Steganography: The Hidden Cyber Threat Inside Images
 Aditya
Aditya
Steganography: The Hidden Cyber Threat Inside Images
“What if I told you this innocent-looking cat image hides a secret?” 🐱
Steganography is not just a fun cybersecurity trick — it’s a serious cyber threat used by hackers to steal data, spread malware, and evade detection. In this blog, you’ll learn:
How hackers use images to attack you
All possible threats and real-world hacking cases
How to protect yourself from steganography-based attacks
Hands-on challenge: Extract a secret message from an image!
Let’s dive into this hidden cyber battlefield! 🚀
What is Steganography?
Steganography is the art of hiding information inside digital files (images, audio, videos) without making it look suspicious. Unlike encryption, where data becomes unreadable, steganography makes it invisible!
Original Image
Infected Image
The Second image looks the same, but a hacker may have hidden a malicious payload inside!
Steganography Using LSB (Least Significant Bit)
One of the most common methods is Least Significant Bit (LSB) steganography, which works by modifying the least significant bits of an image’s pixel values. Since these bits contribute very little to the overall color, altering them does not create noticeable changes in the image, making it an ideal method for covert communication.
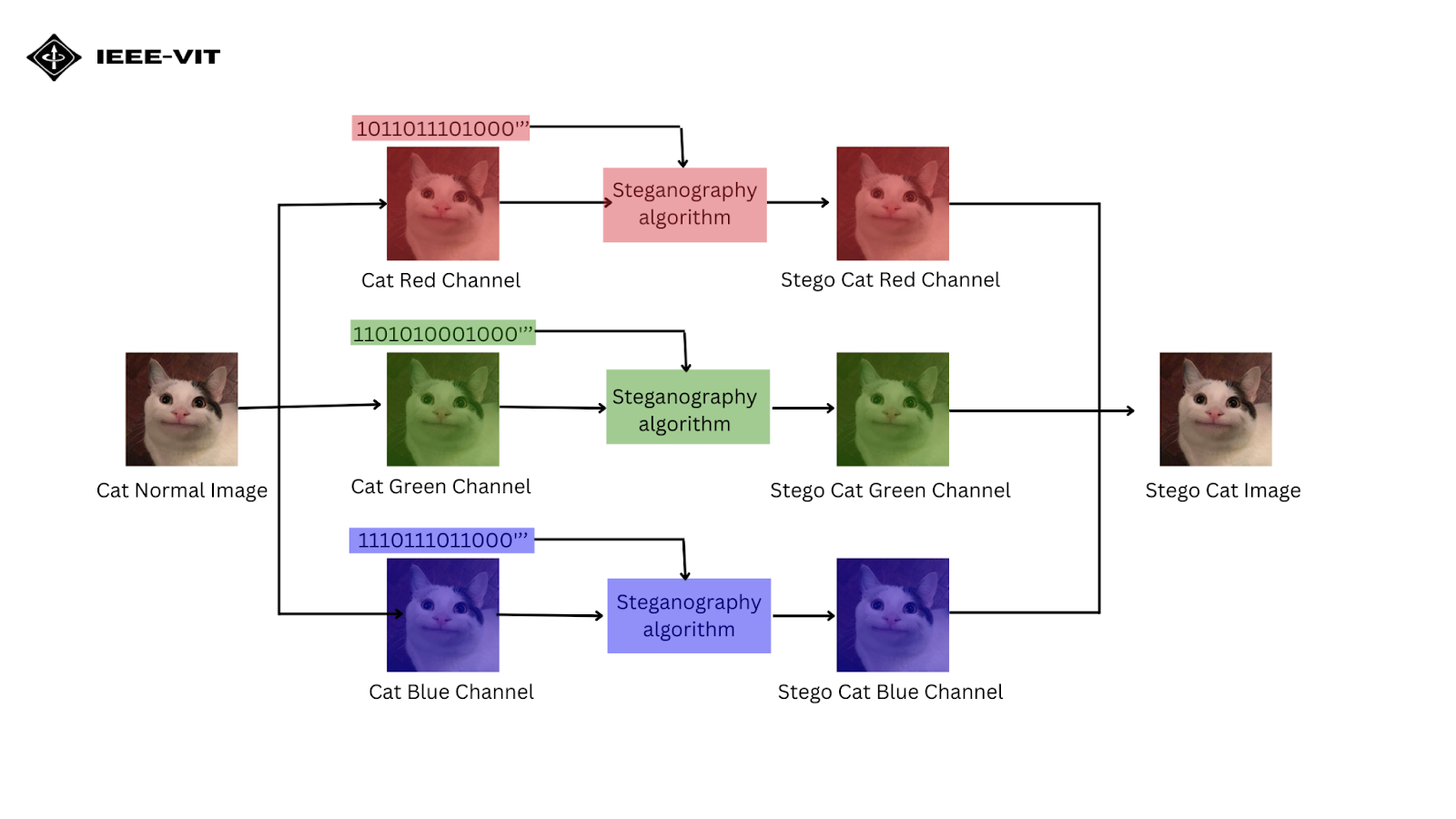
How Steganography Algorithm Works?
