CloudFormation Template -Deploying AWS Fargate service using AWS Elastic Container Service
 Mahira Technology Private Limited
Mahira Technology Private Limited

Introduction:
The following AWS CloudFormation template defines a robust infrastructure deployment for a serverless application using Amazon Elastic Container Service (ECS) and AWS Fargate. AWS CloudFormation simplifies the provisioning and management of AWS resources, making it easier to deploy complex applications with scalability and reliability in mind.
This template allows for the creation of ECS services, suitable for hosting containerized applications, with a specific focus on a “Temporal Worker” service. The template is designed with flexibility in mind, allowing customization through parameters and conditional resource creation based on user-defined criteria.
Here’s a breakdown of the key components and resources in your CloudFormation template:
The CloudFormation template is written in YAML format and appears to define resources for deploying an AWS Fargate service using AWS Elastic Container Service (ECS). Below is a breakdown of the template’s key components:
- Parameters: These are input parameters that can be customized when you deploy the CloudFormation stack. They include:
EnvironmentName: A string parameter to specify the environment (e.g., "dev" or "production").NetworkStackName: The name of an existing CloudFormation stack containing networking resources.EcsStackName: The name of an existing CloudFormation stack containing ECS resources.Various parameters related to the ECS service, such as container port, CPU, memory, image, desired count, and min/max containers.
SetupTemporalWorkers: A string parameter that specifies if workers need to be set up (default is 'false').
2. Conditions: These are used to conditionally create or configure resources based on the value of a parameter. In this template, the SetupTemporalWorkers condition is used to determine whether certain resources are created. It checks if the SetupTemporalWorkers parameter is set to 'true'.
3. Resources: These are the AWS resources that will be created or managed by the CloudFormation stack. Some of the notable resources include:
IAM roles (
TemporalWorkerExecutionRole,TemporalWorkerTaskRole,TemporalWorkerAutoScalingRole,TemporalWorkerECSTaskRole) for various purposes, including ECS task execution and auto-scaling.ECS task definition (
TemporalWorkerTaskDefinition) specifying container details and configurations.CloudWatch Logs group (
TemporalWorkerCloudwatchLogsGroup) for log storage.ECS service (
TemporalWorkerService) defining the Fargate service's parameters, such as the desired count and network configuration.Auto Scaling target (
TemporalWorkerAutoScalingTarget) and scaling policies (TemporalWorkerCPUAutoScalingPolicyandTemporalWorkerMemoryAutoScalingPolicy) to dynamically adjust the number of containers based on CPU and memory utilization.EC2 security group (
TemporalWorkerContainerSecurityGroup) for the ECS containers.
The template is structured to conditionally create these resources based on the value of the SetupTemporalWorkers parameter, allowing flexibility in deploying the workers when needed.
Deployment Steps
Follow these steps to upload and create the CloudFormation stack using the AWS Management Console:
- Sign in to the AWS Management Console: Log in to your AWS account if you haven’t already.
2. Navigate to CloudFormation: Go to the AWS CloudFormation service from the AWS Management Console.
3. Click the “Create stack” button.
4. Upload the CloudFormation template file (YAML).
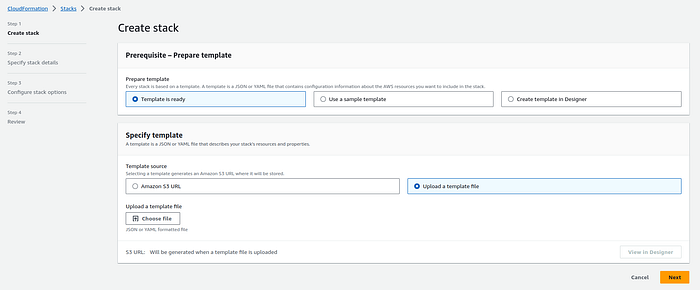
Yaml file :
AWSTemplateFormatVersion: '2010-09-09'
Transform: AWS::Serverless-2016-10-31
Parameters:
EnvironmentName:
Type: String
NetworkStackName:
Description: Name of an active CloudFormation stack of networking resources
Type: String
MinLength: '1'
MaxLength: '255'
AllowedPattern: '^[a-zA-Z][-a-zA-Z0-9]*$'
EcsStackName:
Description: Name of an active CloudFormation stack of ECS resources
Type: String
MinLength: '1'
