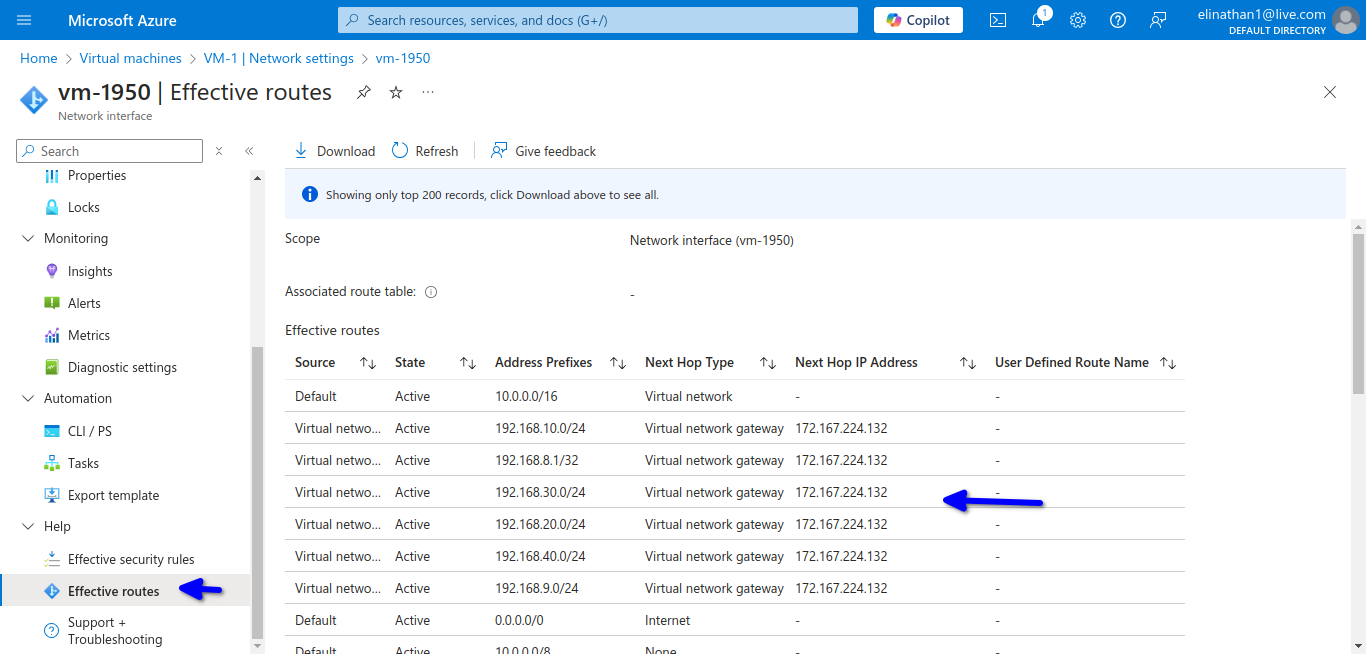
The current active routes in the virtual machine running Windows Server 2022 are marked in the diagram below.
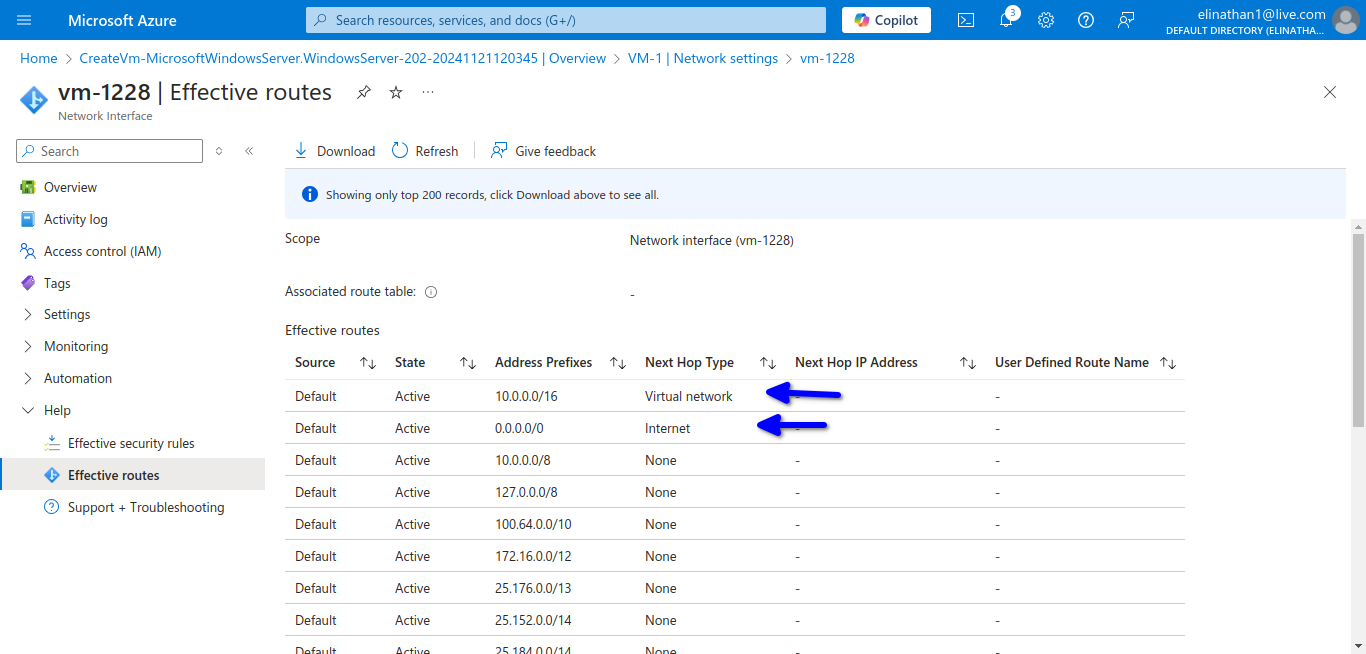
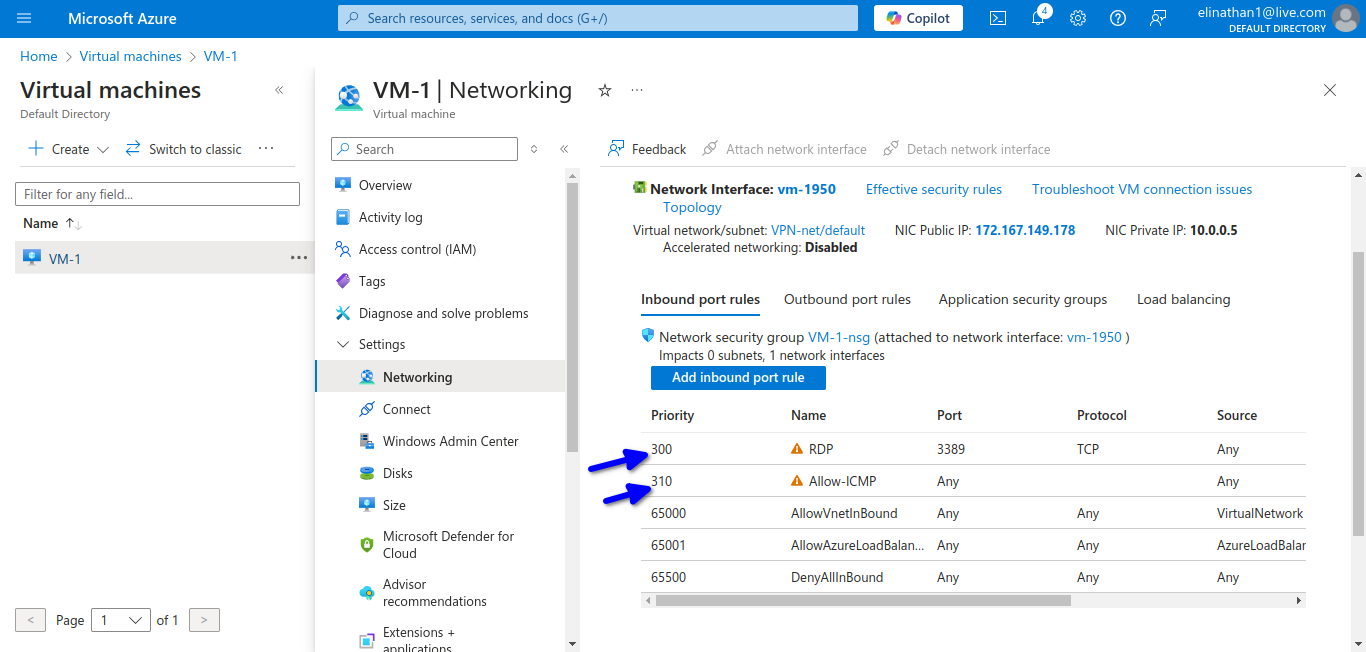
I enabled ping through the firewall to test connectivity from the virtual machine in Azure to on-premises devices.
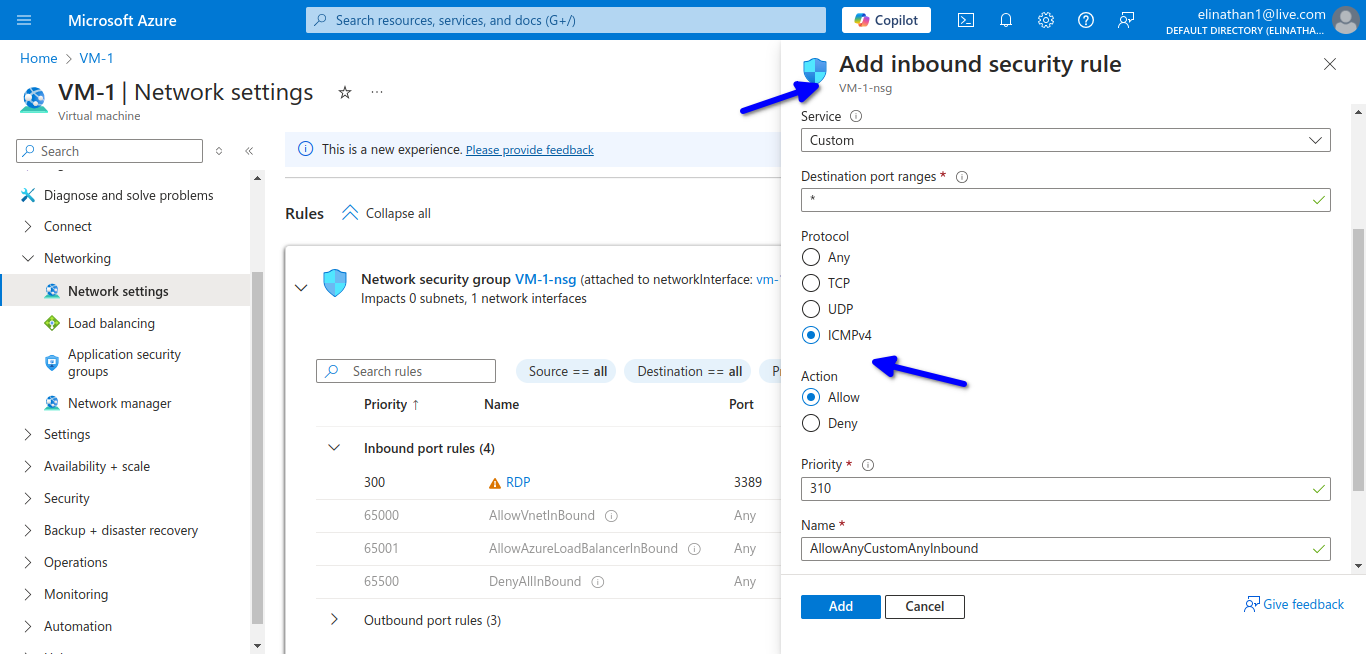
Here I allowed rdp to the Windows Server 2022 and also ICMP protocol in order to connect to the server and also test connectivity.
Setup VPN Gateway
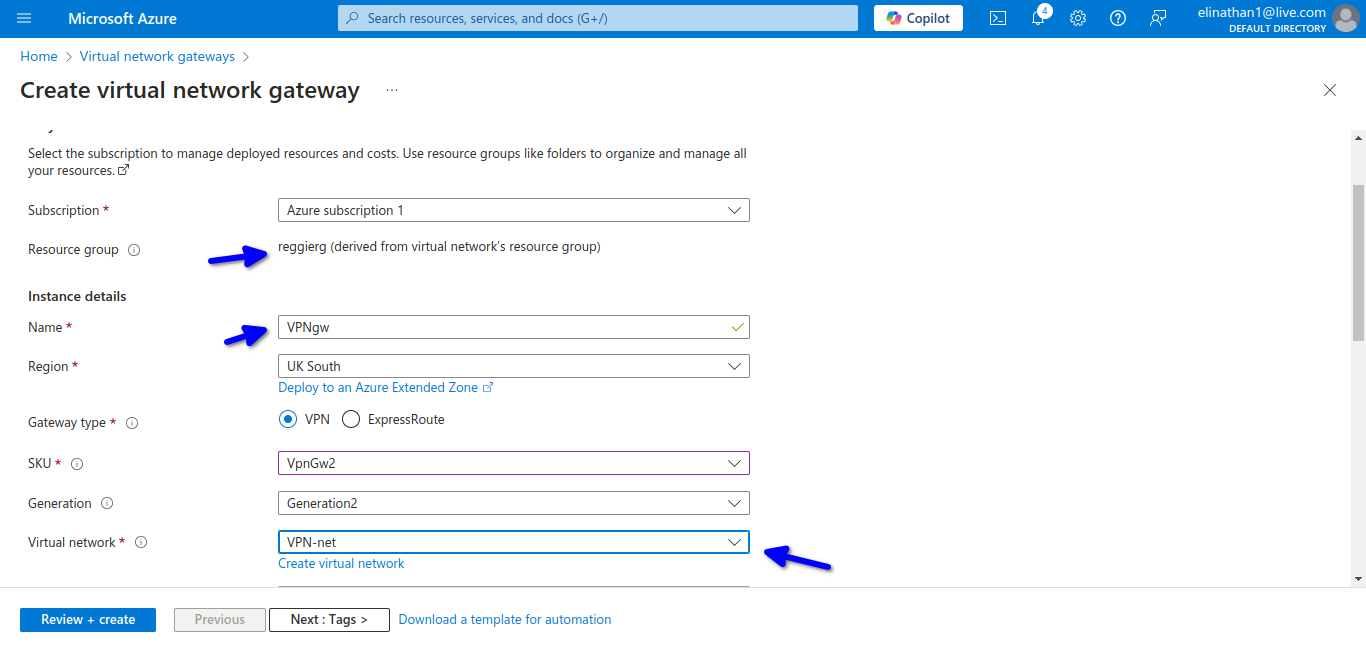
As the diagram above indicates, they all have to be in the same resource group and virtual network.
