Unikernel Containers
 Subhanshu Mohan Gupta
Subhanshu Mohan Gupta
Introduction
In a rapidly evolving technological landscape, where agility and security are paramount, unikernel containers are emerging as a revolutionary force in DevSecOps. These ultra-lightweight containers challenge the status quo by running applications directly on hardware or virtual machines, eliminating the need for traditional operating systems. By doing so, unikernel containers promise to enhance isolation, minimize attack surfaces, and significantly boost performance. This article delves into the potential of unikernel containers to redefine security in DevSecOps.
What Are Unikernel Containers?
Unikernel containers are specialized single-application systems that bundle an application and its dependencies into a standalone binary. Unlike traditional containers that run on an operating system layer (e.g., Docker containers with a Linux kernel), unikernel containers operate without a general-purpose OS. They provide only the necessary functionality for the application, significantly reducing complexity.
Architecture
Source - https://phoenixnap.com/kb/unikernel-vs-container
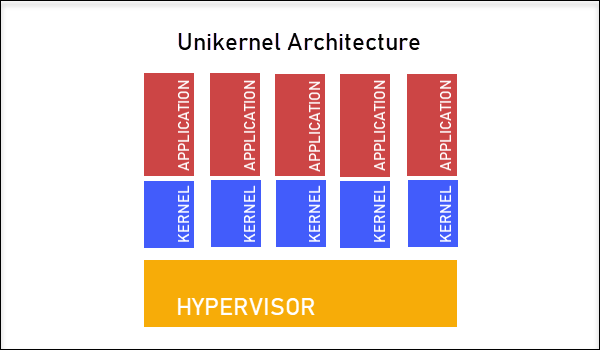
Key Features of Unikernel Containers:
Single-purpose design: Only the application and essential libraries are included.
No general-purpose OS: Removes the traditional kernel and system overhead.
Improved isolation: Each unikernel operates in a sandboxed environment.
Docker Containers vs. Unikernel Containers: A Comparison
| Feature | Docker Containers | Unikernel Containers |
| Underlying OS | Requires a general-purpose OS (e.g., Linux) | OS-less; includes only essential libraries |
| Resource Usage | Higher due to OS overhead | Minimal due to single-purpose design |
| Security | Larger attack surface (shared OS kernel) | Reduced attack surface (no shared OS) |
| Startup Time | Relatively fast | Ultra-fast due to lack of OS initialization |
| Complexity | Moderate (requires container runtime and OS) | Low (single binary directly executed) |
Enhanced Security Through OS-less Architecture
Unikernel containers offer transformative security benefits, making them ideal for DevSecOps:
1. Minimal Attack Surface:
By eliminating the general-purpose OS, unikernel containers drastically reduce exploitable components. Fewer binaries mean fewer vulnerabilities.
2. Improved Isolation:
Each unikernel operates independently, providing robust isolation similar to virtual machines but with the efficiency of containers.
3. Resistance to Lateral Movement:
Without a shared OS kernel, attackers cannot leverage traditional privilege escalation techniques, enhancing security against lateral attacks.
4. Built-in Read-Only Design:
Unikernel containers are typically immutable, making them inherently resistant to tampering and malware.
Redefining Minimalist DevSecOps
Unikernel containers align perfectly with the principles of "minimalist DevSecOps," enabling:
Ultra-Light Deployments:
- Reduce resource consumption by running only what is essential for the application.
Simplified Compliance:
- With fewer components, unikernel systems simplify audits and compliance with frameworks like GDPR and HIPAA.
Faster Incident Response:
- Lightweight binaries and minimal layers enable faster analysis and recovery in case of incidents.
Scalable Security:
- Deploy thousands of unikernel containers with minimal overhead, scaling security without compromising performance.
Guide to Implementing Unikernel Container

Prerequisites
Development Environment: Linux-based OS with support for virtualization (KVM, Xen, or VirtualBox).
