Quantum Security: Redefining the Cybersecurity Landscape
 Yaakulya
Yaakulya
Introduction: With advancements in quantum computing, traditional cybersecurity methods face potential obsolescence. Quantum security, powered by the principles of quantum mechanics, promises to reshape the cybersecurity landscape by offering unparalleled levels of encryption and secure communication methods. This article explores quantum security, its key technologies, and real-world applications.
1. The Quantum Threat to Classical Cryptography
Current cryptographic systems like RSA, ECC, and DSA rely on mathematical problems that are computationally hard for classical computers. However, Shor’s Algorithm, a quantum algorithm, can factor large integers exponentially faster, breaking RSA-based encryption.
Examples:
RSA-2048 Security Today: Takes billions of years to break with classical supercomputers.
RSA-2048 with a Quantum Computer: Could be cracked within hours using a sufficiently powerful quantum computer.
This means sensitive data encrypted today could be vulnerable to quantum-based attacks in the future, creating an urgent need for quantum-resistant cryptography.
2. Core Technologies Behind Quantum Security
2.1. Quantum Key Distribution (QKD)
QKD is a method for generating and sharing encryption keys using quantum principles. The BB84 Protocol is the most popular QKD implementation, relying on the quantum property of superposition and entanglement.
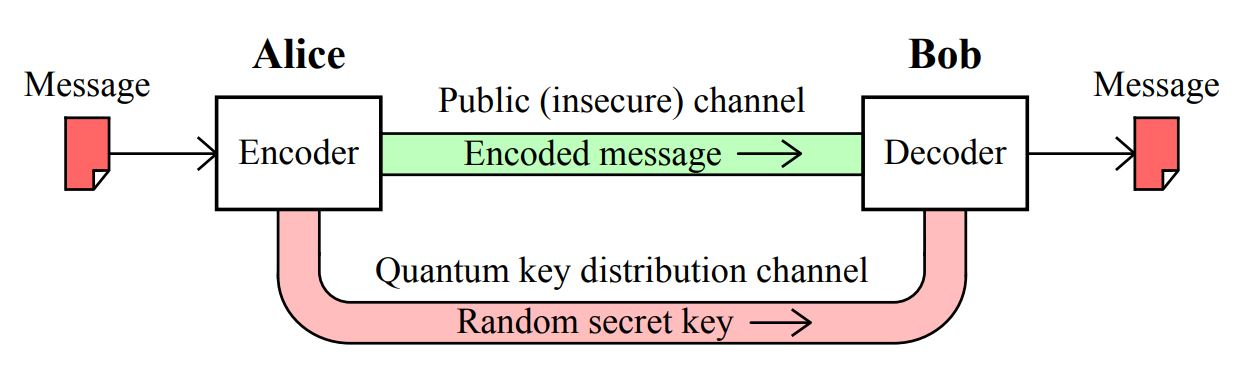
How It Works:
Alice sends quantum bits (qubits) to Bob through a quantum channel.
If an eavesdropper (Eve) intercepts these qubits, the quantum state collapses, alerting Alice and Bob of the intrusion.
Real-World Application:
- SwissQuantum Network: Switzerland implemented a national quantum communication network for secure financial transactions using QKD.
2.2. Post-Quantum Cryptography (PQC)
While QKD requires special infrastructure, Post-Quantum Cryptography is designed to be quantum-resistant while running on classical systems. Algorithms like Lattice-based Cryptography (used in NIST PQC standards) are believed to resist quantum attacks.
Example:
- Google’s New Hope Algorithm: Tested lattice-based encryption in Chrome browsers, offering quantum-resistant communication without using quantum hardware.
3. Quantum Security in Action: Real-World Examples
Example 1: Financial Sector
The financial industry is at significant risk from quantum computing advancements. If quantum computers could break RSA encryption, which many banking systems rely on, it could lead to the theft of billions of dollars. To prevent this, companies like JPMorgan Chase are exploring secure communication systems based on Quantum Key Distribution (QKD) to protect sensitive financial data.
Example 2: Military and Government Communication
Governments, such as China, have already set up advanced quantum communication networks. For instance, the Micius satellite network allows for secure military communications by using Quantum Key Distribution (QKD) to send encrypted data over vast distances. This ensures that sensitive information remains protected from potential interception.
