Unattended Upgrades: A Love-Hate Relationship?
 Aadarsha Dhakal
Aadarsha Dhakal
Since Ubuntu 16.04, unattended upgrades have been a standard feature. I think, at first glance, the idea of automatic security updates sounds fantastic. It's like having a little helper constantly patching those pesky vulnerabilities while you sleep (or, you know, work). Essentially, it automatically installs security updates, which is a big plus for keeping your system safe.
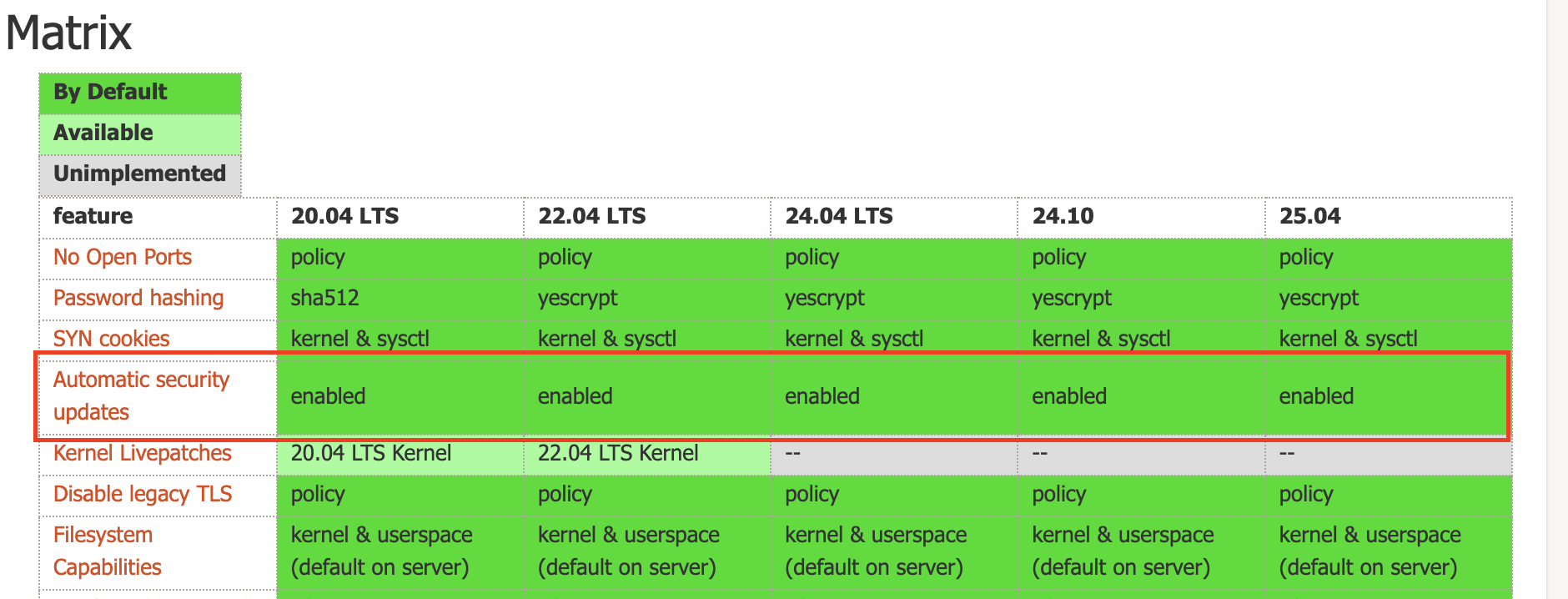
By default, unattended upgrades focus on installing security updates. It usually handles updates from the -security repository. A typical configuration, split across two files, might look like this:
/etc/apt/apt.conf.d/20auto-upgrades
APT::Periodic::Update-Package-Lists "1";
APT::Periodic::Unattended-Upgrade "1";
/etc/apt/apt.conf.d/50unattended-upgrades1
Unattended-Upgrade::Allowed-Origins {
"${distro_id}:${distro_codename}";
"${distro_id}:${distro_codename}-security";
"${distro_id}ESMApps:${distro_codename}-apps-security";
"${distro_id}ESM:${distro_codename}-infra-security";
};
Unattended-Upgrade::Package-Blacklist {
};
Unattended-Upgrade::DevRelease "auto";
While I appreciate the security focus, I've also seen some downsides. In a corporate environment, where a dedicated team handles patching, unattended upgrades can be a bit of a headache. Imagine a critical system getting updated without the sysadmins knowing! This can lead to unexpected downtime or compatibility issues. That's why Debian itself recommends monitoring your systems closely if you use unattended upgrades. They suggest installing apt-listchanges to get email notifications about updates. You can also check the logs at /var/log/dpkg.log and /var/log/unattended-upgrades/ for details on what's been updated.
So, what if you decide unattended upgrades aren't for you? Disabling them is pretty straightforward. You can edit the unattended-upgrades configuration files and adjust the settings. For example, setting APT::Periodic::Unattended-Upgrade to "0" in /etc/apt/apt.conf.d/20auto-upgrades would disable the automatic upgrades. Alternatively, you can remove the unattended-upgrades package altogether:
Bash
sudo apt remove unattended-upgrades
Beyond just removing the package, you can also use systemctl to mask and disable the related services, providing an extra layer of prevention:
Bash
sudo systemctl mask unattended-upgrades.service
sudo systemctl disable unattended-upgrades.service
Masking prevents the service from being easily started, even manually, and disabling it prevents it from starting on boot.
If you want to customize the frequency of the unattended upgrades, you can adjust the systemd timers. More information on modifying the download and upgrade schedules can be found here: https://wiki.debian.org/UnattendedUpgrades#Modifying_download_and_upgrade_schedules_.28on_systemd.29
In my opinion, unattended upgrades feel a bit like a "Windows" approach. The Linux world, in my experience, generally prefers more control and transparency. That's probably why Debian has changed its default behavior in Debian 12 (Bookworm). It no longer installs unattended-upgrades by default with GNOME. Instead, it notifies you about available updates and lets you decide when to install them. I think this is a much better approach. People who want automatic updates can still opt-in, but it's not forced on everyone.
Ultimately, the decision of whether or not to use unattended upgrades depends on your specific needs and preferences. If you're a home user and want a hands-off approach to security, it might be a good fit. But in a corporate environment, where control and monitoring are crucial, it might be best to manage updates manually.
Subscribe to my newsletter
Read articles from Aadarsha Dhakal directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