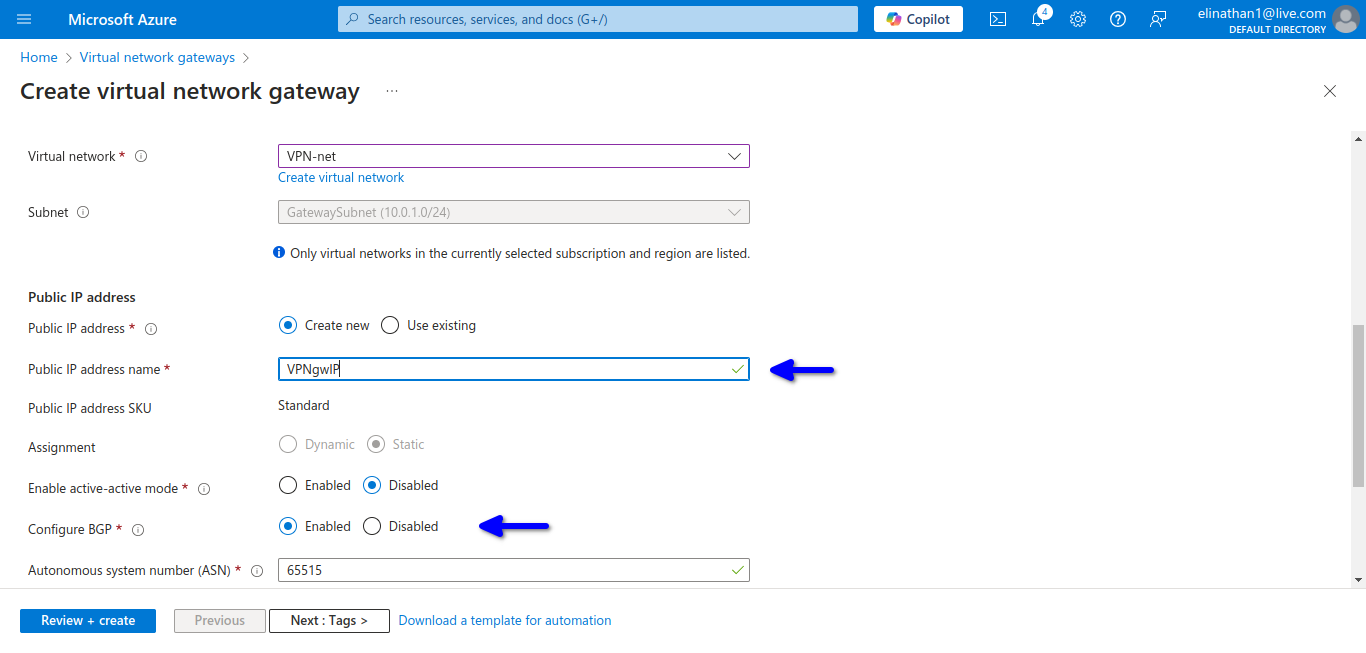
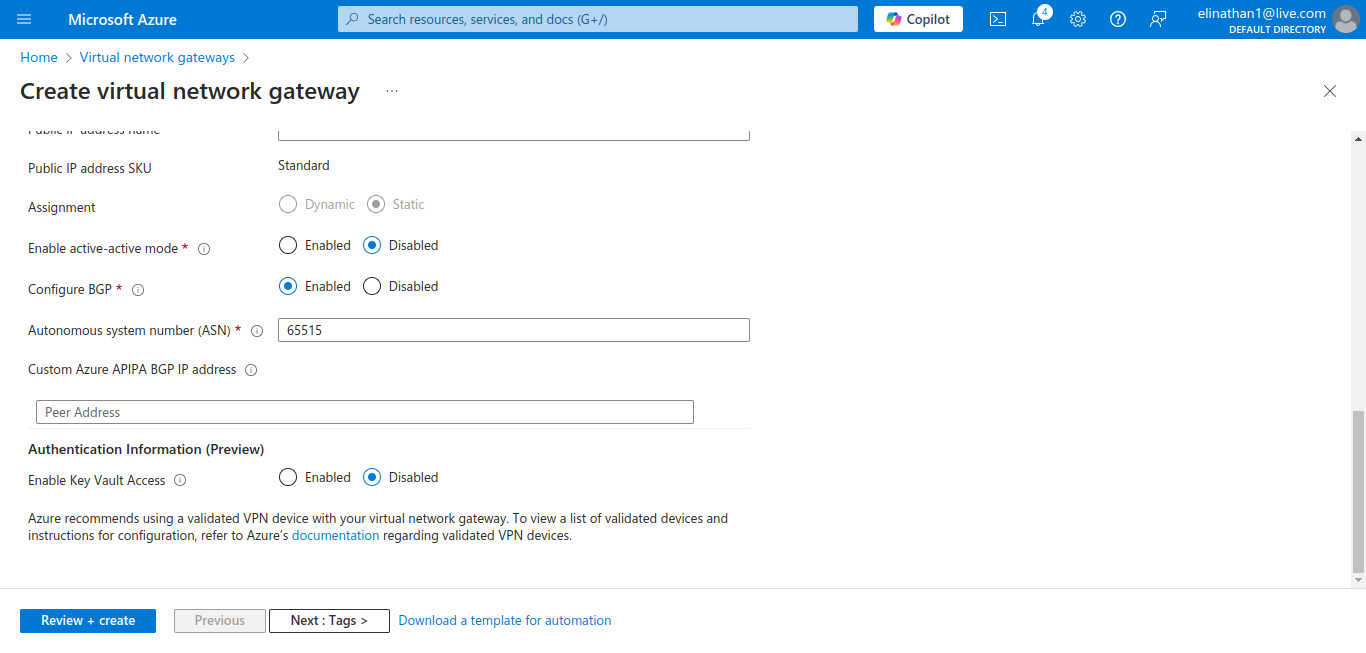
The VPN Gateway will be set up in 45 minutes, so you will have to wait. Enabling BGP in the virtual network gateway automatically gives you the private ASN of 65515.
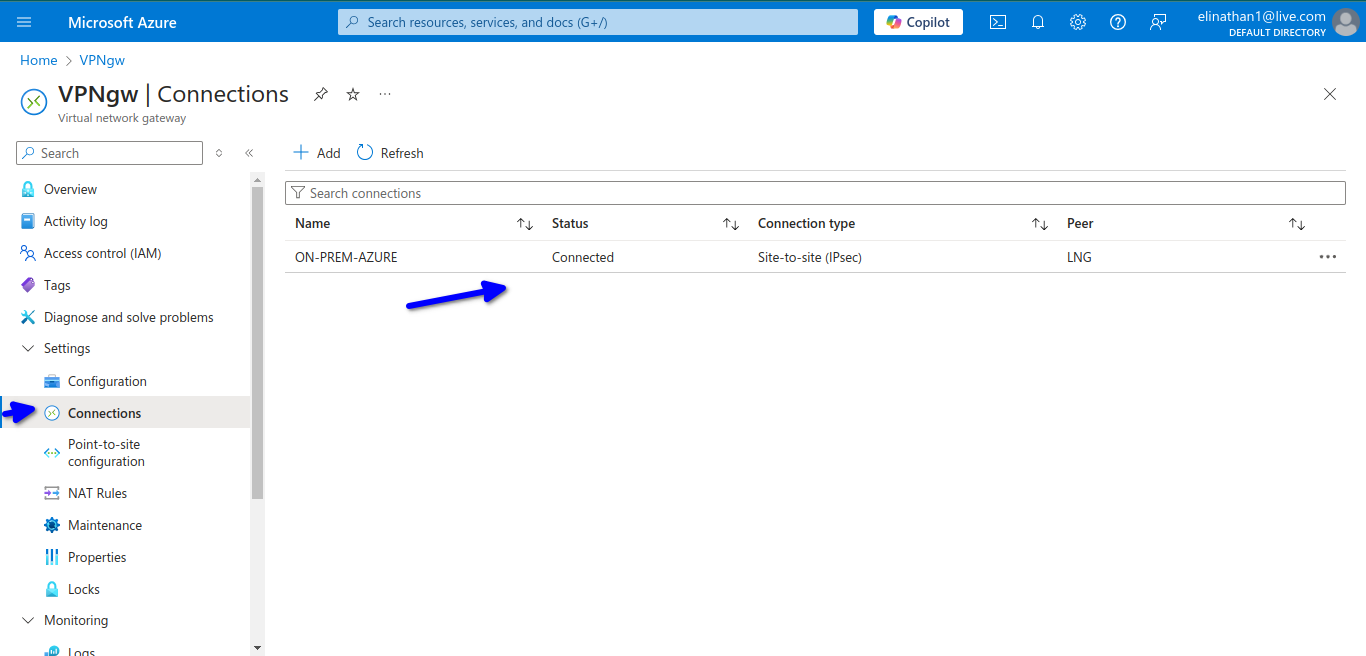
Check VPN Gateway Status
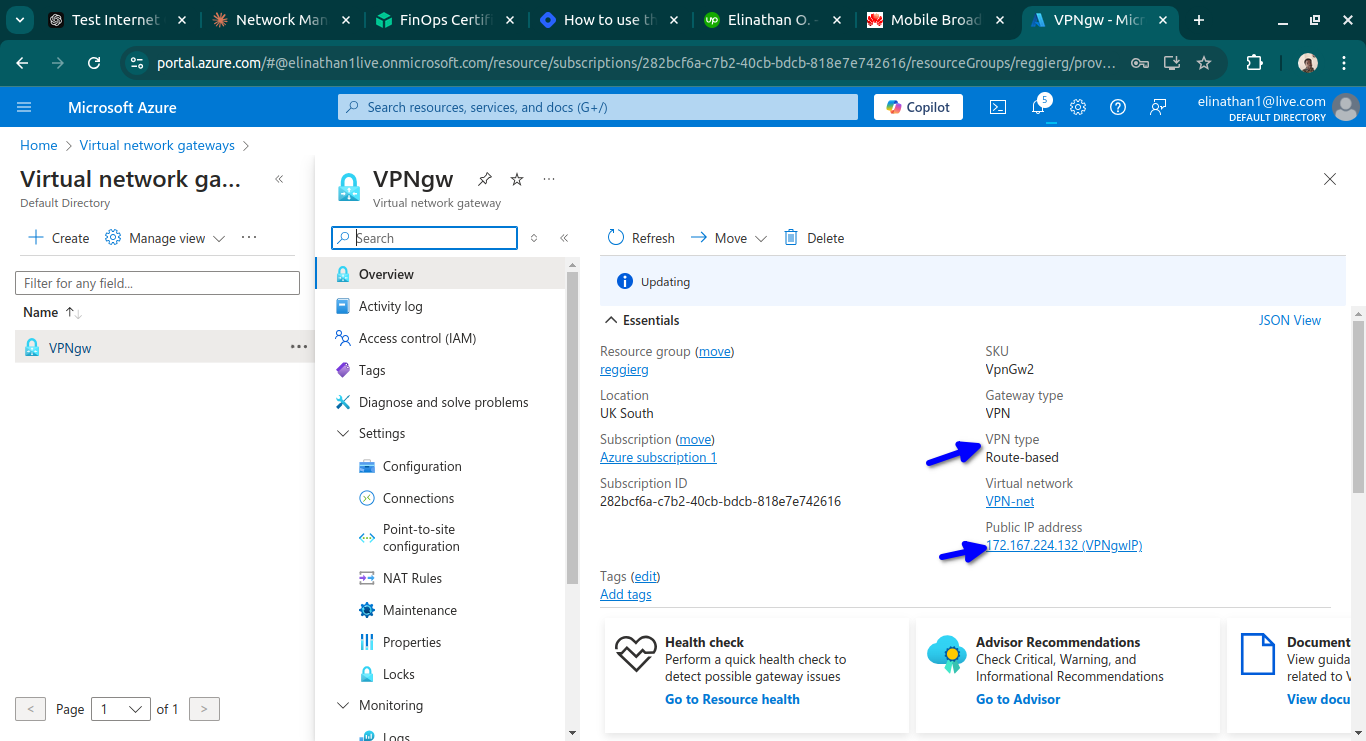
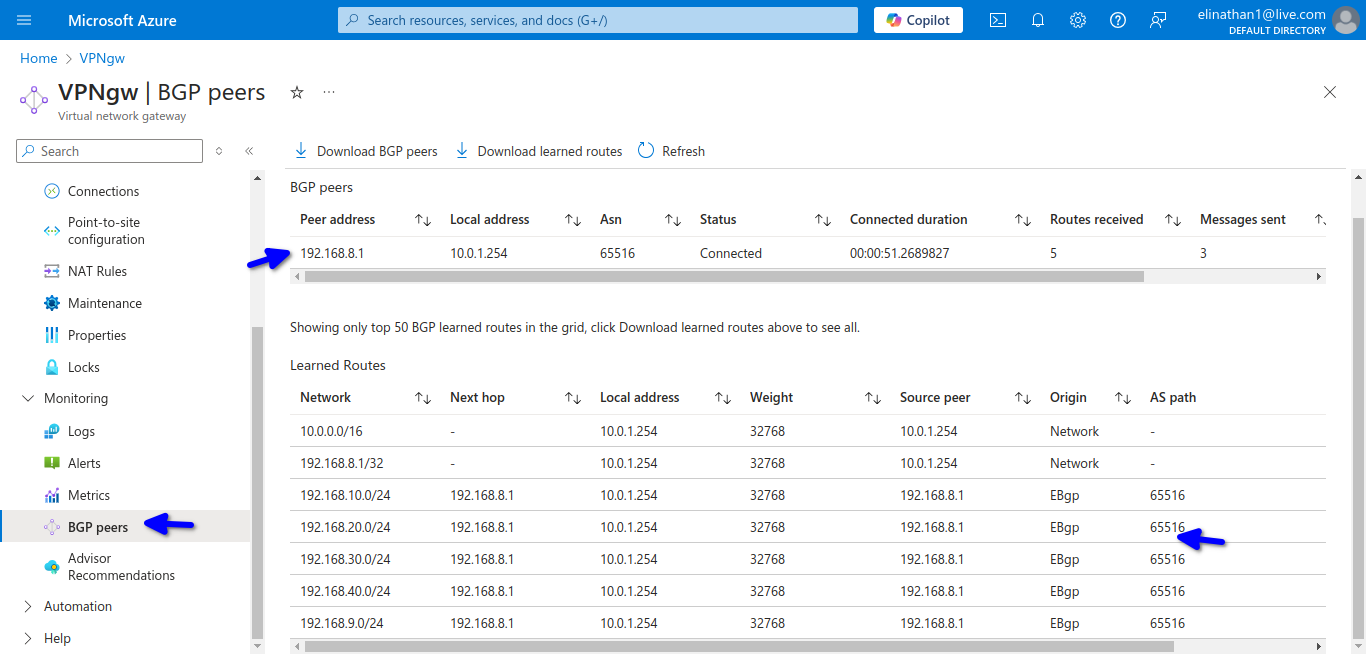
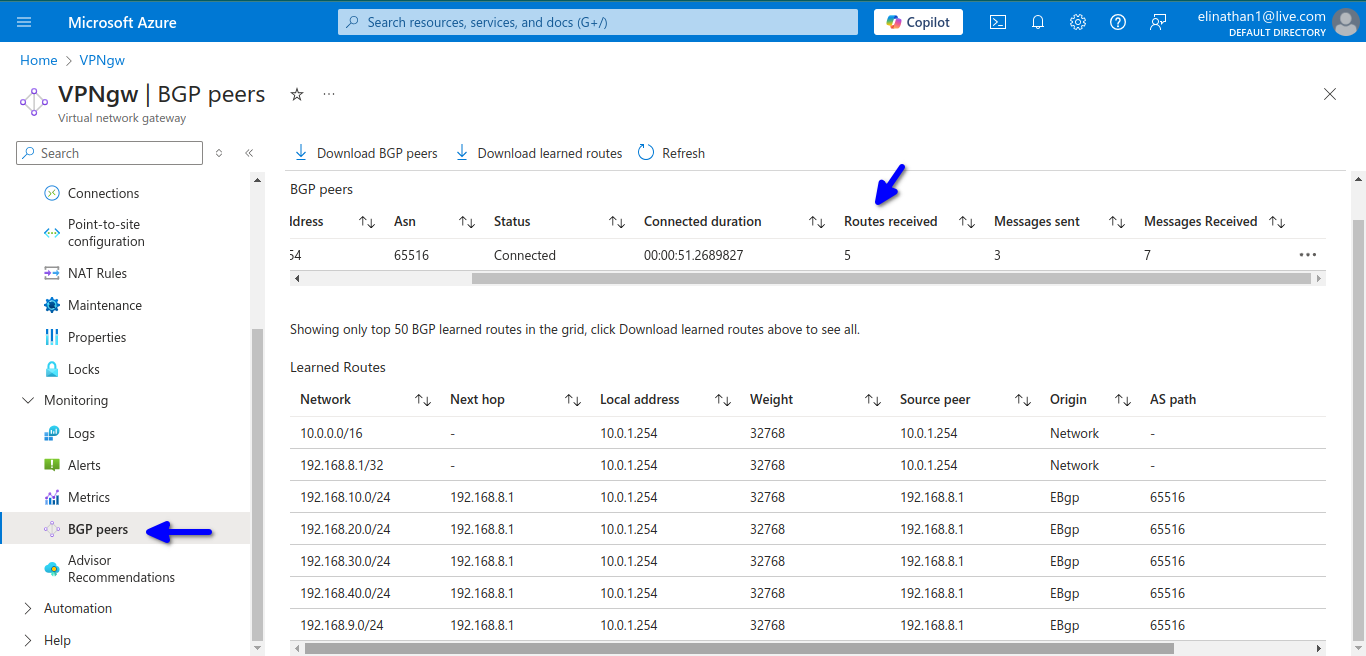
Check VPN Gateway BGP Information
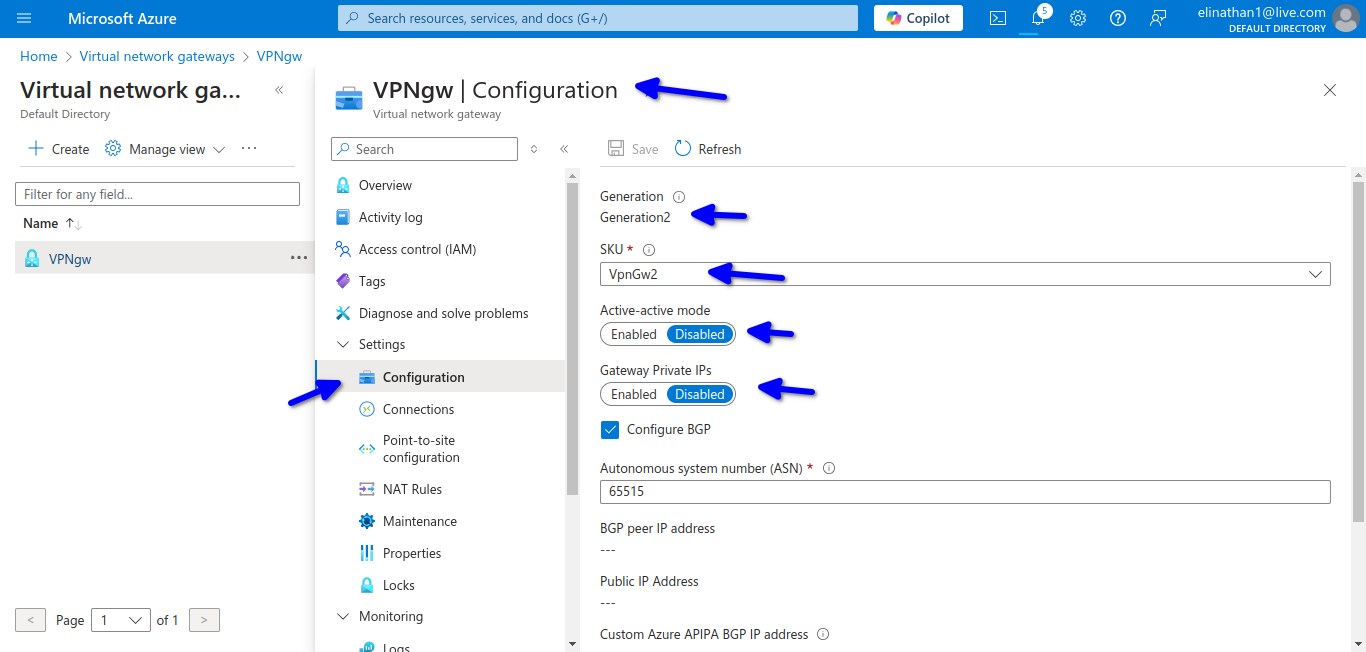
I selected the VPNgw2 Generation 2 for me to see bgp as the configuration, but I needed to enable gateway private IPs because I am using NAT from my on-premises to connect to the internet and Azure.