MaxLength: '255'
AllowedPattern: '^[a-zA-Z][-a-zA-Z0-9]*$'
TemporalWorkerServiceName:
Type: String
Description: A name for the service
TemporalWorkerContainerPort:
Type: Number
Default: 7233
Description: Port number the application inside the docker container is binding to
TemporalWorkerContainerCpu:
Type: Number
Description: CPU to give the container. 1024 is 1 CPU
Default: 512
AllowedValues: [256, 512, 1024]
TemporalWorkerContainerMemory:
Type: Number
Description: Memory in megabytes to give the container
Default: 256
AllowedValues: [256, 512, 1024, 2048]
TemporalWorkerContainerImage:
Type: String
Description: ECR Image URI and Tag
TemporalWorkerDesiredCount:
Type: Number
Default: 2
Description: Number of copies of the service task to run
TemporalWorkerMinContainers:
Type: Number
Default: 1
TemporalWorkerMaxContainers:
Type: Number
Default: 6
SetupTemporalWorkers:
Description: Specifies if workers need to be set up
Type: String
Default: 'false'
Conditions:
SetupTemporalWorkers: !Equals [!Ref SetupTemporalWorkers, 'true']
Resources:
TemporalWorkerExecutionRole:
Type: AWS::IAM::Role
Condition: SetupTemporalWorkers
Properties:
RoleName: !Sub '${EnvironmentName}${TemporalWorkerServiceName}ExecutionRole'
AssumeRolePolicyDocument:
Statement:
- Effect: Allow
Principal:
Service: ecs-tasks.amazonaws.com
Action: 'sts:AssumeRole'
ManagedPolicyArns:
- 'arn:aws:iam::aws:policy/service-role/AmazonECSTaskExecutionRolePolicy'
TemporalWorkerTaskRole:
Type: AWS::IAM::Role
Condition: SetupTemporalWorkers
Properties:
RoleName: !Sub '${EnvironmentName}${TemporalWorkerServiceName}TaskRole'
AssumeRolePolicyDocument:
Statement:
- Effect: Allow
Principal:
Service: ecs-tasks.amazonaws.com
Action: 'sts:AssumeRole'
TemporalWorkerAutoScalingRole:
Type: AWS::IAM::Role
Condition: SetupTemporalWorkers
Properties:
RoleName: !Sub '${EnvironmentName}${TemporalWorkerServiceName}AutoScalingRole'
AssumeRolePolicyDocument:
Statement:
- Effect: Allow
Principal:
Service: ecs-tasks.amazonaws.com
Action: 'sts:AssumeRole'
ManagedPolicyArns:
- 'arn:aws:iam::aws:policy/service-role/AmazonEC2ContainerServiceAutoscaleRole'
TemporalWorkerTaskDefinition:
Type: AWS::ECS::TaskDefinition
Condition: SetupTemporalWorkers
Properties:
Family: !Ref TemporalWorkerServiceName
Cpu: !Ref TemporalWorkerContainerCpu
Memory: !Ref TemporalWorkerContainerMemory
NetworkMode: awsvpc
RequiresCompatibilities: [FARGATE]
ExecutionRoleArn: !GetAtt TemporalWorkerExecutionRole.Arn
TaskRoleArn: !Ref TemporalWorkerECSTaskRole
ContainerDefinitions:
- Name: !Ref TemporalWorkerServiceName
Cpu: !Ref TemporalWorkerContainerCpu
Memory: !Ref TemporalWorkerContainerMemory
Image: !Ref TemporalWorkerContainerImage
StopTimeout: 60
PortMappings:
- ContainerPort: !Ref TemporalWorkerContainerPort
HostPort: !Ref TemporalWorkerContainerPort
Environment:
- Name: NODE_ENV
Value: !Ref EnvironmentName
LogConfiguration:
LogDriver: awslogs
Options:
awslogs-group: !Ref TemporalWorkerCloudwatchLogsGroup
awslogs-region: !Sub '${AWS::Region}'
awslogs-stream-prefix: ecs
TemporalWorkerCloudwatchLogsGroup:
Type: AWS::Logs::LogGroup
Condition: SetupTemporalWorkers
DeletionPolicy: Delete
UpdateReplacePolicy: Delete
Properties:
LogGroupName: !Sub '/ecs/${EnvironmentName}-${TemporalWorkerServiceName}-lg'
TemporalWorkerECSTaskRole:
Type: AWS::IAM::Role
Condition: SetupTemporalWorkers
Properties:
RoleName: !Sub '${EnvironmentName}${TemporalWorkerServiceName}ECSTaskRole'
AssumeRolePolicyDocument:
Statement:
- Action: sts:AssumeRole
Effect: Allow
Principal:
Service: ecs-tasks.amazonaws.com
Policies:
- PolicyName: !Sub '${EnvironmentName}${TemporalWorkerServiceName}PolicyName'
PolicyDocument:
Statement:
- Effect: Allow
Action: [secretsmanager:GetSecretValue]
Resource: !Sub arn:${AWS::Partition}:ses:${AWS::Region}:${AWS::AccountId}:identity/*
- Effect: Allow
Action:
- secretsmanager:DescribeSecret
- secretsmanager:GetSecretValue
- secretsmanager:ListSecretVersionIds
- secretsmanager:ListSecrets
Resource: !Sub arn:${AWS::Partition}:secretsmanager:${AWS::Region}:${AWS::AccountId}:secret:${EnvironmentName}-dm-temporal-visit*
