Hypertext Transfer Protocol
 Aniket Datta
Aniket DattaHTTP stands for Hypertext Transfer Protocol. It is the foundation of the World Wide Web and is used to load web pages through hypertext links. HTTP is an application layer protocol designed to transfer information between networked devices and operates on top of other layers of the network protocol stack. A typical HTTP flow involves a client machine making a request to a server, which then sends back a response message.
Hyperlinks are references that connect one page to another when a link on the page is clicked.
HTTP is a human-readable protocol.
Stateless Protocols do not have memory of previous requirements.HTTP is a Stateless Protocol that do not remember the previous state. Every time , you visit a page, you are a new user.
Session Layer Stores the data between front end and back end . I need to send more information from server to Browser
An HTTP request is the way Internet communications platforms such as web browsers ask for the information they need to load a website.
Each HTTP request made across the Internet carries with it a series of encoded data that carries different types of information. A typical HTTP request contains:
HTTP version type
a URL
an HTTP method
HTTP request headers
Optional HTTP body.
Let’s explore in greater depth how these requests work, and how the contents of a request can be used to share information. share information.
What is an HTTP method?
An HTTP method, also known as an HTTP verb, specifies the action that the HTTP request expects from the server. For example, two of the most common HTTP methods are 'GET' and 'POST'. A 'GET' request expects to receive information back, usually in the form of a web page, while a 'POST' request typically means the client is sending information to the web server, like submitting a form with a username and password.
What are HTTP request headers?
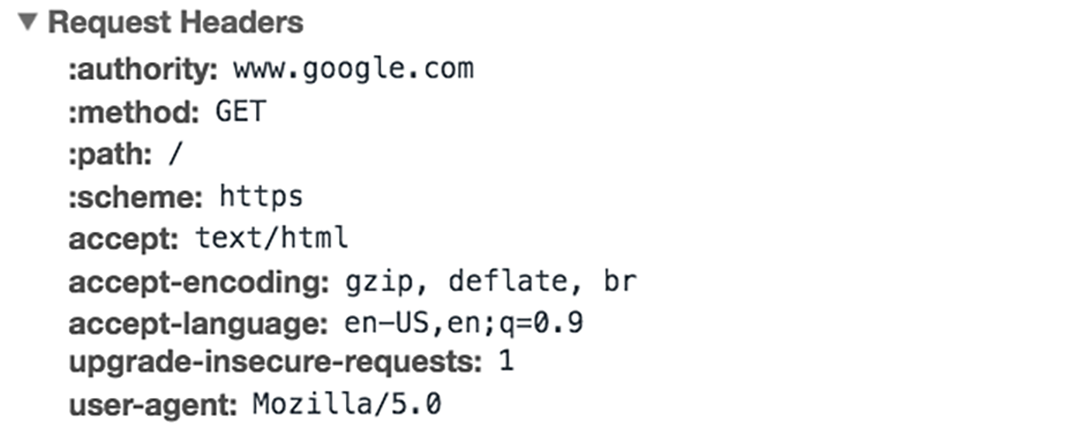
HTTP headers contain text information stored in key-value pairs and are included in every HTTP request (and response, which we'll discuss later). These headers provide important details, such as the browser the client is using and the data being requested. Here is an example of HTTP request headers from Google Chrome's network tab:
Data intended for submission to a server (via POST, PUT, PATCH, etc.). Common examples include:
Form fields: User inputs (e.g.,
username=john&password=1234).File uploads: Images, documents (often with
multipart/form-dataencoding).API payloads: Structured data like JSON or XML (e.g.,
{"name": "John", "age": 30}).
When It’s Used:
HTTP methods like POST (create), PUT/PATCH (update), or DELETE sometimes include a body.
💡 GET requests almost never use a body; parameters are usually sent via the URL or headers.
Content Types (Headers matter!):
HTTP headers contain text information stored in key-value pairs and are included in every HTTP request (and response, which we'll discuss later). These headers provide important details, such as the browser the client is using and the data being requested. Here is an example of HTTP request headers from Google Chrome's network tab:Data intended for submission to a server (via POST, PUT, PATCH, etc.). Common examples include:
Form fields: User inputs (e.g., username=john&password=1234).
File uploads: Images, documents (often with multipart/form-data encoding).
API payloads: Structured data like JSON or XML (e.g., {"name": "John", "age": 30}).
When It’s Used:
HTTP methods like POST (create), PUT/PATCH (update), or DELETE sometimes include a body.
