The OWASP Top 10: A Simple Guide to Common Security Risks
 Megha BL
Megha BL
Introduction
In the digital world, keeping applications secure is crucial. The OWASP Top 10 is a list of the most common security risks for web applications. Understanding these risks can help you protect your applications from cyber-attacks. Let's explore the OWASP Top 10 in simple terms.
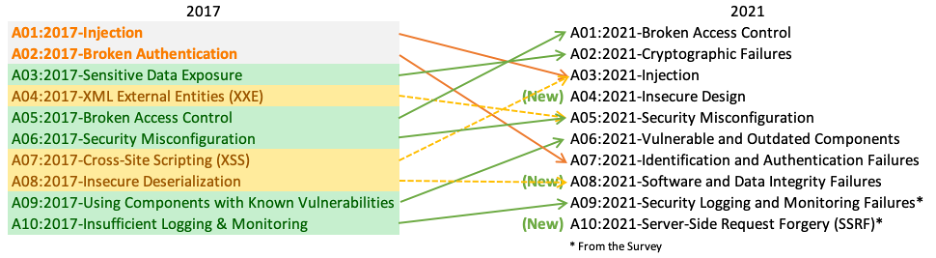
There are three new categories, four categories with naming and scoping changes, and some consolidation in the Top 10 for 2021.
1. Injection
Injection is like letting someone fill out a form with harmful data that messes up your system.
Detailed Explanation: This occurs when untrusted data is sent to an interpreter as part of a command or query. The attacker’s hostile data can trick the interpreter into executing unintended commands or accessing data without proper authorization.
Example: An attacker uses SQL injection to manipulate a query by entering malicious code into a login form, bypassing authentication, and gaining access to the database.
2. Broken Authentication
Broken authentication is like having weak locks on your doors, making it easy for intruders to get in.
Detailed Explanation: This happens when authentication mechanisms are implemented incorrectly, allowing attackers to compromise passwords, keys, or session tokens to assume the identity of other users.
Example: An attacker exploits weak password policies to guess or brute-force passwords and gain unauthorized access to user accounts.
3. Sensitive Data Exposure
Sensitive data exposure is like leaving your personal information out in the open for anyone to see.
Detailed Explanation: Sensitive data exposure occurs when applications do not adequately protect sensitive information, such as financial data, healthcare data, or personal identifiers. This can lead to data breaches and unauthorized access.
Example: An application stores credit card information in plain text, which is then stolen by an attacker through a data breach.
4. XML External Entities (XXE)
XXE is like letting an unknown guest into your house through a hidden door.
Detailed Explanation: XXE occurs when an XML parser improperly processes external entities within XML documents, allowing attackers to exploit vulnerabilities to access internal files, systems, or execute malicious code.
Example: An attacker crafts a malicious XML input containing external entity references that cause the application to expose internal files or network resources.
5. Broken Access Control
Broken access control is like giving everyone the keys to every room in your house.
Detailed Explanation: This happens when access control policies are not enforced, allowing unauthorized users to access restricted areas or perform actions they shouldn’t be able to.
Example: An attacker manipulates URL parameters to access restricted admin functionalities without proper authorization.
6. Security Misconfiguration
Security misconfiguration is like leaving your doors and windows unlocked.
Detailed Explanation: Security misconfiguration occurs when security settings are not defined, implemented, or maintained correctly. This can include default settings, unnecessary features, or unpatched vulnerabilities.
Example: An application uses default credentials for its admin panel, which are easily exploited by attackers.
7. Cross-Site Scripting (XSS)
XSS is like letting someone sneak a harmful note into your notebook.
Detailed Explanation: XSS occurs when an application allows untrusted data to be included in a web page without proper validation or escaping. This enables attackers to execute malicious scripts in the user’s browser.
Example: An attacker injects malicious JavaScript into a comment section, which is then executed when other users view the comment.
8. Insecure Deserialization
Insecure deserialization is like putting together a broken puzzle that can cause unexpected problems.
Detailed Explanation: Insecure deserialization occurs when untrusted data is used to instantiate objects, leading to the execution of arbitrary code or other attacks. This can lead to remote code execution, privilege escalation, and other security issues.
Example: An attacker manipulates serialized data to exploit vulnerabilities and execute malicious code on the server.
9. Using Components with Known Vulnerabilities
Using components with known vulnerabilities is like building a house with faulty materials.
Detailed Explanation: This happens when applications use libraries, frameworks, or other software components that have known security vulnerabilities. Attackers can exploit these vulnerabilities to compromise the application.
Example: An application uses an outdated version of a library with a known security flaw, which is then exploited by an attacker.
10. Insufficient Logging and Monitoring
Insufficient logging and monitoring is like having no security cameras to see what's happening.
Detailed Explanation: Insufficient logging and monitoring occur when security events and incidents are not properly logged or monitored, making it difficult to detect and respond to attacks.
Example: An attacker gains access to the system, but due to lack of logging and monitoring, the breach goes undetected for an extended period.
Understanding these risks and how they can impact your applications is crucial for building secure software. By addressing these vulnerabilities, you can better protect your applications and keep your data safe.
Subscribe to my newsletter
Read articles from Megha BL directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Megha BL
Megha BL
Security operation centre analyst | Vulnerability management and penetration testing (VAPT) | Qualys Compliance | Cloud security