I don’t need the active-active cause it is a lab environment and I need to watch for the costs.
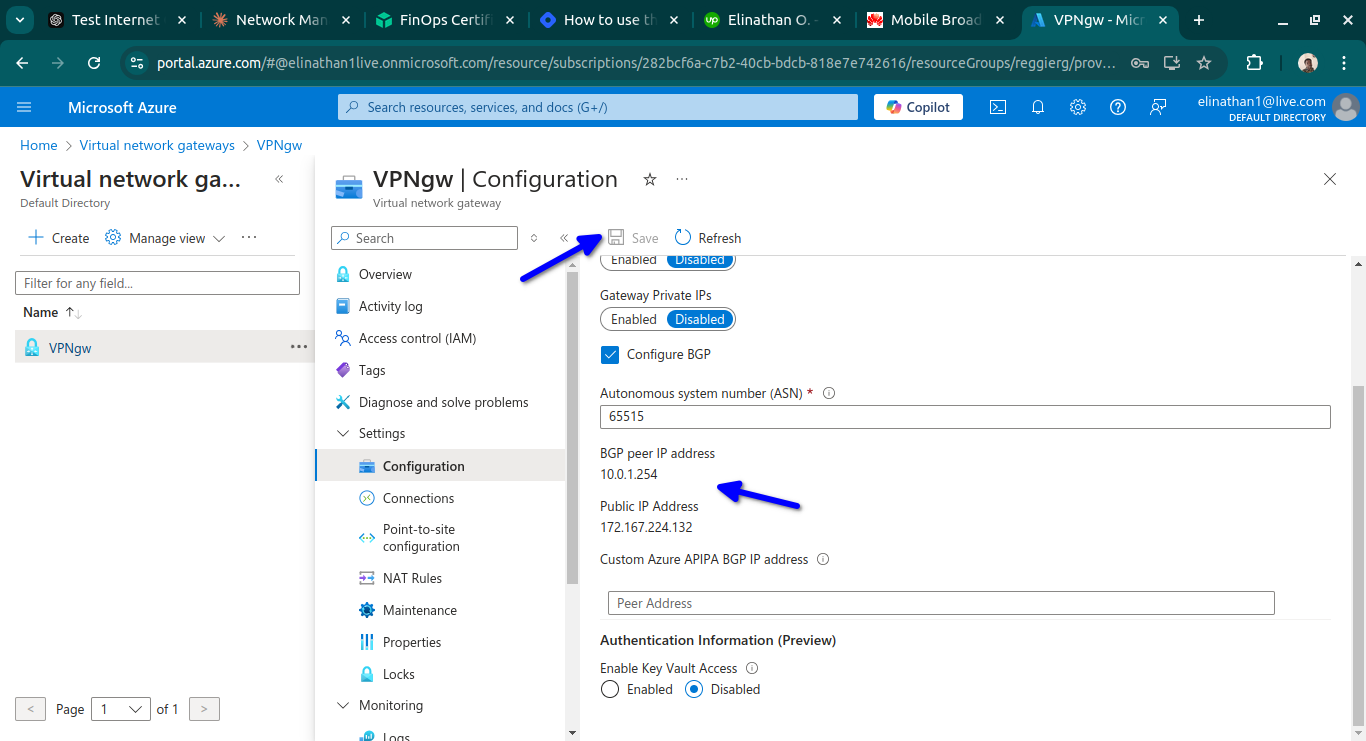
Setup Local Network Gateway
This section in Azure Cloud is where you have to configure your edge device in the on-premises network, which in my case is the router R1.
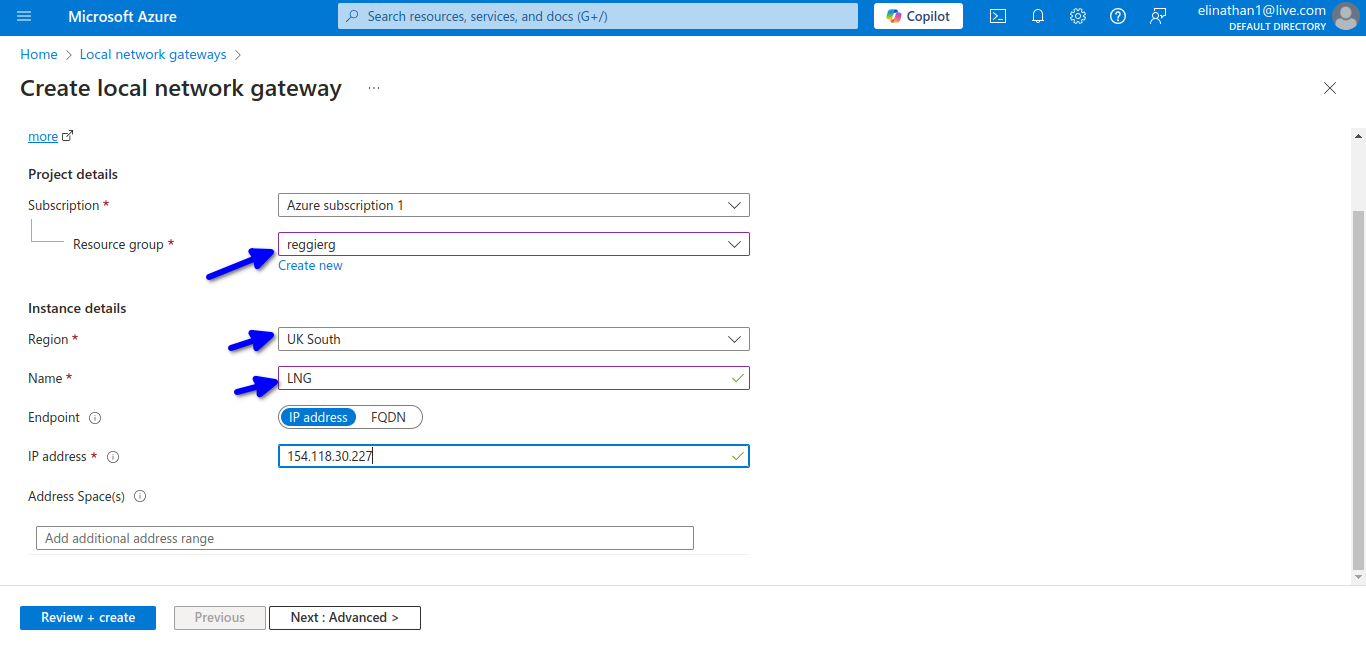
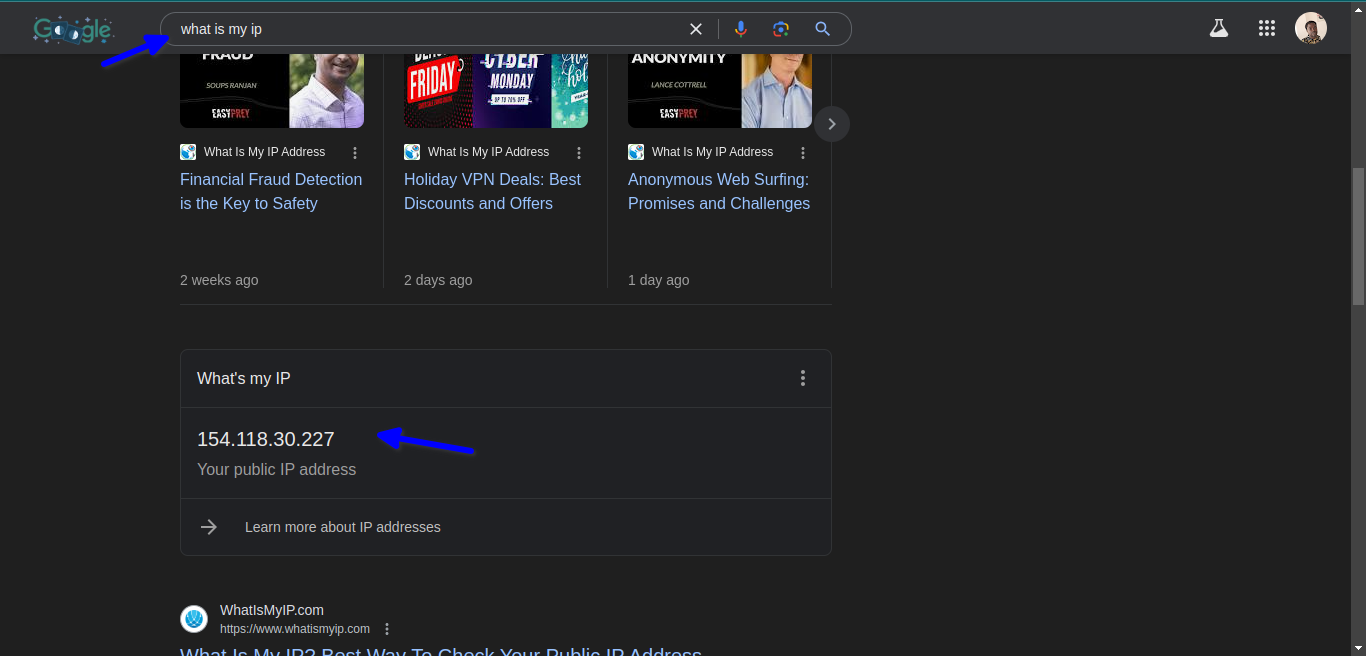
The IP address here is the public IP, which I use from my modem. I type the sentence, What is my IP in the browser?
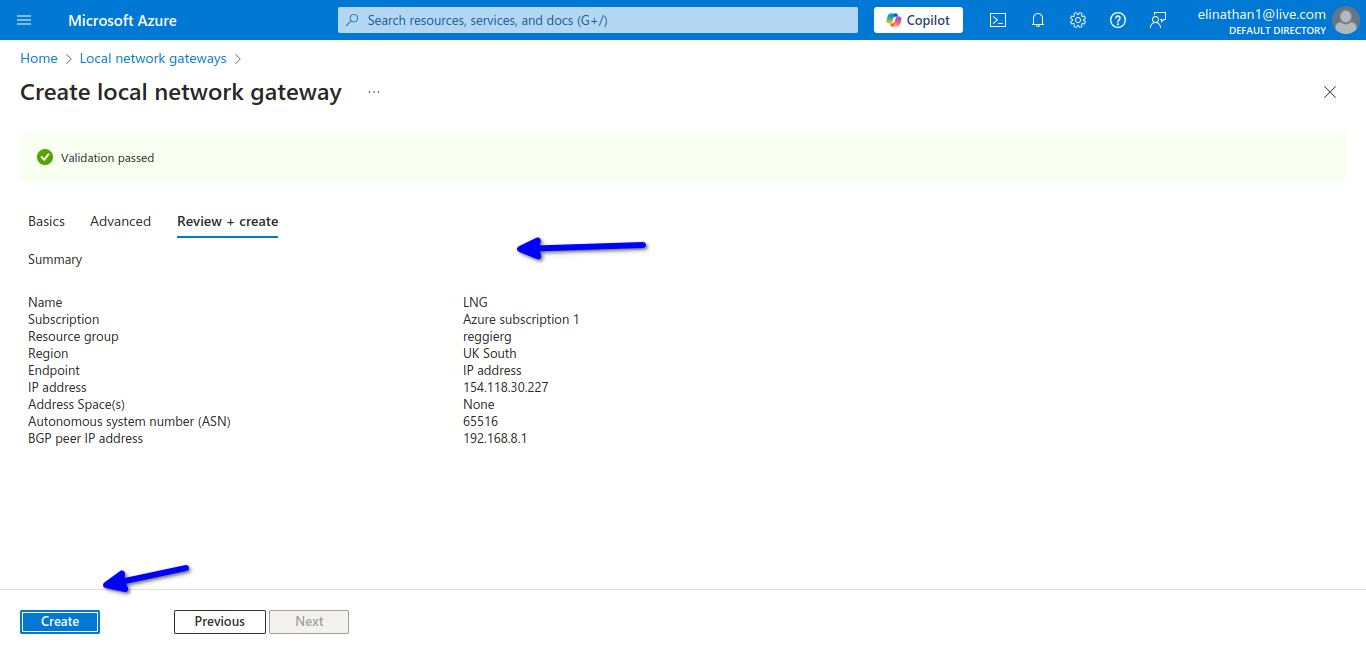
I enabled BGP here too and gave it a BGP ASN of 65516 and gave it my loopback IP address of 192.168.8.1/32 as my BGP peer IP address.
