Understanding Access Tokens and Refresh Tokens
 Rishabh Yadav
Rishabh YadavIn modern authentication and authorization systems, access tokens and refresh tokens play a crucial role in securing API communications. They are widely used in OAuth 2.0 and OpenID Connect frameworks to enable secure access to resources while minimizing security risks.
Access Token
An access token is a short-lived credential that grants a client application access to protected resources. It is typically issued by an authorization server after successful authentication and is included in API requests to verify the user's identity and permissions.
Characteristics of Access Tokens:
Short-lived: Typically expires within minutes to hours.
Bearer token: Often used in HTTP headers (e.g.,
Authorization: Bearer <token>).Contains claims: Encodes user information, permissions, and expiration time.
Can be JWTs: JSON Web Tokens (JWT) are a common format, enabling self-contained authentication.
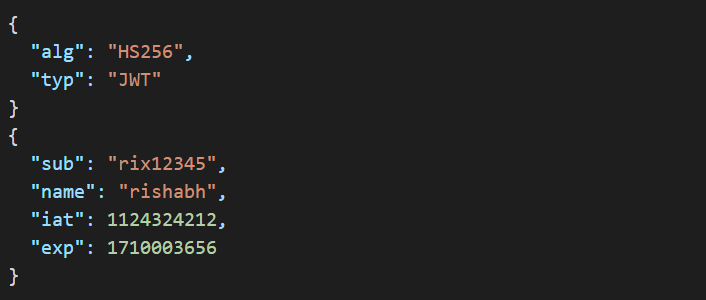
Refresh Token?
A refresh token is a long-lived credential used to obtain new access tokens without requiring the user to re-authenticate. It helps maintain a seamless user experience while keeping security intact.
Characteristics of Refresh Tokens:
Long-lived: Can last from hours to days or even longer.
Stored securely: Should never be exposed in frontend applications.
Issued alongside access tokens: Provided during initial authentication.
Cannot directly access resources: Only used to request new access tokens.
How Access and Refresh Tokens Work Together
User logs in: The authentication server validates the user and issues an access token and a refresh token.
Accessing protected resources: The client includes the access token in API requests.
Token expiration: Once the access token expires, the request fails with a
401 Unauthorizederror.Using the refresh token: The client sends the refresh token to obtain a new access token.
New access token issued: The authorization server validates the refresh token and provides a new access token.
Session continuity: The client continues accessing resources without requiring re-authentication.
Security Best Practices
Store refresh tokens securely: Keep them in HTTP-only cookies or a secure backend.
Use HTTPS: Prevent token interception by ensuring secure communication.
Implement token expiration: Reduce risk by setting appropriate lifetimes.
Use refresh token rotation: Issue a new refresh token each time to mitigate security breaches.
Revoke refresh tokens when needed: Allow users to log out or invalidate compromised tokens.
Conclusion
Access tokens and refresh tokens enhance security and efficiency in authentication systems. While access tokens provide immediate access to resources, refresh tokens allow for seamless token renewal without requiring repeated logins. Implementing these tokens correctly helps in maintaining a balance between security and user experience in modern applications.
By following best practices, developers can safeguard sensitive data while ensuring smooth authentication flows for users.
Subscribe to my newsletter
Read articles from Rishabh Yadav directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
