Decentralising Bridges
 Ani
Ani
In simple terms, bridges are tools that allow the transfer of assets, data, or even smart contract instructions between different blockchain networks. Think of them as the highways connecting isolated blockchain cities. For example, if you have some Ethereum (ETH) but want to use it on the Binance Smart Chain (BSC), you’d use a bridge to "wrap" your ETH into a token that works on BSC.
The idea of blockchain bridges emerged as a response to the growing need for interoperability between siloed blockchain ecosystems. In the early days of blockchain, networks like Bitcoin and Ethereum operated in silos, each with its own set of rules, consensus mechanisms, and asset standards. This lack of connectivity limited the potential for innovation and collaboration across ecosystems.
The first generation of blockchain bridges appeared around 2017–2018 during the ICO boom, as developers began exploring ways to transfer value and data between Ethereum and other nascent chains like EOS and TRON. These early bridges were mostly centralized, operated by single entities or consortiums. While they were functional, they relied heavily on trust, which contradicted the decentralised ethos of blockchain.
By 2020, with the rise of DeFi (Decentralised Finance) and multi-chain ecosystems, the demand for more robust and decentralised bridges skyrocketed. Protocols like Polkadot and Cosmos introduced native interoperability solutions, while others like Ren and Thorchain developed bridges focused on specific use cases like Bitcoin-to-Ethereum transfers or decentralised swaps.
Today, blockchain bridges are a critical part of the Web3 infrastructure. They come in various forms, including:
Asset-Specific Bridges: Focused on transferring specific tokens (e.g., WBTC for Bitcoin on Ethereum).
Generic Message Bridges: Capable of transferring arbitrary data and instructions between chains (e.g., Axelar).
Layer 2 Bridges: Connecting Ethereum to its rollups (e.g., Arbitrum, Optimism).
The ecosystem now includes both centralized and decentralised options, with billions of dollars locked in bridge protocols. Innovations in bridging technology have also introduced concepts like state proofs and zk-rollups to enhance security and scalability. However, challenges like hacks and inefficiencies remain prevalent, making the decentralization and improvement of bridges more important than ever.
Centralised vs Decentralised Bridges
In general, centralized applications offer simplicity, speed, and easier regulatory compliance but come with risks related to control, security, and privacy. In contrast, decentralized applications provide enhanced security, transparency, and user autonomy, but may face complexities, performance issues, and governance challenges.
| Feature | Centralized Bridges | Decentralized Bridges |
| Control | Operated by a single entity or organization. | Operated by distributed validators or smart contracts. |
| Trust Model | Requires users to trust the central operator to act honestly and securely. | Trustless. Relies on network consensus and cryptographic security. |
| Transparency | Limited. Users have little visibility into internal operations. | Fully transparent. Operations are recorded on-chain and governed by open protocols. |
| Censorship Resistance | Vulnerable to censorship. Operators can block or restrict transactions. | Resistant to censorship. No single entity can manipulate or block transactions. |
| Security Risks | Single point of failure. High risk of hacks or insider fraud. | Distributed risk. Depending on the robustness of the smart contracts and validator network. |
| Scalability | Often faster, as centralization allows for streamlined operations. | Can be slower due to the need for network consensus and decentralized verification. |
| Examples | Binance Bridge, Coinbase Wallet | Wormhole, Polygon Bridge, Axelar, Thorchain |
| Innovation Flexibility | Limited by the capabilities and goals of the operator. | Open to community-driven improvements and integrations. |
There are 70+ bridges available today, distributed across various chains as per they support respectively.

Let’s explore some interesting projects amongst them to understand how they work further.
Axelar
Axelar is a decentralized interoperability network designed to facilitate secure communication and asset transfer across multiple blockchains. It operates using a robust, trustless infrastructure that prioritizes security and scalability. However, The multi-step verification process can lead to slightly longer transaction times compared to centralized solutions. Even so, Axelar stands out today as one of the prime go-to cross messaging layer due to some unique componenets:
Decentralised Validator Network: A network of validators runs the Axelar protocol, processing cross-chain transactions and maintaining security. Validators use Byzantine Fault Tolerant (BFT) consensus to ensure the system remains operational even if a subset of validators act maliciously.
