OpenSCAP for security compliance and vulnerability scanning
 Yves Stanislas ADANI
Yves Stanislas ADANI
Main objectives
As a Security Engineer within a Bank , the Chief Security Officer (CSO) of our organization has requested that a compliance scan be conducted to meet the PCI-DSS requirements.
Let’s do that !
The main stages of the procedure adopted
As a security engineer, where can we start or how can we proceed ?
We will then run tools based on the Security Content Automation Protocol (SCAP) standard for compliance and vulnerability scanning to perform our task(s) and at the end generate a comprehensive report to the C level which include our Chief Security Officer.
Let’s see the workflow which will be used to perform our task:
Download the packages necessary for OpenSCAP and the SCAP security guide
Explore the scanning profiles available to use
Run the scan and generate an HTML report
Remediate an issue found during the scan
Re-run the scan to ensure the issue is remediated
Step 1
We have to start by installing the SCAP packages SCAP (Security Content Automation Protocol) which is a NIST project that standardizes the language for describing assessment criteria and findings. In our situation we’ll choose OpenSCAP, available in RHEL, which is a SCAP based compliance toolkit that includes policies and tools that can allow us to scan and evaluate host machines.
Prior to getting started, we will install the package that consists of the command line interface of the OpenSCAP scanner (oscap). OpenSCAP also has a graphical tool called SCAP workbench, but in this lab, we will only be using the command line interface. We will also install the SCAP Security guide, which implements security guidance rules and remediation scripts by respective authorities, namely PCI DSS, STIG, etc. In this lab, we will scan the system against the PCI DSS profile.
Ensure that apache server, OpenSCAP scanner and definitions are installed with the command below; it’s safe to run even if the packages already exist. OpenSCAP is not dependant on apache server, however it is needed in this lab for the purposes of viewing the HTML report generated by OpenSCAP.
yum install -y httpd openscap-scanner scap-security-guide
After the installation, all SCAP Security Guide security policies are in the /usr/share/xml/scap/ssg/content/ directory.
We can verify that by executing this command —> ls /usr/share/xml/scap/ssg/content
Step 2
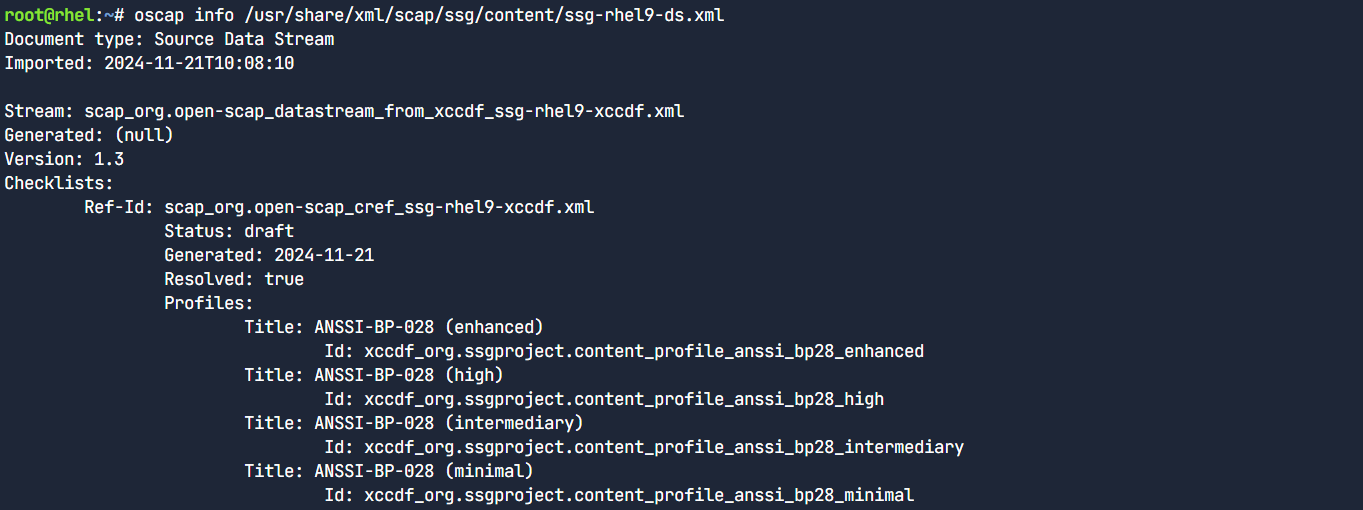
Now let’s continue by displaying available profiles. We can display all available profiles in the datastream file using the openscap info command. For this lab, you will be using the RHEL9 datastream file.
