Block cipher - Modes of Operation
 박서경
박서경What is Mode?
A mode of operation in cryptography refers to the method used to apply a block cipher algorithm (such as AES or DES) to encrypt or decrypt larger amounts of data. Since block ciphers operate on fixed-size blocks (e.g., 128-bit blocks in AES), different modes define how these blocks are processed and linked to ensure security, efficiency, and integrity.
Modes of operation can provide confidentiality, integrity, or both, depending on their design. Some commonly used modes include ECB, CBC, CFB, OFB, CTR, and GCM, each with unique properties suited for different use cases.
(1)ECB, Electronic Codebook
The simplest mode, encrypting each block independently.
The same input block always produces the same output block, making it vulnerable to pattern analysis.
Weak security, so it is rarely used.

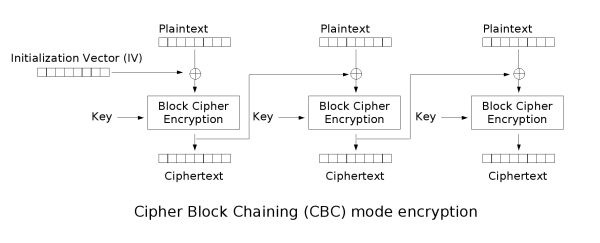
(2) CBC, Cipher Block Chaining
Each block is XORed with the previous ciphertext block before encryption.
The first block uses an Initialization Vector (IV).
More secure than ECB, but not suitable for parallel encryption.
(3)CFB, Cipher Feedback
Works like a stream cipher, allowing operation with smaller block sizes.
Uses the AES encryption function's output to encrypt the next block.
Parallel encryption is not possible, but parallel decryption is possible.


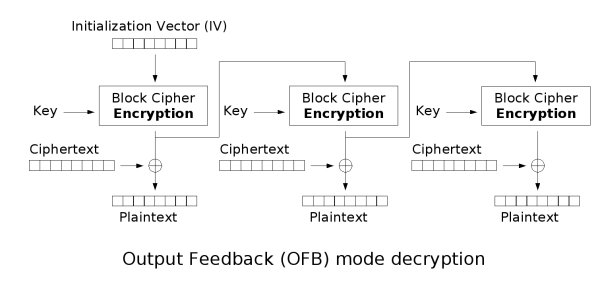
(4) OFB, Output Feedback
Similar to CFB, but the encrypted data is not fed back.
AES encryption output is directly used as the next input, preventing error propagation.
Reusing the same IV weakens security.

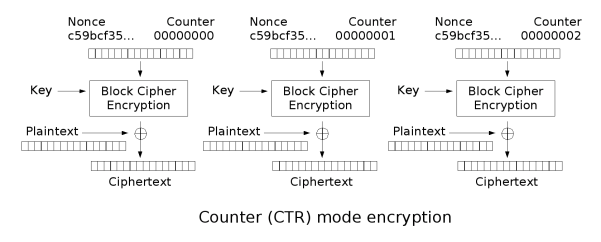
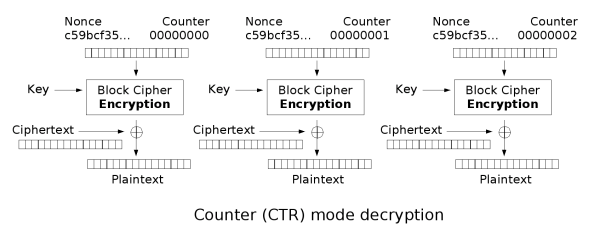
(5) CTR, Counter
Each block is encrypted with a counter value, allowing parallel processing.
Works similarly to a stream cipher, enabling byte-level processing.
Highly secure and efficient, making it one of the most widely used modes.
(6) GCM, Galois/Counter Mode
Based on CTR mode, with additional authentication functionality.
Ensures message integrity and supports AEAD (Authenticated Encryption with Associated Data).
Widely used in TLS, VPNs, and wireless security (WPA3).
What is AEAD (Authenticated Encryption with Associated Data)?
AEAD (Authenticated Encryption with Associated Data) is a cryptographic method that provides both encryption and authentication simultaneously.
It ensures not only confidentiality (encryption) but also integrity and authentication, preventing data tampering.
📌 Key Concepts of AEAD
✔ Encryption: Protects the confidentiality of the data.
✔ Authentication: Ensures the data has not been tampered with.
✔ Associated Data (AD): Additional data that is not encrypted but must be authenticated (e.g., packet headers).
Unlike traditional block cipher modes (e.g., CBC, ECB), AEAD performs encryption and authentication in a single operation, eliminating the need for separate MAC (Message Authentication Code) calculations.
📌 Why is AEAD Important?
Standard encryption methods (e.g., AES-CBC) do not guarantee data integrity, making them vulnerable to modification attacks.
Adding MAC-based authentication separately (e.g., HMAC) increases complexity and slows performance.
AEAD improves security and efficiency by combining encryption and authentication in one step.
📌 Common AEAD Modes
| AEAD Mode | Features | Use Cases |
| GCM (Galois/Counter Mode) | Fast, supports parallel processing, most widely used | TLS (HTTPS), VPNs, Wi-Fi security (WPA3) |
| CCM (Counter with CBC-MAC) | Slower than GCM but efficient for embedded systems | IoT security, wireless networks |
| OCB (Offset Codebook Mode) | Extremely fast but less common due to patent issues | High-speed network encryption |
Among these, AES-GCM is the most widely used AEAD mode, and it has become the standard for modern network security protocols such as TLS, IPsec, and SSH.
📌 Real-World Applications of AEAD
TLS (HTTPS, SSL) → Securing web traffic
WPA3 (Wi-Fi Security) → Wireless network encryption
IPsec, SSH, VPNs → Secure communication channels
IoT & Embedded Systems → Lightweight and efficient encryption
📌 Summary
AEAD provides encryption + authentication in a single step.
It ensures both confidentiality and integrity, preventing data tampering.
Common AEAD modes include AES-GCM, AES-CCM, and OCB.
AEAD is widely used in network security, IoT, Wi-Fi security, and VPNs.
In short, AEAD is a modern encryption method that enhances security by preventing data manipulation while maintaining confidentiality. 🚀
Subscribe to my newsletter
Read articles from 박서경 directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
