Terraform Key Topics & Project Structure
 Venkat Teja Thota
Venkat Teja ThotaTerraform is an open-source tool by HashiCorp that lets you define, create and manage Infrastructure as Code. Using simple configuration language (HCL or JSON) we can manage resources across multiple platforms like AWS, Azure, GCP. It handles everything from low-level components like servers and networks to high-level resources like DNS and SAAS features, ensure infrastructure is consistent, versioned and automated.
Table of Contents
IaC (Infrastructure as Code)
Why Terraform?
Terraform Architecture
Providers
Provisioners
Terraform Workflow
Key Benefits
Comparison of Other IaC Tools
Terraform CLI Commands
Best Practices for Structuring Terraform Projects
Ex :- Terraform Module for EC2 Instance
- Modules
How to Secure State File
Remote Backend
Steps to Secure Terraform State File in AWS S3
Conclusion
IaC (Infrastructure as Code )
It is described using high-level configuration syntax, which allows a blueprint of your data center to be versioned and managed like any other code.
Why Terraform ?
Nowadays, Terraform has become a key tool for managing infrastructure, especially with the rise of multiple cloud providers like AWS, Azure, and Google Cloud. It uses Infrastructure as Code (IaC) to automate the setup and management of resources, improving efficiency and reducing errors. Terraform’s ability to track infrastructure changes has made collaboration between teams much easier. It integrates seamlessly with CI/CD pipelines, supporting the automation of both infrastructure provisioning and application deployment. As businesses place more emphasis on security and compliance, Terraform has introduced features to ensure that infrastructure adheres to best practices. The growing ecosystem of modules and integrations also helps simplify complex tasks. Overall, Terraform has become an essential tool for handling modern cloud infrastructure.
Terraform Architecture
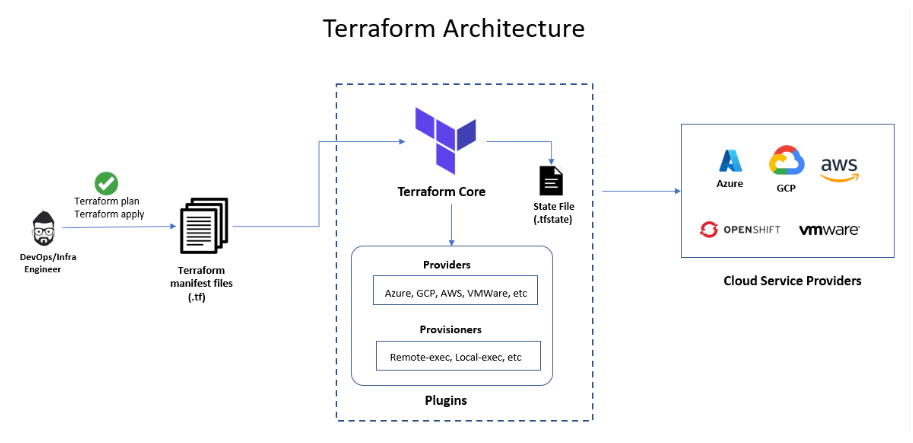
Terraform's architecture follows a simple flow of defining, planning, and applying infrastructure changes. It starts with configuration files written in HashiCorp Configuration Language (HCL), where users define the desired state of infrastructure. These files are then processed by Terraform Core, which handles the logic and operations needed to create, update, and destroy resources.
Terraform interacts with cloud services through providers, which are plugins that allow communication with platforms like AWS, Azure, or Google Cloud. When changes are required, Terraform generates an execution plan, which outlines the differences between the current state and the desired state of the infrastructure. After reviewing and confirming the plan, the user runs terraform apply to implement the changes. Terraform tracks the current infrastructure state in a state file, which ensures consistency and allows for accurate future changes. This architecture helps automate and manage complex infrastructure in a repeatable, version-controlled way.
Providers
Providers in Terraform are plugins that allow Terraform to interact with cloud platforms (like AWS, Azure, or GCP) and services by managing their resources.
provider "aws" {
region = "us-west-2" # Specify the AWS region, e.g., "us-east-1"
access_key = "YOUR_ACCESS_KEY" # Optional, can be set via environment variables or IAM roles
secret_key = "YOUR_SECRET_KEY" # Optional, can be set via environment variables or IAM roles
}
"Optionally, you can run aws configure to set up your environment according to your organization's requirements."
Provisioners
Provisioners are used to execute scripts or commands on a resource after it is created or modified, helping with tasks like configuration management or bootstrapping.
provisioner "remote-exec" {
inline = [
"sudo yum install -y httpd", # This command installs Apache
"sudo service httpd start" # This command starts the Apache service