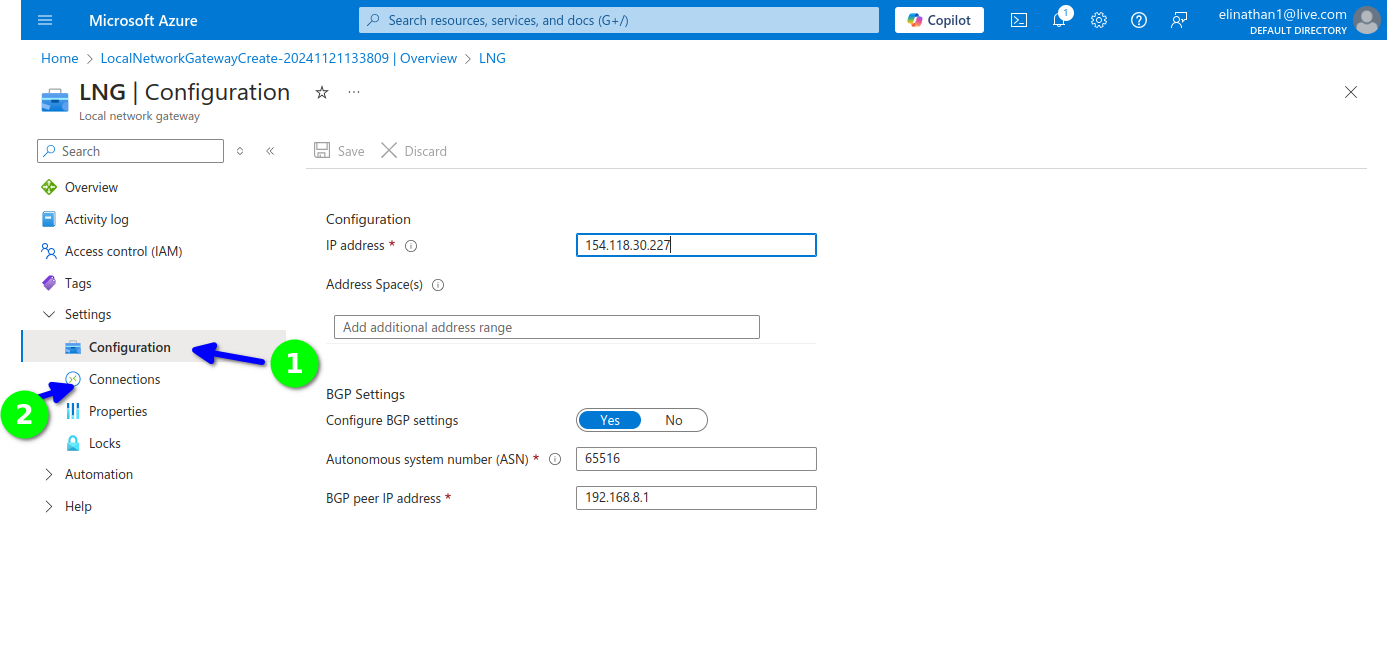
You can configure the connections here and also type connections in the search bar and configure it there, but I configured mine in the virtual network gateway.
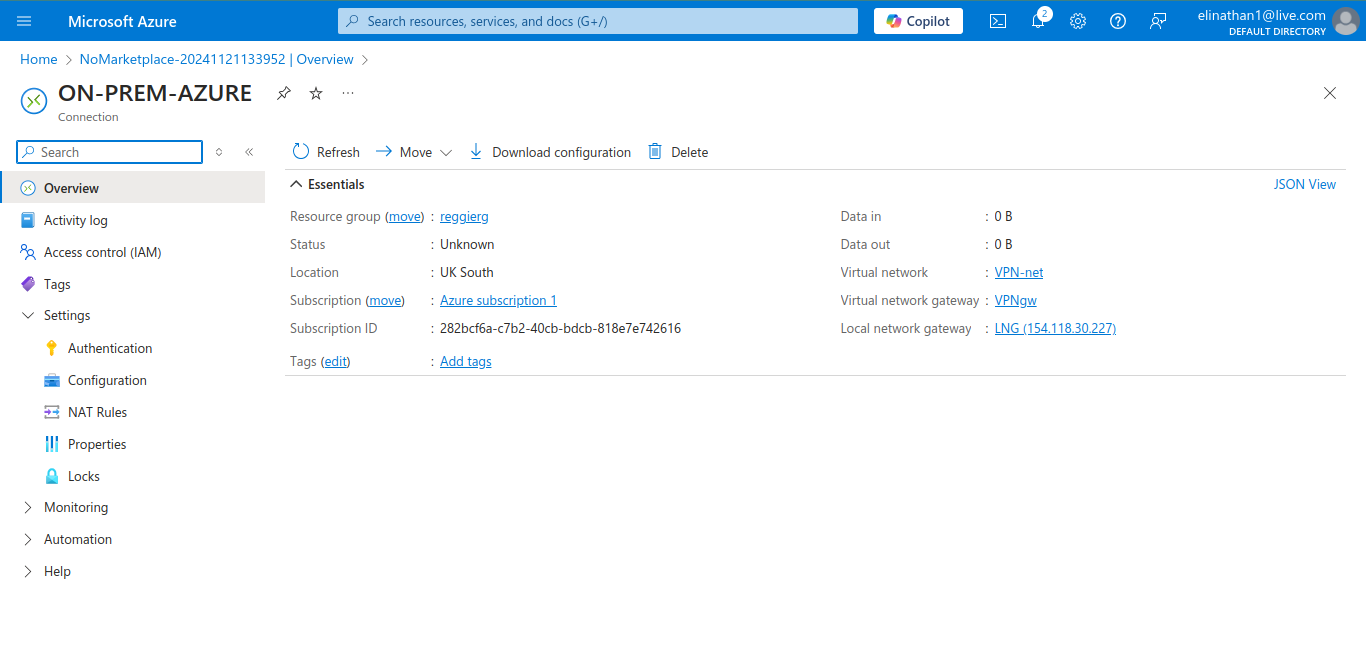
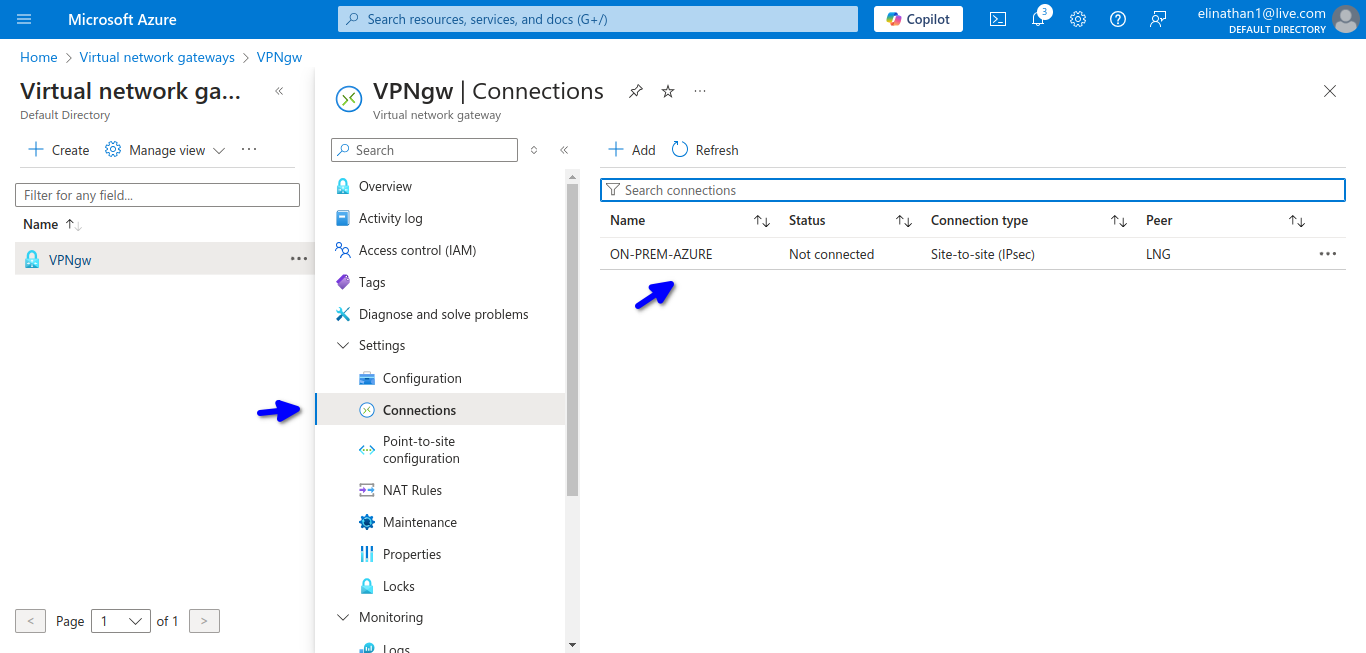
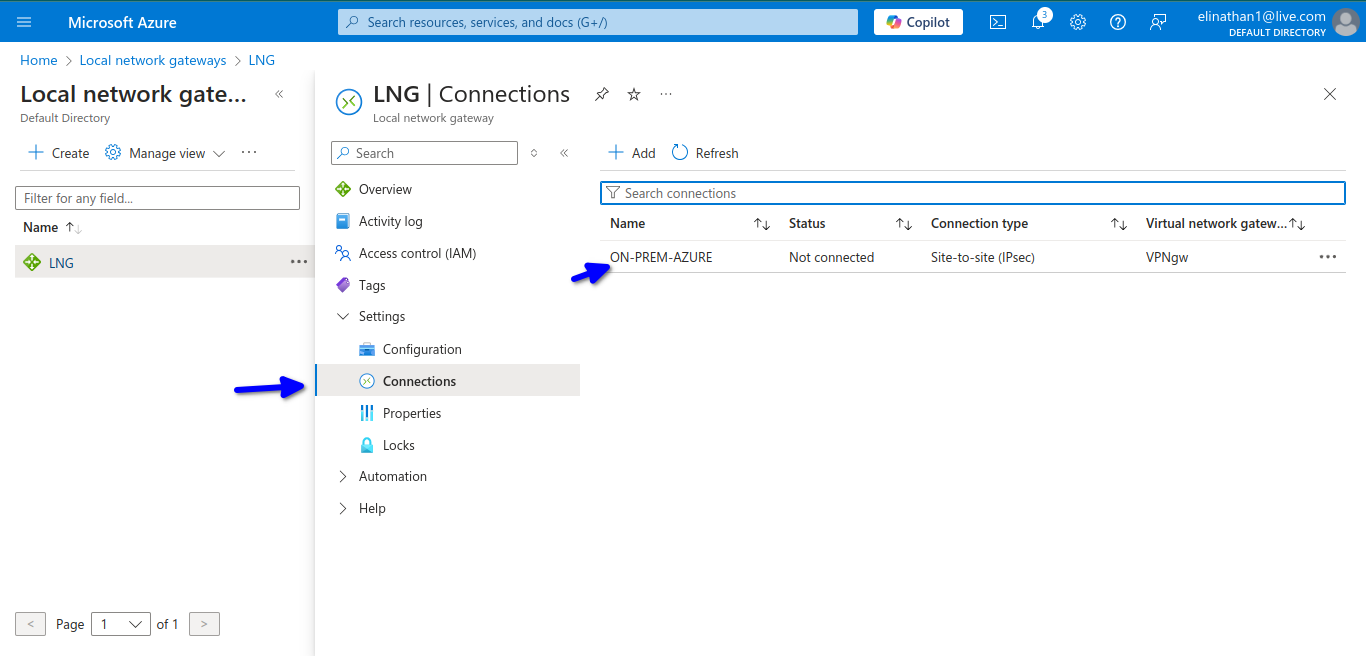
Setup Connection
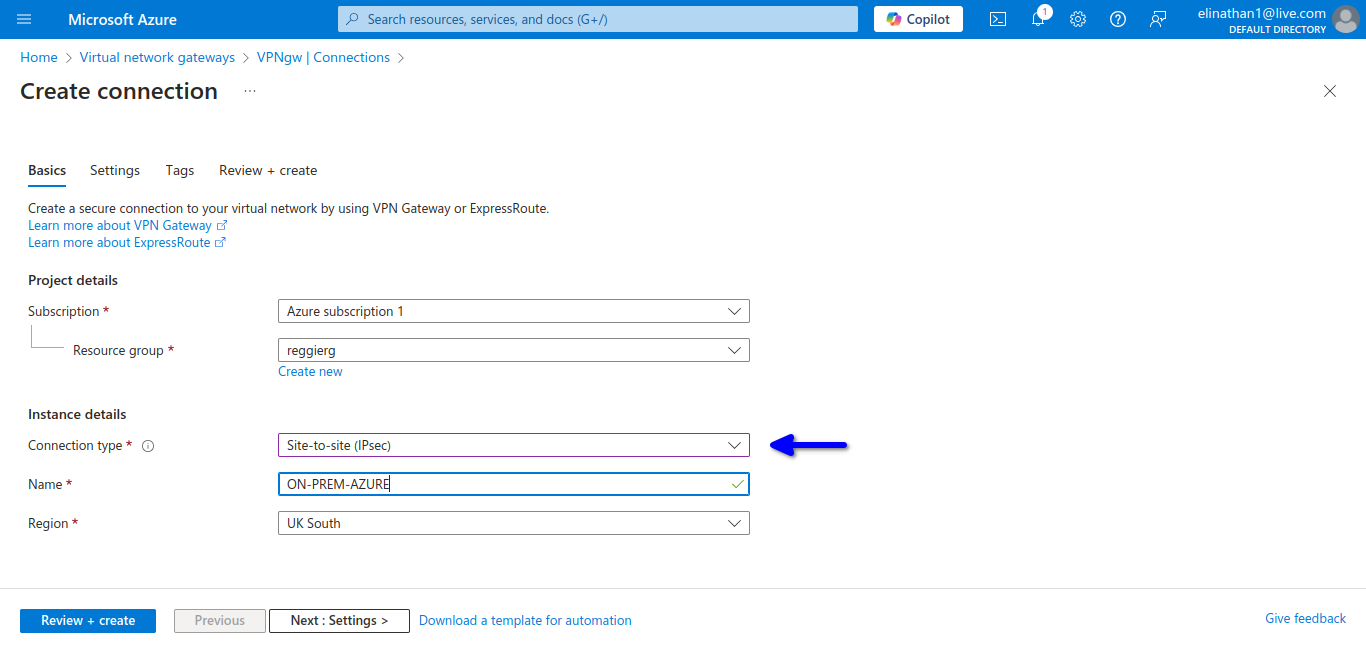
This is where you configure the connections that will connect the virtual network gateway and the local network gateway together.
