The Hidden Journey Of Our Data
 Jay Kadlag
Jay Kadlag
Have you ever wondered how your data travels from a browser on your computer to a server…?
It feels like magic, but it’s actually the result of a complex system working behind the scenes.
In this article, I’ll walk you through the hidden journey of your data — from your device to the server and back — and introduce the important parts that make it all work. From the client-server architecture to the OSI model, let’s dive in!
Client-Server Architecture
Before diving into the process of data transfer, let’s understand the client-server architecture.
The client-server architecture revolutionized computing by separating client and server locations. A client is a device which sends a request and a server is a device which sends back the response. This communication between the client and server happens through a network.
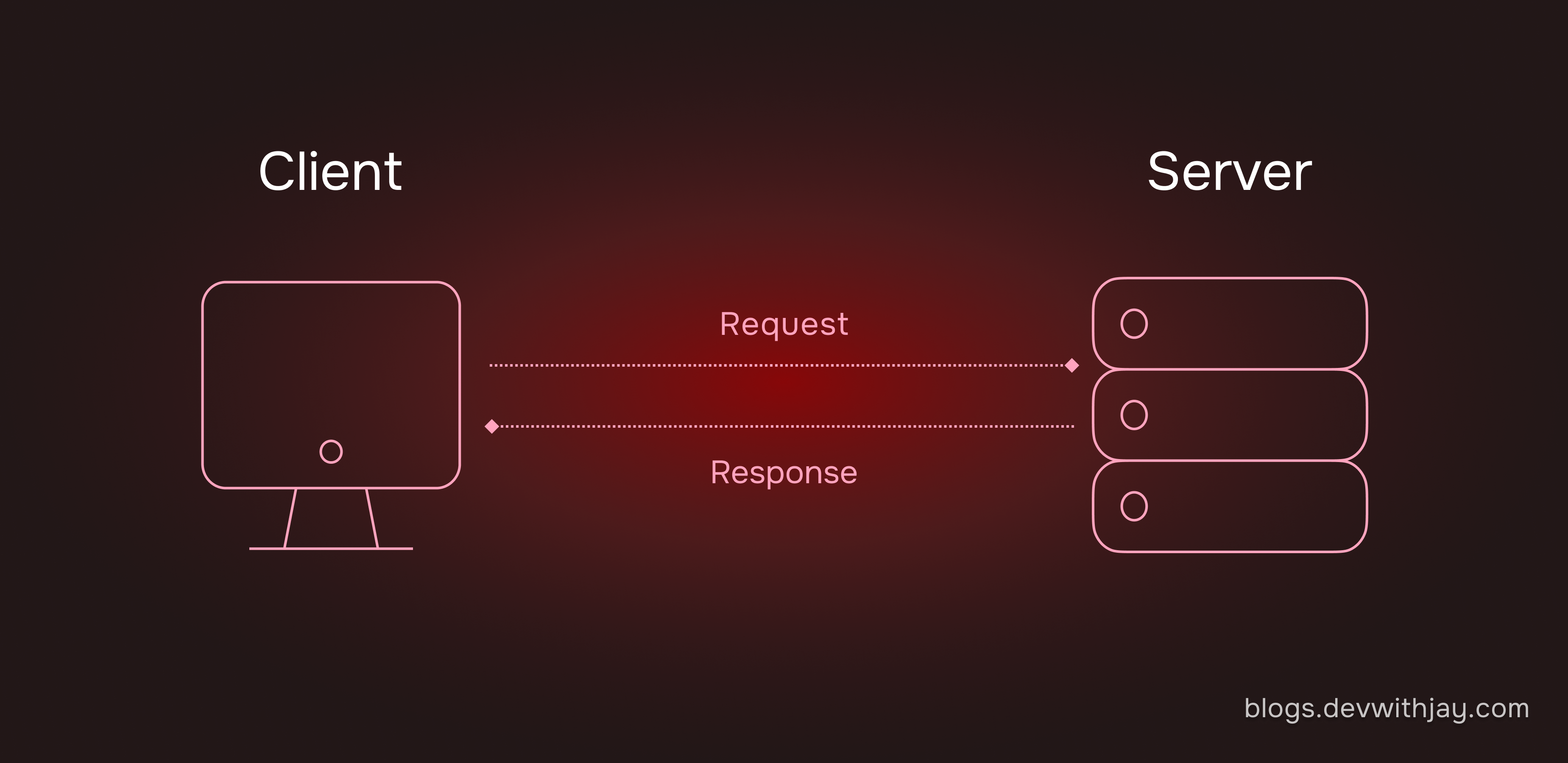
This architecture has several benefits, such as, Resource Allocation, Scalability and Efficiency. It separates the application into multiple components. Microservices evolved from this model, breaking down monolithic services into smaller, interconnected services.
