Understanding the Role of Web Application Firewalls (WAFs)
 Sudeep Bogati
Sudeep Bogati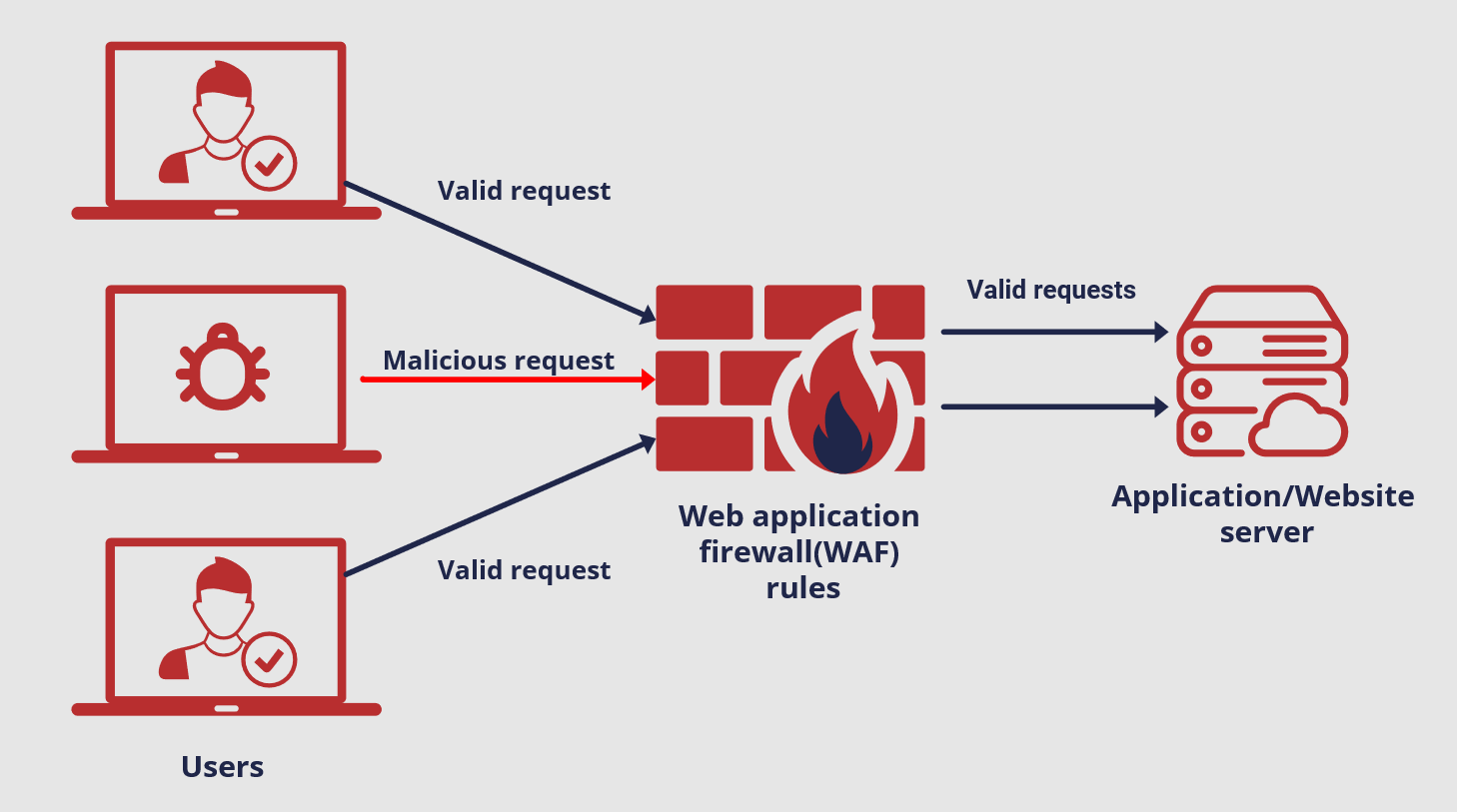
A Web Application Firewall is a security solution designed to monitor, filter, and block HTTP and HTTPS traffic to and from a web application. Unlike traditional firewalls that protect networks at the perimeter level, WAFs specifically shield web applications by inspecting requests at the application layer (Layer 7 of the OSI model). They are instrumental in identifying and mitigating attacks such as SQL injection, cross-site scripting (XSS), and other OWASP Top 10 vulnerabilities.
How Does a WAF Work?
