IAM Roles: A 2-Minute Guide
 Vasudha Jha
Vasudha Jha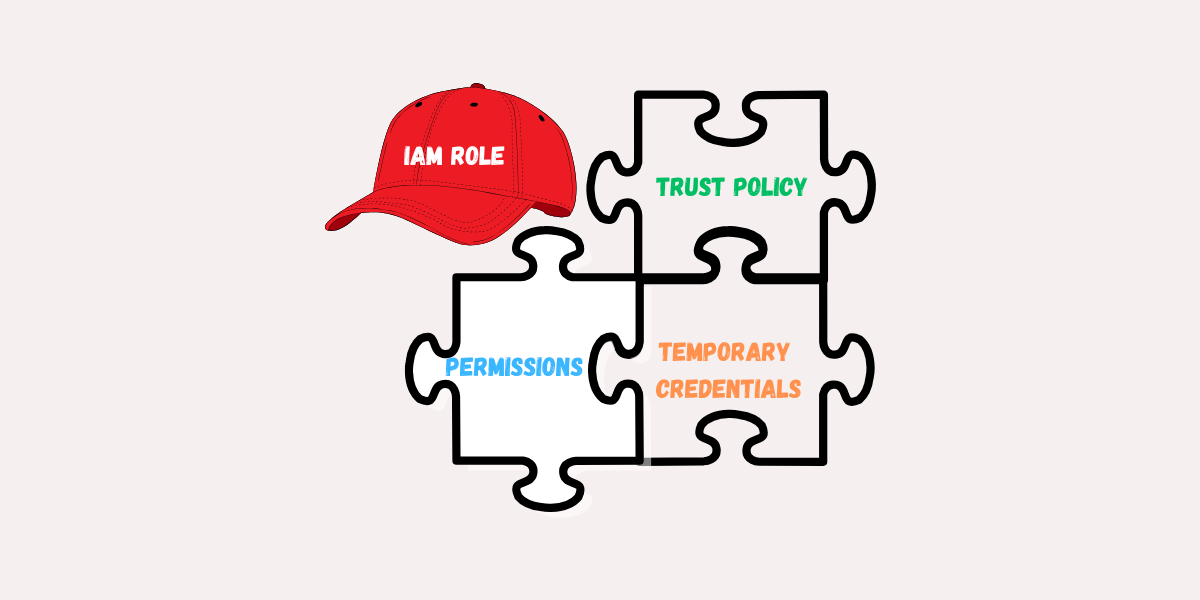
What’s an IAM Role?
An IAM Role is temporary access with specific permissions. Unlike an IAM user, it does not have long-term credentials. Instead, AWS grants temporary security credentials. Think of it like a visitor badge that allows access to certain areas but expires after a set time.
Let’s break it down with an example.
Imagine you have a Lambda function that needs to save logs in S3. Hardcoding AWS credentials would be a bad idea, but I’m sure you already know that. Instead, the right approach is to assign an IAM role that allows Lambda to write to S3.
Any IAM role has three key components you need to understand:
1. Trust Policy (Who Can Assume the Role?)
This tells AWS who is allowed to assume the role (in this case, Lambda):
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": { "Service": "lambda.amazonaws.com" },
"Action": "sts:AssumeRole"
}
]
}
This means only AWS Lambda can use this role.
Another key part of the trust policy is the Action field. The value "sts:AssumeRole" refers to AWS Security Token Service (STS), which allows a user, service, or AWS resource to temporarily assume the role and receive a short-lived set of credentials. These credentials can then be used to make authenticated AWS API requests within the permissions of the assumed role.
2. Permissions (What Can the Role Do?)
This grants permissions to write to an S3 bucket:
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Action": "s3:PutObject",
"Resource": "arn:aws:s3:::my-log-bucket/*"
}
]
}
3. Temporary Credentials (How Long Does it Last?)
When an IAM role is assumed, AWS generates temporary credentials:
Access Key ID
Secret Access Key
Session Token
These credentials expire after a set time (15 minutes to 12 hours).
AWS automatically refreshes them for services like Lambda, EC2, and ECS.
If you assume a role manually (via CLI or API), you must refresh it yourself.
After creating this IAM role, you must attach it to the Lambda function. The role exists independently, but Lambda won’t use it unless explicitly assigned.
Wrapping up
IAM Role = Who (Trust Policy) + What (Permissions Policy) + How Long (Temporary Credentials)
That’s it. You now understand IAM roles.
Want to take it a step further? How would you attach an IAM role to an EC2 instance? (Hint: Look into Instance Profiles).
Subscribe to my newsletter
Read articles from Vasudha Jha directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Vasudha Jha
Vasudha Jha
I love solving problems at the intersection of software development and cloud infrastructure. My journey started as a full-stack developer, building web and mobile applications, but I found myself drawn to automation, cloud scalability, and making deployments smoother. That led me to DevOps and Cloud Engineering, where I now focus on building reliable infrastructure, optimizing workflows, and automating deployments. Right now, I’m hands-on with AWS, Terraform, CI/CD pipelines, Docker and Ansible, working on projects that deepen my understanding of cloud automation and scalable infrastructure. I have found that the best way to learn is by building real things, debugging, and iterating along the way. 🔧 What I’m Currently Working On AWS Cloud Resume Challenge: Setting up a fully automated, serverless personal website on AWS. The core AWS services I'm using include S3, IAM, CloudFront, API Gateway, Lambda, and DynamoDB. I’m writing the infrastructure using Terraform and deploying code through GitHub Actions to ensure an automated, infrastructure-as-code approach. Here's the link to it if you'd like to give it a go: https://cloudresumechallenge.dev/docs/the-challenge/aws/ If you're still here, we probably have similar interests! Let’s connect and geek out over DevOps, cloud, and automation or anything tech-related!