oscap info /usr/share/xml/scap/ssg/content/ssg-rhel9-ds.xml
<< OUTPUT ABRIDGED >> Profiles: Title: ANSSI-BP-028 (enhanced) Id: xccdf_org.ssgproject.content_profile_anssi_bp28_enhanced Title: ANSSI-BP-028 (high) Id: xccdf_org.ssgproject.content_profile_anssi_bp28_high Title: ANSSI-BP-028 (intermediary) Id: xccdf_org.ssgproject.content_profile_anssi_bp28_intermediary Title: ANSSI-BP-028 (minimal) Id: xccdf_org.ssgproject.content_profile_anssi_bp28_minimal Title: CCN Red Hat Enterprise Linux 9 - Advanced Id: xccdf_org.ssgproject.content_profile_ccn_advanced Title: CCN Red Hat Enterprise Linux 9 - Basic Id: xccdf_org.ssgproject.content_profile_ccn_basic Title: CCN Red Hat Enterprise Linux 9 - Intermediate Id: xccdf_org.ssgproject.content_profile_ccn_intermediate Title: CIS Red Hat Enterprise Linux 9 Benchmark for Level 2 - Server Id: xccdf_org.ssgproject.content_profile_cis Title: CIS Red Hat Enterprise Linux 9 Benchmark for Level 1 - Server Id: xccdf_org.ssgproject.content_profile_cis_server_l1 Title: CIS Red Hat Enterprise Linux 9 Benchmark for Level 1 - Workstation Id: xccdf_org.ssgproject.content_profile_cis_workstation_l1 Title: CIS Red Hat Enterprise Linux 9 Benchmark for Level 2 - Workstation Id: xccdf_org.ssgproject.content_profile_cis_workstation_l2 Title: [DRAFT] Unclassified Information in Non-federal Information Systems and Organizations (NIST 800-171) Id: xccdf_org.ssgproject.content_profile_cui Title: Australian Cyber Security Centre (ACSC) Essential Eight Id: xccdf_org.ssgproject.content_profile_e8 Title: Health Insurance Portability and Accountability Act (HIPAA) Id: xccdf_org.ssgproject.content_profile_hipaa Title: Australian Cyber Security Centre (ACSC) ISM Official Id: xccdf_org.ssgproject.content_profile_ism_o Title: Protection Profile for General Purpose Operating Systems Id: xccdf_org.ssgproject.content_profile_ospp Title: PCI-DSS v3.2.1 Control Baseline for Red Hat Enterprise Linux 9 Id: xccdf_org.ssgproject.content_profile_pci-dss Title: [DRAFT] DISA STIG for Red Hat Enterprise Linux 9 Id: xccdf_org.ssgproject.content_profile_stig Title: [DRAFT] DISA STIG with GUI for Red Hat Enterprise Linux 9 Id: xccdf_org.ssgproject.content_profile_stig_gui Referenced check files: ssg-rhel9-oval.xml system: http://oval.mitre.org/XMLSchema/oval-definitions-5 ssg-rhel9-ocil.xml system: http://scap.nist.gov/schema/ocil/2 security-data-oval-v2-RHEL9-rhel-9.oval.xml.bz2 system: http://oval.mitre.org/XMLSchema/oval-definitions-5 << OUTPUT ABRIDGED >>
We have to note that each profile in the output has a title which describes the profile and corresponding Id. For this lab, we are interested in the PCI-DSS profile, and the corresponding Id is xccdf_org.ssgproject.content_profile_pci-dss.
A profile contains generic security recommendations that apply to all Red Hat Enterprise Linux installations and additional security recommendations that are specific to the intended usage of a system. To obtain information about a specific profile, specify the profile Id using the --profile option.
oscap info --profile xccdf_org.ssgproject.content_profile_pci-dss /usr/share/xml/scap/ssg/content/ssg-rhel9-ds.xml
The datastream file makes references to remote OVAL content that is regularly updated. During scanning, OpenSCAP attempts to download the resources locally if --fetch-remote-resources option is provided.
