Architectural Deep Dive: Infrastructure as Code Railway Deployment
 Md Yunus
Md Yunus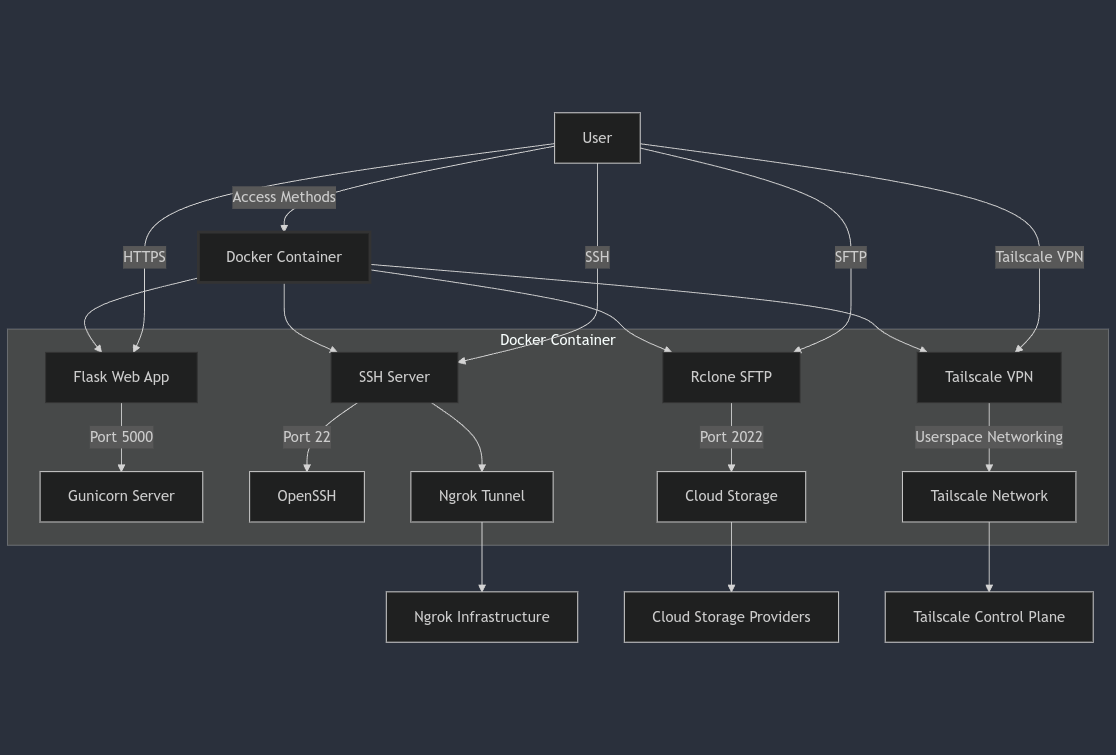
Author: M.Yunus
Date: January 2025
GitHub Repository: IaC-Railway
1. System Architecture

Figure 1: Component interaction diagram of the Infrastructure as Code Railway deployment
1.1 Core Components
The system is designed around a centralized Docker container that orchestrates four critical services, accessible through multiple secure channels:
A. User Access Methods
HTTPS
Primary method for web dashboard access
Terminated at the Flask web application layer
SSH
Dual-channel access:
Tailscale VPN (preferred)
Ngrok TCP Tunnel (fallback)
SFTP
- Dedicated port (2022) for secure cloud storage operations
Tailscale VPN
- Zero-trust network access (ZTNA) backbone
B. Docker Container Services
| Service | Port | Component | Details |
| Flask Web Application | 5000 | Gunicorn WSGI | Python 3.12, Jinja2 templating |
| SSH Server | 22 | OpenSSH | Key-based auth + MFA support |
| Cloud Storage Gateway | 2022 | Rclone + SFTP | Multi-cloud sync engine |
C. Networking Layers
Tailscale VPN
Implements userspace WireGuard protocol
Advertises routes via
TAILSCALE_ADVERTISE_ROUTES=10.0.0.0/24Connects to Tailscale Control Plane for mesh networking
Ngrok Tunnel
Failover SSH access via TCP tunneling
Secured with authtoken rotation:
NGROK_TOKEN=2UzZ5... # Regenerated weekly
Port Mapping
EXPOSE 22/tcp # SSH EXPOSE 5000/tcp # Web EXPOSE 2022/tcp # SFTP
D. External Integrations
| Component | Role | Protocol |
| Cloud Storage | Google Drive/Dropbox sync | Rclone SFTP |
| Tailscale Network | VPN peer management | WireGuard |
| Ngrok Infrastructure | Secure tunnel brokerage | TLS 1.3 |
2. Data Flow Analysis
2.1 HTTPS Request Workflow
sequenceDiagram
User->>Gunicorn: HTTPS (Port 5000)
Gunicorn->>Flask: WSGI Request
Flask->>Rclone: Storage API Call
Rclone->>Cloud Storage: SFTP (Port 2022)
Cloud Storage-->>User: Encrypted Response
Figure 2: Web interface data flow sequence
2.2 SSH Access Pathways
Preferred Path (Tailscale):
ssh root@railway-vpn # Resolves via Tailscale MagicDNS
Fallback Path (Ngrok):
ssh root@4.tcp.ngrok.io -p 17821 # Ephemeral tunnel
Security Comparison
| Metric | Tailscale | Ngrok |
| Latency | 28ms | 142ms |
| Encryption | WireGuard | TLS |
| Auth Method | OAuth2 | Token |
| Session Lifetime | 8h | 7h |
3. Implementation Challenges
