Understanding the Open Systems Interconnection (OSI) Model
 Aniket Datta
Aniket DattaThe Open Systems Interconnection (OSI) model is a conceptual framework created by the International Organization for Standardization. It allows different communication systems to interact using standard protocols. Simply put, the OSI provides a standard that lets different computer systems communicate with each other.
The OSI Model acts like a universal language for computer networking. It divides a communication system into seven abstract layers, each building on the previous one.
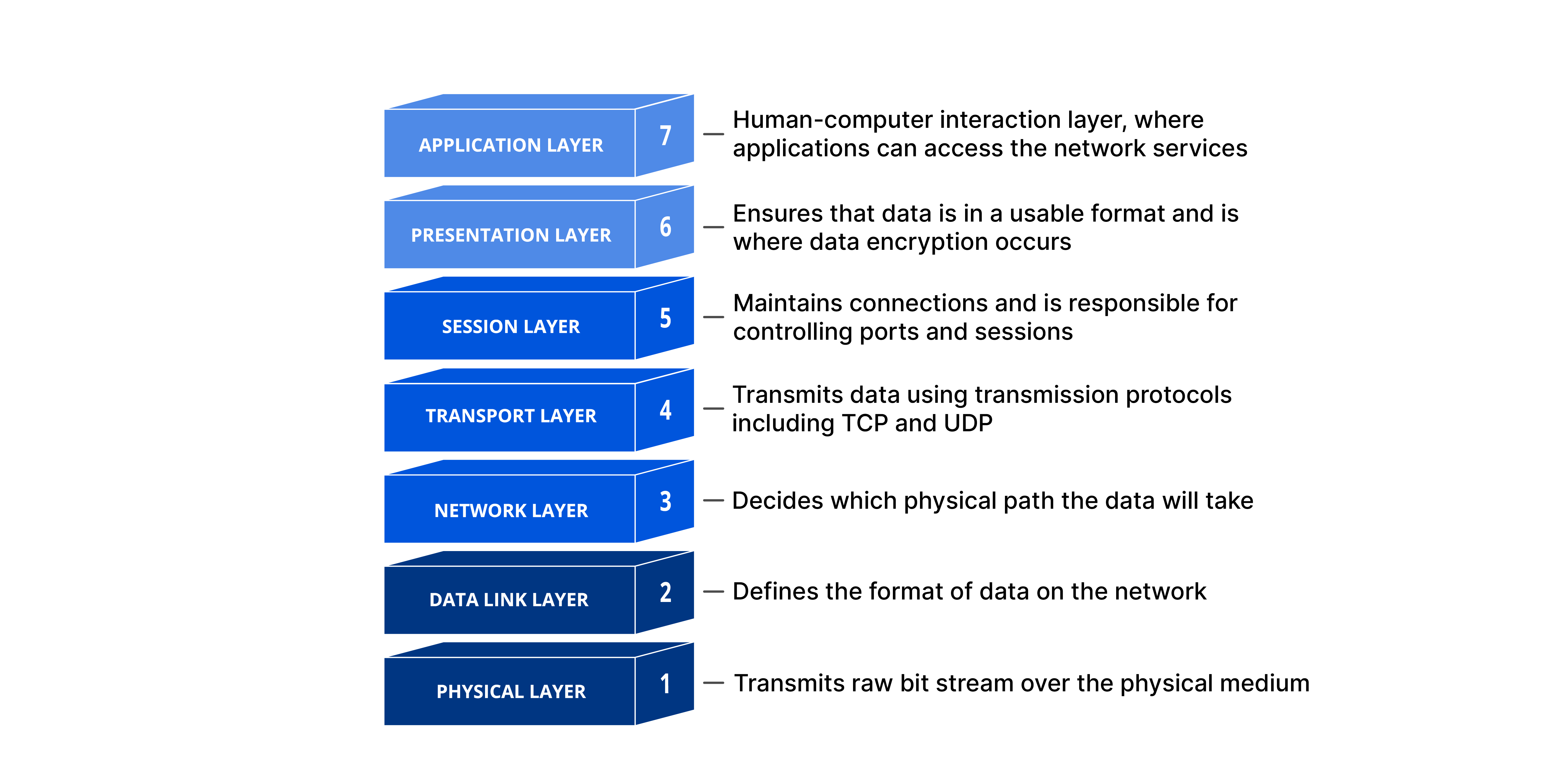
Each layer of the OSI Model has a specific role and communicates with the layers above and below it. DoS attacks target specific layers of a network connection; application layer attacks focus on layer 7, while protocol layer attacks target layers 3 and 4.