Step 3
At this level we will scan and generate a report
A XCCDF document is a structured collection of security configuration rules for some set of target system. In this case, it has the configuration rules that meet the PCI regulation.
To start scanning using OpenSCAP, we will use the oscap xccdf eval command with the profile Id, option to fetch remote resources, output XML results file, and the datastream file.
oscap xccdf eval --fetch-remote-resources --profile xccdf_org.ssgproject.content_profile_pci-dss --results /tmp/scan-xccdf-results.xml /usr/share/xml/scap/ssg/content/ssg-rhel9-ds.xml
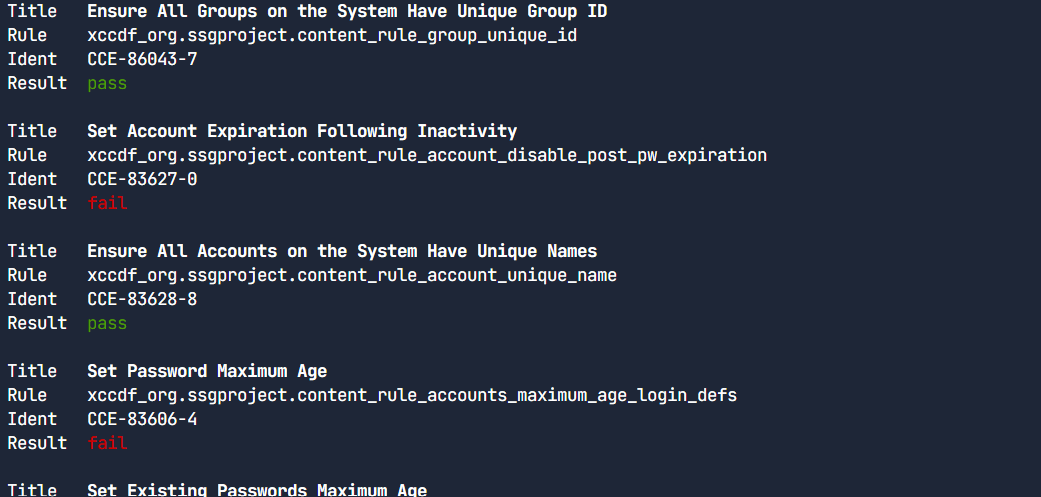
This scan can take a few minutes to complete as it has to evaluate all the rules, and generate a XML file that has the results.