Example 3: Blockchain and Cryptocurrency
Blockchain technology depends on digital signatures, which could be vulnerable to quantum computer attacks. Researchers are working on developing Quantum Blockchain protocols to ensure that these digital ledgers remain secure and trustworthy, even in a world where quantum computing is prevalent. These protocols aim to protect the integrity and security of blockchain networks against future quantum threats.
4. Current Challenges in Quantum Security
Despite its potential, quantum security encounters several significant challenges:
Quantum computers that can break RSA encryption are still being developed. Current quantum devices, such as Google’s Sycamore and IBM’s Q System One, are advanced but not yet capable of posing a real threat to existing encryption methods. These machines are still in the experimental phase and require further advancements to reach the level needed to compromise traditional cryptographic systems.
Setting up Quantum Key Distribution (QKD) infrastructure is expensive. It involves the installation of specialized equipment like quantum repeaters and optical fibers, which are necessary to transmit quantum keys over long distances. The high cost of these components and the complexity of integrating them into existing communication networks pose significant financial and logistical hurdles.
The development of Post-Quantum Cryptography standards is ongoing, and this process is crucial for ensuring that new cryptographic methods can be widely adopted. However, the lack of finalized standards means that there is uncertainty and hesitation in adopting these new technologies. The delay in standardization slows down the implementation of quantum-resistant security measures across industries that rely on secure communication and data protection.
5. The Road Ahead: Securing a Quantum Future
The future of cybersecurity is set to evolve significantly as it will incorporate a blend of cutting-edge technologies to protect information in the quantum era. This evolution will involve several key components:
QKD for ultra-secure communication: Quantum Key Distribution (QKD) is a groundbreaking technology that leverages the principles of quantum mechanics to create communication channels that are virtually immune to eavesdropping. By using quantum bits, or qubits, QKD ensures that any attempt to intercept the communication will be immediately detectable, thus providing an unprecedented level of security for sensitive data exchanges.
Post-Quantum Cryptography for everyday applications: As quantum computers become more advanced, they pose a potential threat to current cryptographic systems. Post-Quantum Cryptography (PQC) is being developed to counter this threat by creating algorithms that are resistant to quantum attacks. These algorithms are designed to be implemented in everyday applications, ensuring that even as quantum computing capabilities grow, our digital communications remain secure.
Hybrid Systems combining quantum and classical security measures: To maximize security, hybrid systems that integrate both quantum and classical cryptographic techniques are being developed. These systems aim to provide a layered security approach, combining the strengths of traditional cryptography with the advanced capabilities of quantum technologies to protect data against a wide range of threats.
Leading technology companies such as IBM, Microsoft, and Google are making substantial investments in the development of quantum-secure technologies. Their efforts are focused on ensuring that as quantum computing becomes more prevalent, the necessary security measures are in place to protect sensitive information. In parallel, the National Institute of Standards and Technology (NIST) is spearheading the Post-Quantum Cryptography Standardization Project, which aims to establish industry-wide encryption standards. These standards are anticipated to be finalized by 2025, providing a framework for the widespread adoption of quantum-resistant cryptographic methods across various industries.
Conclusion
Quantum security is no longer just a theoretical concept; it has become a pressing technological challenge that requires immediate attention. As quantum computing technology advances at a rapid pace, there is an urgent need for cybersecurity professionals to adopt quantum-resistant technologies. This is crucial because traditional cryptosystems, which have been the backbone of digital security, may soon become ineffective against the powerful capabilities of quantum computers.
The development of quantum algorithms is progressing quickly, and as these algorithms mature, they pose a significant threat to the security of current cryptographic systems. Therefore, it is essential for cybersecurity experts to understand and implement quantum security measures today. Doing so could mean the difference between having a defense system that is prepared for the future and facing catastrophic data breaches that could compromise sensitive information. In this race against time, the adoption of quantum-resistant technologies is not just a proactive measure but a necessary one to ensure that our digital communications and data remain secure in the face of emerging quantum threats.
Subscribe to my newsletter
Read articles from Yaakulya directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