In the image above, the process is demonstrated step by step:
1️. The original image is separated into its Red, Green, and Blue (RGB) channels.
2️. The LSB of each pixel in every channel is modified to store secret binary data.
3️. The altered channels are then combined to form the stego image, which looks identical to the original but contains hidden data.
This method is widely used for secure communication, watermarking, and digital forensics, ensuring that sensitive data remains undetected in plain sight.
💀 How Hackers Use Steganography to Attack You ?
Cybercriminals abuse steganography in many dangerous ways:
1️. Malware Delivery 🦠
Hackers embed viruses inside images (JPG, PNG,JPEG) and send them via email, social media, or websites.
When you open/download the image, the malware executes silently, infecting your system.
Real-World Example:
🔹 In 2022, hackers used steganography to hide malicious code inside Instagram images, targeting users with remote access trojans (RATs).
**How to stay safe:
- Never download random images from unknown sources.
- Use antivirus software to scan images before opening.**
2️. Secret Data Theft
Employees or spies steal company secrets by hiding sensitive data in images and sending them via email or messaging apps.
Hackers use steganographic data exfiltration to steal passwords, credit card info, or military intelligence.
🔴 Real-World Example:
🔹 The Duqu 2.0 cyber espionage attack used image steganography to steal classified files from companies and governments.
**How to stay safe:
- Monitor unusual network traffic (large image uploads could be data leaks!).
- Use DLP (Data Loss Prevention) software to detect steganographic attacks.**
3️. Hiding Phishing & Exploits
Hackers send images that look normal but contain links to phishing websites or exploit codes that run in the background.
Clicking the image may redirect you to a malicious page that steals your login details.
🔴 Real-World Example:
🔹 In 2021, attackers used QR codes hidden in images to direct users to phishing sites and steal bank credentials.
**How to stay safe:
- Never click on suspicious images or QR codes.
- Use URL scanners to check for malicious links.**
4️. Evading Security Systems
Hackers communicate secretly by embedding messages, commands, or encryption keys inside images.
This bypasses firewalls & AI security detection since the image looks completely normal.
🔴 Real-World Example:
Cybercriminals used steganography in Telegram bot commands to control malware remotely without detection.
How to stay safe:
1. Monitor image file sizes — suspiciously large images may contain hidden data.
2. Use steganography detection tools (like StegExpose) to analyze images.
How to Protect Yourself from Steganography-Based Attacks
1. Don’t Trust Random Images
Never download images from unknown sources, shady websites, or email attachments.
2. Scan Images Before Opening
Use antivirus tools or image forensic scanners like:
1. StegExpose — Detects LSB-based steganography
2. ExifTool — Analyzes image metadata for hidden data
3. Monitor Your Network for Unusual Image Traffic
If someone in your organization is uploading large numbers of images, they might be hiding stolen data inside!
4. Use Sandboxing to Open Suspicious Images
Open unknown images inside a virtual machine (VM) to prevent malware from affecting your main system.
5. Train Employees & Users on Cybersecurity Awareness
Many steganographic attacks rely on social engineering. If you’re trained to spot suspicious images, you’re already one step ahead!
Steganography Challenge: Extract the Hidden Flag!
Now it’s YOUR turn! Can you find the hidden flag inside this cat image? 🐱
Step 1: Download the Image
Click here to download beluga.jpeg
Step 2: Inspect the Image
Start by checking if there’s any hidden data inside the image:
steghide info beluga.jpeg
Look for embedded files. If something is hidden, you’re on the right track!
Step 3: Extract the First Hidden Message
If there’s something hidden inside, try extracting it:
steghide extract -sf beluga.jpeg
🔑 Hint: You might need a password to unlock it. Think carefully—what could it be?
cat <filename>
⚠️ But beware—not everything you find is real. Some things are just there to troll you!
unzip <filename>.zip
🔑 Hint: The password was somewhere in the previous step.
cat <filename>
unzip <filename>.zip
If you made it here, you’re close to the real answer... or maybe, just maybe, you’ve been trolled all along. 😈🔥
Step 6: Dig Deeper
If you think you’ve found the flag, think again. Look closer at the data, and maybe try extracting something else.
💡 Hint: One secret leads to another. Use what you’ve found to uncover more!
Step 7: The Final Challenge
There’s something hidden that needs another method to extract. A certain file might require one more password before revealing the truth.
💡 Hint: Don’t trust the first thing you see. Keep digging until you’re sure you’ve got the right flag!
Did you find the flag? Drop it in the comments below! 🚀
What’s Next?
Follow These Resources To Learn more About Steganography:
1. Stego — Tools & Resources
3. NCLC Tools
Now that you’ve explored steganography, try: 1. Hiding your own messages inside images
- Detecting steganography in real-world files
- Exploring advanced steganography techniques
🕵️Steganography is a powerful tool — use it wisely!
🚀 Follow IEEE-VIT for more cybersecurity challenges! 🔥
Did you solve the challenge? Drop your answers below! ⬇️
Stay tuned for more hacking & security blogs! 🚀
Subscribe to my newsletter
Read articles from Aditya directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by