AZ-104 Identity - Entra-Subscriptions mapping, and Entra Roles
 Cloudville
Cloudville
Introduction
A subscription is an agreement with Microsoft that allows access to one or more cloud services, with costs based on either a per-user licensing fee or cloud resource consumption. However, to utilize these resources, users must be authenticated and authorized, which is managed by Entra ID. This shows that there is a relationship between subscriptions and Entra tenants, ensuring that identity and access management are properly controlled. If you have been following this AZ-104 series, you probably already know what Entra ID is, but let us revisit the definition.
Entra ID
Microsoft Entra ID is Microsoft's cloud-based identity and access management service. An Entra ID tenant represents a specific instance of Entra ID containing accounts and groups. Think of it as an isolated environment where you can manage users, groups, and resources. Every Entra ID tenant is distinct and separate from other tenants. A tenant has a unique domain, like yourcompany.onmicrosoft.com. You can have custom domains, but behind the scenes, the .onmicrosoft.com domain is what identifies your tenant.
Subscriptions
An Azure subscription is a logical unit of Azure services that is linked to an Azure account. It's where you provision and manage Azure resources. Each subscription can have a separate billing and payment setup, allowing for flexibility in how you manage costs and resources. Subscriptions help in organizing access to cloud service resources. They determine how resources are paid for. Each subscription is associated with a single Entra ID tenant, or let’s say a subscription can only trust a single Entra tenant at a time.
There is a hierarchy for organizations, subscriptions, licenses, and user accounts for Microsoft cloud services:
An organization can have multiple subscriptions (using a management group).
A subscription can have multiple licenses.
Licenses can be assigned to individual user accounts.
User accounts are stored in a Microsoft Entra tenant.
This further establishes a relationship between subscriptions and tenants. Now let’s learn about the relationship between these two.
The Mapping between subscriptions and tenants
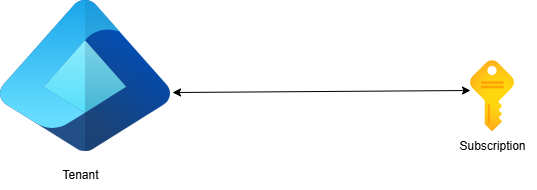
One-to-One Mapping
There is a one-to-one mapping between a subscription and a tenant; this means that a subscription can only be connected to one tenant at a time. The subscriptions depend on this tenant to authenticate and authorize identities and devices
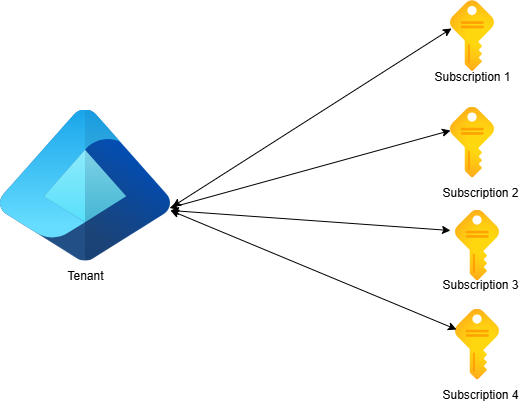
One-to-Many Mapping
A single Entra ID tenant can be associated with multiple Azure subscriptions. Remember from the hierarchy that you can have multiple subscriptions in an organization. You can link all these subscriptions to the same tenant, and this allows you to use the same users, roles, and permissions across these subscriptions.
Switching Tenants
While a subscription can only trust a tenant at a time, you can switch the tenant a subscription trusts to another if you have access to multiple tenants. But the resources you will see will be tied to the currently selected tenants, as well as the associated permissions.
