Stop Pod Security Risks! How to Safely Connect to AWS Services
 Vikas Dubey
Vikas Dubey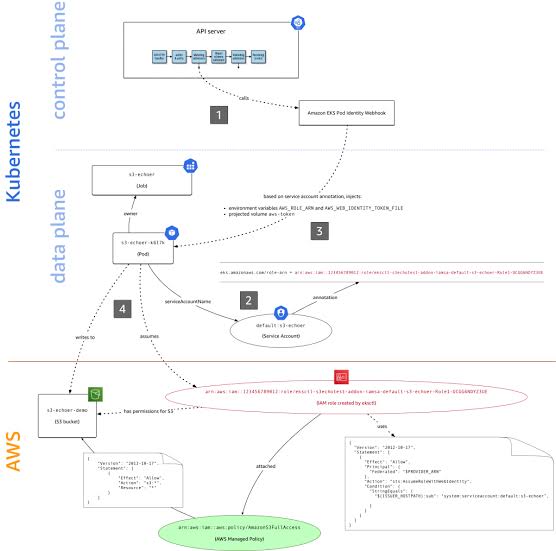
We are in the world of quick set deployment and packaging the application wanted it to deliver with ease with heavy traffic we want them to autoscale horizontally thats what K8s is build for
If EKS Cluster wants to communicate with native aws services it has to follow the conventional authentication and authorisation mechanism which means in EKS we have feasibility OPEN ID Connect Provider URL which is linked with AWS IAM Role, let us see how it functions step by step
1) POD contacts Kubernetes API Server using kubectl to communicate let say S3 bucket
2) Kubectl requests OIDC server to provide the Token which consists of
a) POD Identity b) OIDC signed URL c) Service Account Name
3) OIDc responds back to POD with Signed Token consisting above details
4) Using this Token POD requests AWS Security Token Service
5) AWS STS verifies below details
a) POD Identity b) OIDC signed URL c) Service Account Name
It Also checks trust relationship built between OIDC as principal which assume the role with web identity token for only Service Account Name mentioned in OIDC provided token
6) Once its verified AWS STS provides temporary credential to POD to access the s3 bucket.
To access the s3 bucket we have to create a Object as service account which will then be used by POD to access the s3 bucket.
This is more prominent nowadays
Happy Learning!
Subscribe to my newsletter
Read articles from Vikas Dubey directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Vikas Dubey
Vikas Dubey
Cloud Solution Architect, can drag you out of problem