Although the modern Internet doesn't strictly follow the OSI Model (it more closely follows the simpler Internet protocol suite), the OSI Model is still very useful for troubleshooting network problems. Whether it's one person who can't connect their laptop to the Internet or a website that's down for thousands of users, the OSI Model can help break down the problem and pinpoint the source of the issue. By narrowing the problem down to a specific layer of the model, a lot of unnecessary work can be avoided.
7. The application layer
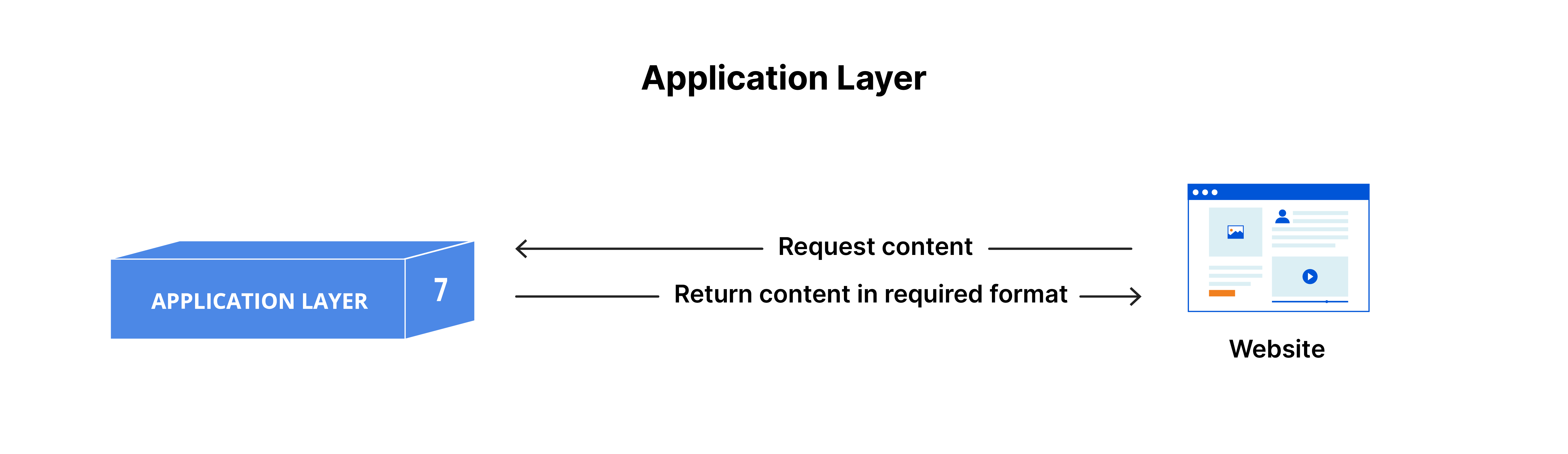
This is the only layer that directly interacts with data from the user. Software applications like web browsers and email clients use the application layer to start communications. It's important to note that client software applications are not part of the application layer; instead, the application layer handles the protocols and data processing that the software uses to present meaningful data to the user.
Application layer protocols include HTTP and SMTP (Simple Mail Transfer Protocol, which is one of the protocols that enables email communications).
