Symmetric key algorithm - (2) AES
 박서경
박서경AES is a symmetric key encryption algorithm that has replaced DES due to its higher security and efficiency.
1. Block Cipher Structure
AES encrypts fixed-size 128-bit blocks of data.
Unlike DES (which uses a Feistel structure), AES uses a substitution-permutation network (SPN).
2. Key Length Variants
AES supports three different key sizes, each defining the number of encryption rounds:
AES-128: 128-bit key, 10 rounds
AES-192: 192-bit key, 12 rounds
AES-256: 256-bit key, 14 rounds
3. Security & Resistance to Attacks
Stronger than DES and 3DES, resistant to brute-force attacks.
Resistant to differential and linear cryptanalysis, which were used to attack DES.
Not vulnerable to practical attacks except for side-channel attacks (e.g., timing attacks).
4. Encryption Process (Rounds Structure)
Each round consists of four main operations:
SubBytes: Byte substitution using an S-Box (nonlinear transformation).
ShiftRows: Row-wise shifting to enhance diffusion.
MixColumns: Column-wise mixing to introduce confusion (not used in the last round).
AddRoundKey: XOR operation with a round key derived from the main key.
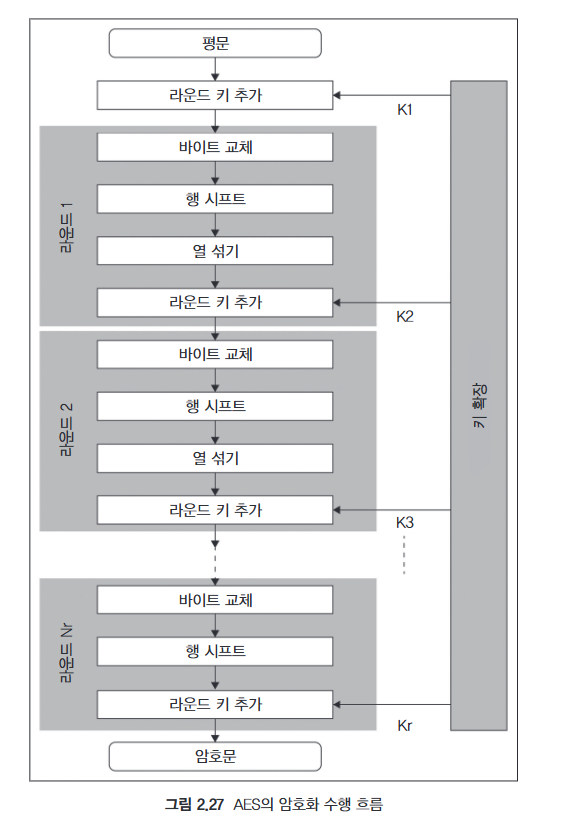
5. Key Expansion (Key Schedule)
Uses Rijndael key schedule to generate multiple round keys from the original key.
Round keys are derived through byte substitution (S-Box), XOR operations, and shifts.
6. Speed & Efficiency
Faster than DES because it encrypts in 128-bit blocks instead of 64-bit.
Optimized for both hardware and software implementations.
Widely used in embedded systems, IoT, and cloud security due to its efficiency.
7. Common Applications
TLS/SSL (secure web communication)
Disk encryption (BitLocker, VeraCrypt)
Wi-Fi security (WPA2, WPA3)
Blockchain encryption (protecting private keys)
File and database encryption
8. Future Considerations
AES is currently secure against classical attacks, but quantum computing could pose future risks.
Post-quantum cryptography (PQC) research is ongoing to find alternatives.
AES remains the gold standard for symmetric encryption, providing high security, efficiency, and adaptability in modern cryptographic applications. 🚀
9. Weaknesses of AES
📌 Summary of AES Vulnerabilities
| Vulnerability | Description | Mitigation |
| Brute-Force Attack | AES-128 weakened by quantum computing | Use AES-256 |
| Key Schedule Weakness | Structural patterns in AES-256 key schedule | Use random keys, apply KMS (Key Management System) |
| Side-Channel Attacks | Timing, power analysis, and electromagnetic attacks | Maintain constant execution time, strengthen hardware security |
| Chosen-Plaintext Attack | Vulnerable to certain plaintext pattern analysis | Use random IV, implement AES-GCM |
| Related-Key Attack | Weakness in AES-192/AES-256 key schedule | Use fully random keys |
| Quantum Computing Threat | Grover’s algorithm weakens AES-128 security | Use AES-256, research Post-Quantum Cryptography (PQC) |
| Poor Implementation | Timing attacks successfully exploited in OpenSSL | Use secure libraries, apply security patches |
AES remains one of the most secure encryption algorithms, but its implementation and key management must be carefully handled to mitigate potential vulnerabilities. 🚀
Subscribe to my newsletter
Read articles from 박서경 directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