]
}
Key Components:
Provisioner Block:
- provisioner “remote-exec“: Defines the use of the remote-exec provisioner, meaning the commands will be executed on the remote instance (e.g., EC2 instance) after it is created.
inline Argument: Defines the actual commands that will be executed on the remote instance. The inline argument expects a list of strings, where each string is a command that will be executed on the remote instance.
- “Apache HTTP (httpd) will be installed automatically as part of the provisioning process when you run terraform apply, as long as the remote-exec provisioner is defined with the given commands.”
Terraform Workflow
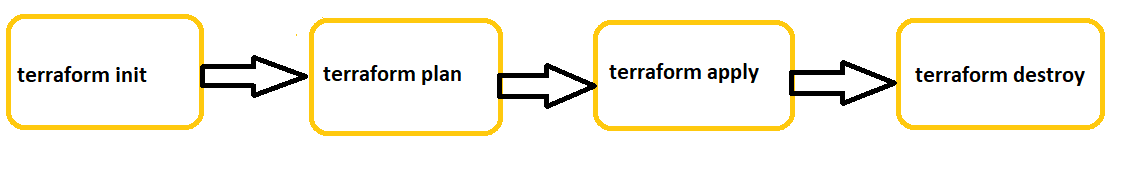
The Terraform workflow involves defining infrastructure in .tf configuration files, running terraform plan to preview changes, and applying them with terraform apply. Terraform tracks infrastructure state in a state file, ensuring consistency across updates. This process automates and manages infrastructure changes efficiently.
Key Benefits
Multi-Cloud and Multi-Provider Support: Supports various cloud providers and services, allowing management of infrastructure across multiple platforms.
Declarative Configuration: Allows users to define desired infrastructure states, with Terraform handling the complexity.
Automation and Efficiency: Speeds up deployments and reduces human errors by automating infrastructure provisioning.
State Management: Keeps track of infrastructure changes using a state file, ensuring consistency and accurate updates.
Reusability with Modules: Encourages reusable modules for consistent and efficient infrastructure setup across environments.
Plan and Preview Changes: Lets users preview infrastructure changes with terraform plan before applying them.
Collaboration: Terraform enhances team collaboration through version control, remote backends, and workspaces for shared infrastructure management.
Cost Optimization: Terraform helps reduce costs by efficiently provisioning and de-provisioning resources based on demand.
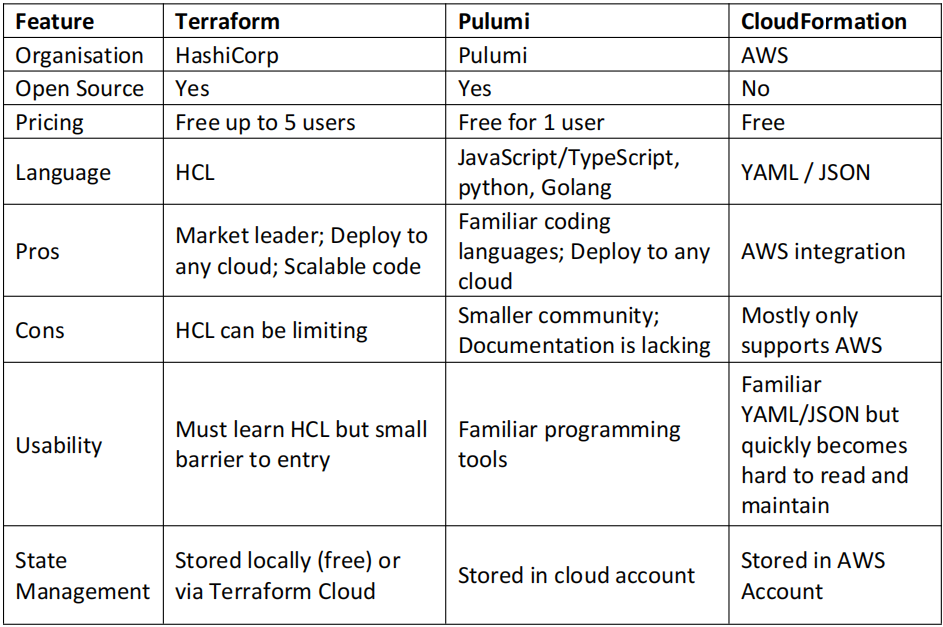
Comparison of Other IaC Tools
Terraform CLI commands
terraform help
Terraform has a built-in help system that can be accessed from the command line for commands that you are not familiar with, or want to learn more about. You can get specific help for any specific command, use the -help option with the relevant subcommand.
terraform -helpterraform init
The terraform init command is used to initialise a working directory containing terraform configuration files, preparing is it for use with terraform by downloading necessary plugins.
terraform initterraform validate
The terraform validate command is used to validates the configuration files for syntax errors and checks that the configuration is valid or not.
terraform validateterraform plan
The terraform plan command is used to creates an execution plan, showing the changes that will be made to infrastructure without actually applying them.
terraform plan -out=path save generated plan output as a file
terraform plan -target command generates a plan that focuses on creating, modifying, specific resources, ignoring others in the configuration.
terrafomr plan terraform plan -target=<resource_address>terraform apply
The terraform apply command is used to apply the changes required to reach the desired state of the configuration. Terraform apply will also write data to the terraform.tf state file.
terraform apply –auto-approve : Apply changes without being prompted to enter ”yes”
terraform apply -target : Only apply/deploy changes to the targeted resource
terraform apply terraform apply -auto-approve terraform apply -target=<resource_address>“ Default format for <resource_address> is <resource_type>.<resource_name> “
This format is used to uniquely identify a resource within your Terraform configuration.
terraform refresh