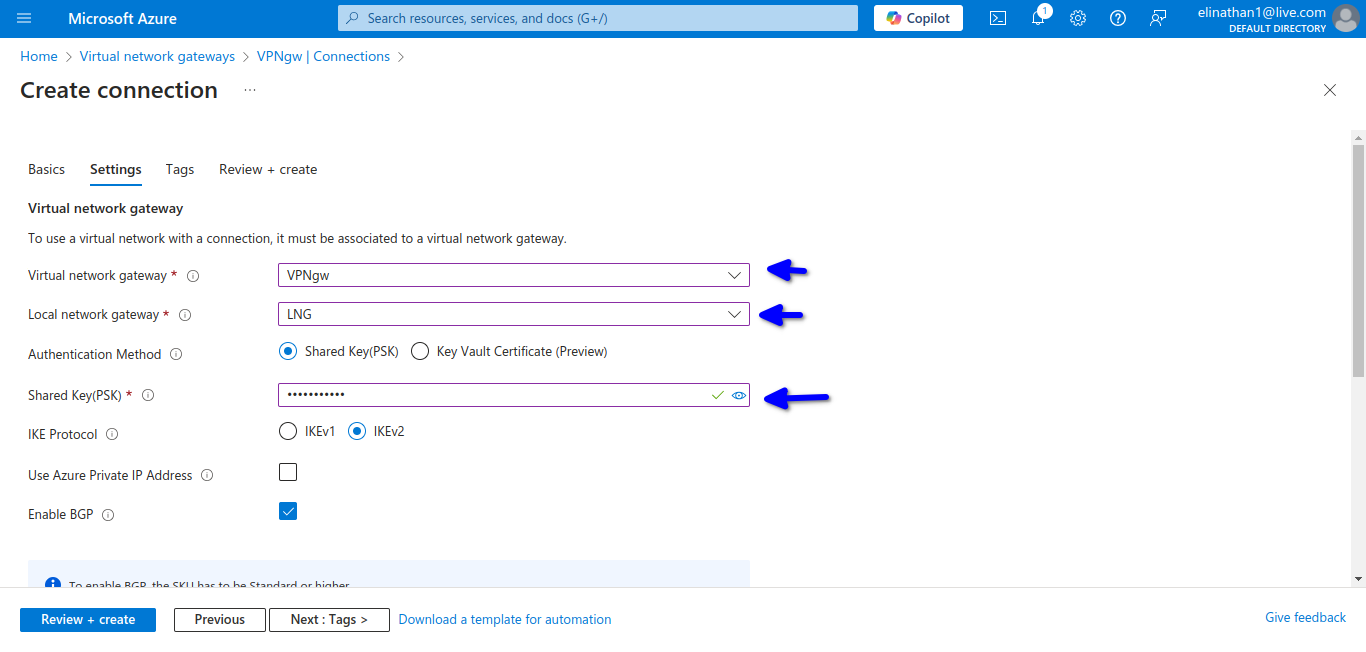
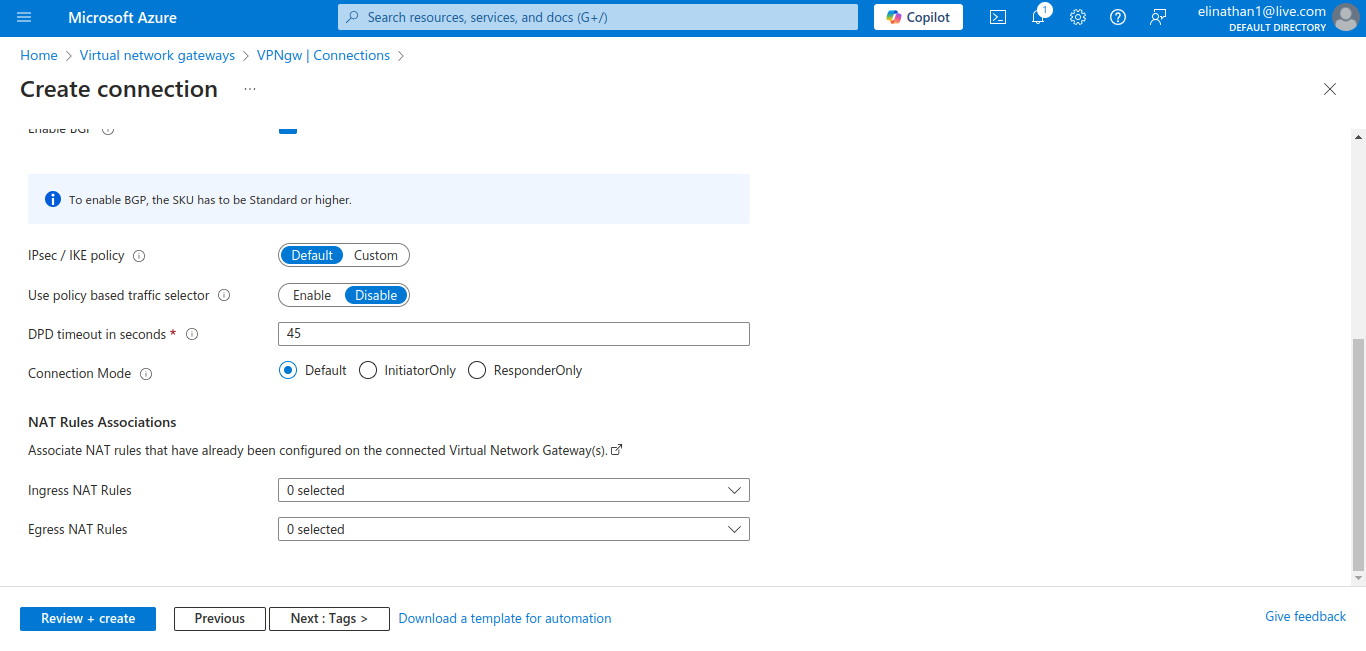
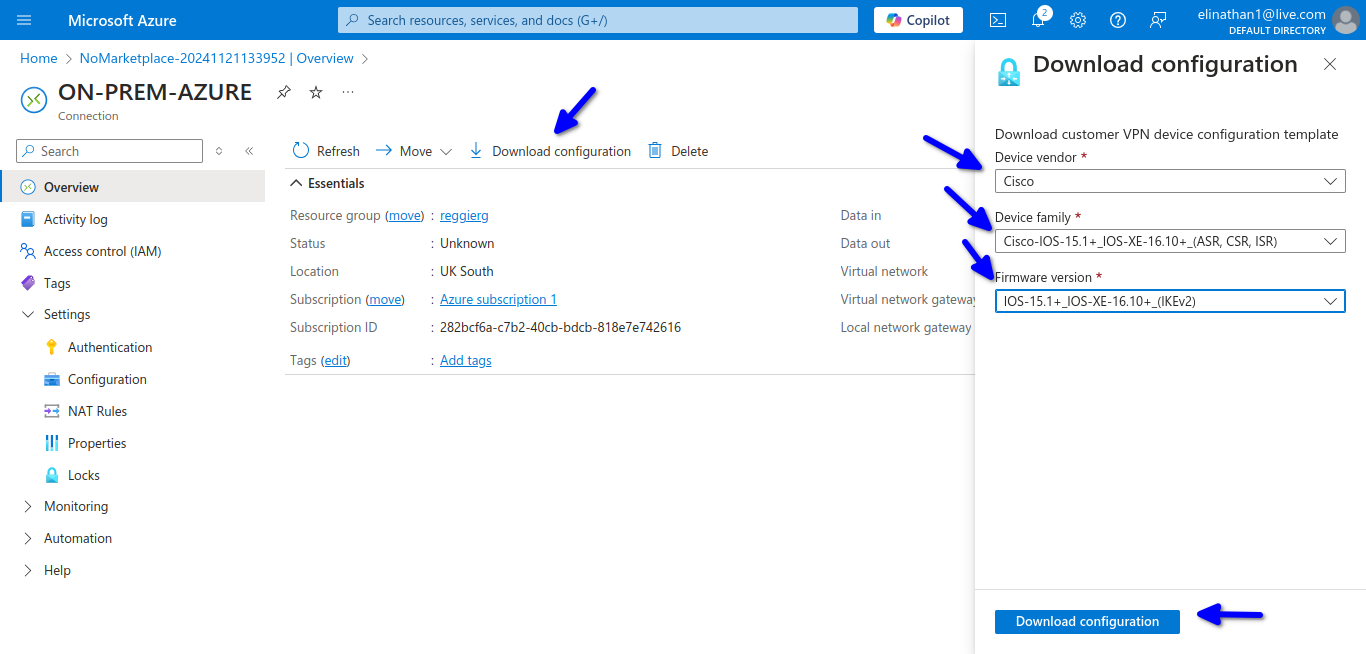
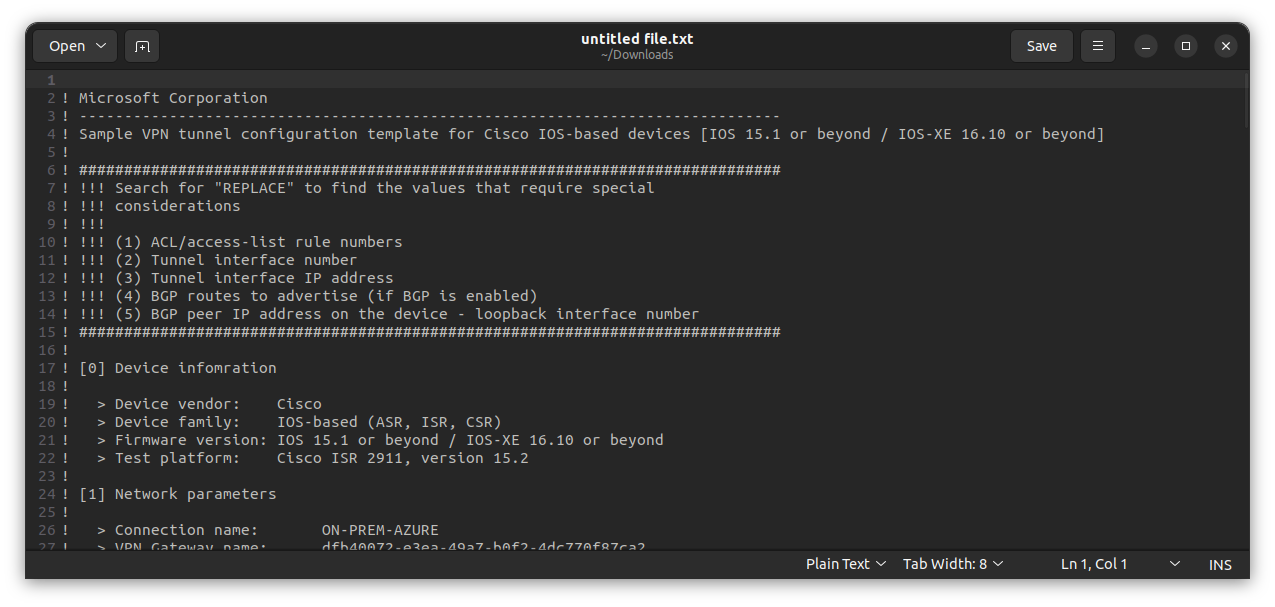
As shown in the diagram above, similar to my previous blog on site-to-site using AWS VPN, you download the configuration; however, Azure does not have as robust a pool of device configurations to choose from, which is why I used the Cisco IOS 15.1+.
On-premises edge router R1 configuration
here is a sample of the configuration
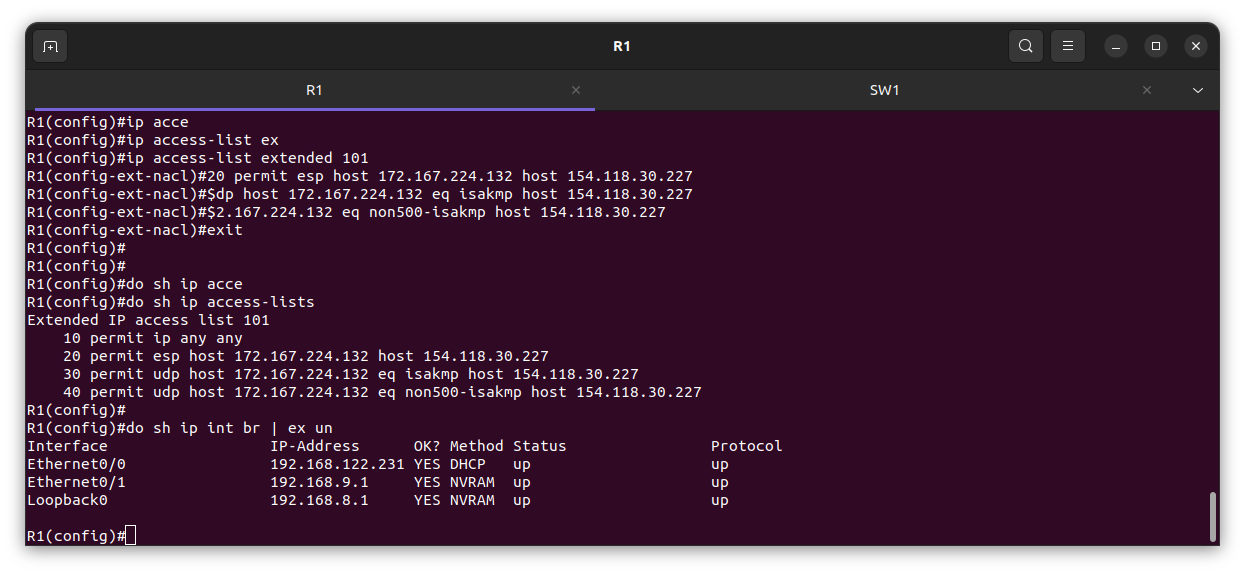
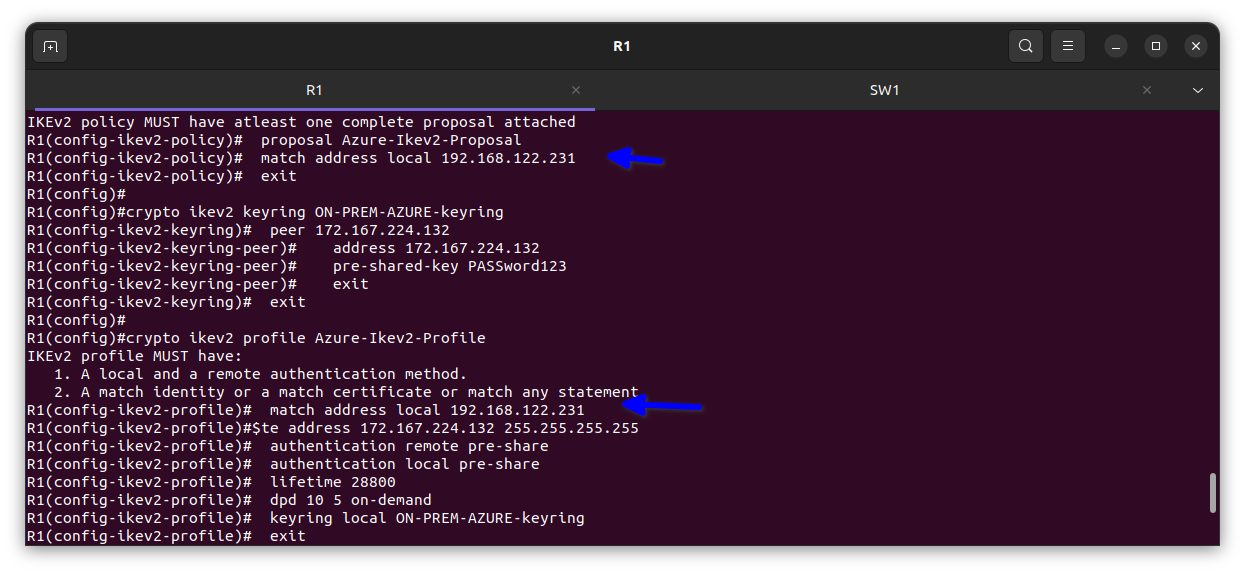
Note: Since I am using NAT to connect to the internet from on-premises and I have already enabled gateway private IP, I have to replace anywhere I see a local IP address with my interface e0/0 IP address.
