Decoding Hedgey Finance’s $45M Exploit.
 Shivank Kapur
Shivank Kapur
TL;DR
Hedgey Finance is a platform that specialises in offering DeFi solutions, especially in the areas of lending/borrowing protocols and yield farming.
On April 19, it had two separate exploits that resulted in the loss of $44.7 million in total.
The cancelCampaign() function did not revoke the token allowance granted during campaign creation, allowing the attacker to exploit this oversight.
About the Project
Hedgey Finance, a token infrastructure platform, had two separate exploits that resulted in the loss of $44.7 million in total.
An April 19 report claims that Hedgey was the victim of an exploit involving more than $42.8 million Arbitrum (ARB) tokens on the Arbitrum network and the rest Ethereum (ETH). A portion of the money was transferred by the attacker to the Bybit cryptocurrency exchange.
Decoding the Smart Contract Vulnerability
On-Chain Details
Attacker Address :- https://etherscan.io/address/0xDed2b1a426E1b7d415A40Bcad44e98F47181dda2
Attack Contract:- https://etherscan.io/address/0xC793113F1548B97E37c409f39244EE44241bF2b3
Vulnerable Contract:- https://etherscan.io/address/0xBc452fdC8F851d7c5B72e1Fe74DFB63bb793D511
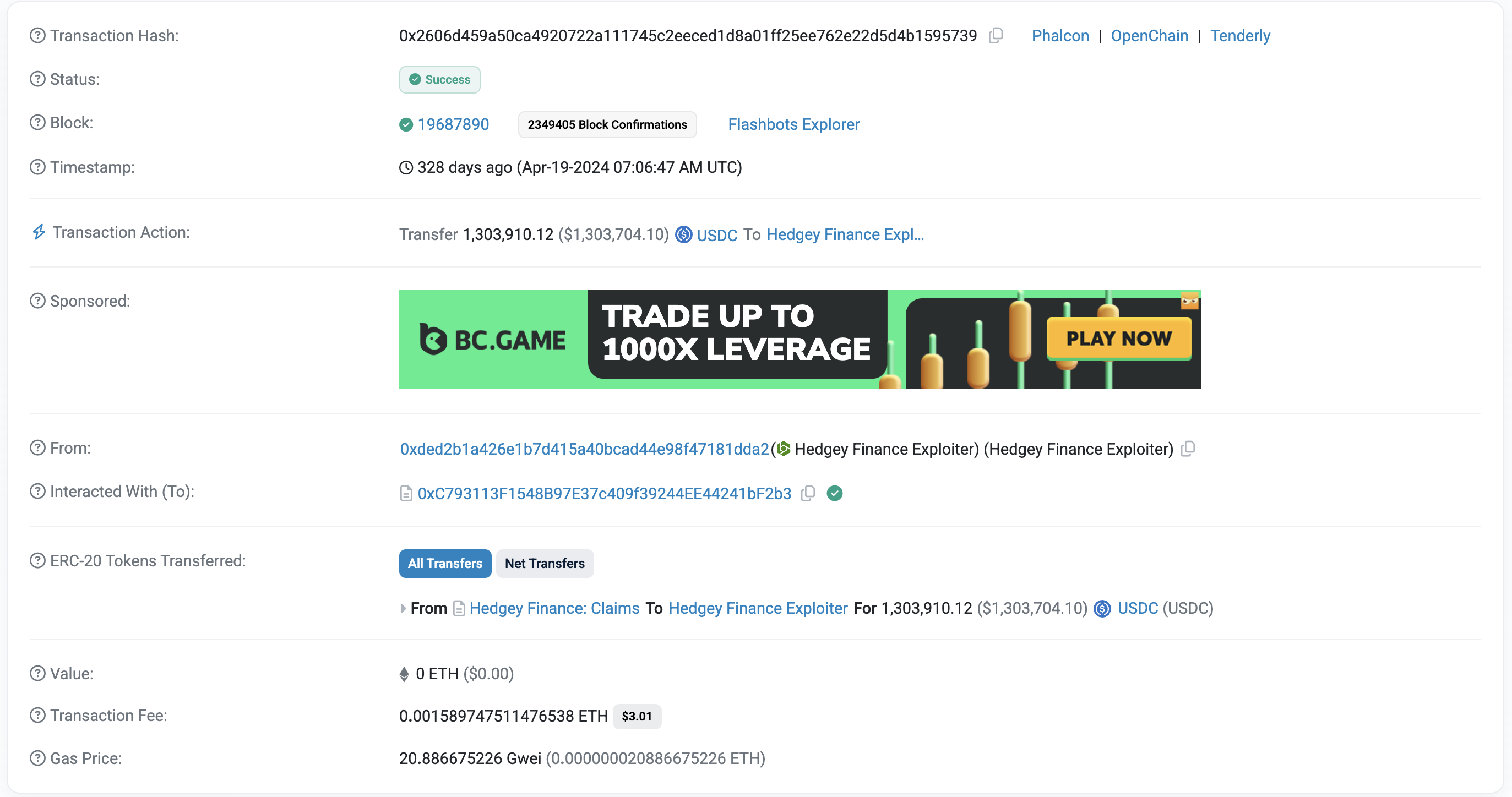
Attack Transaction:- https://etherscan.io/tx/0x2606d459a50ca4920722a111745c2eeced1d8a01ff25ee762e22d5d4b1595739

Smart Contract Hack Overview
The smart contract's campaign creation and cancellation processes are where the vulnerability arises.