Unikernel Toolchains: Tools like MirageOS, Unik, or OSv.
CI/CD Tool: Jenkins, GitLab CI, or GitHub Actions.
Step 1: Install the Unikernel Toolchain
Install MirageOS (Example):
sudo apt update
sudo apt install opam m4 build-essential
opam init
opam switch create mirage 4.0.0
opam install mirage
Install Unik:
# Clone and install Unik
git clone https://github.com/solo-io/unik.git
cd unik
make
sudo make install
unik up
Step 2: Create a Sample Application
Write a Simple HTTP Server in OCaml (for MirageOS):
Create server.ml:
open Lwt.Infix
open Mirage
let start _ =
let callback _conn request _body =
let uri = Cohttp.Request.uri request in
let response_body = Printf.sprintf "Hello, world! Requested URI: %s" (Uri.to_string uri) in
Server.respond_string ~status:`OK ~body:response_body ()
in
let server = Server.make ~callback () in
Conduit_mirage.with_tls (Tls.Config.server ()) >>= fun tls_config ->
Server.create ~tls_config (Server.TCP (Ipaddr.V4.any, 8080)) server
Step 3: Build the Unikernel
For MirageOS:
Configure the unikernel:
mirage configure -t xen
Build the unikernel:
make
For Unik:
Create an image:
unik build --name hello-world --path ./path-to-your-application --base rump --language python
Run the unikernel:
unik run --instanceName hello-instance --imageName hello-world --mounts /data:/data
Step 4: Integrate into CI/CD Pipeline
GitLab CI Example:
Create .gitlab-ci.yml:
stages:
- build
- test
- deploy
build:
stage: build
script:
- opam init
- opam switch create mirage 4.0.0
- opam install mirage
- mirage configure -t xen
- make
artifacts:
paths:
- unikernel.xen
test:
stage: test
script:
- echo "Running unit tests..."
deploy:
stage: deploy
script:
- echo "Deploying to production..."
Step 5: Deploy and Monitor
Deploy the unikernel to a lightweight hypervisor like KVM:
qemu-system-x86_64 -kernel unikernel.xen -nographic
Integrate monitoring with Prometheus:
# Use Prometheus Node Exporter for unikernel environments
./node_exporter --web.listen-address ":9100"
Enhanced Security Practices
Immutability: Ensure all unikernels are read-only.
TLS Encryption: Use libraries like
tls-miragefor encrypted communications.Automated Vulnerability Scanning: Integrate tools like Lynis for security checks.
Challenges and the Road Ahead
Despite their advantages, unikernel containers face challenges:
Tooling and Ecosystem: Limited orchestration tools compared to Docker.
Learning Curve: Requires teams to learn new unikernel-specific tools and workflows.
Compatibility: Legacy applications may require refactoring to fit the unikernel model.
However, as DevSecOps evolves, the benefits of unikernel containers make them a compelling choice for organizations seeking secure, lightweight, and high-performance solutions.
Conclusion
Unikernel containers offer a groundbreaking approach to achieving ultra-lightweight security in DevSecOps. By eliminating the traditional OS layer, they reduce complexity, enhance isolation, and deliver unmatched performance. While the ecosystem is still maturing, the potential of unikernel containers to redefine security practices and enable minimalist DevSecOps is undeniable. As organizations strive for faster, safer, and more efficient workflows, unikernel containers are poised to lead the way.
Subscribe to my newsletter
Read articles from Subhanshu Mohan Gupta directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Subhanshu Mohan Gupta
Subhanshu Mohan Gupta
A passionate AI DevOps Engineer specialized in creating secure, scalable, and efficient systems that bridge development and operations. My expertise lies in automating complex processes, integrating AI-driven solutions, and ensuring seamless, secure delivery pipelines. With a deep understanding of cloud infrastructure, CI/CD, and cybersecurity, I thrive on solving challenges at the intersection of innovation and security, driving continuous improvement in both technology and team dynamics.