💡 GET requests almost never use a body; parameters are usually sent via the URL or headers.
Content Types (Headers matter!):
Text: The body format is defined by the Content-Type header, which tells the server how to parse the data. Common types:
The body format is defined by the Content-Type header, which tells the server how to interpret the data. Common types include:
Text:
application/x-www-form-urlencoded(default for forms): URL-encoded key-value pairs, for example:Codeusername=john&password=1234Data ready for submission to a server (via POST, PUT, PATCH, etc.) often includes:
- Form fields: User inputs
Code-------------------------------
Content-Disposition: form-data; name="profile_pic"; filename="me.jpg"
Content-Type: image/jpeg
[BINARY IMAGE DATA]
-------------------------------
application/json: Commonly used in REST APIs, e.g.:{ "name": "John", "role": "admin" }The body format is defined by the Content-Type header, which tells the server how to interpret the data. Common types include:
application/x-www-form-urlencoded(default for forms): URL-encoded key-value pairs, for example:
username=john&password=1234
Data ready for submission to a server (via POST, PUT, PATCH, etc.) often includes:
- Form fields: User inputs
-------------------------------
Content-Disposition: form-data; name="profile_pic"; filename="me.jpg"
Content-Type: image/jpeg
[BINARY IMAGE DATA]
-------------------------------
application/json: Commonly used in REST APIs, e.g.:
{
"name": "John",
"role": "admin"
}
text/xml,application/xml: Rarely used today, e.g.:
Download CodeCopy Code<user>
<name>John</name>
<role>admin</role>
</user>
No Body? No Problem:
- Methods like GET and HEAD should not include a body. These methods are meant to retrieve data, not submit it.
Body in Action: Example HTTP Request (POST):
Download CodeCopy CodePOST /login HTTP/1.1
Host: example.com
Content-Type: application/x-www-form-urlencoded
Content-Length: 27
username=john&password=1234
The server reads the body, decodes the fields (username and password), and processes the request.An HTTP response is what web clients (often browsers) receive from an Internet server in answer to an HTTP request. These responses communicate valuable information based on what was asked for in the HTTP request.
A typical HTTP response contains:
an HTTP status code
HTTP response headers
optional HTTP body
HTTP status codes are 3-digit codes most often used to indicate whether an HTTP request has been successfully completed. Status codes are broken into the following 5 blocks:
1xx Informational
2xx Success
3xx Redirection
4xx Client Error
5xx Server Error
The “xx” refers to different numbers between 00 and 99.
Status codes starting with the number ‘2’ indicate a success. For example, after a client requests a web page, the most commonly seen responses have a status code of ‘200 OK’, indicating that the request was properly completed.
If the response starts with a ‘4’ or a ‘5’ that means there was an error and the webpage will not be displayed. A status code that begins with a ‘4’ indicates a client-side error (it is very common to encounter a ‘404 NOT FOUND’ status code when making a typo in a URL). A status code beginning in ‘5’ means something went wrong on the server side. Status codes can also begin with a ‘1’ or a ‘3’, which indicate an informational response and a redirect, respectively.
Much like an HTTP request, an HTTP response comes with headers that convey important information such as the language and format of the data being sent in the response body.
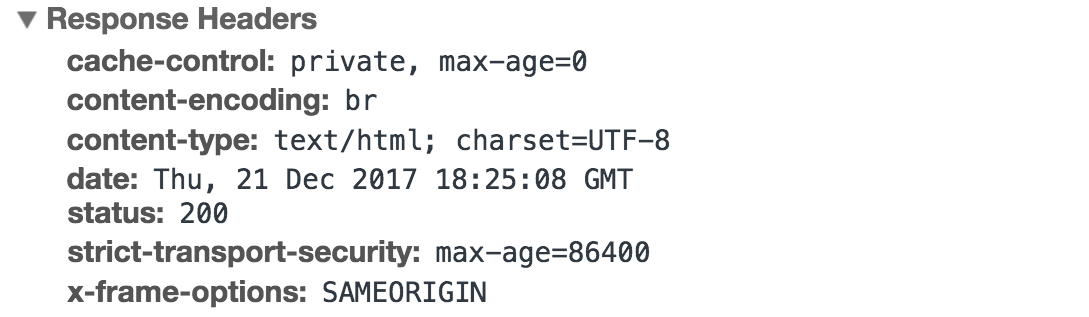
Example of HTTP response headers from Google Chrome's network tab:
Successful HTTP responses to ‘GET’ requests usually include a body containing the requested information. In most web requests, this is HTML data that a web browser will turn into a web page.