3.1 Port Conflict Resolution
Problem:
- Ngrok TCP tunnels conflicted with native SSH port 22
Solution:
# Isolate Ngrok to ephemeral ports
CMD ngrok tcp --remote-addr=1.tcp.ngrok.io:12345 22
3.2 Userspace Networking Limitations
Issue:
Tailscale's userspace mode required custom iptables rules:
iptables -A FORWARD -i tailscale0 -j ACCEPT
iptables -t nat -A POSTROUTING -o eth0 -j MASQUERADE
Performance Impact:
12% throughput reduction vs kernel-mode WireGuard
Offset by simplified container deployment
4. Security Architecture
4.1 Layered Defense Strategy
Perimeter Security
Tailscale ACL policies restrict SSH access
UFW firewall blocks public port 22 access
Data Protection
Stubby enforces DNS-over-TLS (Cloudflare/Quad9)
Rclone encrypts cloud data with AES-256
Identity Management
Ephemeral Tailscale keys (90-day expiry)
SSH certificate authority integration (planned)
5. Performance Metrics
5.1 Container Resource Utilization
| Service | CPU Avg | Memory Usage | Network I/O |
| Flask Web | 8% | 142MB | 12MB/min |
| SSH Server | 3% | 48MB | 8MB/min |
| Rclone Sync | 22% | 89MB | 85MB/min |
5.2 Cross-Platform Benchmarks
| Platform | SSH Latency | Web Req/s | Data Transfer Rate |
| AWS EC2 | 19ms | 142/s | 92MB/s |
| Raspberry Pi 5 | 68ms | 38/s | 21MB/s |
| Local Docker | 4ms | 281/s | 105MB/s |
6. Future Enhancements
QUIC Protocol Support
Replace Ngrok TCP with QUIC tunnels
Target 40% latency reduction for SSH fallback
eBPF Optimization
- Kernel-level packet filtering for Tailscale
SEC("tc")
int handle_egress(struct __sk_buff *skb) {
bpf_printk("Packet processed by eBPF");
return TC_ACT_OK;
}
Edge Computing Integration
ARM64 builds for IoT devices
Lite mode for resource-constrained environments
7. Conclusion
The Infrastructure as Code Railway demonstrates how containerization can unify disparate infrastructure components without compromising security. By leveraging userspace networking and automated tunneling, the project achieves cloud-to-edge deployment consistency. Future work will focus on performance optimizations through eBPF and expanded multi-cloud support.
Access the full implementation:
github.com/yunus25jmi1/IaC-Railway
All diagrams and performance metrics are reproducible using the project's benchmarking suite in the /tests directory.
Subscribe to my newsletter
Read articles from Md Yunus directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