OSI → Open System Interconnections
Why do we need OSI Model ?
The OSI Model is used as a standard to ensure smooth communication between systems. Without a common standard, different systems won’t be able to communicate with each other. In such case, we would need different versions of the same app for different network types like Wifi, Fiber, LTE and Ethernet.
When we use the OSI Model, apps do not need to know the type of network being used (Wifi, Ethernet, etc). Communication is smooth, no matter which type of network is used.
Layers of the OSI Model
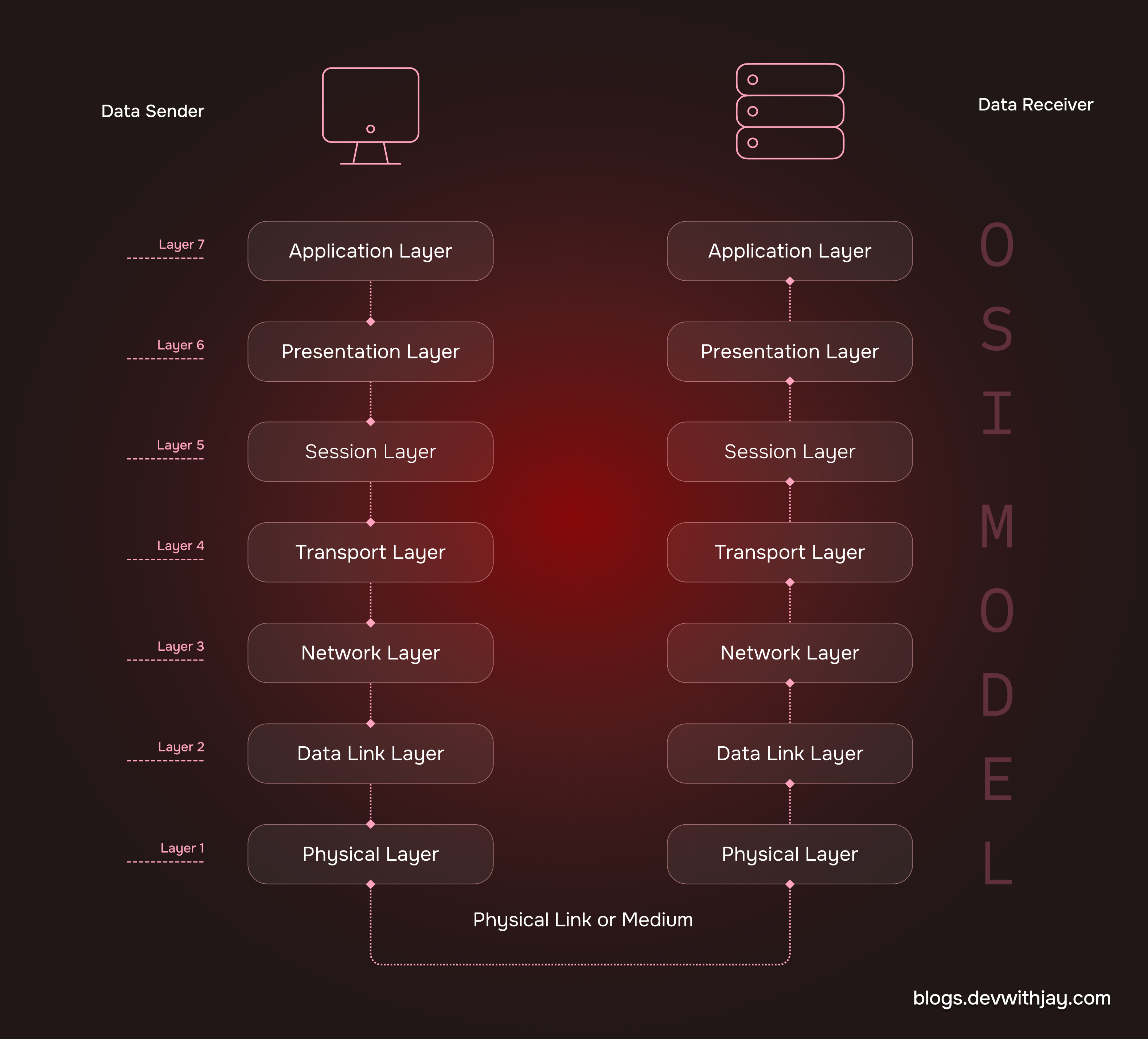
At the client side, the data passes from the top layers to the bottom layers, each layer performing certain operation on the data.
Application Layer: When you type a link, consider https://www.google.com, the browser initiates a request such as HTTP POST or GET. The request includes the data (e.g., form data, JSON payload), headers, and protocol (e.g., HTTPS).
Presentation Layer: The data is encoded or serialized into a format suitable for transmission (e.g., JSON, XML). Encryption is applied if required (e.g., SSL/TLS for HTTPS).
Session Layer: A session is established if the protocol is stateful, like, in case of TCP. The session manages connection states between the client and server. It handles starting, maintaining and ending connections.
Transport Layer: The data is segmented into smaller chunks. The TCP protocol ensures reliable delivery by establishing a connection via the three-way handshake (SYN, SYN-ACK, ACK). The segments are labeled with source and destination port numbers (e.g., port 443 for HTTPS).
Network Layer: Each segment is encapsulated in an IP packet. The source and destination IP addresses are then added to the packet header. Routing decisions are made based on the destination IP address.
