Warning: Bitwarden Users Face Complex Phishing Threat on Facebook
 Nguyễn Văn Trung
Nguyễn Văn Trung
Recently, FPT Threat Intelligence discovered a dangerous phishing campaign targeting Bitwarden users (a popular password manager) through fake ads on Facebook.
Details
In November, fake ads for the Bitwarden password manager on Facebook were spreading a malicious Chrome extension designed to collect and steal users' sensitive data from their browsers.
Bitwarden is a popular password management application with a "free" version that offers end-to-end encryption, cross-platform support, multi-factor authentication (MFA) integration, and a user-friendly interface.
Its user base has steadily increased over the past few years, especially after security breaches by competitors led many to seek alternatives.
The Facebook ad campaign warned users that they were "using an outdated version of Bitwarden" and needed to update the program immediately to protect their passwords.
The link in the ad was 'chromewebstoredownload[.]com,' impersonating Google's official Chrome Web Store at 'chromewebstore.google.com.'
The landing page also closely resembled the Chrome Web Store, including the 'Add to Chrome' button.
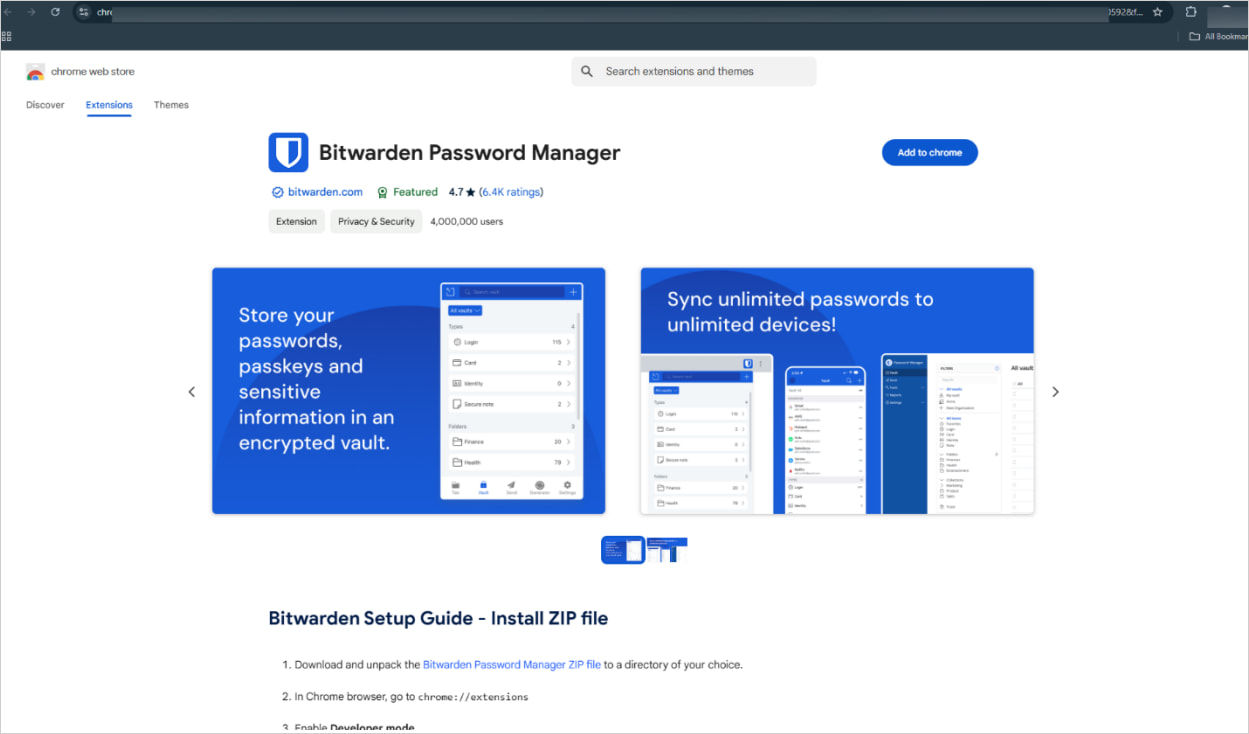
Malicious Website Imitates the Real Google Web Store Source: Bitdefender
However, instead of the extension installing automatically when you click the link, visitors are asked to download a ZIP file from a Google Drive folder.
Although this is a clear warning sign, users unfamiliar with the Chrome Web Store might proceed with manual installation by following the instructions on the website.
The installation requires enabling 'Developer Mode' on Chrome and manually loading the extension into the browser, essentially bypassing security checks.
Once installed, the extension is registered as 'Bitwarden Password Manager' version 0.0.1 and gains permissions that allow it to interfere with and manipulate user activities.
The main functions of this extension include:
Collecting Facebook cookies, especially the 'c_user' cookie that contains the user ID.
Gathering IP data and geolocation using public APIs.
Collecting Facebook user details, account information, and payment data through Facebook's Graph API.
Manipulating the browser's DOM to display fake loading messages to appear legitimate or deceptive.
Encrypting sensitive data and sending it to a Google Script URL controlled by the attacker.
Recommendations
To minimize this risk, FPT Threat Intelligence advises users to ignore ads that prompt you to update extensions, as Chrome extensions are automatically updated when a new version is released by the provider.
Additionally, follow these guidelines:
Only install extensions from the official Chrome Web Store.
Do not trust ads that ask for updates—Bitwarden updates automatically through Chrome.
Always carefully check the permissions requested by the extension.
Only download Bitwarden from the official website bitwarden.com.
References
Fake Bitwarden ads on Facebook push info-stealing Chrome extension <https://www.bleepingcomputer.com/news/security/fake-bitwarden-ads-on-facebook-push-info-stealing-chrome-extension/\>
Subscribe to my newsletter
Read articles from Nguyễn Văn Trung directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