Gateway Contracts: Each blockchain integrated with Axelar runs a gateway smart contract. These contracts act as the entry and exit points for messages and assets.
Cross-Chain Gateway Protocol (CGP): The CGP enables seamless communication between blockchains by packaging transactions, signing them, and relaying them securely.
One-Time Addresses: For each cross-chain transaction, Axelar generates a one-time deposit address. This mechanism simplifies user experience by eliminating the need to deal with complex multi-signature processes.
How Axelar Works:
A user initiates a transfer from Blockchain A to Blockchain B using Axelar's API or SDK.
The asset is locked in the gateway contract on Blockchain A.
Axelar validators verify the transaction, package it, and relay it to Blockchain B.
On Blockchain B, the gateway contract mints or unlocks the equivalent asset, completing the transaction.

Wormhole
Wormhole is a decentralized bridge designed to connect high-performance blockchains like Solana, Ethereum, Binance Smart Chain, and others. It operates as a message-passing protocol, enabling both asset transfers and other data exchanges between chains. It did however, suffered a $325M exploit in 2022, highlighting the need for ongoing improvements. While decentralized, the relatively small number of Guardians poses a risk of collusion.
Guardians Network: A decentralized network of validators known as Guardians monitors multiple chains for events. Guardians verify cross-chain transactions and sign messages to validate them.
Core Layer: Handles the core logic for cross-chain messaging and ensures that data integrity is maintained.
Wrapped Assets: Tokens transferred via Wormhole are wrapped into equivalent representations on the target chain.
How Wormhole Works:
A user locks an asset in a smart contract on the source chain (e.g., Ethereum).
Guardians detect the lock event and sign a message confirming the transaction.
The signed message is relayed to the target chain (e.g., Solana).
On the target chain, the Wormhole protocol mints a wrapped version of the locked asset for the user.

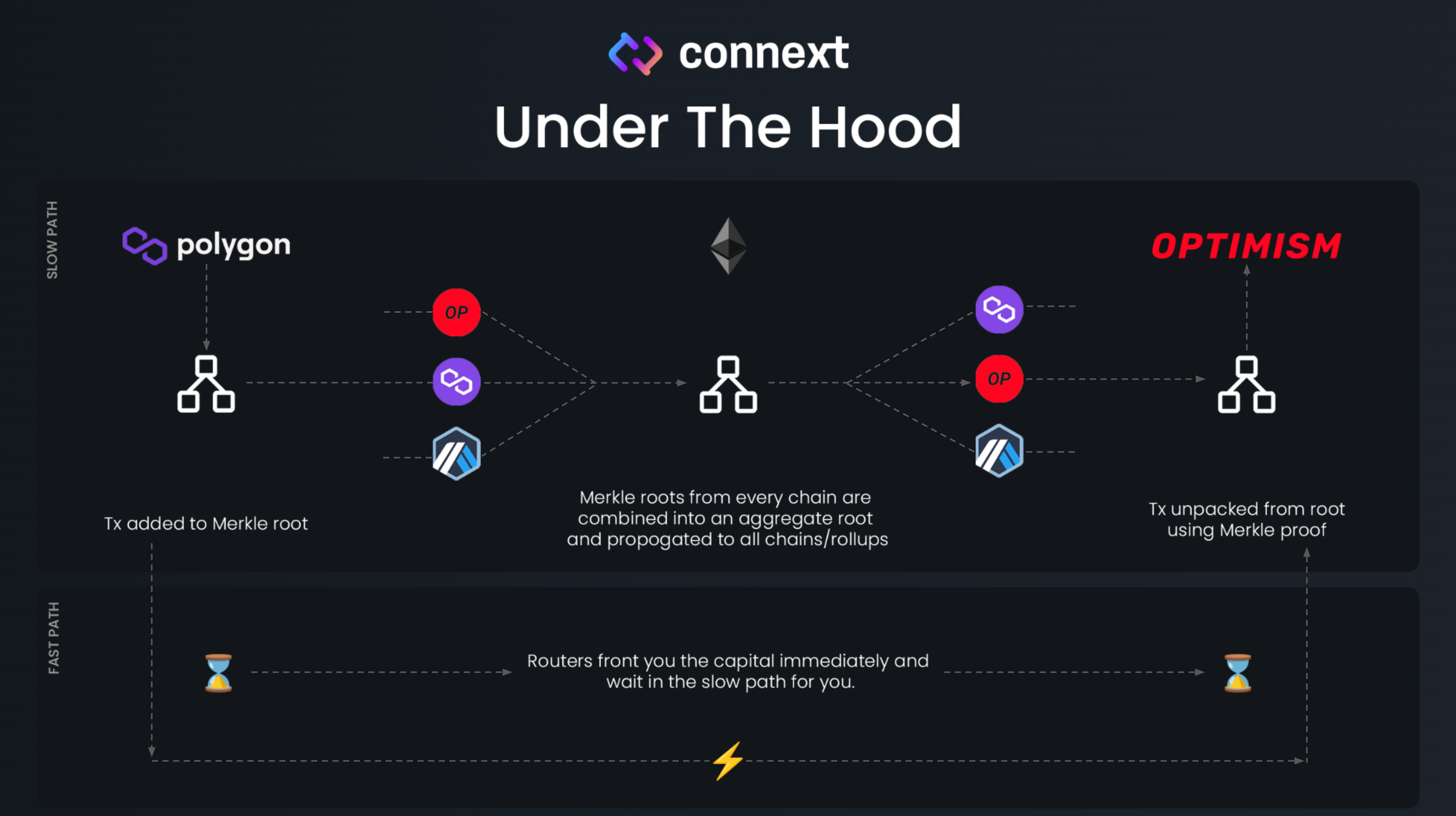
Connext