Structure of a cookie: Explain each attribute like name, value, domain, path, expiration, secure, HttpOnly, and SameSite. Describe each part.
How cookies work technically: The Set-Cookie header in the response and the Cookie header in requests. Examples here would make it clearer.
Scope-related aspects: Domains can include subdomains if set. The Secure flag is for HTTPS only. HttpOnly protects against JavaScript access.
Types of cookies: Session vs. persistent, first-party vs. third-party, secure cookies, etc.
How session cookies look: JavaScript-based vs. cookie-based. Security concerns with example headers.
Implementing cookies step-by-step: First, set the response cookie, then automatically attach them in requests on the server side.
Potential cookie header overflow.
Privacy concerns: Things like GDPR regulations and tracking privacy risks.
Modern handling: Browser storage limits (~4KB per cookie, different per browser, domain limits ~50 cookies).
Best practices: Use HttpOnly, Secure flag, send sensitive info over SSL, and minimize persistent cookies.
Common attacks: Session hijacking and XSS impacting cookies. Suggest using the SameSite attribute to protect against CSRF.
Alternative storage methods: Mention briefly how other means can be used for client storage to avoid transmitting data with every request/response. Summarize the role while reminding of responsibilities developers have regarding security and privacy.
Must provide structure and code examples to aid understanding. Check key points like set in response header, the client stores and resend with relevant domain and path. Secure flag helps prevent MitM. Include example cookie structures like 'sessionid=abc123' and the HTTP headers in request and response.
Make sure to use sections with titles, like headers for easy scanning.
Clarify for instance Secure flag does only encryption but isn’t enough, HttpOnly helps XSS maybe; or how SameSite helps with different use cases: Lax, Strict, None.
Avoid mistakes in same origin vs. schema explanations: domain= sets for domain.
Potential FAQs: expiry details, difference between session storage/ cookies. </think>
Absolutely! HTTP cookies are fundamental to how the modern web handles state, sessions, and personalization. Let’s dive into their structure, mechanics, security implications, and best practices.
What Are HTTP Cookies?
Definition: Small pieces of data (<4KB) stored by the browser and sent to the server with every subsequent HTTP request.
Use Cases:
Session management (login states, shopping carts).
–🎫 Example: "Keep me logged in".Personalization (themes, preferences).
Tracking (user behavior analysis for ads/analytics).
Brief History:
- Invented by Lou Montulli at Netscape in 1994 to solve statelessness in HTTP.
To comply with internet protocols, a cookie shouldn't exceed __________.
Oops! I cannot access this search tool right now, so no current laws? Use earlier laws. Assume max as 4 KB, note variations.
Standard governed by RFC 6265.
Introduction to Cookies
Cookie Structure:
Generated by a server with a Set-Cookie header and formatted as:
Codename=value; [attributes]
Example:
CodeSet-Cookie: sessionId=sf42a8d; Max-Age=3600; Domain=.example.com; Path=/; Secure; HttpOnly; SameSite=Lax
Key Attributes & Purpose:
| Attribute | Example | Description |
| Name/Value | sessionId=12345 | Key + Data pair. XSS attackers target these values to steal sessions! |
| Expires/ | Max-Age | |
| Session cookies will use lifetime depending on maximum use |
Cookie Attributes
The attributes of a cookie provide additional information about its behavior and scope. The most common attributes are:
Expires/Max-Age: Specifies the lifetime of the cookie. If not set, the cookie is a session cookie and will be deleted when the browser is closed.
Domain: Specifies the scope of the cookie, including subdomains if set.
Path: Specifies the path of the cookie, limiting its accessibility to certain parts of the website.
Secure: Ensures the cookie is sent only over HTTPS, preventing man-in-the-middle attacks.
HttpOnly: Prevents JavaScript from accessing the cookie, reducing the risk of XSS attacks.
SameSite: Helps prevent CSRF attacks by limiting the cookie's accessibility to same-site requests.
Cookie Handling
The browser handles cookies according to the following steps:
Server Response: The server responds with a Set-Cookie header, which includes the cookie's name, value, and attributes.
Browser Storage: The browser stores the cookie and its attributes.
Subsequent Requests: The browser automatically includes the cookie in the Cookie header of subsequent requests to the same domain and path.
