Understanding AWS Virtual Private Cloud (VPC): A Complete Guide
 Sai Praneeth
Sai Praneeth
Before jumping into VPC we need to know networking first, networking is connectivity, to access the server present in a remote location we need to have a network.
There are different types of networks :
Local Area Network ( LAN ) :
This can also be called INTRANET, We can create a network between the servers within my office/small building. We can use networking devices such as Switches, cables, routers, firewalls, etc., servers in LAN don’t need public IP or internet connection to talk to another server.
Wide Area Network ( WAN ) :
This can also be called an INTERNET, we can access google.com which is present outside the network, I only need internet connectivity and public IP to reach google.com, WAN allows businesses to connect multiple office locations or access cloud-based applications across regions.
Servers in the same network can talk to another without public IP and internet so that we can imagine it as our home network. We can control our TV, AC with our mobile as all these devices are connected to the same network, whereas the neighbor cannot control our TV as he is not part of the network.
We can SSH to the server present inside a VPC using a public IP.
What is VPC?
VPC stands for Virtual Private Cloud, it is our own private network inside Amazon’s cloud infrastructure.
It is an alternative to maintaining our own data center and it is cheaper since it creates resources on demand.
Resources in VPC are secure and we can decide who can access it.
Amazon will take care of the entire infrastructure and its security which makes our job easy.
In VPC we can control our virtual networking environment, IP address, creation of subnets, route tables, and Gateways.
VPC is regional and in a region, we can have 5 VPC’s.
We can create EC2, ELB, EFS, and S3 in my VPC and we can control them as per our requirements. We can define who can access and who cannot access using Security Groups and NACL ( Network Access Control List ).
Terminologies :
- Subnet :
Subnet means a small network inside a big network. We can have a VPC that spans across all the AZs as VPC is regional level. We can have one or more subnets in an AZ. Subnets cannot spread across AZ.
If a subnet has a route to AWS Internet Gateway it is called a Public Subnet.
If a subnet has no route to Internet Gateway then it is called a Private Subnet.
Security Groups work at the instance level whereas NACL works at the subnet level.

- Internet Gateway :
Only 1 IGW can be attached to a VPC. IGW cannot be detached from a VPC while there are active resources in the VPC. Without IGW the resources can talk to each other but not to the internet.
- Route Table :
It is a set of rules called routes that are used to determine where the network traffic is directed. Unlike and IGW, we can have multiple route tables in a VPC.
- CIDR ( Classless Inter-Domain Range ) :
CIDR is used to allocate IP addresses within a network. We will use CIDR blocks to mark a range of IP addresses for each subnet within a VPC.
While creating VPC we need to define our network range, basically IP range in the form of CIDR.
The CIDR has two components :
The base IP ( xx.xx.xx.xx )
The subnet Mask ( /16 )
If we define it as 172.31.0.16/16 → here this is VPC CIDR and it tells the range of our network.
The formula is 2 power 32 - 16, as we have /16 here., which comes to 65,536. So in our network, we can have these many IP addresses.
Similarly, if we have /24 we have 2 power 32 - 24 = 256, in our network we have 256 IPs.
RFC1918 Address :
RFC1918 address is an IP address that is assigned by an enterprise organization to an internal host. These IP addresses are used in private networks, which are not available or reachable from the internet.
RFC1918 address space includes the following networks :
10.0.0.0 - 10.255.255.255
172.16.0.0 - 172.31.255.255
192.168.0.0 - 192.168.255.255
As we are already running out of IP addresses, they came up with these so now all the private IPs will be in this range only. These IPs will act as private IPs and are reserved for private networks. So just by looking at the IP address, we can say whether it’s a public or private IP. These IPs are not reachable from the internet. We can have the same IPs used but for different networks.
So let’s say I have a network with 65536 IPs and person B can also have 65536 IPs in his network, I can use 192.168.0.0/16 even though this same CIDR can be used by person B for his VPC.
The subnet mask should be in the range of /16 ( 65,536 IPs ) and /28 ( 16 IPs).
If we have a VPC with CIDR block 10.0.0.0/24, we will get 256 IPs and we can break this into two subnets with 128 IPs each. One subnet can be 10.0.0.0/25 and another can be 10.0.0.128/25.
Among these 256 IPs, 5 of them are reserved. In each subnet, the first 4 and last IP will be reserved by the AWS.
.0 - network address
.1 - router
.2 - DNS
.3 - Future Use
.255 - Network Broadcast Address
If we don’t know how to break there are some online websites available that can help us to break the subnets, https://www.davidc.net/sites/default/subnets/subnets.html
So without defining the CIDR range, we cannot create a network, it tells how big our network is.