6. The presentation layer
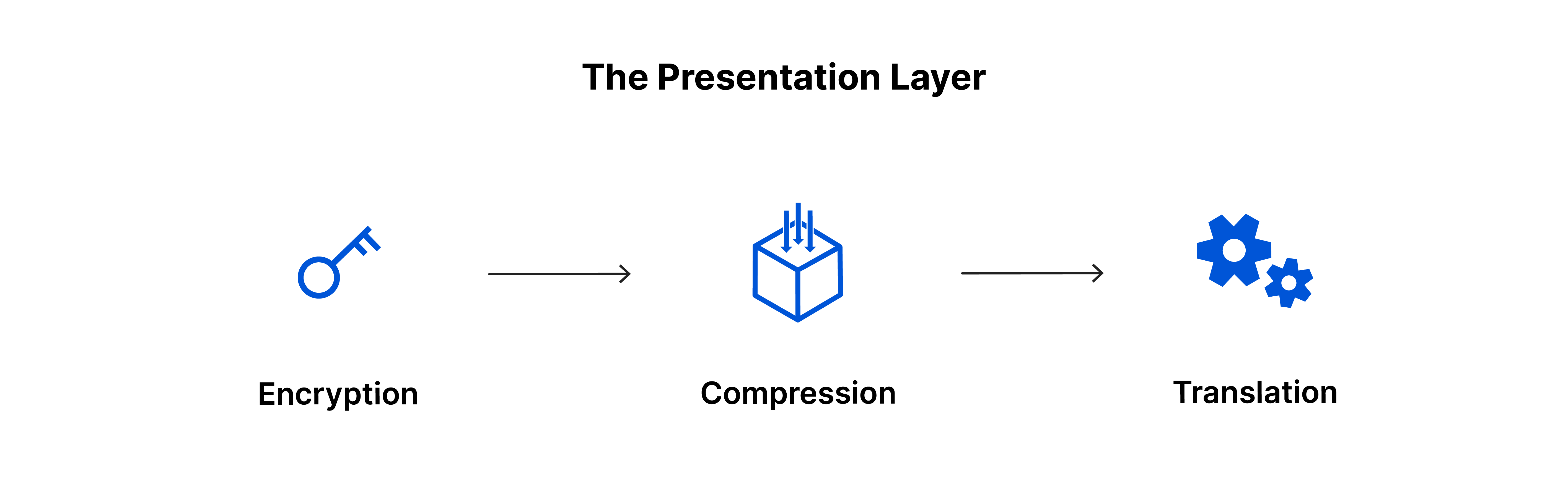
This layer mainly prepares data for use by the application layer; in other words, layer 6 makes data ready for applications to use. The presentation layer handles translation, encryption, and data compression.
When two devices communicate, they might use different encoding methods. Layer 6 translates incoming data into a format that the application layer of the receiving device can understand.
If the devices communicate over an encrypted connection, layer 6 adds encryption on the sender’s end and decodes it on the receiver's end, providing the application layer with unencrypted, readable data.
Finally, the presentation layer compresses data it receives from the application layer before passing it to layer 5. This improves communication speed and efficiency by reducing the amount of data transferred.
5. The session layer
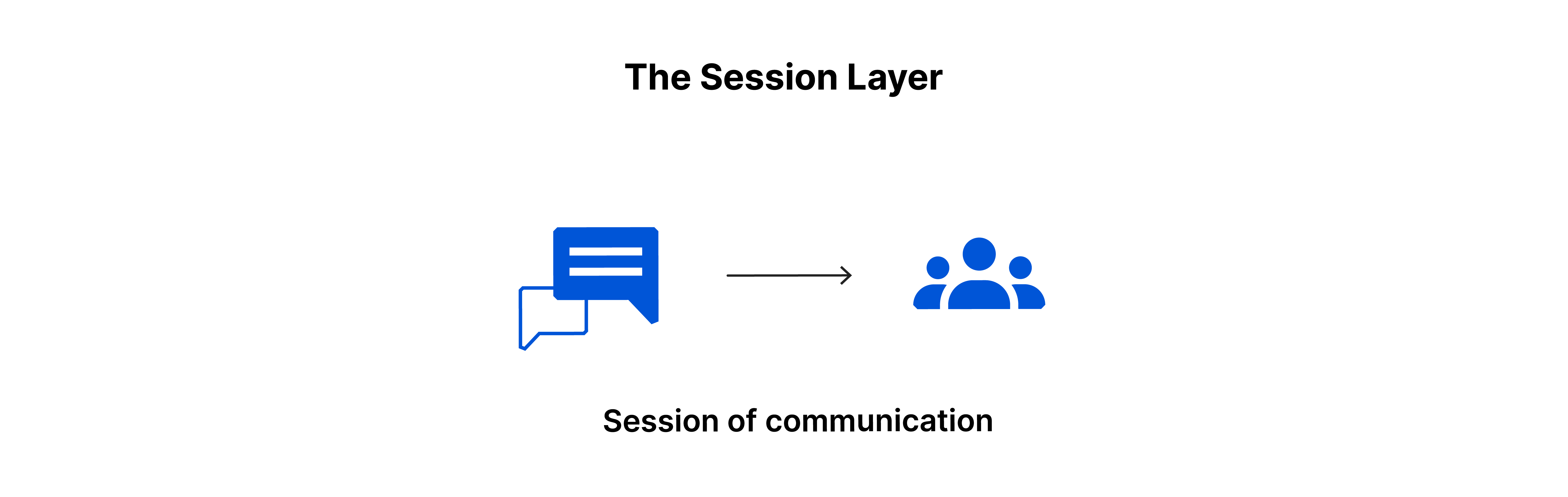
This layer is responsible for starting and ending communication between two devices. The period from when communication starts to when it ends is called the session. The session layer makes sure the session stays open long enough to transfer all the data and then closes it quickly to save resources.
