IAM Service in AWS
 Harshit Sahu
Harshit Sahu
AWS Identity and Access Management is a web service that helps you securely, control access to AWS resources. You use IAM to control who is authenticated (signed-in) and authorized (has permission).
Important Points -
When you first create an AWS account, you begin with a single sign-in identity that has completely access to all AWS services and resources in the account.
This identity is called the AWS account “Root User" and is accessed by signing-in with the email address and password that you used to create the account.
AWS strongly recommends that you do not use the root user for your everyday task, even the administrative ones.
Use other IAM user account to manage the administrative task of your account and securely lock away the root user credentials and use them to perform only a few account and server management tasks.
IAM user limit is
5000per AWS account. You can add up to 10 users at a time.You are also limited to 300 groups per account in AWS.
Default limits of managed policies attached to an IAM role and IAM user is 10.
IAM user can be members of 10 groups max.
We can assign two access keys maximum to an IAM user.
Features
Shared access to your AWS account
You can grant other people permission to administrator and use resource in your AWS account without having share your access credentials (password or access keys).
Granular Permission
You can grant different permissions to different people for different need and resource allocation.
For instance, you can allow some users complete access to EC2, S3, DynamoDB, Redshift. While for others, you can allow read only access to just some S3 buckets, or permission to administrator just some EC2 instances or to access your billing information bur nothing else.
Secure Access
Secure access to AWS resource for applications that run on amazon EC2.
You can use IAM features to securely give application that run on EC2 instances the credentials that they need in order to access other AWS resources. Example S3 buckets and RDS or DynamoDB databases.
Multifactor Authentication (MFA)
You can add two-factor authentication to your account and to individual users for extra level security. You can use physical hardware or virtual MFA (eg- google authenticator).
Identity Federation
You can allow users who already have passwords elsewhere. For example, in your corporate network or with an internet identity provider to get temporary access to your AWS account.
Note- Federation means allow third-party application for login or creating accounts.
Identity information for assurance
If you use AWS CloudTrail, you receive log records that include information about these who made request for resources in your account. That information is based on IAM identities.
PCI-DSS Compliance
IAM supports the processing, storage and transmission of credit card by a merchant or service provider and has been validated as being compliant with payment card industries (PCI), Data security standard (DSS).
Eventually Consistent
If a request to change some data is successful, then change is committed and safely stored. However, the change must be replicated across IAM, which can take some time.
IAM achieves high availability by replicating data across multiple servers within AWS data centre around the world.
IAM Terms

Principal: - A principal is a person or application that can make a request for an action or operation on an AWS account.
Request: - When a principal tries to use the AWS management console, the AWS API, or the AWS Console CLI that principal send a request to AWS.
Authentication: - A principal sending a request must be authenticated (signed to AWS) to send a request to AWS.
Authorization: - To authorize request, IAM uses value from the request context to check for matching policies and determine whether to allow or deny the request.
Actions: - Actions are defined by a service and are the things that you can do to a resource, such as viewing, creating, editing and deleting that resource.
Resource: - A resource is an entity that exist within a service.
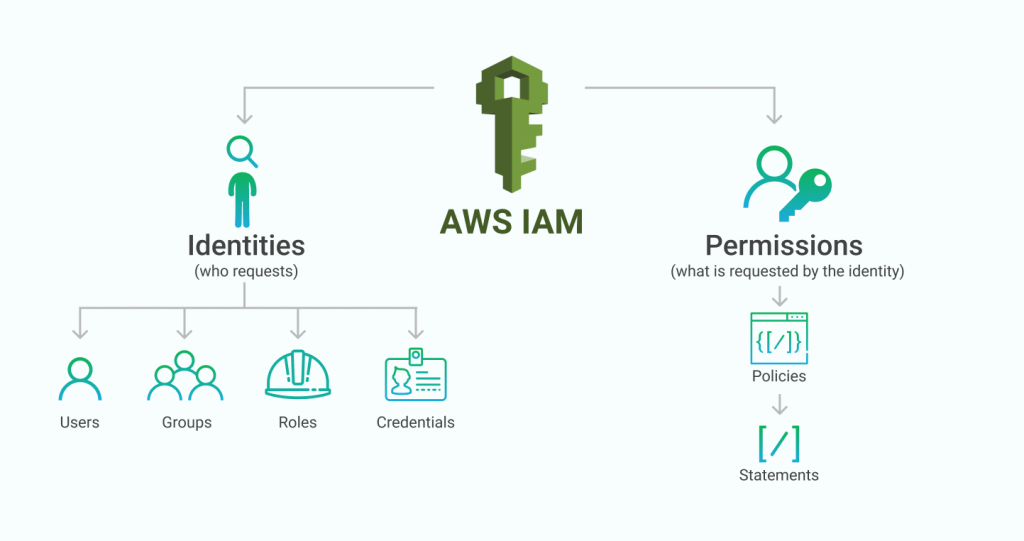
Components of IAM
Users: IAM users represent individual people or entities (such as applications or services) that interact with your AWS resources. Each user has a unique name and security credentials (password or access keys) used for authentication and access control.
Groups: IAM groups are collections of users with similar access requirements. Instead of managing permissions for each user individually, you can assign permissions to groups, making it easier to manage access control. Users can be added or removed from groups as needed.
Roles: IAM roles are used to grant temporary access to AWS resources. Roles are typically used by applications or services that need to access AWS resources on behalf of users or other services. Roles have associated policies that define the permissions and actions allowed for the role.
Policies: IAM policies are JSON documents that define permissions. Policies specify the actions that can be performed on AWS resources and the resources to which the actions apply. Policies can be attached to users, groups, or roles to control access. IAM provides both AWS managed policies (predefined policies maintained by AWS) and customer managed policies (policies created and managed by you).