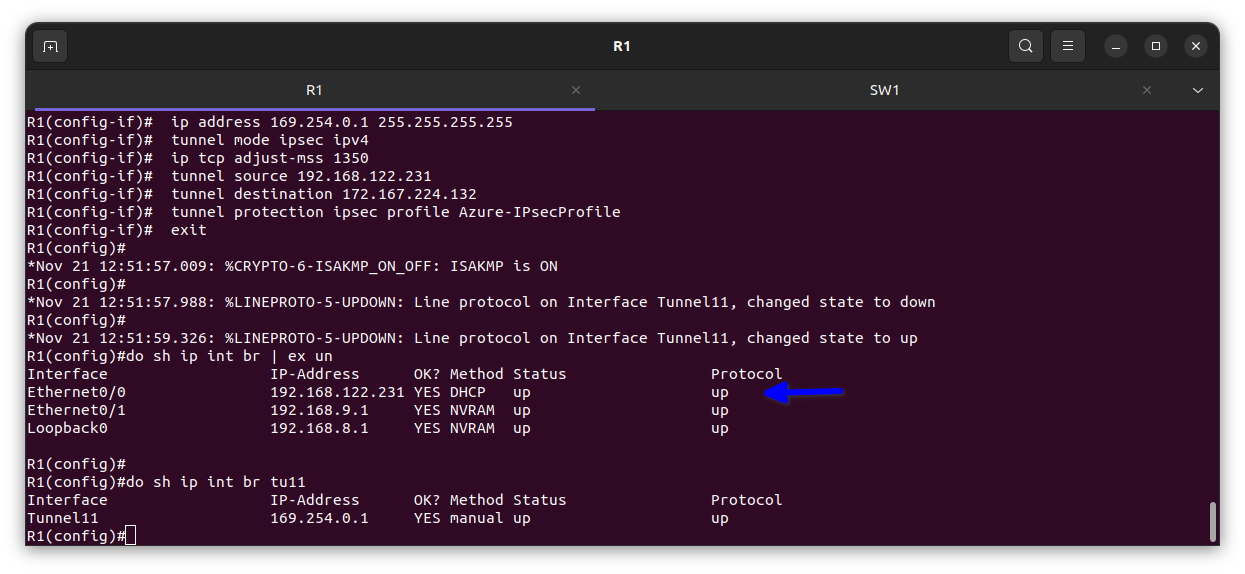
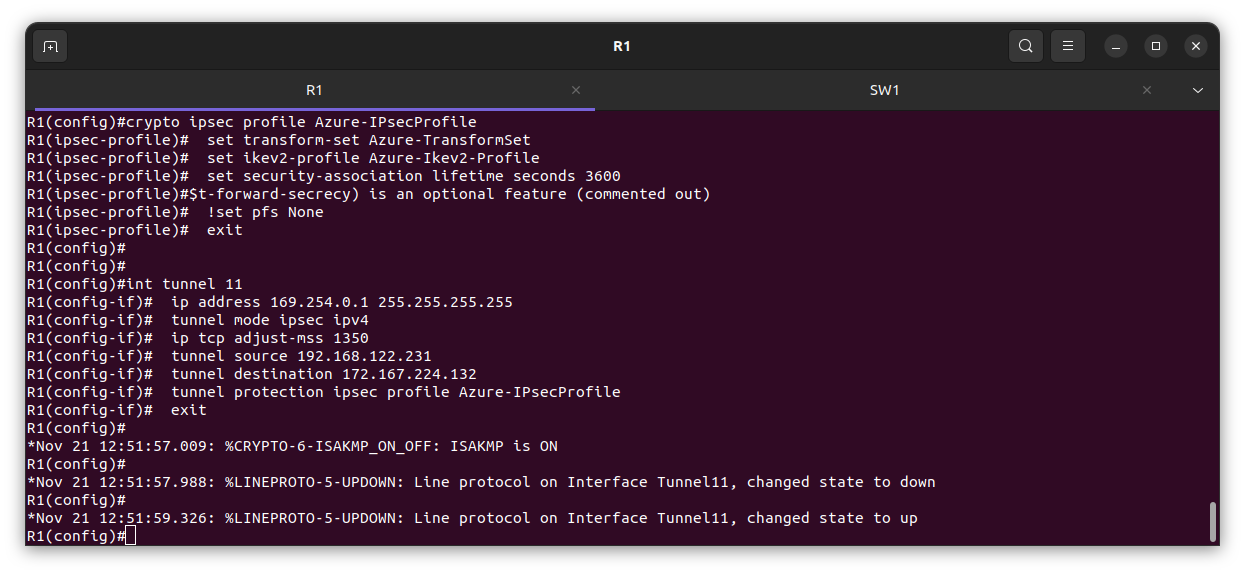
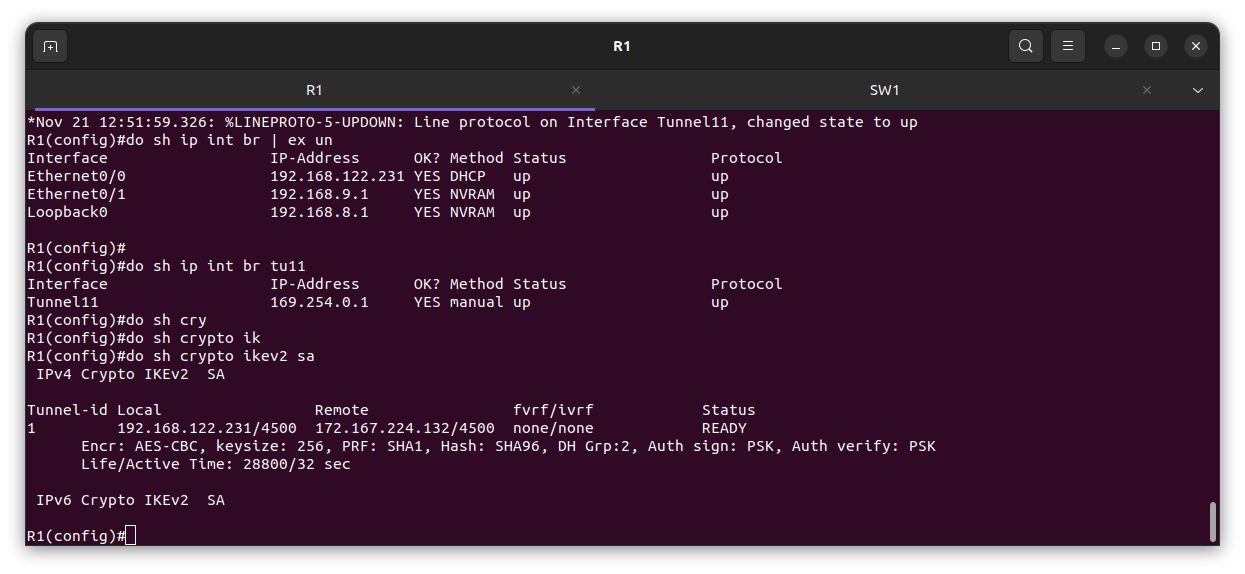
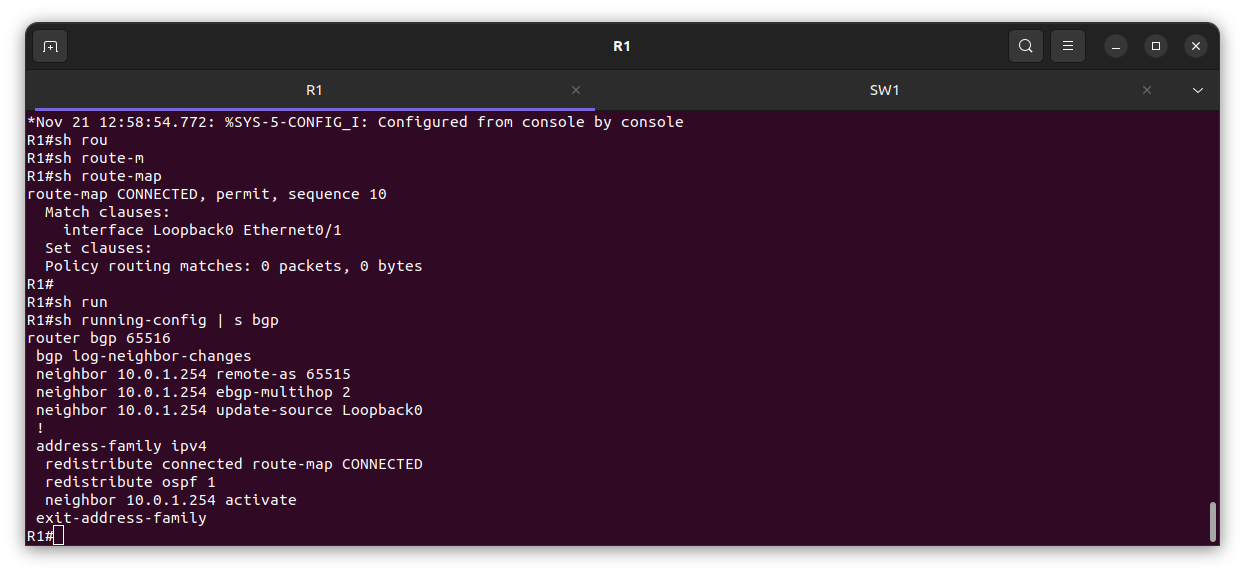
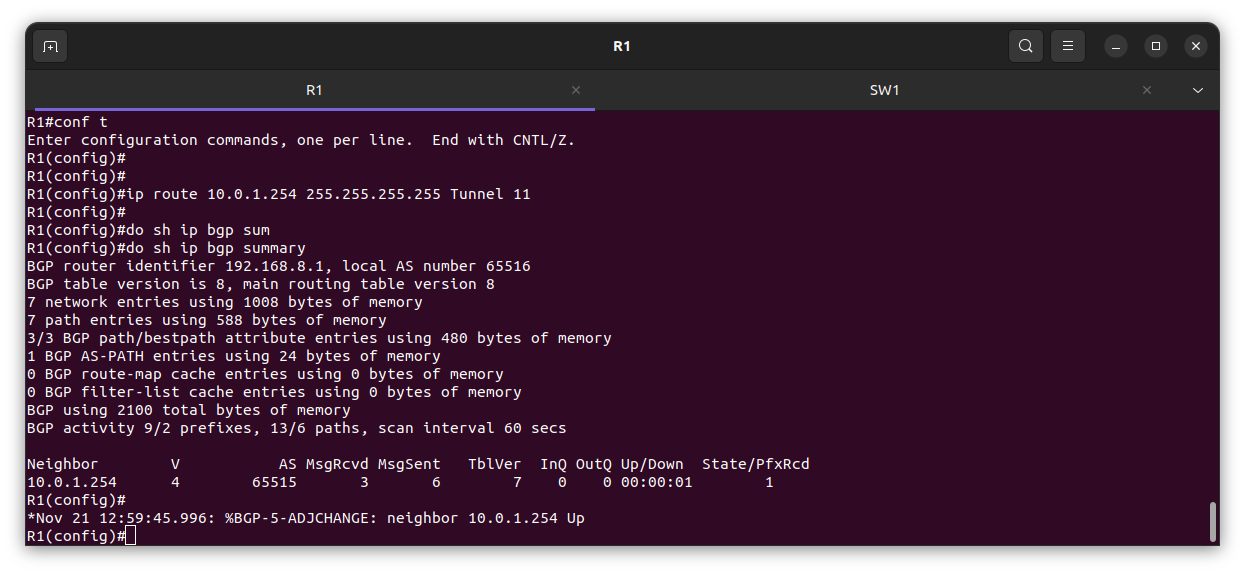
Verification
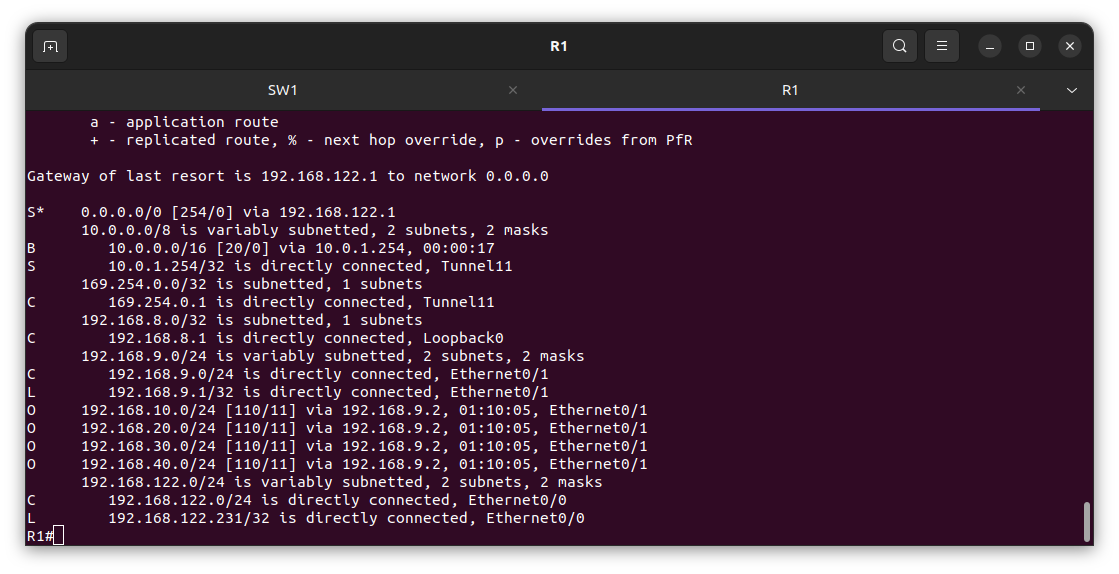
From the edge Router R1
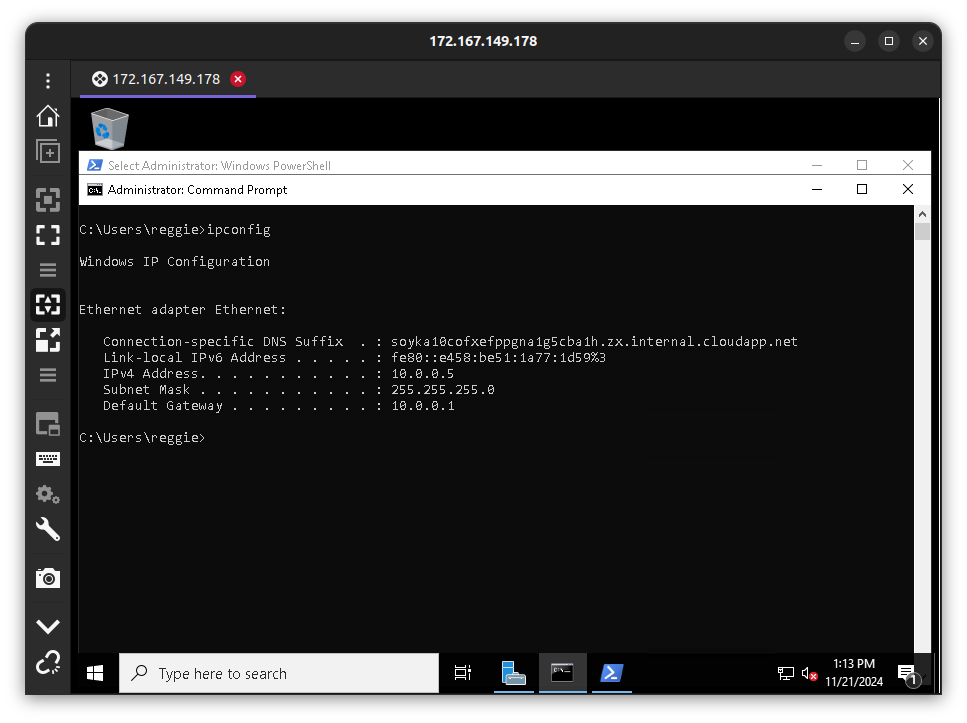
In the diagram above, the IP address of our virtual machine instance in the Azure cloud.