Connext is a decentralized protocol designed to facilitate fast, secure, and cost-effective cross-chain communication. It achieves this by using state channels and a unique xCall architecture for transferring value and data across Layer 2 networks and Ethereum. Unlike other bridges, Connext is tailored for fast, low-cost communication between Ethereum rollups and other Layer 2 solutions. By leveraging state channels, Connext minimizes on-chain transactions, significantly reducing gas fees. With xCall, developers can integrate cross-chain functionality into their applications without dealing with complex bridging mechanics. Connext’s router-based liquidity model ensures decentralization and eliminates reliance on a single liquidity provider. However, Connext is primarily designed for Layer 2 scaling solutions and doesn’t yet support all Layer 1 blockchains. The network relies heavily on router liquidity. Insufficient liquidity can delay or increase the cost of transactions.
State Channels: Connext builds on state channels, a Layer 2 scalability solution that allows transactions to occur off-chain while retaining the security guarantees of the underlying blockchain. These channels minimize the number of on-chain interactions, reducing latency and gas costs.
Routers: Routers are liquidity providers in the Connext network. They facilitate cross-chain transactions by locking liquidity on one chain and unlocking it on the target chain. They earn fees for their service and must collateralize their positions to ensure security.
xCall: Connext’s xCall is a generic cross-chain communication primitive. It enables developers to build applications that pass messages or assets across chains without needing to handle complex bridging logic. This mechanism abstracts the bridging process for both developers and users, ensuring simplicity.
Nomad Integration: Connext uses Nomad’s optimistic roll-up model to verify and validate cross-chain interactions. This approach reduces trust assumptions and enhances security.
How Connext Works
Transaction Initiation:
A user starts a cross-chain transaction using a Connext-integrated dApp or wallet.
For example, a user wants to transfer tokens from Optimism (Layer 2) to Polygon (another Layer 2).