The terraform refresh command is used to update the entire Terraform state file with the latest information from the infrastructure.
terraform refreshterraform graph
The terraform graph command is use to generate a graphical representation of the Terraform resource dependencies. It creates a DOT format output (which is a plain text graph description language) of the Terraform resources and their dependencies. This is useful for visualizing how resources are related to one another in your Terraform configuration.
terraform graph -- Generate the graph in DOT format terraform graph | dot -Tpng > graph.png -- Generates a PNG image of the resource graph and saves it as graph.pngterraform show
The terraform show command displays the current state or a specific plan in a human-readable format. It helps you inspect the Terraform state file or the result of a Terraform execution plan.
terraform showterraform output
The terraform output command is used to extract and display the output variables defined in the Terraform configuration after an infrastructure apply. These outputs can be used to get important information like instance IDs, IP addresses, or any other values set to be outputted in your Terraform code.
terraform outputterraform taint
The terraform taint command is used to manually mark a resource for destruction and recreation. When you taint a resource, Terraform will destroy and then recreate that resource during the next terraform apply.
terraform taint <resource_address>terraform untaint
The terraform untaint command removes the taint from a resource. If a resource is marked as "tainted," it will be destroyed and recreated on the next terraform apply. Running terraform untaint removes this mark, meaning Terraform will no longer recreate the resource.
terraform untaint <resource_address>terraform import
The terraform import command allows you to import existing infrastructure into Terraform management. This is useful if you've created resources outside of Terraform or want to bring existing infrastructure under Terraform management.
terraform import <resource_address>terraform destroy
The terraform destroy command is used to delete all the resources managed by Terraform. It removes everything from your infrastructure that is defined in your configuration files.
terraform destroyThis will prompt you to confirm the action before destroying the resources. If you want to skip the confirmation, you can add the —auto-approve flag.
terraform destroy --auto-approve
Note:-
To target specific resources for destruction in Terraform, you can use the -target flag with the terraform destroy command. This allows you to destroy only specific resources, rather than destroying all resources defined in your Terraform config.
terraform destroy -target=<resource_address>Example with Multiple Resources:
You can specify multiple resources to be destroyed by repeating the -target flag for each resource:
terraform destroy -target=aws_instance.my_instance -target=aws_s3_bucket.my_bucketIf your resource name contains characters that the shell might interpret differently (like
.or-), or if your resource name has spaces, you might need to put quotes around it. Example for plan, apply and destroy.terraform plan -target="aws_instance.my-instance" terraform apply -target="aws_instance.my-instance" terraform target -target="aws_instance.my-instance"
Best Practices for Structuring Terraform Projects
To structure Terraform projects effectively, organize code into distinct files like main.tf, variables.tf, outputs.tf, and provider.tf for clarity and modularity. Use modules to promote reusability, and separate environments (e.g., dev, test, prod) into different directories. Store sensitive information securely with remote backends and ensure state files are versioned. Consistently follow naming conventions and maintain documentation to streamline collaboration and future maintenance.