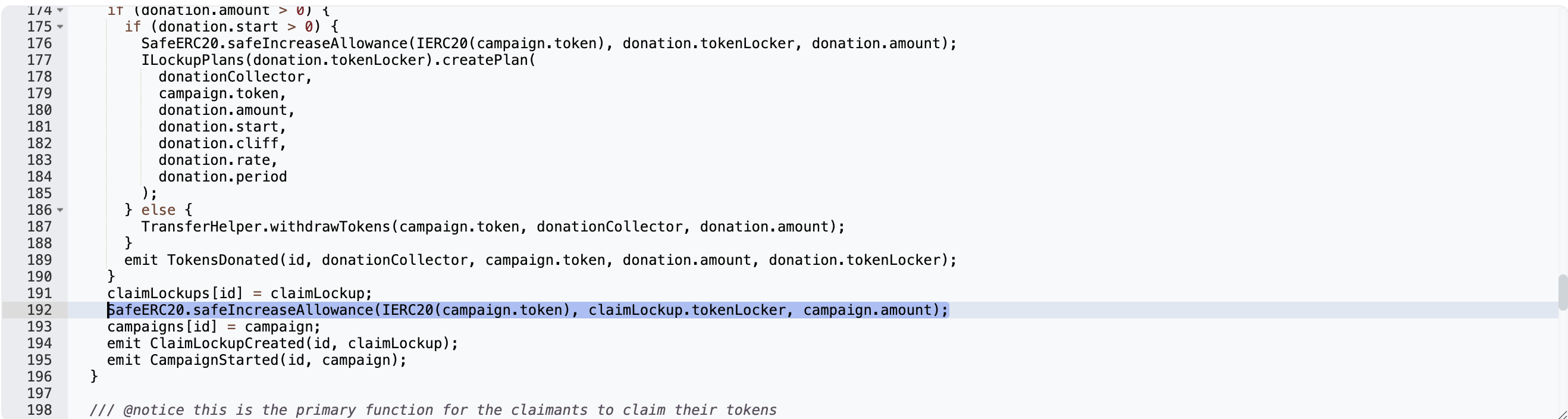
First, the locked tokens are transferred to a contract upon campaign creation, and the user is given an allowance. However, the campaign manager's allowance is not revoked by the contract upon cancellation. Allowance revocation isn't handled from the token's point of view, even if it is said to stop further token claims in the contract logic.
The exploiter creates a campaign, cancels it, and then receives the locked cash after using a flash loan to obtain $1.3M USDC. Then, using the previously given allowance, the exploit contract transfers the $1.3M USDC from the ClaimCampaigns contract, draining it.
Funds Flow
The initial exploit by 0xDed2b1a426E1b7d415A40Bcad44e98F47181dda2, in which they stole 1.3m USDC, served as the basis for this attack flow. The attack took place in two transactions One of them transferred assets, while the other took advantage of the weakness.
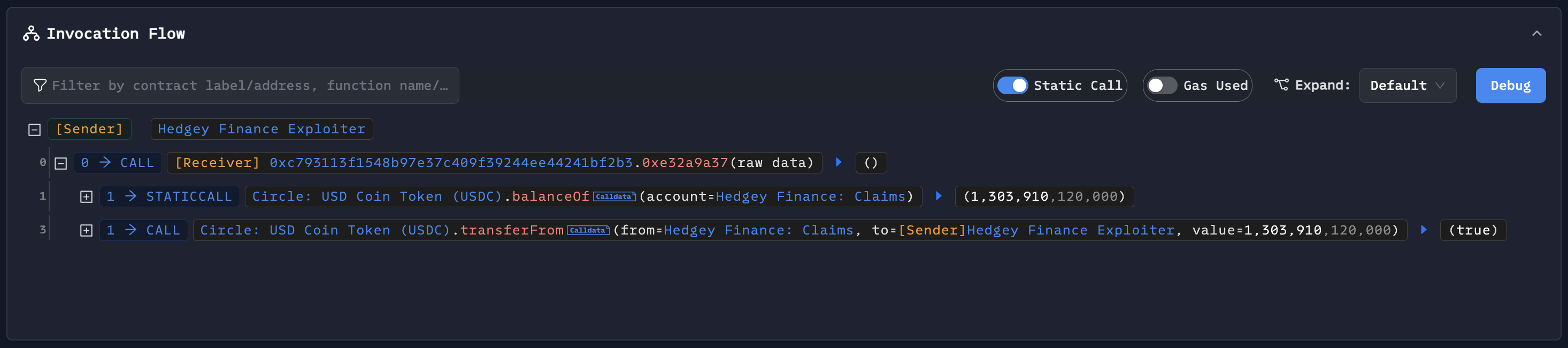
The attacker used createLockedCampaign() from the ClaimCampaigns contract and flash-loaned 1.305 million USDC from Balancer.