Liquidity Locking:
- The router locks the required liquidity on the source chain (Optimism) and forwards an off-chain message to the destination chain (Polygon).
Off-Chain Message Passing:
- Connext uses the xCall mechanism to relay the message securely and quickly across chains. The message includes transaction details, such as the asset amount and the recipient’s address.
Transaction Finalization:
- On the destination chain (Polygon), the router unlocks equivalent liquidity and sends it to the recipient’s wallet. This process is verified by the network, ensuring security and integrity.
Bridges and the Future of Digital Assets
Bridges will play a massive role in making digital assets more usable. Imagine a world where users don’t need to know which blockchain their assets reside on, they simply transact. For example:
Abstraction: The average user shouldn’t need to know technical details about bridging. A good decentralized bridge abstracts complexities like gas fees, token wrapping, and network selection. For instance, a user transferring stablecoins across chains shouldn’t need to worry about manually configuring gas tokens or selecting intermediary networks. All such intricacies should be handled in the background by the bridge’s architecture.
Enhanced UX: With smoother cross-chain swaps and wallet integrations, bridging becomes as simple as a single click. Wallets and dApps will incorporate intuitive interfaces that seamlessly execute bridging processes, allowing users to focus on their goals rather than the mechanisms.
Interoperability-Driven Applications: Applications will harness bridges to become truly chain-agnostic. For example, a DeFi app on Ethereum could directly interact with liquidity on Solana or Avalanche without requiring the user to know or manage the underlying mechanics.
This abstraction is key to mainstream adoption. Users care about outcomes, not mechanisms. By simplifying processes, bridges can drive the mass adoption of digital assets for everyday use cases, including payments
Security Concerns
Decentralized bridges, while offering a trustless alternative, are not without their challenges.
Smart Contract Vulnerabilities: Bugs or exploits in the smart contract code can lead to massive losses, as seen in various high-profile hacks.
- Mitigation: Conduct rigorous audits by reputable firms and incentivize white-hat hackers through bug bounty programs.
Sybil Attacks: Malicious actors can attempt to overwhelm the validator network by creating multiple fake identities.
- Mitigation: Implement robust mechanisms like Proof of Stake (PoS) or Proof of Authority (PoA) to ensure validators have a vested interest in the network’s security.
Cross-Chain Attack Surface: Bridging increases the potential attack vectors since multiple chains and protocols are involved.
- Mitigation: Use cryptographic techniques like zk-rollups and state proofs to secure interactions between chains.
Economic Incentive Exploits: Attackers might manipulate incentives to destabilize the bridge’s operations.
- Mitigation: Regularly review and optimize incentive structures to align with security goals.
Decentralized Governance Risks: Poorly designed governance mechanisms can lead to decision-making that compromises security.
- Mitigation: Ensure governance models are decentralized and resistant to collusion.
Decentralized bridges are set to transform the blockchain ecosystem. Bridges will evolve to provide near-instant, cost-effective transfers, making multi-chain interactions indistinguishable from single-chain experiences. The blockchain industry will likely adopt universal protocols and standards for cross-chain communication, similar to how the internet uses TCP/IP. Advanced cryptographic techniques like zk-proofs and multi-party computation (MPC) will make bridges more secure and scalable. As DeFi and traditional finance converge, bridges will play a crucial role in enabling cross-platform transactions involving both crypto and fiat assets. Projects like Polkadot and Cosmos might pave the way for blockchain ecosystems where bridging is natively integrated, reducing the need for standalone solutions. By abstracting complexities and ensuring security, bridges will drive the mainstream adoption of blockchain technology, empowering users to interact with decentralized applications effortlessly.
Decentralized bridges are not just a technological innovation, but a necessity for the future of web3. By addressing current challenges and pushing the boundaries of interoperability, they will enable a truly interconnected and user-friendly digital economy.
Subscribe to my newsletter
Read articles from Ani directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