Ex :- Terraform Module for EC2 Instance
This Terraform module is designed to provision an EC2 instance using AWS. It follows modularization by placing resources, variables, and outputs in separate files under the Modules/ec2 directory.
provider.tf : Defines and configures the cloud or service provider (like AWS, Azure, GCP) and its settings for managing resources.

Modules
Modules in Terraform are reusable, self-contained configurations that help organize infrastructure as code. They allow users to define, group, and manage resources efficiently, promoting modularity and reusability.
Reusability – Helps avoid duplication by reusing configurations across multiple projects.
Maintainability – Simplifies complex infrastructure by breaking it into smaller, manageable parts.
Scalability – Makes it easier to scale infrastructure by reusing predefined templates.
Collaboration – Encourages better teamwork by structuring code in an organized way.
main.tf : Defines the EC2 instance resource, specifying the AMI, instance type, key pair, and tags. This file ensures the instance is created with the desired configuration.

variables.tf : Manages input parameters like ami_id and instance_type, making the module flexible and reusable.

output.tf : Captures instance details such as instance_id, private_ip, instance_type, ami_used and public_ip, which can be used for further automation.

Root main.tf : Serves as the main configuration file, referencing the EC2 module using module ec2 and sourcing it from “./Modules/ec2” . This approach promotes better organization and reusability of Terraform code.

After applying terraform apply command, the terraform.tfstate file is generated and stored locally. This file is a crucial component in Terraform's infrastructure management, as it keeps track of the resources Terraform has created, updated, or deleted.
In Terraform, when managing infrastructure with multiple modules, you might want to apply changes to a specific module without affecting others. This can be achieved using the -target flag with the terraform command. Here's how you can do it:
terraform plan-target="module.<module_name>"
terraform apply -target="module.<module_name>"
terraform destroy -target="module.<module_name>"
For example, to apply changes only to the EC2 module, use:
terraform plan-target="module.ec2"
terraform apply -target="module.ec2"
terraform destroy -target="module.ec2"
In organizations, there are a few cases where the terraform.tfstate file can be lost or corrupted.
Accidental Deletion
Corruption Due to System Failure
Lost in a Local Environment
Multiple Users Overwriting the File
Untracked State File in Version Control
How to secure statefile ?
To prevent state loss, securing it in a remote backend (such as AWS S3, Azure Blob, or HashiCorp Terraform Cloud) is highly recommended. This ensures state consistency, collaboration, and recovery in case of failures.
Remote Backend:-
A remote backend in Terraform is a storage location where the terraform.tfstate file is saved instead of storing it locally. It helps in state management, collaboration, and recovery by keeping the state file in a centralized and secure location like AWS S3, Azure Blob, or HashiCorp Terraform Cloud.
Steps to Secure Terraform State File in AWS S3
1. Create an S3 Bucket
The bucket name must be globally unique across AWS.
Enable versioning to allow better state recovery in case of accidental deletion or corruption.
2. Create a DynamoDB Table (for State Locking)
Use terraform_locks as the table name (or any preferred name).
Set Primary Key as LockID (String type) to enable state locking and prevent conflicts.
3. Ensure IAM Permissions
The IAM role or user running Terraform must have read/write access to the S3 bucket.
It should also have permissions to use DynamoDB for state locking.
backend.tf : defines the configuration for storing and managing the Terraform state file, specifying the backend type (e.g., local, S3, Azure, etc.) and the related settings for state storage.

Note:
Before applying this configuration, you need to manually create the S3 bucket and DynamoDB table for state locking in your AWS management console.
Conclusion
Terraform is a game-changer in the world of Infrastructure as Code, offering a unified, automated approach to managing cloud resources. Its powerful features, such as state tracking, modularity, and multi-cloud support, help organizations improve operational efficiency while reducing human error. Terraform helps organizations safeguard their infrastructure, ensuring consistency and compliance across environments.
Subscribe to my newsletter
Read articles from Venkat Teja Thota directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Venkat Teja Thota
Venkat Teja Thota
Cloud/DevOps Engineer embracing new challenges, dedicated to crafting insightful articles and blogs that tackle life’s challenges and cloud solutions.