Data Link Layer: Each packet is encapsulated in a frame for transmission over the network. The frame contains the source and destination MAC addresses. The frame is prepared for the specific physical medium (e.g., Ethernet, Wi-Fi).
Physical Layer: The frame is converted into a series of electrical signals, light pulses, or radio waves. These signals are transmitted through the physical medium (e.g., copper wire, fiber-optic cable, or airwaves).
At the server side, the process is reversed. The data passes from the bottom layers to the top layers.
Physical Layer: Receives the signal and converts it back into bits.
Data Link Layer: Extracts the frame and verifies the MAC address.
Network Layer: Reads the IP packet and verifies the destination IP.
Transport Layer: Reassembles the segments and verifies the ports and connection state.
Session Layer: Ensures the session is valid.
Presentation Layer: Decrypts and deserializes the data (e.g., JSON to an object).
Application Layer: Processes the request and sends a response back to the client.
Conclusion
In this article, we saw how the data transfers from your device to a server. The amount of hard work smart people have put in to make this underlying system is rarely acknowledged. So the next time you send a message to a friend or browse a website, take a moment to appreciate the work of great engineers who designed and implemented these communication protocols that power everything on the internet.
If you found this article helpful, share it with others and feel free to leave your feedback—I’d love to hear your thoughts!
Want More…?
I write articles on blog.devwithjay.com and also post development-related content on the following platforms:
Subscribe to my newsletter
Read articles from Jay Kadlag directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