Once the scan completes, you can look at the pass/fail status of each rule in the output . The XML results file can be transformed into HTML or plain-text format for easier readability
oscap xccdf generate report /tmp/scan-xccdf-results.xml > /var/www/html/index.html
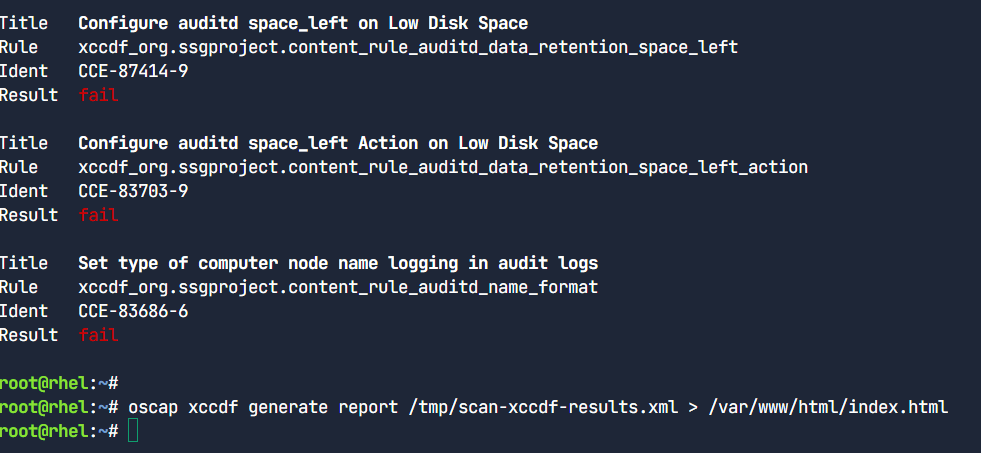
Now Let's see our result in HTML format
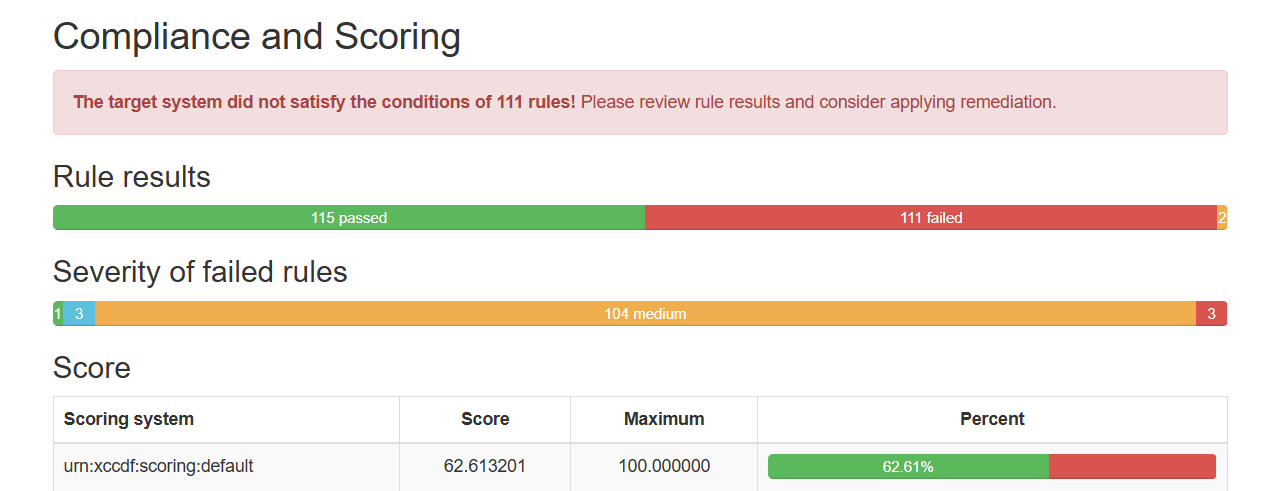
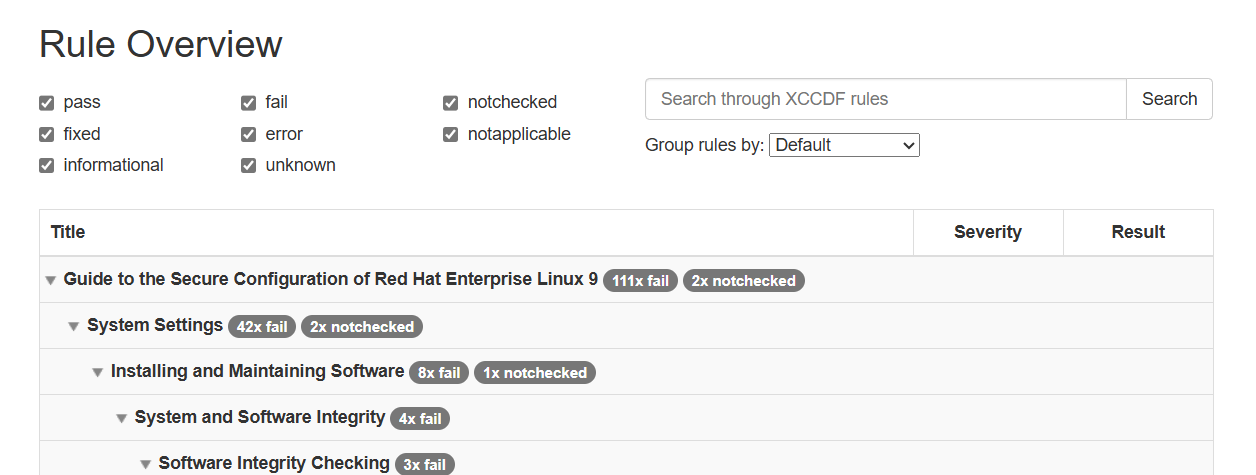
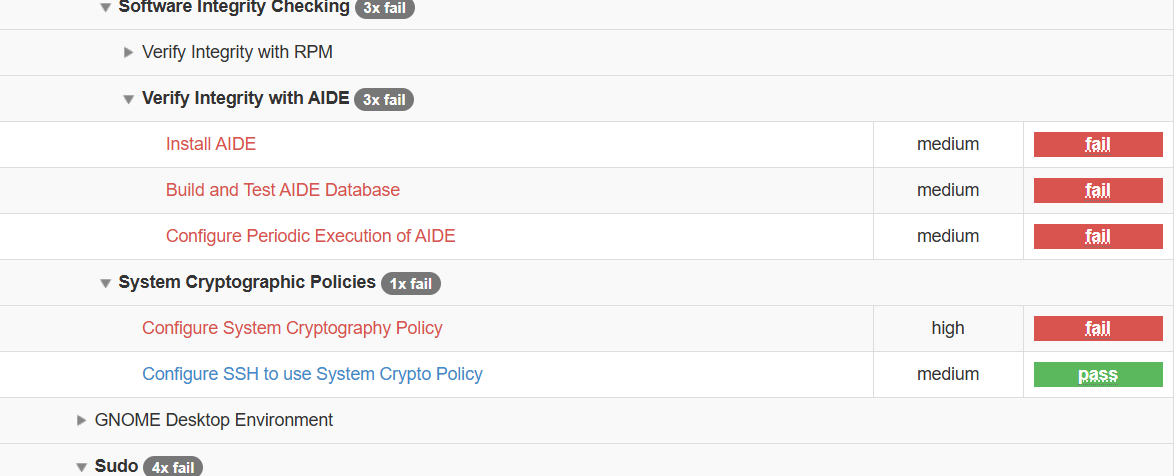
Step 4
Now let’s remediating and rescanning against a profile. One of the many failed rules in the scan previously done was related to IPSec support. In this step, we will remediate a single failed rule related to IPSec support.
It is really important to note that many of the remediations involve restarting the host to be effective.
