Discovering the Latest Features of AWS CloudFront: Enhancing Performance and Security
 Fady Nabil
Fady Nabil
🚀 Amazon CloudFront now supports VPC Origins, allowing private network resources in your AWS account to connect directly to CloudFront.
https://aws.amazon.com/about-aws/whats-new/2024/11/amazon-cloudfront-vpc-origins/
🚀 CloudFront Virtual Private Cloud (VPC) Origins: Shield your web applications from public internethttps://aws.amazon.com/blogs/networking-and-content-delivery/introducing-cloudfront-virtual-private-cloud-vpc-origins-shield-your-web-applications-from-public-internet/
Amazon CloudFront introduced CloudFront Virtual Private Cloud (VPC) Origins, a new feature that allows users to use CloudFront to deliver content from applications hosted in a VPC private subnet.
This long-awaited feature eliminates the need to make load balancers public to leverage CloudFront’s performance and caching capabilities. 🌐
🎯 The benefits?
- Enhanced Security Posture: Keep your backend resources private while still benefiting from CloudFront’s global distribution.
- Simplified Architecture: No more workarounds to protect sensitive resources.
- Improved Compliance: Aligns with many security and regulatory requirements.
- No additional costs compared to the ‘old’ setup
Steps for VPC origins in CloudFront:-
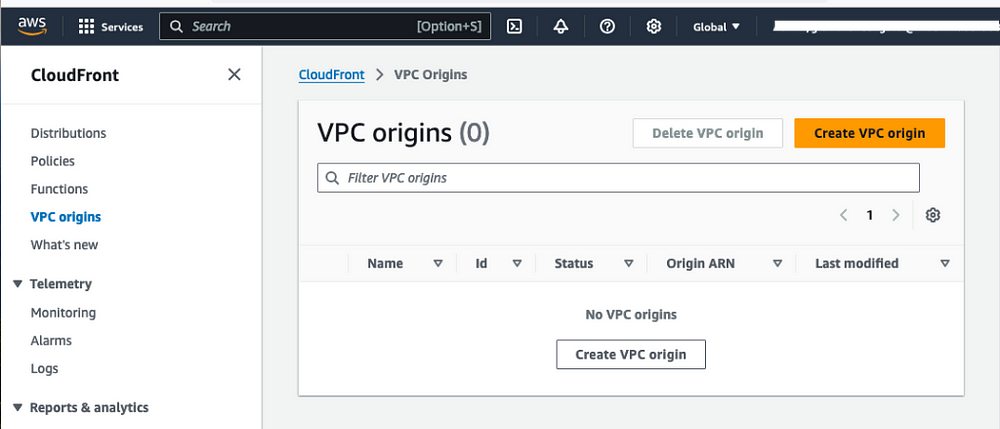
1. Create a VPC Origin for your existing public subnet application:
A. Open the CloudFront console and select VPC Origins from the left navigation, as shown in the following figure.
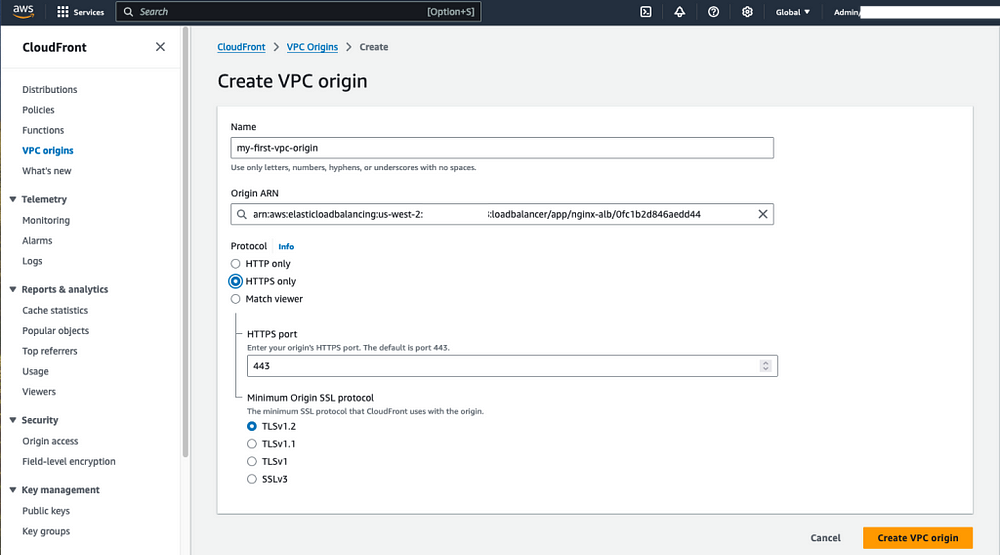
2. Use CloudFront’s continuous deployment to create a staging distribution:
A. Create a VPC Origin by selecting the ALB that we created previously.
B. Now that we have a VPC origin created and deployed, then we can use the VPC origin to create an origin within a CloudFront distribution.