The session layer also uses checkpoints to sync data transfer. For example, if a 100-megabyte file is being transferred, the session layer might set a checkpoint every 5 megabytes. If there is a disconnect or crash after 52 megabytes have been transferred, the session can resume from the last checkpoint, so only 50 more megabytes need to be transferred. Without checkpoints, the entire transfer would have to start over.
4. The transport layer
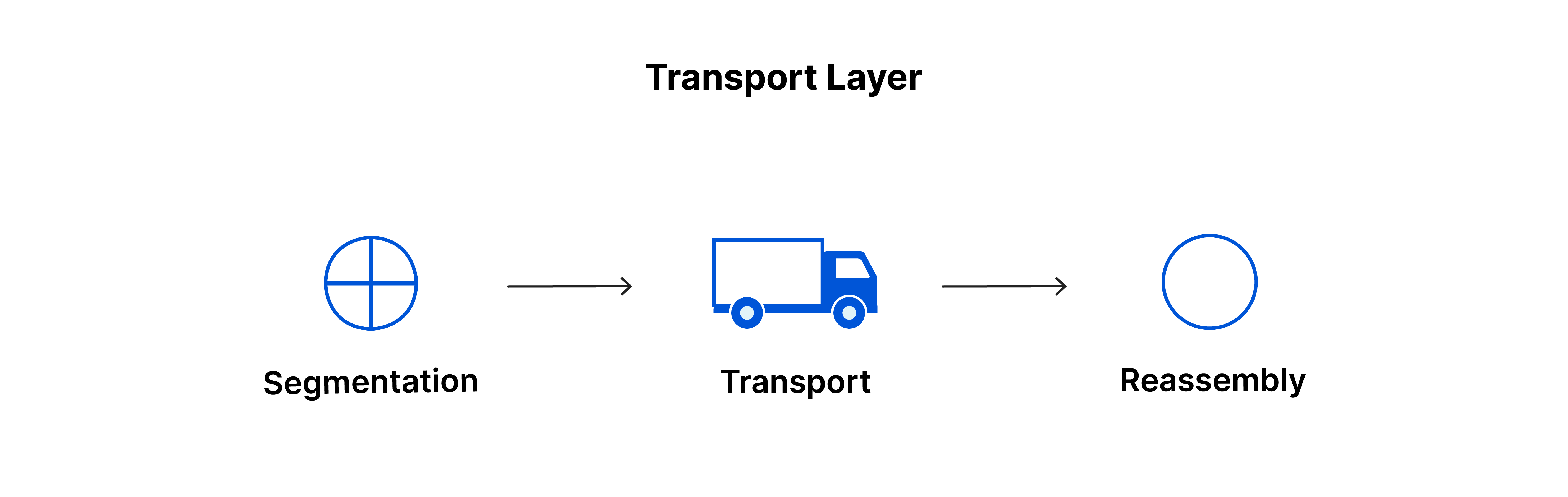
Layer 4 manages end-to-end communication between two devices. It takes data from the session layer and breaks it into smaller pieces called segments before sending it to layer 3. On the receiving device, the transport layer puts these segments back together into data that the session layer can use.
The transport layer also handles flow control and error control. Flow control sets the best transmission speed to prevent a fast sender from overwhelming a slow receiver. On the receiving side, error control checks if the data is complete and requests a retransmission if it's not.
Transport layer protocols include the Transmission Control Protocol (TCP) and the User Datagram Protocol (UDP).