Re-scan the host passing the --remediation option to carry out an online remediation. Additionally, provide the Rule ID from the previous step (xccdf_org.ssgproject.content_rule_package_libreswan_installed) to remediate the specific rule. If no Rule ID is provided, oscap attempts to remediate all the failed rules.
oscap xccdf eval --profile xccdf_org.ssgproject.content_profile_pci-dss --remediate --fetch-remote-resources --results scan-xccdf-results.xml --rule xccdf_org.ssgproject.content_rule_package_libreswan_installed /usr/share/xml/scap/ssg/content/ssg-rhel9-ds.xml
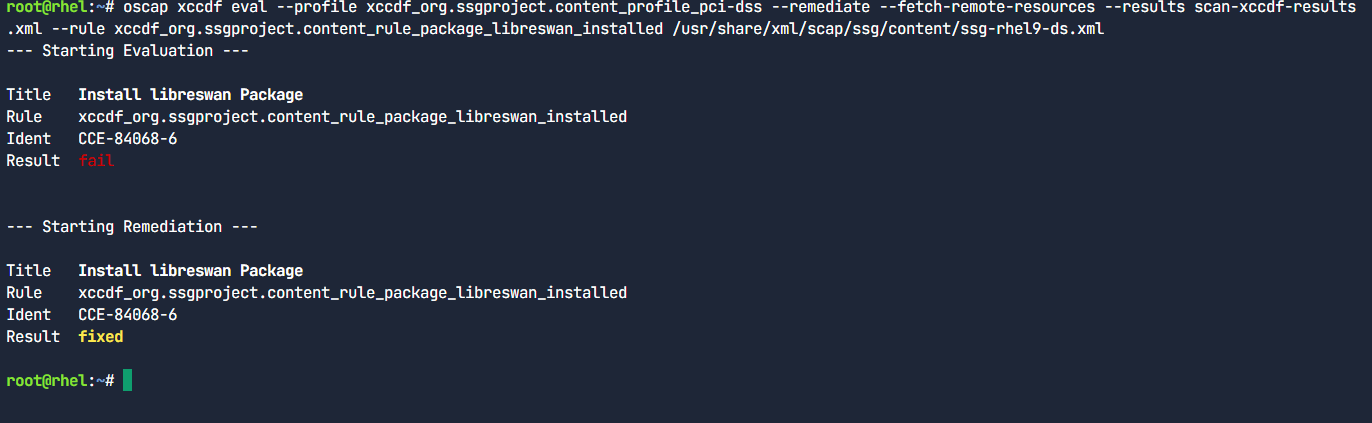
To verify that the issue is remediated, we have to re-run the previous command. Oscap only attempts to fix what is broken, so it will not remediate an already fixed rule.