C. Do that through a staging distribution to safely promote the switch to the newly created VPC origin.
D. Create a staging distribution, and add a new origin by choosing the VPC Origin created.
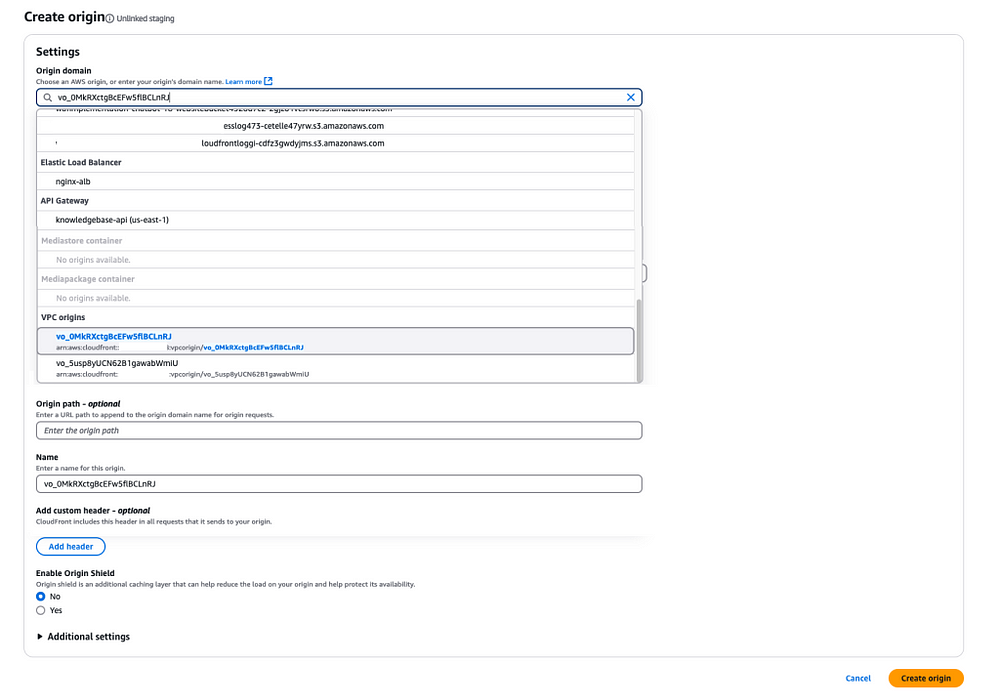
E. Update the behaviors pointing to the existing origin to use the new VPC Origin.
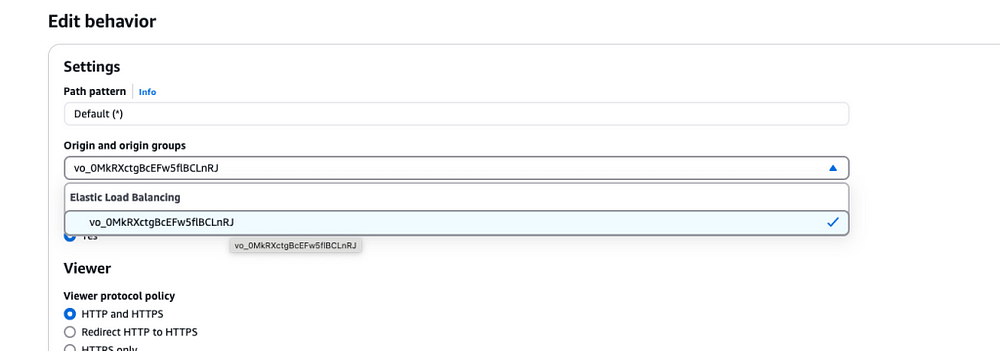
3. Test the VPC Origin in the staging distribution:
A. Make sure that the VPC Origin functions as expected.
B. This helps make sure that your VPC configuration is accurate.
4. Promote the staging distribution’s configuration to the primary distribution:
A. After confirming that the VPC Origin works correctly in the staging environment, you can promote the configuration to your production distribution.
B. Remove public access to your application.
Your application now inaccessible from the public internet, but CloudFront still has private access to it through the VPC Origin.
🚀 Amazon CloudFront VPC origins: Enhanced security and streamlined operations for your applications.
For resources such as ALBs/NLBs/EC2s, CloudFront now allows the most secure origin cloaking mechanism. You can keep these resources on a private subnet, and only CloudFront will be able to communicate with them. No additional charge.
https://aws.amazon.com/blogs/aws/introducing-amazon-cloudfront-vpc-origins-enhanced-security-and-streamlined-operations-for-your-applications/
🚀 Amazon CloudFront now supports additional log formats and destinations for access logs.
CloudFront’s standard logging got some love. You can now select the field you want to log, select additional destinations such as CloudWatch and Amazon Data Firehose, and choose new formats such as JSON and Parquet.
Here’s what’s new:
✅ Direct log delivery to CloudWatch Logs and DataFirehose
✅ Expanded log output formats, including Parquet and JSON
✅ Customizable S3 prefixes and partitioning for S3 log delivery
✅ Selectable log fields for tailored insights
✅ Log delivery to S3 buckets in opt-in AWS regions
