The Risks of Publicly Disclosed ASP.NET Machine Keys in Code Injection Attacks
 FPT Metrodata Indonesia
FPT Metrodata Indonesia
Summary
Cyble Research Intelligence Lab (CRIL) came across insights provided by Microsoft regarding a ViewState code injection attack observed in December 2024. A threat actor used a publicly available ASP.NET machine key to inject malicious code and deliver the Godzilla post-exploitation framework, enabling remote code execution on IIS web servers. Microsoft found over 3,000 publicly disclosed keys online, posing significant risks. Organizations are advised to avoid using public keys and rotate them regularly to prevent such attacks.
Technical Details
In ASP.NET Web Forms, ViewState preserves the state of a webpage (such as form data) during postbacks. This data is stored in a hidden field and encoded in Base64 format. To protect this data from tampering or disclosure, the ASP.NET machine keys (ValidationKey and DecryptionKey) are used:
● ValidationKey: Generates a message authentication code (MAC) to verify data integrity.
● DecryptionKey: Encrypts ViewState to prevent unauthorized access.
How the Attack Works
When attackers gain access to a machine key (either through public repositories or compromised sources), they can craft a malicious ViewState payload and send it to the server using a POST request. Here’s how the attack proceeds:
Craft Malicious ViewState: Using the stolen machine key, the attacker builds a malicious ViewState payload.
POST Request: The payload is sent to the target server.
Server Execution: Since the server validates the ViewState using the correct keys, it processes the malicious code.
Remote Code Execution: The malicious code runs in the server’s memory, giving the attacker remote control over the server
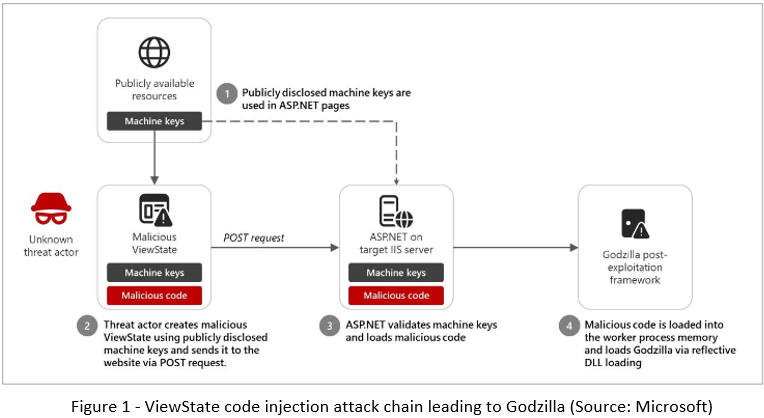
In the December 2024 attack, the threat actor used a publicly disclosed machine key to deliver a malicious ViewState payload, which reflectively loaded an assembly.dll file (SHA-256: 19d87910d1a7ad9632161fd9dd6a54c8a059a64fc5f5a41cf5055cd37ec0499d). This file is part of the Godzilla post-exploitation framework, which provides attackers with advanced capabilities, including:
● Executing arbitrary commands
● Injecting shellcode into processes
● Performing further post-exploitation tasks
Recommendations
We have listed some essential cybersecurity best practices that create the first line of control against attackers. We recommend that our readers follow the best practices given below:
● Always generate unique machine keys for each environment and avoid using publicly available keys from documentation or repositories. Regularly rotate your machine keys to reduce the risk of exposure, especially in web farm configurations where multiple servers share the same keys. Where possible, rely on auto-generated keys to minimize human error and potential key leakage.
● Protect critical information in configuration files, such as the machineKey and connectionStrings, by encrypting these elements in the web.config file. This ensures that sensitive data is not stored in plaintext, making it significantly harder for attackers to access secrets. Additionally, restrict access to these files and monitor them regularly for unauthorized changes.
● Ensure your applications are running on the latest version of ASP.NET, such as ASP.NET 4.8, to benefit from Antimalware Scan Interface (AMSI) integration, which enhances threat detection. Harden your Windows Servers by applying attack surface reduction rules, such as blocking webshell creation, and conduct regular security audits to detect and mitigate vulnerabilities.
Conclusion
The ViewState code injection attack demonstrates the serious risk posed by publicly disclosed ASP.NET machine keys. Attackers can exploit these keys to inject malicious code and gain remote code execution using tools like the Godzilla framework. This highlights the importance of securing machine keys, rotating them regularly, and avoiding keys from public sources.
Subscribe to my newsletter
Read articles from FPT Metrodata Indonesia directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

FPT Metrodata Indonesia
FPT Metrodata Indonesia
PT FPT Metrodata Indonesia (FMI) is a joint venture between FPT IS and Metrodata Electronics, focusing on providing Cybersecurity-as-a-Service—including SOC, managed security, professional services, consulting, and threat intelligence—to support Indonesia’s rapidly growing digital economy. FMI is expanding into AI and cloud GPU services to deliver innovative protection and solutions for enterprises. Learn more at https://fmisec.com.