Interview Questions
Q: What are AWS IAM, and why is it important?
A: AWS IAM (Identity and Access Management) is a service provided by Amazon Web Services that helps you control access to your AWS resources. It allows you to manage user identities, permissions, and policies. IAM is important because it enhances security by ensuring that only authorized individuals or entities have access to your AWS resources, helping you enforce the principle of least privilege and maintain a secure environment.
Q: What is the difference between IAM users and IAM roles?
A: IAM users represent individual people or entities that need access to your AWS resources. They have their own credentials and are typically associated with long-term access. On the other hand, IAM roles are used to grant temporary access to AWS resources, usually for applications or services. Roles have associated policies and can be assumed by trusted entities to access resources securely.
Q: What are IAM policies, and how do they work?
A: IAM policies are JSON documents that define permissions. They specify what actions are allowed or denied on AWS resources and can be attached to IAM users, groups, or roles. Policies control access by matching the actions requested by a user or entity with the actions allowed or denied in the policy. If a requested action matches an allowed action in the policy, access is granted; otherwise, it is denied.
Q: What is the principle of least privilege, and why is it important in IAM?
A: The principle of least privilege states that users should be granted only the permissions necessary to perform their tasks and nothing more. It is important in IAM because it minimizes the risk of unauthorized access and limits the potential damage that could be caused by a compromised account. Following the principle of least privilege helps maintain a secure environment by ensuring that users have only the permissions they need to perform their job responsibilities.
Q: What is an AWS managed policy?
A: An AWS managed policy is a predefined policy created and managed by AWS. These policies cover common use cases and provide predefined permissions for specific AWS services or actions. AWS managed policies are maintained and updated by AWS, ensuring they stay up to date with new AWS services and features. They can be attached to IAM users, groups, or roles in your AWS account.
Important Question for Amazon Solution Architect Associate Exam
1. What is AWS Identity and Access Management (IAM)?
AWS IAM is a service that allows you to manage users, groups, and permissions for accessing AWS resources. It provides centralized control over authentication and authorization.
2. What are the key components of AWS IAM?
Key components of AWS IAM include users, groups, roles, policies, permissions, and identity providers.
3. How does AWS IAM work?
AWS IAM allows you to create users and groups, assign policies that define permissions, and use roles to delegate permissions to AWS services and resources.
4. What is the difference between authentication and authorization in AWS IAM?
Authentication is the process of verifying the identity of users or entities, while authorization is the process of granting or denying access to resources based on policies and permissions.
5. How can you secure your AWS account using IAM?
You can secure your AWS account by enforcing the principle of least privilege, creating strong password policies, enabling multi-factor authentication (MFA), and regularly reviewing permissions.
6. How do IAM users differ from IAM roles?
IAM users are individuals or entities that have a fixed set of permissions associated with them. IAM roles are temporary credentials that can be assumed by users or AWS services to access resources.
7. What is an IAM policy?
An IAM policy is a JSON document that defines permissions. It specifies what actions are allowed or denied on which AWS resources for whom (users, groups, or roles).
8. What is the AWS Management Console?
The AWS Management Console is a web-based interface that allows you to interact with and manage AWS resources. IAM users can use the console to access resources based on their permissions.
9. How does IAM manage access keys?
IAM users can have access keys (access key ID and secret access key) associated with their accounts, which are used for programmatic access to AWS resources.
10. What is the purpose of IAM groups?
IAM groups allow you to group users and apply policies to them collectively, simplifying permission management by granting the same set of permissions to multiple users.
11. What is the role of an IAM policy document?
An IAM policy document defines the permissions and actions that are allowed or denied. It is written in JSON format and attached to users, groups, or roles.
12. How can you grant permissions to an IAM user?
You can grant permissions to an IAM user by attaching policies to the user directly or by adding the user to groups with associated policies.
13. How can you delegate permissions to AWS services using IAM roles?
IAM roles allow you to delegate permissions to AWS services like EC2 instances, Lambda functions, and more, without exposing long-term credentials.
14. What is cross-account access in AWS IAM?
Cross-account access allows you to grant permissions to users or entities from one AWS account to access resources in another AWS account.
15. How does IAM support identity federation?
IAM supports identity federation by allowing users to access AWS resources using temporary security credentials obtained from trusted identity providers (e.g., SAML, OpenID Connect).
16. What is the purpose of an IAM access advisor?
IAM access advisors provide insights into the services that users accessed and the actions they performed. This helps in auditing and understanding resource usage.
17. How does IAM enforce the principle of least privilege?
IAM enforces the principle of least privilege by allowing you to define specific permissions for users, groups, or roles, reducing the risk of unauthorized access.
18. What is the difference between IAM policies and resource-based policies?
IAM policies are attached to identities (users, groups, roles), while resource-based policies are attached to AWS resources (e.g., S3 buckets, Lambda functions) to control access from different identities.
19. How can you implement multi-factor authentication (MFA) in IAM?
You can enable MFA for IAM users to require an additional authentication factor (e.g., a code from a virtual MFA device) along with their password when signing in.
20. What is the IAM policy evaluation logic?
IAM uses an explicit deny model, which means that if a user's permissions include an explicit deny statement, it overrides any allow statements in the policy.
Subscribe to my newsletter
Read articles from Harshit Sahu directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Harshit Sahu
Harshit Sahu
Enthusiastic about DevOps tools like Docker, Kubernetes, Maven, Nagios, Chef, and Ansible and currently learning and gaining experience by doing some hands-on projects on these tools. Also, started learning about AWS and GCP (Cloud Computing Platforms).