- Effect: Allow
Action:
- secretsmanager:DescribeSecret
- secretsmanager:GetSecretValue
- secretsmanager:ListSecretVersionIds
- secretsmanager:ListSecrets
Resource: !Sub arn:${AWS::Partition}:secretsmanager:${AWS::Region}:${AWS::AccountId}:secret:AmazonMSK_*
TemporalWorkerService:
Type: AWS::ECS::Service
Condition: SetupTemporalWorkers
Properties:
ServiceName: !Sub ${EnvironmentName}-${TemporalWorkerServiceName}
Cluster: !ImportValue: !Sub ${EcsStackName}-ClusterName
LaunchType: FARGATE
DeploymentConfiguration:
MaximumPercent: 200
MinimumHealthyPercent: 75
DesiredCount: !Ref TemporalWorkerDesiredCount
NetworkConfiguration:
AwsvpcConfiguration:
AssignPublicIp: DISABLED
Subnets:
- !ImportValue: !Sub ${NetworkStackName}-PrivateSubnet1Id
- !ImportValue: !Sub ${NetworkStackName}-PrivateSubnet2Id
TaskDefinition: !Ref TemporalWorkerTaskDefinition
PlatformVersion: '1.4.0'
TemporalWorkerAutoScalingTarget:
Type: AWS::ApplicationAutoScaling::ScalableTarget
Condition: SetupTemporalWorkers
Properties:
MinCapacity: !Ref TemporalWorkerMinContainers
MaxCapacity: !Ref TemporalWorkerMaxContainers
ResourceId:
Fn::Join: ['/', ['service', !ImportValue: !Sub '${EcsStackName}-ClusterName', !GetAtt TemporalWorkerService.Name]]
ScalableDimension: ecs:service:DesiredCount
ServiceNamespace: ecs
RoleARN: !GetAtt TemporalWorkerAutoScalingRole.Arn
TemporalWorkerCPUAutoScalingPolicy:
Type: AWS::ApplicationAutoScaling::ScalingPolicy
Condition: SetupTemporalWorkers
Properties:
PolicyName: !Sub "${EnvironmentName}-${TemporalWorkerServiceName}-CPUAutoScalingPolicy"
PolicyType: TargetTrackingScaling
ScalingTargetId: !Ref TemporalWorkerAutoScalingTarget
TargetTrackingScalingPolicyConfiguration:
PredefinedMetricSpecification:
PredefinedMetricType: ECSServiceAverageCPUUtilization
ScaleInCooldown: 300
ScaleOutCooldown: 300
TargetValue: 60.0
TemporalWorkerMemoryAutoScalingPolicy:
Type: AWS::ApplicationAutoScaling::ScalingPolicy
Condition: SetupTemporalWorkers
Properties:
PolicyName: !Sub "${EnvironmentName}-${TemporalWorkerServiceName}-MemoryAutoScalingPolicy"
PolicyType: TargetTrackingScaling
ScalingTargetId: !Ref TemporalWorkerAutoScalingTarget
TargetTrackingScalingPolicyConfiguration:
PredefinedMetricSpecification:
PredefinedMetricType: ECSServiceAverageMemoryUtilization
ScaleInCooldown: 300
ScaleOutCooldown: 300
TargetValue: 75.0
TemporalWorkerContainerSecurityGroup:
Type: AWS::EC2::SecurityGroup
Condition: SetupTemporalWorkers
Properties:
GroupDescription: !Join ['-', [!GetAtt TemporalWorkerService.Name, ContainerSecurityGroup]]
VpcId: !ImportValue: !Sub ${NetworkStackName}-VpcId
SecurityGroupEgress:
- IpProtocol: '-1'
CidrIp: 0.0.0.0/0
Description: Allow all outbound traffic
5. Specify Stack Details:
Enter a Stack name for your deployment.
Provide parameter values as needed.
Review and acknowledge the capabilities .
You can set additional stack options or tags if necessary.
6. Review and Create:
Review the stack details and configuration.
Click “Create stack” to initiate the deployment.
7. Monitor Stack Creation:
The CloudFormation stack creation process will begin.
Monitor the stack events in the AWS Management Console.
Conclusion:
In conclusion, the provided AWS CloudFormation template serves as a powerful blueprint for orchestrating a serverless application infrastructure on AWS. By utilizing ECS and Fargate, it leverages containerization to provide a scalable and efficient deployment environment. The flexibility inherent in this template, with configurable parameters and conditional resource creation, allows users to adapt the infrastructure to their specific needs, whether it’s for development, production, or any other environment.
Subscribe to my newsletter
Read articles from Mahira Technology Private Limited directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Mahira Technology Private Limited
Mahira Technology Private Limited
A leading tech consulting firm specializing in innovative solutions. Experts in cloud, DevOps, automation, data analytics & more. Trusted technology partner.