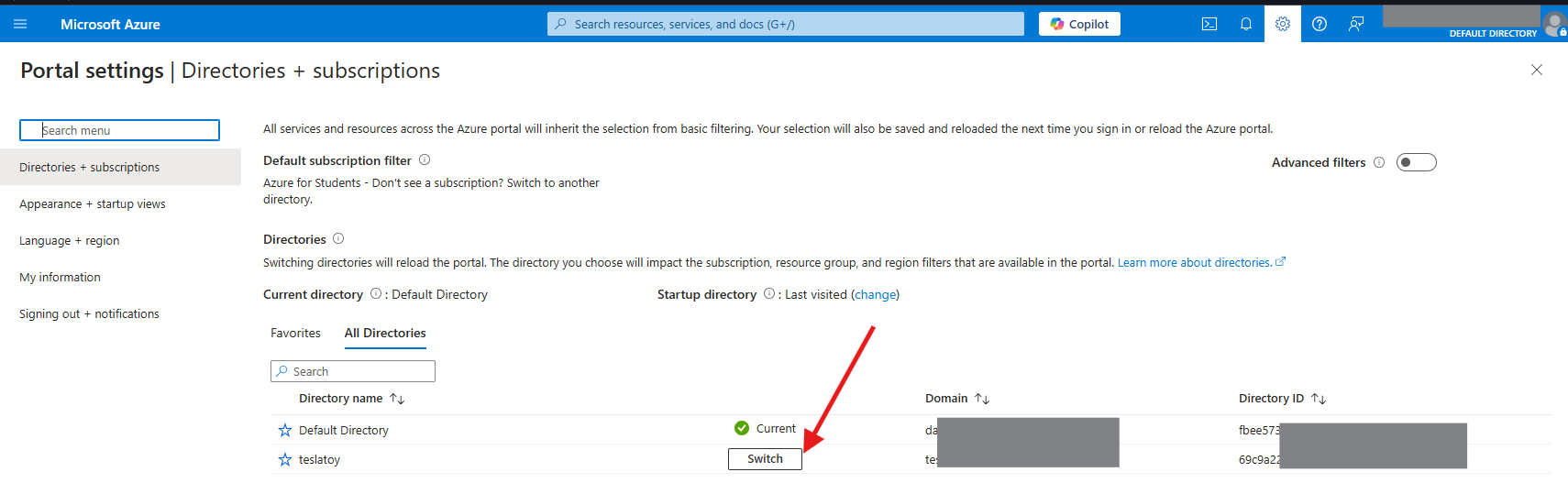
The prerequisites to achieve this are:
An active user account with permissions to change the directory tenant in your current subscription.
Be added by an admin in the other tenant you want to switch to, either as a user or a guest.
Be granted the needed permissions and roles in the new tenant.
Entra Roles
To be able to manage Entra tenants, you need some level of access and permissions to do it. This brings the concept of Entra roles; they are used for managing identities. This includes creating or editing users, assigning administrative roles to others, resetting user passwords, managing user licenses, and managing domains. Microsoft Entra roles operate primarily at the tenant level, focusing on Microsoft Entra resources. There are multiple default roles available in Microsoft Entra, each designed to grant specific permissions. Some of the prominent Microsoft Entra roles include:
Global Administrator: Has access to all administrative features in Microsoft Entra.
User Administrator: Manages aspects of users and groups.
Billing Administrator: Handles billing and subscription-related tasks.
Application Administrator: Manages all aspects of app registrations and enterprise apps.
Entra Roles vs Azure RBAC Roles
Entra roles are often mistaken for Azure RBAC (Role-Based Access Control) roles, but they serve distinct purposes. First, it's important to note that Microsoft Entra is not limited to Azure, It is a Microsoft-wide identity management service used across microsoft cloud offerings like Microsoft 365, Dynamics 365 and Azure. Because of this, Entra roles are strictly for managing identities and are typically scoped at the tenant level.
Azure RBAC roles are designed to control access and permissions for Azure resources. They follow the principle of least privilege, ensuring users have only the permissions necessary for their tasks. Azure RBAC roles can be assigned at different levels/scopes:
Management group level
Subscription level
Resource group level
Resource level
| Azure Roles | Entra Roles |
| Manage access to Azure resources | Manage access to Microsoft Entra resources |
| Scopes can be be specified at the management group, subscription, resource group, resource levels, respectively | Scopes can be specified at the tenant level, administrative units, or on individual objects such as a specific application. |
| Role information can be accessed in Azure portal, Azure CLI, Azure PowerShell, Azure Resource Manager templates, REST API | Role information can be accessed in the Azure portal, Microsoft Entra admin center, Microsoft 365 admin center, Microsoft Graph, Microsoft Graph PowerShell |
| Prominent roles include Owner, Contributor, Reader | Prominent roles include global administrator, user administator and application administrator. |
Subscribe to my newsletter
Read articles from Cloudville directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