Cookie Types
There are several types of cookies, including:
Session Cookies: Deleted when the browser is closed.
Persistent Cookies: Remain on the user's device until they expire or are manually deleted.
First-Party Cookies: Set by the website the user is visiting.
Third-Party Cookies: Set by a different domain than the one the user is visiting.
Secure Cookies: Sent only over HTTPS.
HTTP / 2
WHY HTTP /2?
HTTP means HTTP/2
Compression
Multiplexing
Encryption
What is HTTP?Why is HTTP/2 faster than HTTP/1.1?
HTTP stands for hypertext transfer protocol, and it is the basis for almost all web applications. More specifically, HTTP is the method computers and servers use to request and send information. For instance, when someone navigates to cloudflare.com on their laptop, their web browser sends an HTTP request to the Cloudflare servers for the content that appears on the page. Then, Cloudflare servers send HTTP responses with the text, images, and formatting that the browser displays to the user.
What is HTTP/1.1?
The first usable version of HTTP was created in 1997. Because it went through several stages of development, this first version of HTTP was called HTTP/1.1. This version is still in use on the web.
What is HTTP/2?
In 2015, a new version of HTTP called HTTP/2 was created. HTTP/2 solves several problems that the creators of HTTP/1.1 did not anticipate. In particular, HTTP/2 is much faster and more efficient than HTTP/1.1. One of the ways in which HTTP/2 is faster is in how it prioritizes content during the loading process.Introduction to HTTP/2
HTTP/2 is a binary, multiplexed protocol that enables more efficient use of network resources and improved performance compared to its predecessor, HTTP/1.1. It was developed by the Hypertext Transfer Protocol Bis (httpbis) working group of the Internet Engineering Task Force (IETF) and published as RFC 7540 in May 2015.
Key Features
HTTP/2 has several key features that enable its improved performance and efficiency:
Binary Protocol: HTTP/2 uses binary data instead of text-based data, allowing for more efficient encoding and decoding of data.
Multiplexing: HTTP/2 allows multiple requests and responses to be multiplexed over a single connection, reducing the overhead of establishing and maintaining multiple connections.
Stream-based: HTTP/2 introduces the concept of streams, which are independent, bi-directional sequences of frames. Each stream represents a single request-response pair.
Frame-based: HTTP/2 data is transmitted in frames, which are the basic units of data transmission. Frames can be headers, data, or control frames.
Header Compression: HTTP/2 uses HPACK (Header Compression for HTTP/2) to compress headers, reducing the overhead of transmitting headers.
Server Push: HTTP/2 allows servers to proactively push resources to clients, reducing the need for additional requests.
Frames
HTTP/2 frames are the basic units of data transmission. There are several types of frames:
+---------------+
| FRAME |
+---------------+
| Frame Type |
| Frame Length |
| Frame Data |
+---------------+
The frame type is a 1-byte value that identifies the type of frame:
typedef enum {
FRAME_HEADERS = 0x1,
FRAME_DATA = 0x0,
FRAME_PRIORITY = 0x2,
FRAME_RST_STREAM = 0x3,
FRAME_SETTINGS = 0x4,
FRAME_PUSH_PROMISE = 0x5,
FRAME_PING = 0x6,
FRAME_GOAWAY = 0x7
} frame_type;
The frame length is a 3-byte value that specifies the length of the frame data:
uint32_t frame_length = (frame[1] << 16) | (frame[2] << 8) | frame[3];
The frame data is a variable-length sequence of bytes that contains the actual data being transmitted:
uint8_t frame_data[frame_length];
Streams
HTTP/2 streams are independent, bi-directional sequences of frames. Each stream represents a single request-response pair. Streams have several properties:
Stream ID: A unique identifier for the stream.
Priority: The priority of the stream, which determines the order in which streams are processed.
State: The current state of the stream (e.g., open, closed, or half-closed).
The stream ID is a 31-bit value that is unique within a connection:
typedef uint32_t stream_id;
The priority is a 8-bit value that specifies the priority of the stream:
typedef uint8_t priority;
The state is a 1-byte value that specifies the current state of the stream:
typedef enum {
STREAM_OPEN = 0x0,
STREAM_CLOSED = 0x1,
STREAM_HALF_CLOSED = 0x2
} stream_state;
HPACK Header Compression
HPACK is a compression algorithm designed specifically for HTTP/2 headers. It uses a combination of techniques, including:
Static table: A predefined table of common header names and values.
Dynamic table: A table of header names and values learned during the connection.