A WAF operates by applying a set of rules or policies to HTTP requests and responses. These rules are tailored to identify and block malicious traffic while allowing legitimate requests to pass through. Here's a breakdown of how a WAF typically functions:
Traffic Inspection: The WAF intercepts incoming HTTP/HTTPS traffic before it reaches the application server.
Request Analysis: It evaluates the request headers, parameters, and payloads against predefined security policies.
Response Handling: If the request is deemed malicious, the WAF blocks or redirects it. Otherwise, the request proceeds to the application server.
Logging and Alerts: Malicious activities are logged, and alerts are sent to the administrators for further analysis.
Importance of WAFs
The significance of Web Application Firewalls (WAFs) has markedly increased in recent years, driven by the growing prevalence of cyber threats targeting web applications.
Protection Against OWASP Top 10 Threats: A WAF provides robust protection against the most common and critical web application vulnerabilities, including SQL injection, XSS, and CSRF.
Improved Compliance: Many regulatory frameworks, such as PCI DSS and GDPR, require organizations to implement measures to protect sensitive data. A WAF can help meet these compliance requirements.
Zero-Day Threat Mitigation: WAFs use heuristic and signature-based detection to block unknown vulnerabilities before patches are available.
Customizable Security Policies: Administrators can tailor rules to suit the specific needs of their web applications, ensuring optimal protection without disrupting legitimate traffic.
Reduced Risk of Data Breaches: By blocking malicious traffic, WAFs prevent attackers from exploiting vulnerabilities to gain unauthorized access to sensitive data.
Types of WAF Deployments
WAFs can be deployed in several ways, depending on the organization's infrastructure and needs:
Network-Based WAF: These are hardware appliances installed at the network edge. They offer high performance but can be costly to deploy and maintain.
Host-Based WAF: Installed directly on the application server, these WAFs are highly customizable but can consume server resources and require expertise to manage.
Cloud-Based WAF: Delivered as a service, cloud-based WAFs are easy to deploy, scalable, and require minimal maintenance. Examples include AWS WAF, Cloudflare, and Akamai.
Benefits of a Cloud-Based Web Application Firewall
Cloud-based Web Application Firewalls (WAFs) offer several advantages to organizations, including:
Scalability and Elasticity: Cloud WAFs exhibit inherent scalability, readily adapting to fluctuating traffic demands by leveraging the on-demand nature of cloud resources.
Service-Oriented Architecture: Instead of managing a dedicated physical appliance, cloud WAFs are delivered as a service. This fosters greater flexibility and facilitates the seamless addition of resources and advanced capabilities as organizational needs evolve.
Enhanced Performance: The utilization of cloud-based infrastructure can significantly enhance WAF performance. For instance, computationally intensive operations, such as Transport Layer Security (TLS) decryption, can be executed with minimal performance degradation compared to on-premises deployments.
Simplified Management: Cloud WAFs adhere to a service-oriented model, wherein the vendor assumes responsibility for numerous management tasks. This alleviates the burden on an organization's internal security team, allowing them to focus on other critical security priorities.
Access to Real-time Threat Intelligence: Cloud WAFs often benefit from direct access to their provider's real-time threat intelligence feeds, thereby augmenting their threat prevention capabilities.
Seamless Cloud-Native Integration: As virtual and cloud-native solutions, cloud WAFs seamlessly integrate with an organization's cloud-based applications. This strategic alignment can contribute to improved application performance by minimizing network latency.
Challenges and Limitations of WAFs
While WAFs provide significant security benefits, they are not without limitations:
False Positives and Negatives: Misconfigured rules can block legitimate traffic (false positives) or allow malicious traffic (false negatives).
Performance Overheads: Inspecting and filtering traffic can introduce latency, especially in high-traffic environments.
Dependency on Regular Updates: To stay effective, WAFs require frequent updates to their rule sets to address emerging threats.
Limited Protection for Non-HTTP Attacks: WAFs focus on HTTP/HTTPS traffic and may not protect against lower-layer attacks or social engineering tactics.
Conclusion
Web Application Firewalls are a critical component of modern cybersecurity strategies. By protecting web applications against a wide range of threats, they help organizations maintain the integrity, availability, and confidentiality of their systems. However, to maximize their effectiveness, WAFs should be part of a broader, multi-layered security framework. With proper deployment and management, WAFs can significantly enhance an organization’s defense against the ever-evolving landscape of cyber threats.
Subscribe to my newsletter
Read articles from Sudeep Bogati directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Sudeep Bogati
Sudeep Bogati
Hello world, This is Sudeep Bogati. I am a full stack software engineer from Nepal, passionate about developing robust web applications. I focus on creating efficient, scalable solutions and continuously enhancing my skills in the ever-evolving tech landscape.