UEFI Secure Boot security flaw opens the way for malware to infiltrate
 Lưu Tuấn Anh
Lưu Tuấn Anh
Overview
A recent report by ESET discovered a vulnerability that allows bypassing UEFI Secure Boot, affecting a large number of UEFI-based systems. This vulnerability is named CVE-2024-7344. Exploiting this vulnerability leads to the execution of untrusted code during the system boot process, allowing attackers to easily deploy malicious UEFI like Bootkitty or BlackLotus even on systems with UEFI Secure Boot enabled, regardless of the installed operating system.
Since the vulnerability occurs during the boot stage, the malware can gain control of the system before the operating system and other security measures are loaded.

Main Findings
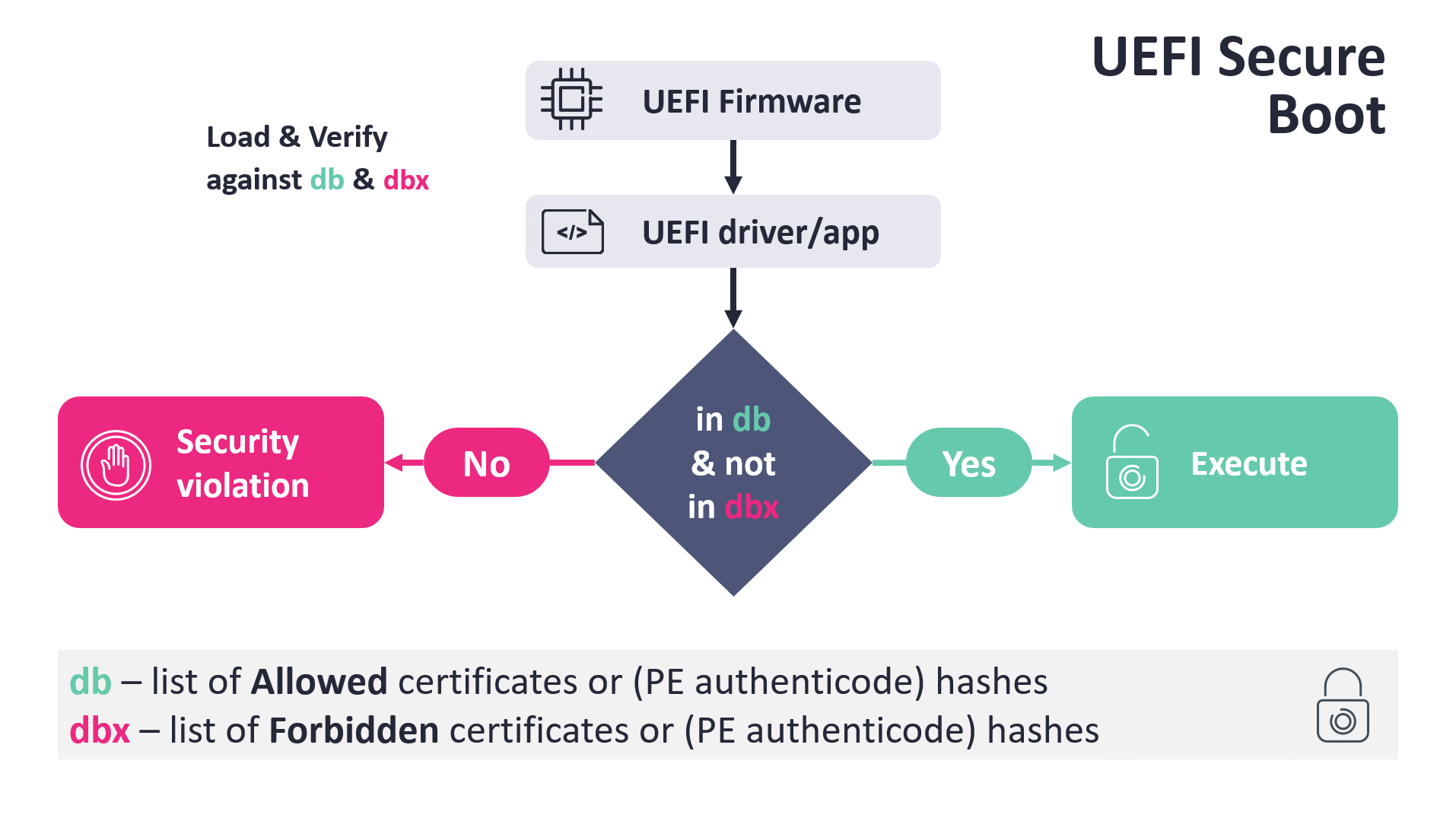
UEFI Secure Boot is a security feature designed to prevent the execution of untrusted code during the computer's boot process by checking the digital signatures of software before they are loaded. However, this vulnerability allows attackers to bypass those checks, enabling them to load bootkits—malicious software capable of hiding during the system's boot process.