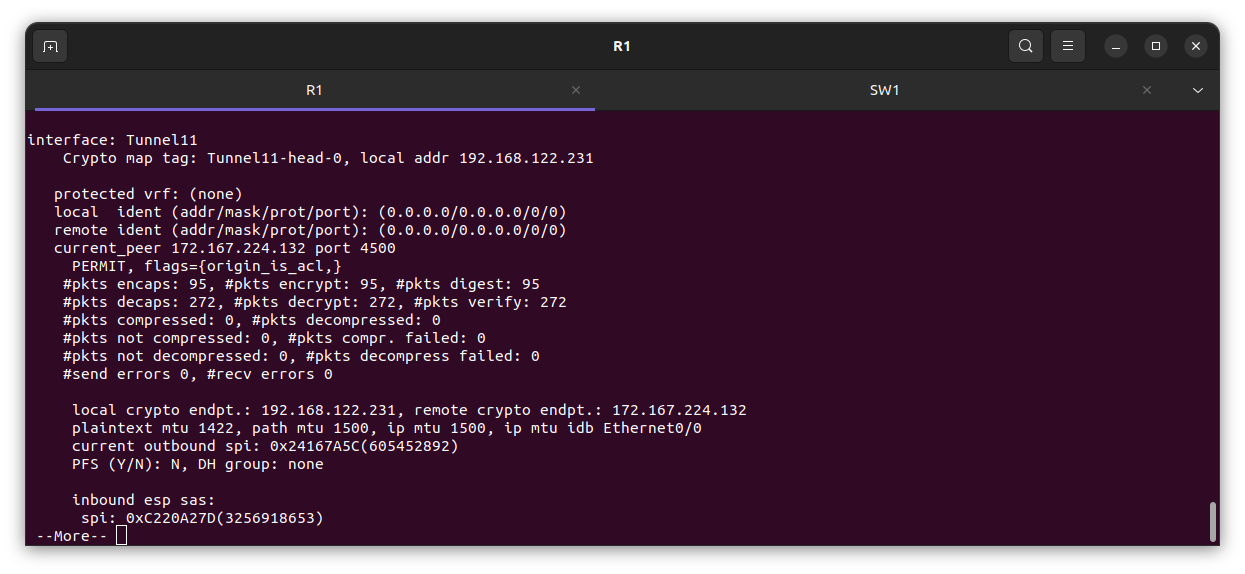
The diagram above shows the IPsec is both encrypting and decrypting, meaning traffic is passing through.
VLAN 10 Denver branch
VLAN 20 New York branch
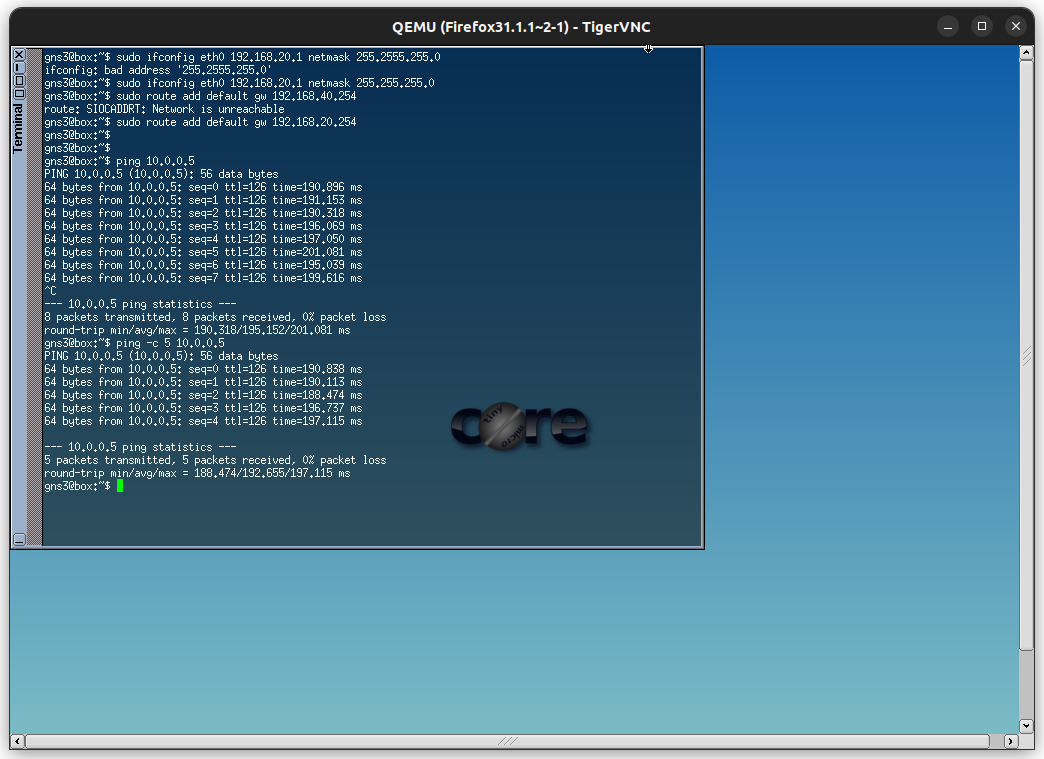
VLAN 30 Berlin branch
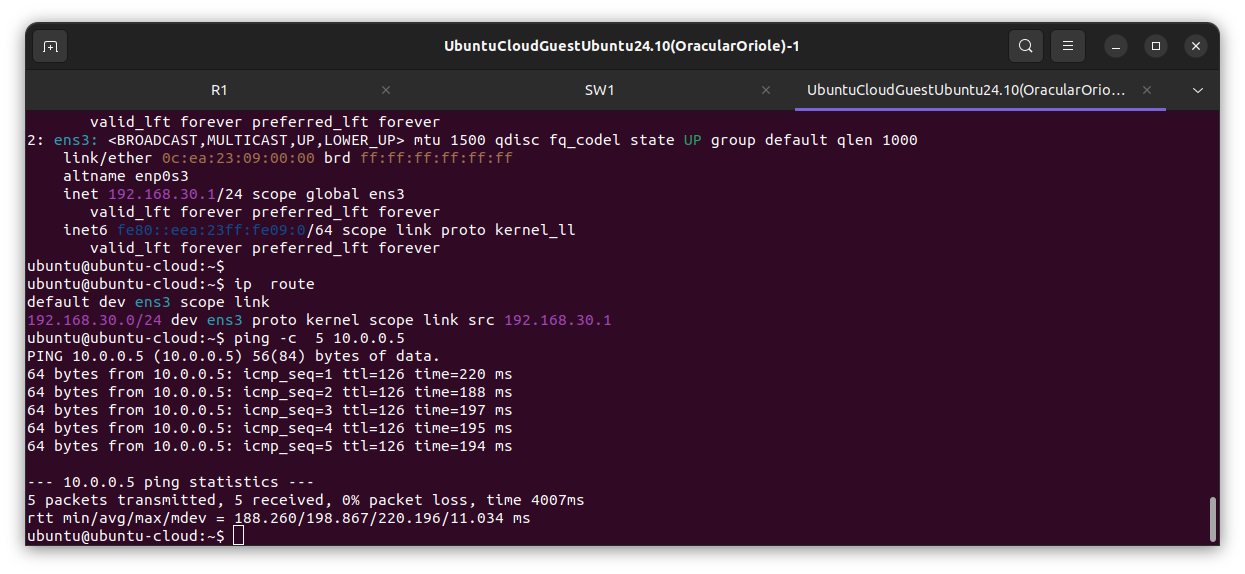
VLAN 40 Barcelona branch
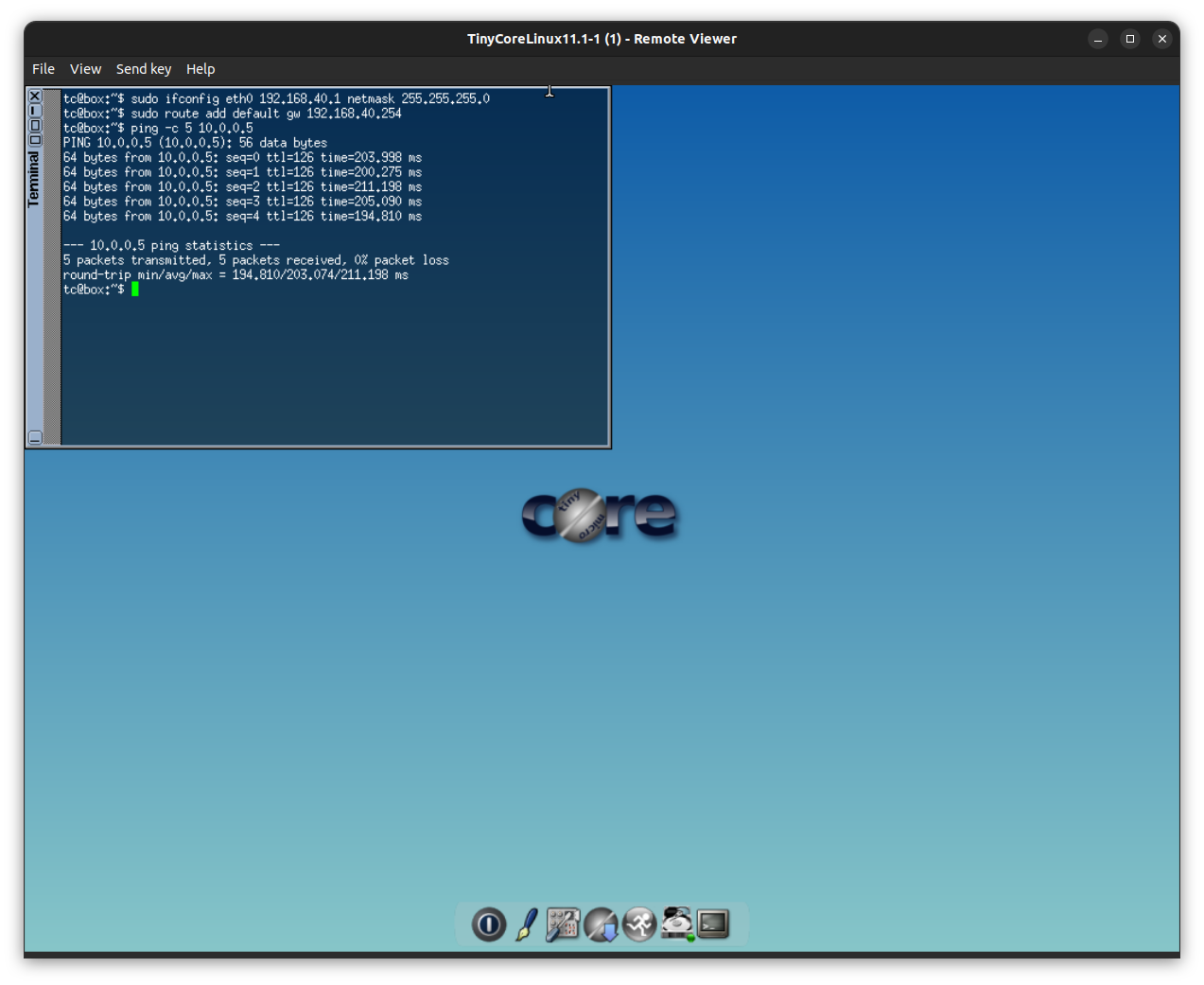
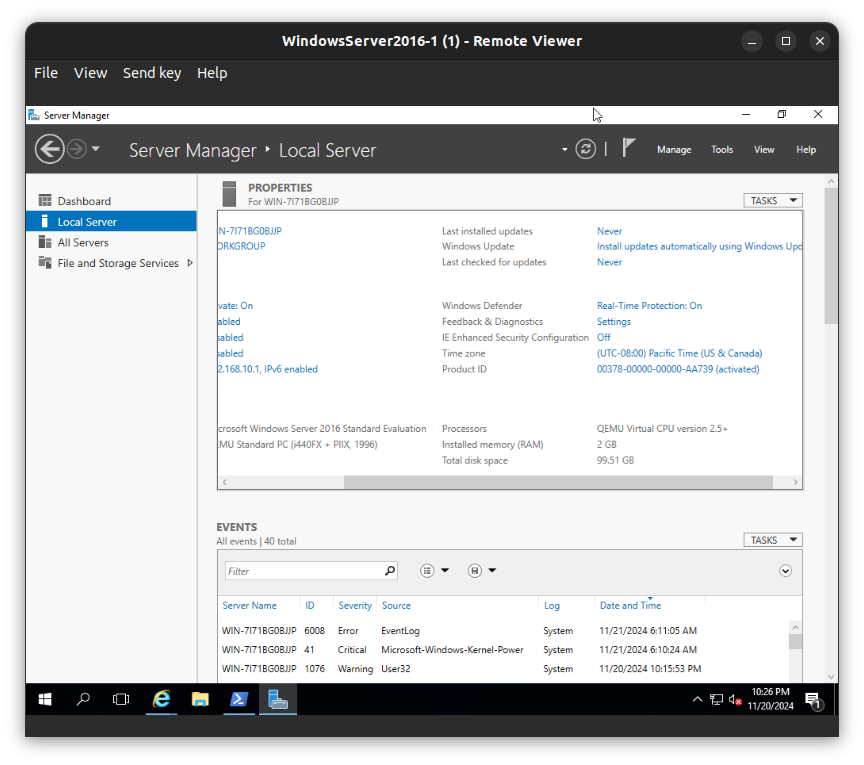
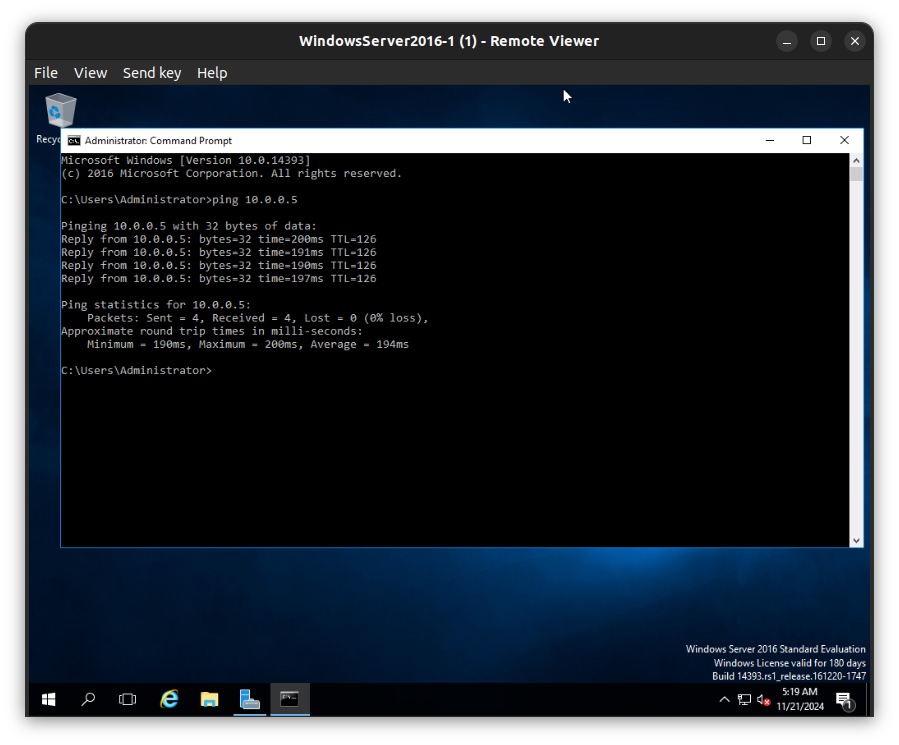
From the virtual machine Windows Server 2022 in Azure cloud
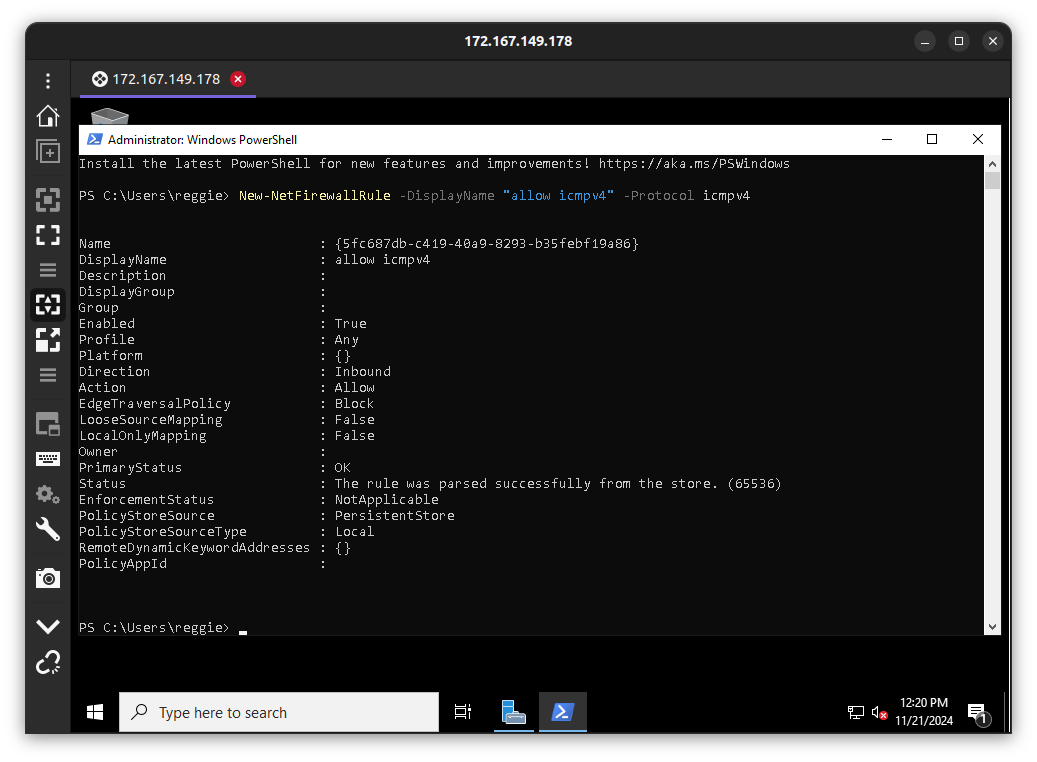
In the diagram above, I allowed icmpv4 through the server firewall in order for pings to work from the on-premises devices.