https://aws.amazon.com/about-aws/whats-new/2024/11/amazon-cloudfront-log-formats-destinations-access/
🚀 Using CloudFront Functions, you can now route requests to different origins. Couple of KeyValueStore, it’s a powerful capability to implement global traffic routing with minimal cost.
https://aws.amazon.com/about-aws/whats-new/2024/11/amazon-cloudfront-origin-modifications-cloudfront-functions/
🚀 CloudFront supports another API communication protocol, gRPC, i addition to WebSockets and HTTP (REST, graphQL, etc..). gRPC is a byte efficient protocol based on Google’s protobuf. No additional charge.
https://aws.amazon.com/blogs/aws/amazon-cloudfront-now-accepts-your-applications-grpc-calls/
🚀 CloudFront allows anycast routing with static IP addresses, opening up new use cases such as Zero rating agreements or allow listing IP addresses on firewalls. It has additional charges and currently it requires ticket to support, to progressively ramp up customers to this feature.
https://aws.amazon.com/blogs/networking-and-content-delivery/zero-rating-and-ip-address-management-made-easy-cloudfronts-new-anycast-static-ips-explained/
🚀 When running live video streaming workload, you can now implement better resiliency using Media Quality-Aware Resiliency. It catches grey failures (e.g. black screen or bad video quality) on a MediaPackage endpoint to failover to another MediaPackage endpoint with better quality score.
https://aws.amazon.com/about-aws/whats-new/2024/11/aws-announces-media-quality-aware-resiliency-live-streaming/
#aws #awscommunitybuilder #awscommunitybuilders #cloudfront #aws_cloudfront #cdn #security #waf #aws_waf
Subscribe to my newsletter
Read articles from Fady Nabil directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Fady Nabil
Fady Nabil
I am an Front End Web Developer and chatbots creator from Egypt who likes Software Engineer and UI/UX studies. I enjoy reading about Entreprenuership, Innovation, product manage, Scrum, and agile. I like to play around with Figma, Adobe XD and build tools/ideas to help me during get things done quickly.