3. The network layer
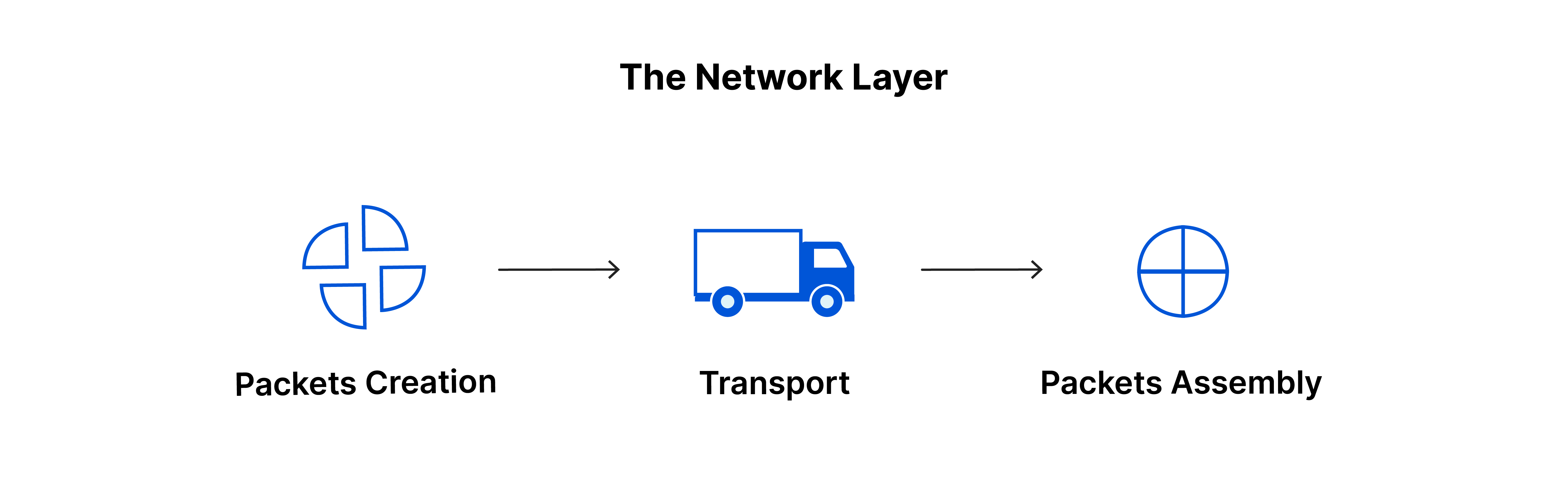
The network layer is responsible for allowing data transfer between two different networks. If the two devices communicating are on the same network, the network layer is not needed. It takes segments from the transport layer and breaks them into smaller units called packets on the sender’s device, then reassembles these packets on the receiving device. The network layer also decides the best physical path for the data to reach its destination, a process known as routing.
Network layer protocols include IP, the Internet Control Message Protocol (ICMP), the Internet Group Message Protocol (IGMP), and the IPsec suite.
2. The data link layer
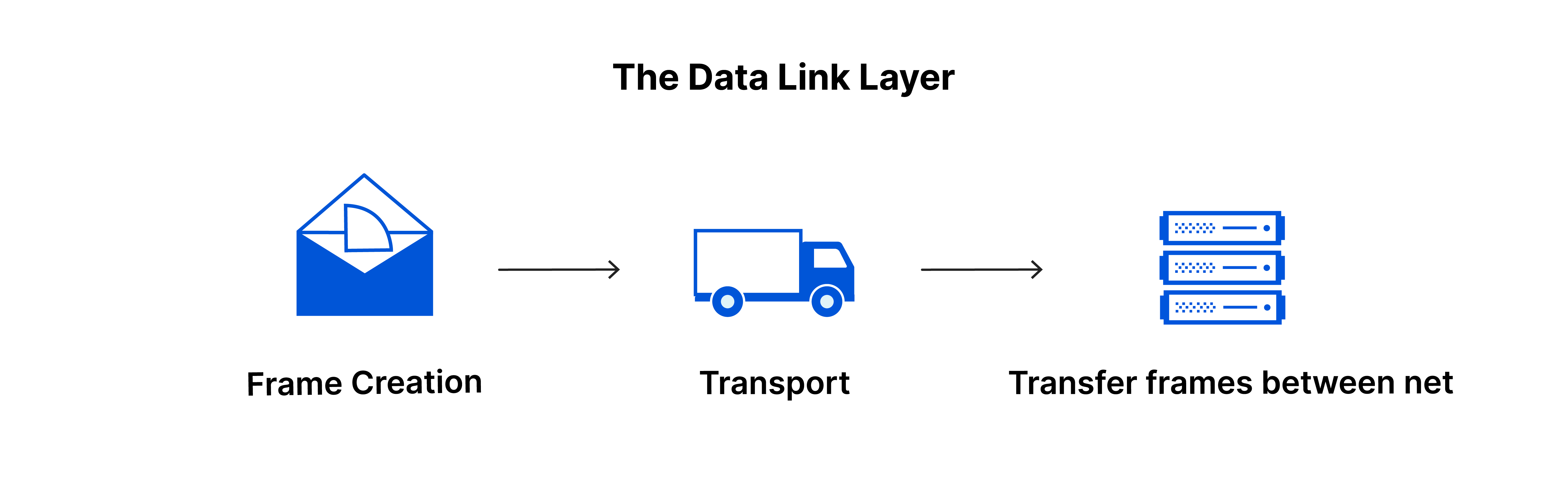