oscap xccdf eval --profile xccdf_org.ssgproject.content_profile_pci-dss --remediate --fetch-remote-resources --results scan-xccdf-results.xml --rule xccdf_org.ssgproject.content_rule_package_libreswan_installed /usr/share/xml/scap/ssg/content/ssg-rhel9-ds.xml
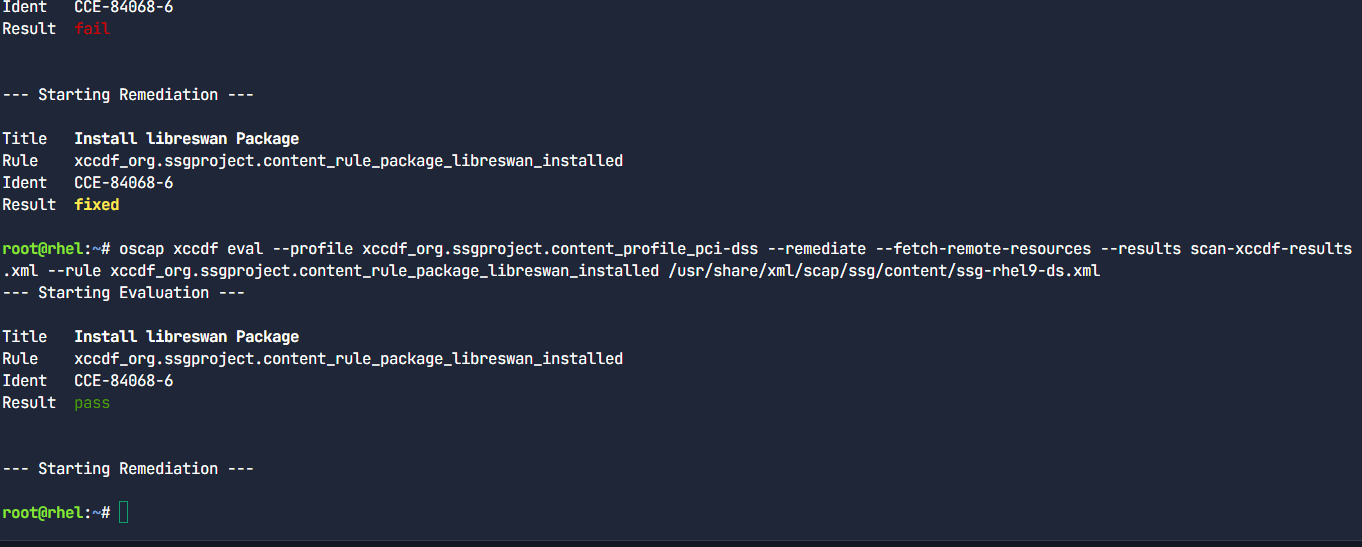
The remediation starts but there is no work left to be done.
And guest what ? We have done

Subscribe to my newsletter
Read articles from Yves Stanislas ADANI directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Yves Stanislas ADANI
Yves Stanislas ADANI
As a dedicated cybersecurity learner, trainer and professional with extensive expertise in vulnerability management, SIEM solution implementation, IAM administration, and security solution integration, I assist businesses in leveraging digital technologies to mitigate cyber risks and ensure compliance with regulatory standards such as PCI-DSS, SOX, and NIST Framework. In essence, I am a modern engineer with a perpetual learner, experienced, and a hands-on practitioner. I thrive on challenges and maintain a calm demeanor under pressure. I am known for fostering positive relationships with clients and stakeholders, and I consistently cultivate a positive and collaborative atmosphere around me. LET'S CONNECT !