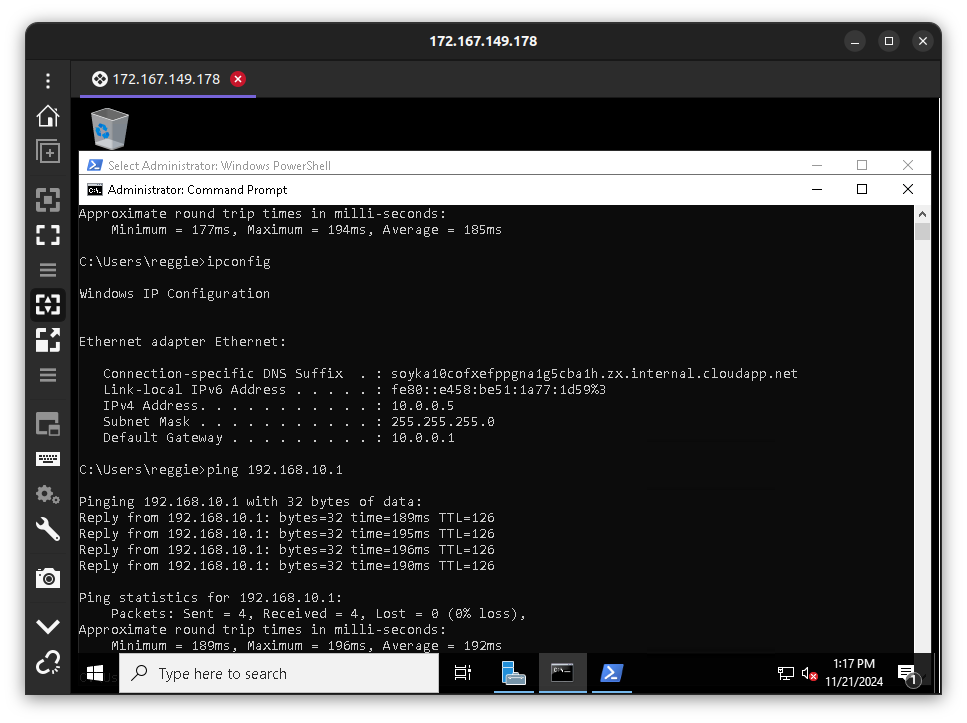
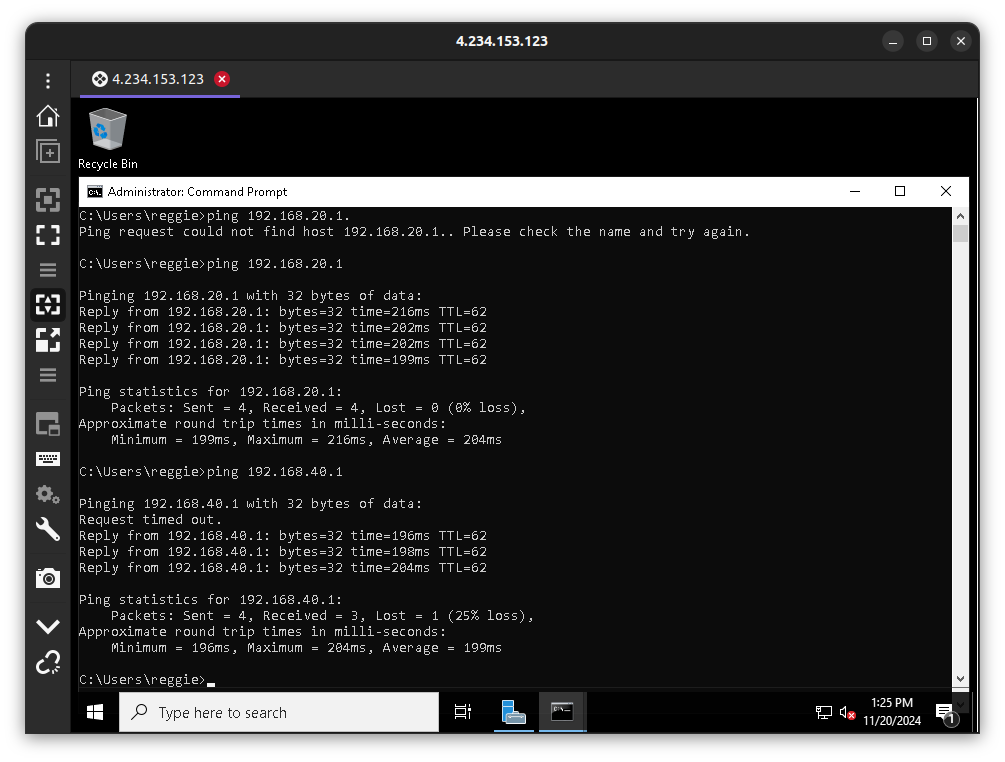
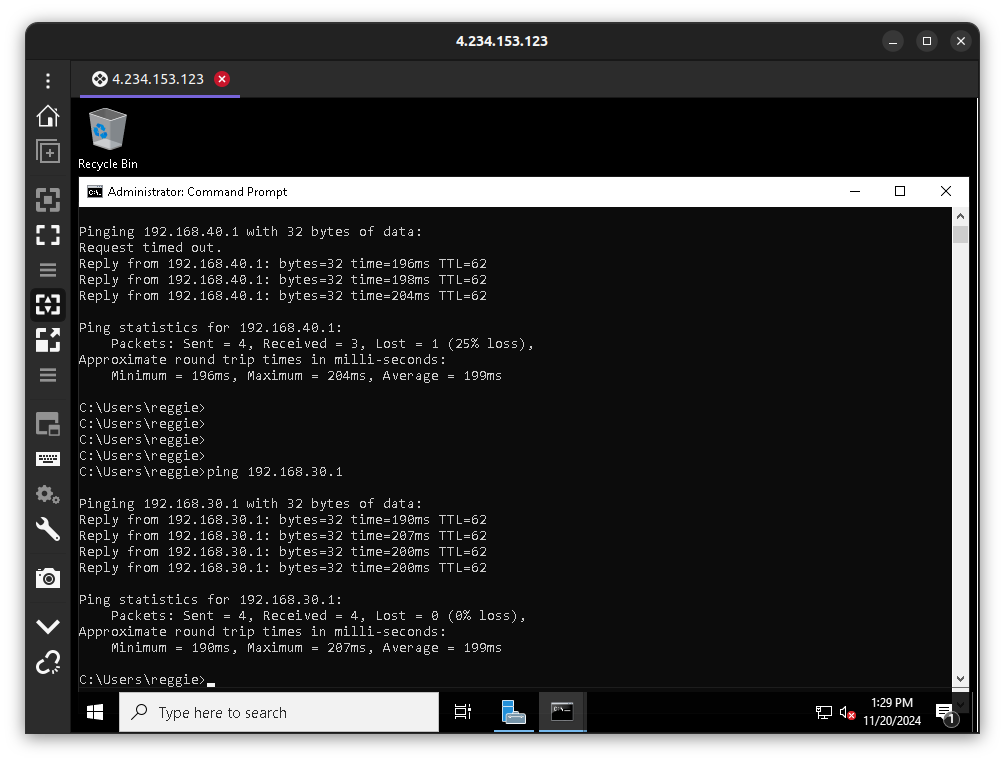
Clean up
In the Azure cloud, as soon as you are done testing, to save costs.
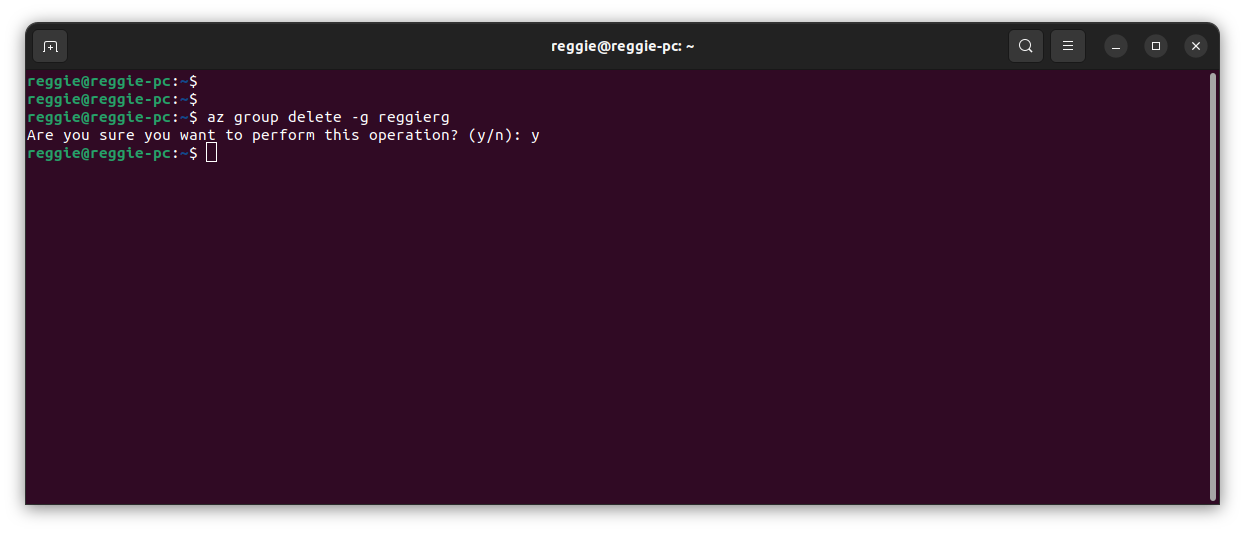
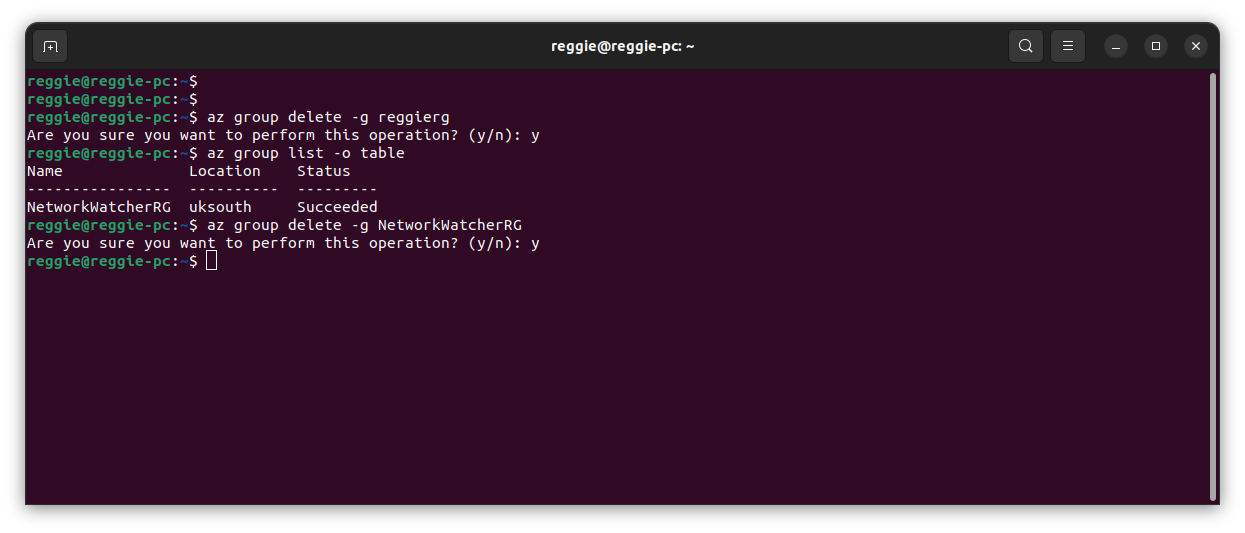
If you like it, please leave a like, subscribe, and check out my other articles as I bring more your way.
Subscribe to my newsletter
Read articles from Elinathan Olotu directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Elinathan Olotu
Elinathan Olotu
I am a Cloud Engineer with a strong foundation in multi-cloud environments, specializing in AWS and Azure with hands-on experience in Google Cloud Platform (GCP). Skilled in architecting and optimizing secure, scalable cloud infrastructures, I bring a robust background in Cisco networking to enhance connectivity and reliability. Passionate about leveraging cloud technologies to solve complex challenges, streamline operations, and drive innovation.