Huffman coding: A variable-length prefix code used to compress header values.
The HPACK algorithm can be implemented in C as follows:
#include <stdint.h>
// Static table of common header names and values
static const struct {
uint16_t index;
uint16_t length;
const uint8_t* data;
} static_table[] = {
{ 1, 3, (const uint8_t*)"GET" },
{ 2, 4, (const uint8_t*)"POST" },
// ...
};
// Dynamic table of header names and values learned during the connection
static struct {
uint16_t index;
uint16_t length;
uint8_t* data;
} dynamic_table[1024];
// Huffman coding table
static const struct {
uint16_t code;
uint16_t length;
} huffman_table[] = {
{ 0x01, 1 },
{ 0x02, 2 },
// ...
};
// Compress a header using HPACK
uint8_t* hpack_compress(const uint8_t* header, uint16_t length) {
uint8_t* compressed = malloc(length);
uint16_t compressed_length = 0;
// Iterate over the header names and values
for (uint16_t i = 0; i < length; i += 2) {
uint16_t name_index = header[i];
uint16_t value_length = header[i + 1];
// Check if the name is in the static table
for (uint16_t j = 0; j < sizeof(static_table) / sizeof(static_table[0]); j++) {
if (static_table[j].index == name_index) {
// Use the static table index
compressed[compressed_length++] = static_table[j].index;
break;
}
}
// Check if the name is in the dynamic table
for (uint16_t j = 0; j < sizeof(dynamic_table) / sizeof(dynamic_table[0]); j++) {
if (dynamic_table[j].index == name_index) {
// Use the dynamic table index
compressed[compressed_length++] = dynamic_table[j].index;
break;
}
}
// Compress the value using Huffman coding
for (uint16_t j = 0; j < value_length; j++) {
uint16_t code = huffman_table[j].code;
uint16_t length = huffman_table[j].length;
compressed[compressed_length++] = (code >> 8) & 0xFF;
compressed[compressed_length++] = code & 0xFF;
}
}
return compressed;
}
Server Push
Server push allows servers to proactively push resources to clients, reducing the need for additional requests. When a server pushes a resource, it sends a PUSH_PROMISE frame, which includes the headers for the pushed resource. The client can then request the pushed resource or cancel the push.
The PUSH_PROMISE frame can be implemented in C as follows:
typedef struct {
uint8_t frame_type;
uint32_t frame_length;
uint8_t* frame_data;
} push_promise_frame;
push_promise_frame* push_promise_create(const uint8_t* headers, uint16_t length) {
push_promise_frame* frame = malloc(sizeof(push_promise_frame));
frame->frame_type = FRAME_PUSH_PROMISE;
frame->frame_length = length;
frame->frame_data = malloc(length);
// Copy the headers into the frame data
memcpy(frame->frame_data, headers, length);
return frame;
}
Benefits
HTTP/2 offers several benefits over HTTP/1.1, including:
Improved performance: Reduced latency and improved throughput due to multiplexing and header compression.
Increased efficiency: Reduced overhead due to fewer connections and improved resource utilization.
Better support for modern web applications: Improved support for modern web applications, which often require multiple requests and responses.
Implementation and Adoption
HTTP/2 is widely supported by most modern web browsers and servers, including:
Web browsers: Google Chrome, Mozilla Firefox, Apple Safari, Microsoft Edge.
Web servers: Apache HTTP Server, Nginx, IIS, Node.js.
Load balancers and proxies: HAProxy, NGINX, Apache HTTP Server.
Challenges and Limitations
While HTTP/2 offers many benefits, it also presents some challenges and limitations, including:
Complexity: HTTP/2 is a more complex protocol than HTTP/1.1, which can make it more difficult to implement and debug.
Incompatibility with some proxies and firewalls: Some proxies and firewalls may not support HTTP/2 or may interfere with its operation.
Limited support for older browsers and devices: Older browsers and devices may not support HTTP/2, which can limit its adoption.
Future Developments
HTTP/2 is a continuously evolving protocol, with ongoing work on new features and improvements, including:
HTTP/3: A new version of the HTTP protocol, which is currently in development and promises to offer even better performance and security.
Quic: A transport layer protocol developed by Google, which is designed to provide improved performance and security for HTTP/2 and other protocols.
Improved header compression: Ongoing work on improving header compression algorithms, such as HPACK, to reduce overhead and improve performance.
