Let’s Build Enterprise Cybersecurity Risk Assessment Using AI Agents
 Aniket Hingane
Aniket Hingane

TL;DR
I built an app that uses multiple AI agents (Security Architect, Risk Analyst, and Compliance Officer) to automatically review security proposals from different perspectives. The agents discuss the proposal together and generate a comprehensive security report. The code shows how to orchestrate multiple agents, manage their conversation, and present their findings through a clean web interface.
Introduction
Ever been stuck waiting for the security team to review your project? Or maybe you’re on that security team, drowning in review requests? I built a system that uses AI agents to speed up cybersecurity risk assessments. The agents work together like a real security team — each with their own expertise and perspective — to provide comprehensive reviews in minutes instead of days.
What’s This Article About?
This article walks through building an AI-powered security review system. I’ve created a Streamlit application where users can submit security proposals for analysis. Behind the scenes, a team of specialized AI agents works together to assess the proposal:
A Security Architect examines technical vulnerabilities and suggests controls
A Risk Analyst evaluates business impacts and quantifies potential losses
A Compliance Officer checks for regulatory adherence to standards like GDPR and HIPAA
These agents have a structured conversation, challenge each other’s perspectives, and ultimately produce a comprehensive security recommendation. The application then formats this into a downloadable report that summarizes their findings.
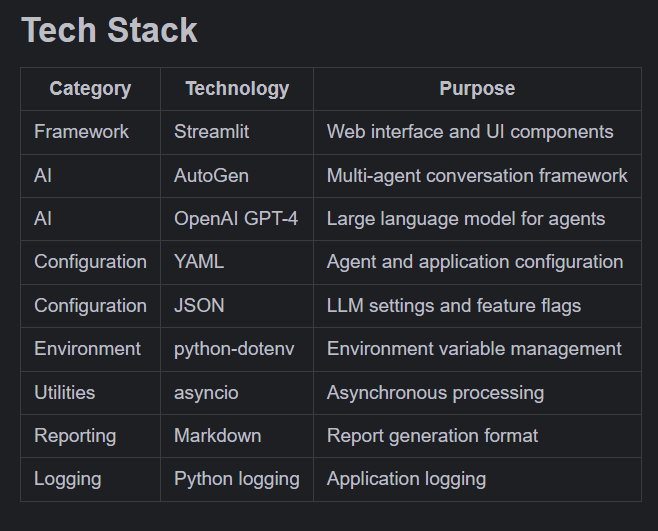
Tech stack
Why Read It?
AI is transforming how businesses handle cybersecurity. According to Gartner, by 2026, organizations using AI in security will respond to incidents 80% faster than those that don’t. This article shows how even fictional companies like our “Enterprise Cyber AI Council” can implement AI agents to:
Scale security expertise across the organization
Standardize risk assessment processes
Dramatically reduce review turnaround times
Ensure consistent consideration of technical, business, and compliance perspectives
The approach demonstrated here can be adapted to your own organization’s security frameworks and risk appetite. By building this system, you’ll learn practical techniques for orchestrating AI agents that can be applied to many business processes beyond security.
Subscribe to my newsletter
Read articles from Aniket Hingane directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