When the UEFI Boot Manager loads a boot application, such as Windows Boot Manager, shim, or GRUB2, it verifies the boot application's binary file based on two Secure codes.
db – list of allowed certificates or PE Authenticode signatures.
dbx – list of revoked certificates or PE Authenticode signatures.
Some key features of malicious bootkits in the attack campaign
Interference with the boot process: Bootkits infect the Master Boot Record (MBR), Volume Boot Record (VBR), or other parts of the UEFI/BIOS boot system, allowing them to start before the operating system and other security measures.
Stealth capability: Since bootkits operate at a very low level of the system, they can evade detection by regular antivirus software and other security tools.
Comprehensive control: After a successful infection, bootkits can grant attackers access and control over the entire system. They can load other malware, steal data, or use the computer in other attacks without the user's knowledge.
Difficulty in removal: Due to the bootkits' infection location in the boot process, detecting and removing them is very complex and often requires special remediation measures, such as using external rescue tools or reinstalling the operating system.

Affected Versions
Howyar SysReturn version before 10.2.023_20240919
Greenware GreenGuard version before 10.2.023-20240927
Radix SmartRecovery version before 11.2.023-20240927
Sanfong EZ-back System version before 10.3.024-20241127
WASAY eRecoveryRX version before 8.4.022-20241127
CES NeoImpact version before 10.1.024-20241127
SignalComputer HDD King version before 10.3.021-20241127
The Stages of Attack
In this campaign, the attacker exploited a vulnerability called CVE-2024-7344 to perform unusual actions on the system. The attacker created a malicious UEFI binary file, saved under the name
“cloak.dat”, and deployed it along with a Microsoft-signed UEFI application named“loading.efi”.
The file
cloak.datused by the software SysReturn is a malware exploit tool used to exploit vulnerabilities in UEFI Secure Boot. SysReturn does this by taking advantage of flawed UEFI applications to push unsigned binaries (likecloak.dat).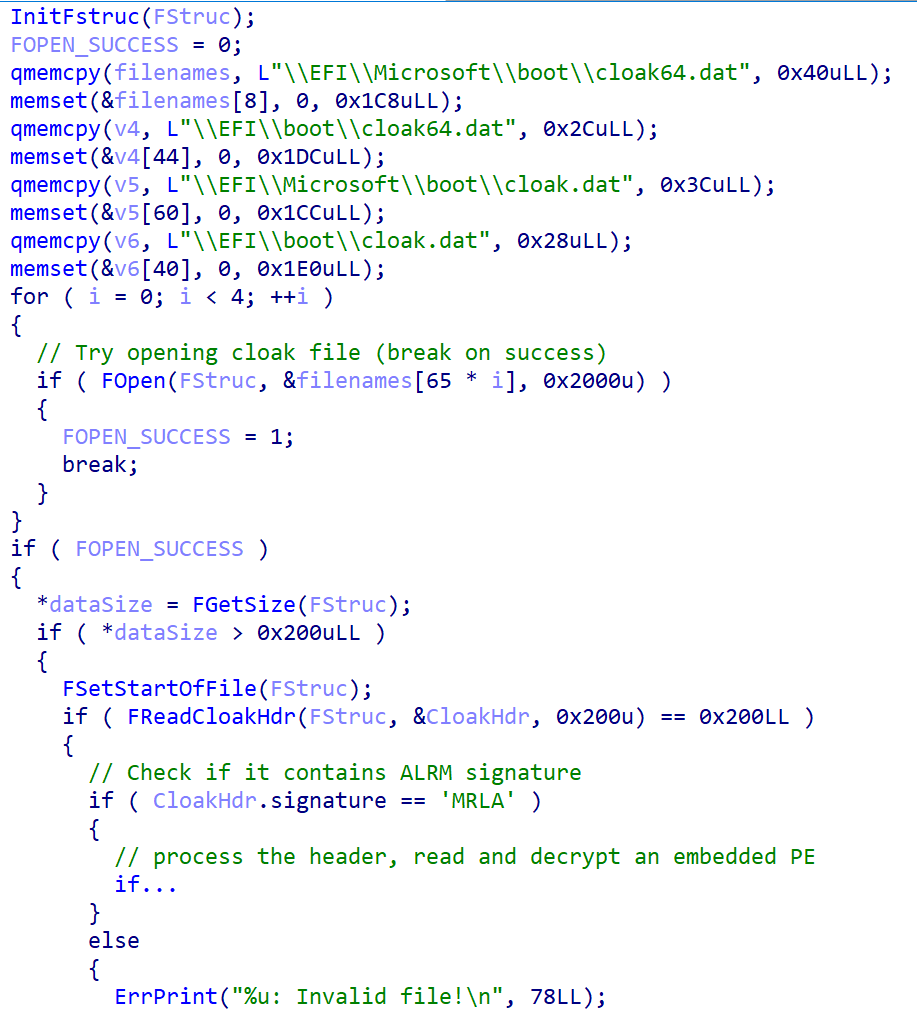
After UEFI Secure Boot, the file “loading.efi” will attempt to push .dat files into the EFI partition
\EFI\Microsoft\boot\cloak64.dat