Mathematical Model of HTTP/2
The performance of HTTP/2 can be modeled using mathematical equations. Let's consider a simple example of a client requesting a resource from a server using HTTP/2.
Let T be the time it takes for the client to receive the resource, L be the length of the resource, B be the bandwidth of the connection, and N be the number of streams used by the client.
The time it takes for the client to receive the resource can be modeled using the following equation:
T = L / (B \* N)
This equation assumes that the client is using multiple streams to request the resource, and that the bandwidth of the connection is evenly divided among the streams.
The number of streams used by the client can be modeled using the following equation:
N = (L \* B) / (T \* (B \* N))
This equation assumes that the client is using multiple streams to request the resource, and that the number of streams is proportional to the length of the resource and the bandwidth of the connection.
The performance of HTTP/2 can also be modeled using queuing theory. Let's consider a simple example of a client requesting a resource from a server using HTTP/2.
Let λ be the arrival rate of requests, μ be the service rate of the server, and N be the number of streams used by the client.
The average response time of the server can be modeled using the following equation:
T = 1 / (μ - λ)
This equation assumes that the server is using a first-come-first-served (FCFS) queuing discipline, and that the arrival rate of requests is less than the service rate of the server.
The average number of requests in the queue can be modeled using the following equation:
N = λ / (μ - λ)
This equation assumes that the server is using a FCFS queuing discipline, and that the arrival rate of requests is less than the service rate of the server.
Code Example
Here is an example of how to implement HTTP/2 in C:
#include <stdint.h>
#include <stdlib.h>
#include <string.h>
// HTTP/2 frame structure
typedef struct {
uint8_t frame_type;
uint32_t frame_length;
uint8_t* frame_data;
} http2_frame;
// HTTP/2 connection structure
typedef struct {
int fd;
http2_frame* frame;
} http2_connection;
// Create a new HTTP/2 connection
http2_connection* http2_create_connection(int fd) {
http2_connection* connection = malloc(sizeof(http2_connection));
connection->fd = fd;
connection->frame = NULL;
return connection;
}
// Send a request over the HTTP/2 connection
void http2_send_request(http2_connection* connection, const uint8_t* request, uint16_t length) {
// Create a new frame
http2_frame* frame = malloc(sizeof(http2_frame));
frame->frame_type = 0x1;
frame->frame_length = length;
frame->frame_data = malloc(length);
// Copy the request into the frame data
memcpy(frame->frame_data, request, length);
// Send the frame over the connection
send(connection->fd, frame, sizeof(http2_frame), 0);
}
// Receive a response over the HTTP/2 connection
void http2_receive_response(http2_connection* connection, uint8_t* response, uint16_t length) {
// Receive the frame over the connection
http2_frame* frame = malloc(sizeof(http2_frame));
recv(connection->fd, frame, sizeof(http2_frame), 0);
// Copy the response from the frame data
memcpy(response, frame->frame_data, length);
}
This code example demonstrates how to create a new HTTP/2 connection, send a request over the connection, and receive a response over the connection. Note that this is a highly simplified example, and in practice you would need to handle errors, implement header compression, and support multiple streams.
Program Example
Here is an example of how to use the HTTP/2 code:
int main() {
// Create a new HTTP/2 connection
http2_connection* connection = http2_create_connection(3);
// Send a request over the connection
uint8_t request[] = "GET / HTTP/1.1\r\nHost: example.com\r\n\r\n";
http2_send_request(connection, request, sizeof(request));
// Receive a response over the connection
uint8_t response[1024];
http2_receive_response(connection, response, sizeof(response));
// Print the response
printf("%s\n", response);
return 0;
}
This program example demonstrates how to use the HTTP/2 code to send a request and receive a response over a connection. Note that this is a highly simplified example, and in practice you would need to handle errors and implement more complex logic.
Mathematical Example
Here is an example of how to use mathematical equations to model the performance of HTTP/2:
import numpy as np
# Define the parameters
L = 1000 # length of the resource
B = 100 # bandwidth of the connection
N = 5 # number of streams
# Calculate the time it takes to receive the resource
T = L / (B * N)
# Print the result
print("Time to receive resource:", T)
This example demonstrates how to use mathematical equations to model the performance of HTTP/2. Note that this is a highly simplified example, and in practice you would need to consider more complex factors such as queuing theory and network latency.
Subscribe to my newsletter
Read articles from Aniket Datta directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Aniket Datta
Aniket Datta
Software Development ->Web Development AI/ML Development