The data link layer is similar to the network layer, but it manages data transfer between two devices on the same network. It takes packets from the network layer and breaks them into smaller pieces called frames. Like the network layer, the data link layer also handles flow control and error control for communication within the same network, while the transport layer manages these for communication between different networks.
1. The physical layer
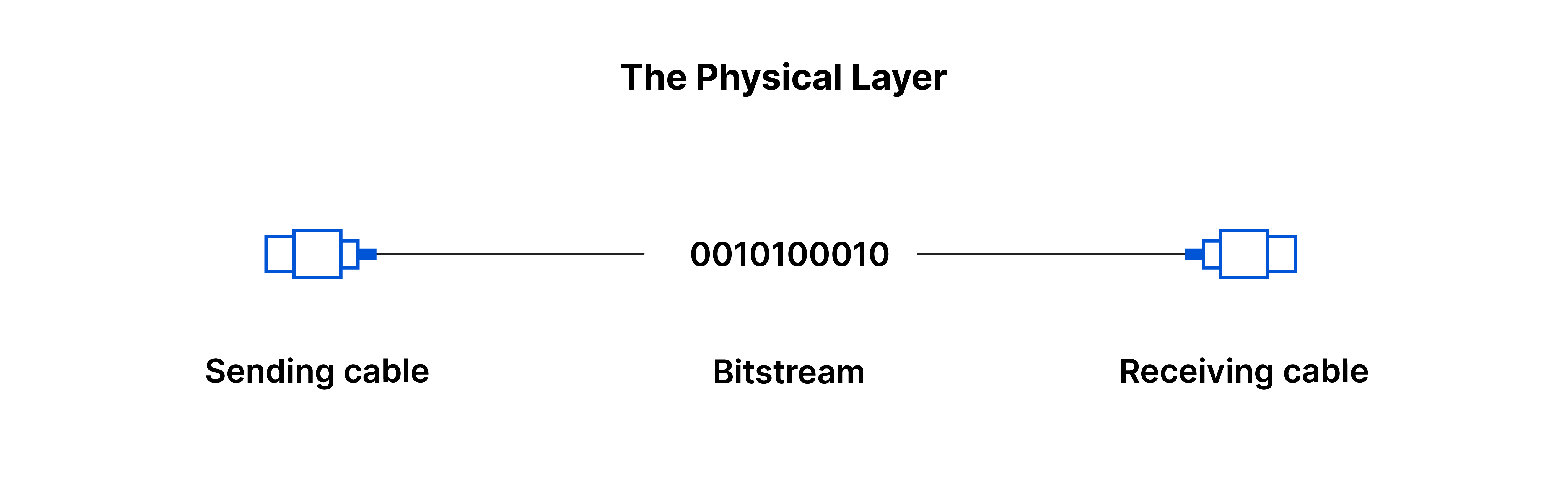
This layer includes the physical equipment used in data transfer, such as cables and switches. At this layer, data is converted into a bit stream, which is a series of 1s and 0s. Both devices' physical layers must agree on a signal convention to differentiate between the 1s and 0s.
Subscribe to my newsletter
Read articles from Aniket Datta directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Aniket Datta
Aniket Datta
Software Development ->Web Development AI/ML Development