\EFI\boot\cloak64.dat
\EFI\Microsoft\boot\cloak.dat
\EFI\boot\cloak.dat
Then, a series of actions load and execute PE files from
cloak.datand perform exploits. This allows the attacker to fully control the system's boot process, leading to the execution of malicious code before the operating system starts, facilitating the setup of bootkits that are hard to detect and remove.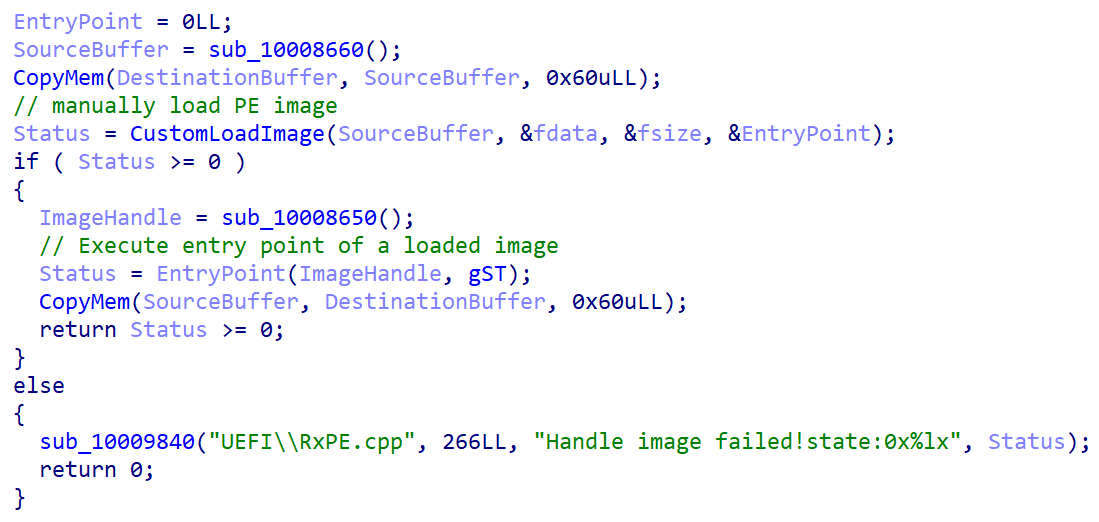
Exploiting this vulnerability is not limited to systems with affected recovery software installed, as the attacker can bring their own copy of the vulnerable
Reloader.efibinary file to any UEFI system registered with Microsoft's third-party UEFI certificate.
IOCs
Malicious file
cloak.datbootx64.efishellx64.efi
Malicious activity
CopyMem
FReadCloakHdrEntryPoint(thực thi mã nhị phân được nạp thủ công).
Hash Code:
cdb7c90d3ab8833d5324f5d8516d41fa990b9ca721fe643fffaef9057d9f9e48
e9e4b5a51f6a5575b9f5bfab1852b0cb2795c66ff4b28135097cba671a5491b9
Recommendations
Update from the software provider:
Howyar has released an update for the "Reloader" application to fix this vulnerability. Users should visit Howyar's official website to download and install the latest version of the software.
Update the Secure Boot database (DBX):
- The UEFI Forum has updated the revocation list to prevent the execution of affected UEFI applications. Users should update their system's DBX to ensure unsafe applications are blocked.
Update firmware and operating system:
Motherboard and device manufacturers may release firmware updates to address this vulnerability. Users should check the manufacturer's website for details and update the firmware if available.
Ensure the operating system is fully updated with the latest security patches from the provider.
Conclusion
In recent years, the number of discovered UEFI vulnerabilities and the failure to patch them or revoke vulnerable binaries in a timely manner indicate that even an essential feature like UEFI Secure Boot should not be considered an impenetrable barrier.
Moreover, the exploitation and operation of this vulnerability highlight the importance of maintaining security for the UEFI boot process and applying timely security updates.
References
Subscribe to my newsletter
Read articles from Lưu Tuấn Anh directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
