Hashing for Beginner Developers part I
 ritiksharmaaa
ritiksharmaaa
Introduction
Security in web development and computer science revolves around ensuring data confidentiality, integrity, and authenticity. Developers often come across terms like hashing, encryption, and digital signatures. These concepts play a crucial role in securing data, but understanding their practical applications can be confusing. This article aims to simplify hashing, its uses, and how it works under the hood by providing clear explanations and real-world examples to help beginner developers grasp these essential concepts.
What is the difference between hashing and encryption?
Whenever you attend a lecture or engage in a conversation about digital security, you frequently hear terms like hashing, encryption, and digital signatures. These are fundamental concepts in cybersecurity and data protection. While encryption ensures confidentiality and digital signatures verify authenticity, hashing plays a key role in data integrity and efficient data retrieval. Unlike encryption, which is reversible with a decryption key, hashing is a one-way process, meaning the original data cannot be retrieved from the hash. This makes hashing useful for storing sensitive information, verifying file integrity, and indexing data efficiently.
A Brief History of Hashing
Hashing was first introduced in the 1950s as a method for efficiently retrieving data from large datasets. It evolved with advancements in computing and became an essential component of cryptography. The concept was formalized with the introduction of algorithms like MD5 (1991) and SHA-1 (1993) by the National Security Agency (NSA). Over time, due to vulnerabilities in older algorithms, stronger hashing methods like SHA-256 and Argon2 were developed to enhance security. The increasing power of computational attacks has led researchers to develop even more secure hashing algorithms, ensuring that digital security keeps up with evolving threats.
What is Hashing?
If you search online or ask an AI assistant about hashing, you will likely come across the following key points:
Hashing is primarily developed for efficient data retrieval.
It converts input data into a fixed-length string (hash).
Even a minor change in input results in a drastically different hash (avalanche effect).
Hashing is a one-way process, meaning the original data cannot be derived from the hash.
It is widely used in cybersecurity, database indexing, and digital signatures.
How It Works

A hashing algorithm takes an input (e.g., password, file, or message) and generates a unique hash.
Even a small change in the input results in a completely different hash (avalanche effect).
Hashes cannot be reversed to get the original data.
How does hashing work in programming?
If you have learned any programming language, you might have encountered hash-based data structures. For example:
Python: Dictionary (
dict)JavaScript: Object (
{}) andMapJava: HashMap
C++: Unordered_map
How Hash-Based Functions Work Under the Hood
Hash-based data structures use hashing functions to efficiently store and retrieve data. Here's how it works:

Key Processing: When you insert data into a hash-based structure (like a dictionary or object), the key is passed through a hash function.
Hash Calculation: The function converts the key into a fixed-length hash value.
Index Mapping: The hash value determines where the data should be stored in memory.
Collision Handling: If multiple keys produce the same hash (collision), techniques like chaining or open addressing resolve the conflict.
Fast Retrieval: Hashing ensures that lookup operations occur in constant time (O(1)), making data access extremely efficient.
This process makes lookups, insertions, and deletions very fast, often with O(1) time complexity, making hashing one of the most efficient techniques in data structures.
Common Hashing Algorithms
Which hashing algorithm should you use?
Hashing algorithms differ based on their use cases and security levels. Here are some widely used ones:
MD5 (Message Digest Algorithm 5) – Deprecated due to security flaws and vulnerability to collision attacks.
SHA-1 (Secure Hash Algorithm 1) – Weak, no longer recommended for security-sensitive applications.
SHA-256 – Used in Bitcoin, SSL certificates, and digital signatures due to its strong security features.
bcrypt – Designed for password hashing; includes salting to prevent attacks like rainbow table attacks.
Argon2 – Modern and recommended for password security, designed to be memory-intensive to resist brute-force attacks.
SHA-3 & BLAKE3 – Advanced cryptographic hash functions designed to provide higher security than SHA-256.
For general security applications, SHA-256 is widely used, while for password hashing, bcrypt or Argon2 is preferred due to their added security layers.
Where is Hashing Used?
Hashing has various applications in computer science and cybersecurity:
Password Hashing: Secure storage of passwords (bcrypt, Argon2) prevents plaintext password leaks.
File Integrity Checks: Verifying file authenticity (SHA-256 in checksums) ensures no tampering has occurred.
Digital Signatures: Ensuring document authenticity, used in legal documents and online transactions.
Data Indexing: Efficient searching in databases speeds up queries and optimizes storage.
Blockchain Technology: Cryptographic hashing secures transactions and prevents double-spending.
CAPTCHAs & Authentication Tokens: Used to store secure session tokens and authentication details.
How Hashing Works with Examples
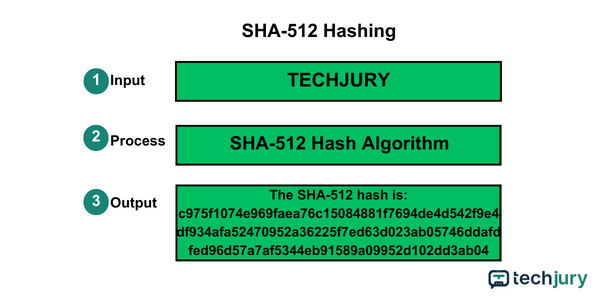
Hashing is about representing data uniquely. Let's explore this with an example.
Why does hashing change so much with a small input difference?
If you hash the word radha, it may look like this:
e9f61b083005d02bdeefc949c5ffcce3
This hash will always be the same, regardless of the system or operating system you use.
However, a small change, such as adding a space (rad ha), drastically changes the hash:
3a9f2190582580f60004e4733e9f9bc0
This phenomenon is known as the avalanche effect in hashing terminology.
Similarly, changing just one letter in a sentence results in a completely different hash:
"Radha is the only girl who knows how to behave well in class."
Hash: 88b6929983a6199ab4bcca3cc8e220aa
"radha is the only girl who knows how to behave well in class."
Hash: 25b97999f217c9180ae232607a13b8f8
This demonstrates that even small changes in input data result in completely different hash values, ensuring uniqueness and security.
Why Do We Have Multiple Hashing Algorithms?
Different hashing algorithms exist because some are more secure than others. If a hashing algorithm fails to create completely unique hashes for different data, it leads to collisions (when two different inputs produce the same hash).
What happens if two different inputs produce the same hash?
A hash collision occurs when two different inputs produce the same hash output. This is a significant security risk, as attackers can exploit collisions to forge digital signatures or certificates. Examples of real-world hashing collisions include:
SHAttered Attack (2017): Demonstrated a SHA-1 collision by generating two different PDF files with the same hash.

Flame Malware (2012): Used an MD5 collision to create a fake Microsoft security certificate.

Cryptographic Breaches: Weak hashes have been broken using modern GPU-powered attacks.
Due to these vulnerabilities, modern cryptographic systems prefer stronger algorithms like SHA-256, SHA-3, and BLAKE3.
Conclusion
Hashing is a fundamental concept in computing, essential for security, data integrity, and efficient data retrieval. Understanding how it works and its importance in password protection, digital signatures, and data indexing can help beginner developers implement secure systems.
What's next?
In upcoming articles, we will explore practical hashing implementations, real-world cryptographic applications, and how hashing is used in digital forensics. as well as salt based hashing for saving the password
Stay tuned for more insights into the world of cryptography! 🚀
Subscribe to my newsletter
Read articles from ritiksharmaaa directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

ritiksharmaaa
ritiksharmaaa
Hy this is me Ritik sharma . i am software developer