In a VPC we can have a maximum of 200 subnets, but in the case of a small network, we cannot have 200 subnets. For each subnet, we need to define CIDR and subnet mask. The subnet should be a subset of VPC CIDR.
Let’s see an example :
If we have VPC CIDR as 10.0.0.0/24
As the subnet mask is /24 we know the formula, 2 power 32-24 = 256 IPs, in total we have 256 IPs, if we need to break it into 4 subnets we can have it like this,
Subnet A - 10.0.0.0 to 10.0.0.63
Subnet B - 10.0.0.64 - 10.0.0.127
Subnet C - 10.0.0.128 - 10.0.0.192
Subnet D - 10.0.0.193 - 10.0.0.255
We can also break into 3 subnets, 2 subnets with 64 IPs and the last subnet with 128 IPs. It completely depends upon our requirements.
- NAT Gateway :
We can allow instances from the private subnet to connect to the internet using a NAT gateway. The instances in the private subnet do not have a public IP address, so the NAT gateway translates the private IP to a public IP before routing the traffic out to the internet. NAT stands for Network Address Translation, it translates private IPs to Public IP
Let’s say we have a 3 Tier application,
Web Layer: Usually Load Balancers will be present in this Web layer.
Application Layer: Where our application is present
DB Layer: Where our database is present
So for the outsiders to access we keep Load Balancers in the public subnet and Application, DB in the private subnet as we don’t need to expose these to the public. So our architecture looks like these.,
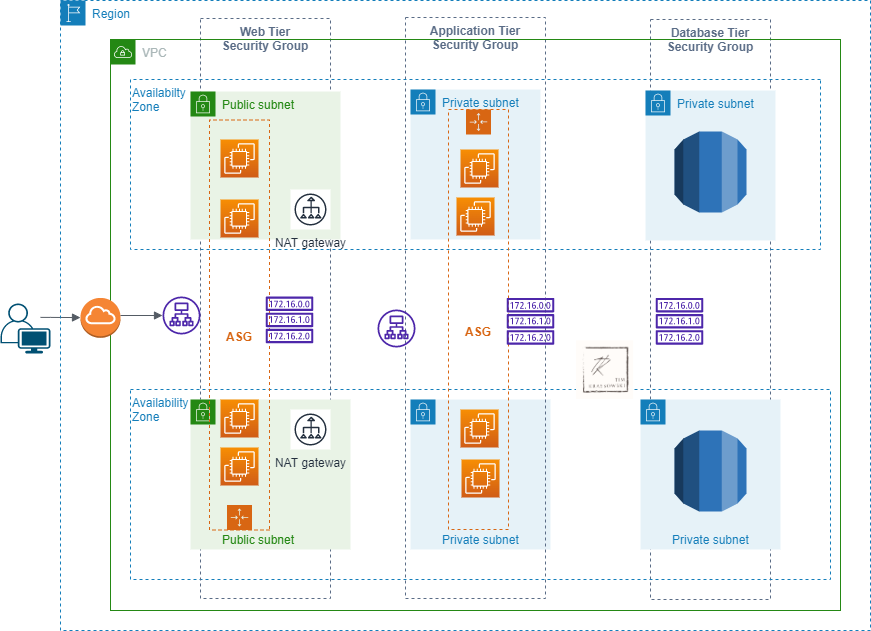
In the above picture, we can see DB sitting in a private subnet to limit access for outsiders and the same goes for the Application Servers.
The main use-case of NAT gateway is when resources in a private subnet try to access the network, we can reach the server from the internet only if these are satisfied –
Server should be in a public subnet
Subnet should have a route to IGW
Server should have a public IP
Server should have a Firewall Open
All these are not satisfied by the servers present in a private subnet, if we have an EC2 instance in private subnet and we need to do apt install git -y, if we do not have internet we cannot do updates/patching, here we need NAT gateway.
- Bastion Host :

The main purpose of Bastion host it when outsiders need to access resources in a private subnet, let’s say we have our application in a private subnet as we know outsiders ( people not belonging to the network ) cannot access it, to provide access we need to have an ec2 instance in a public subnet, this ec2 is called bastion host. We will SSH to this EC2 instance and from here with the help of the pem file we can connect to a private instance, this is the only way for the outsiders to connect. Bastion Host is also called a Jump Server.
In the next blog we will connect these dots and create a VPC
Subscribe to my newsletter
Read articles from Sai Praneeth directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