The code is 0xbc452fdc8f851d7c5b72e1fe74dfb63bb793d511. The attacker was authorised to use the 1.305 million USDC they transferred to the ClaimCampaign contract as a result of this procedure.
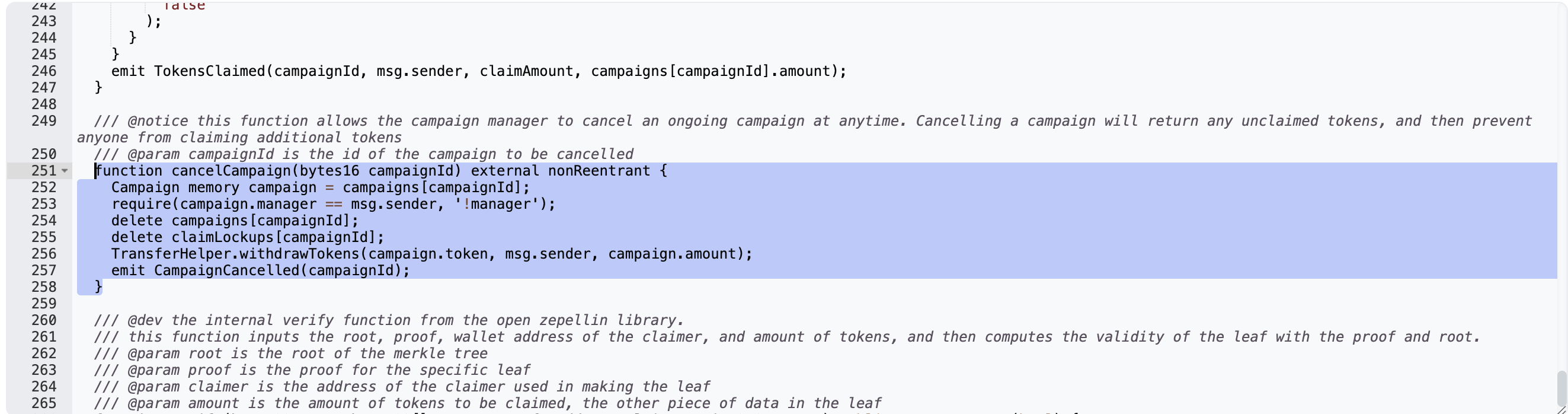
After that, the attacker invoked cancelCampaign() and removed the USDC that Balancer had been reimbursed.
The attacker started a transfer of 1,303,910 USDC using the transferFrom() function. The USDC was transferred since the cancelCampaign() function did not revoke the approval that had been obtained.
The attacker took NOBL tokens, which were sold for almost $600k, by repeating the procedure. Since the original exploit, copycat exploiters have stolen further assets, including 78,148,820 BONUS tokens and about $20k in MASA tokens.
Who’s to Blame?
The core issue stemmed from inadequate input validation and allowance management within the smart contract:
Lack of Allowance Revocation: The cancelCampaign() function did not revoke the token allowance granted during campaign creation, allowing the attacker to exploit this oversight.
Insufficient Input Validation: The createLockedCampaign() function lacked proper validation for critical parameters, enabling the attacker to manipulate the function's behavior maliciously.
Mitigation Process
To prevent similar exploits, the following measures are recommended:
Comprehensive Input Validation: Ensure all function parameters are thoroughly validated to prevent unauthorized or malicious inputs.
Allowance Management: Implement mechanisms to revoke token allowances promptly when they are no longer necessary, especially upon function completion or cancellation.
Security Audits: Conduct regular and thorough security audits of smart contracts to identify and address potential vulnerabilities before deployment.
Subscribe to my newsletter
Read articles from Shivank Kapur directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Shivank Kapur
Shivank Kapur
I'm a FullStack Developer currently working with Technologies like MERN Stack, BlockChain, GraphQL, Next.js, LLMs, and a plethora of other cutting-edge tools. I'm working as a Developer Relations Engineering intern at Router Protocol and also as a Contributor at SuperteamDAO. My journey also encompasses past experiences at Push Protocol, where I orchestrated seamless community management strategies. I help Communities by Bridging the Gap between Developers and Clients. Crafting, launching, and meticulously documenting products fuel my passion, infusing every endeavor with purpose and precision. Beyond the binary, I find solace in the pages of self-help and spirituality, honing both mind and spirit with each turn of the page. phewww... I love a cup of coffee ☕ while writing code. So let's connect and have a meet over something you wanna discuss. I'll be more than happy to have it. Drop me a line at shivankkapur2004@gmail.com