Secure OAuth 2.0 in React Native: Implementing RFC 8252
 Pawan Gangwani
Pawan GangwaniOAuth 2.0 is the industry standard for securing API access, but when implementing it in mobile apps, security best practices must be followed. RFC 8252, also known as "OAuth 2.0 for Native Apps," provides guidance on securely handling authorization flows in mobile applications, including React Native. In this blog, we'll walk through implementing secure OAuth 2.0 authentication in a React Native app while adhering to RFC 8252 guidelines.
Why Follow RFC 8252?
RFC 8252 outlines best practices that mitigate security risks like phishing, token interception, and unauthorized access. It recommends using the system browser for authentication instead of embedding login forms in the app. This approach ensures:
Better security: Users authenticate with their provider in a trusted environment.
SSO (Single Sign-On) support: Users stay logged in across multiple applications.
Protection against phishing: No credentials are entered directly in the app.
OAuth 2.0 Sequence Diagram
To better understand the sequence of interactions, here’s a sequence diagram illustrating the process:
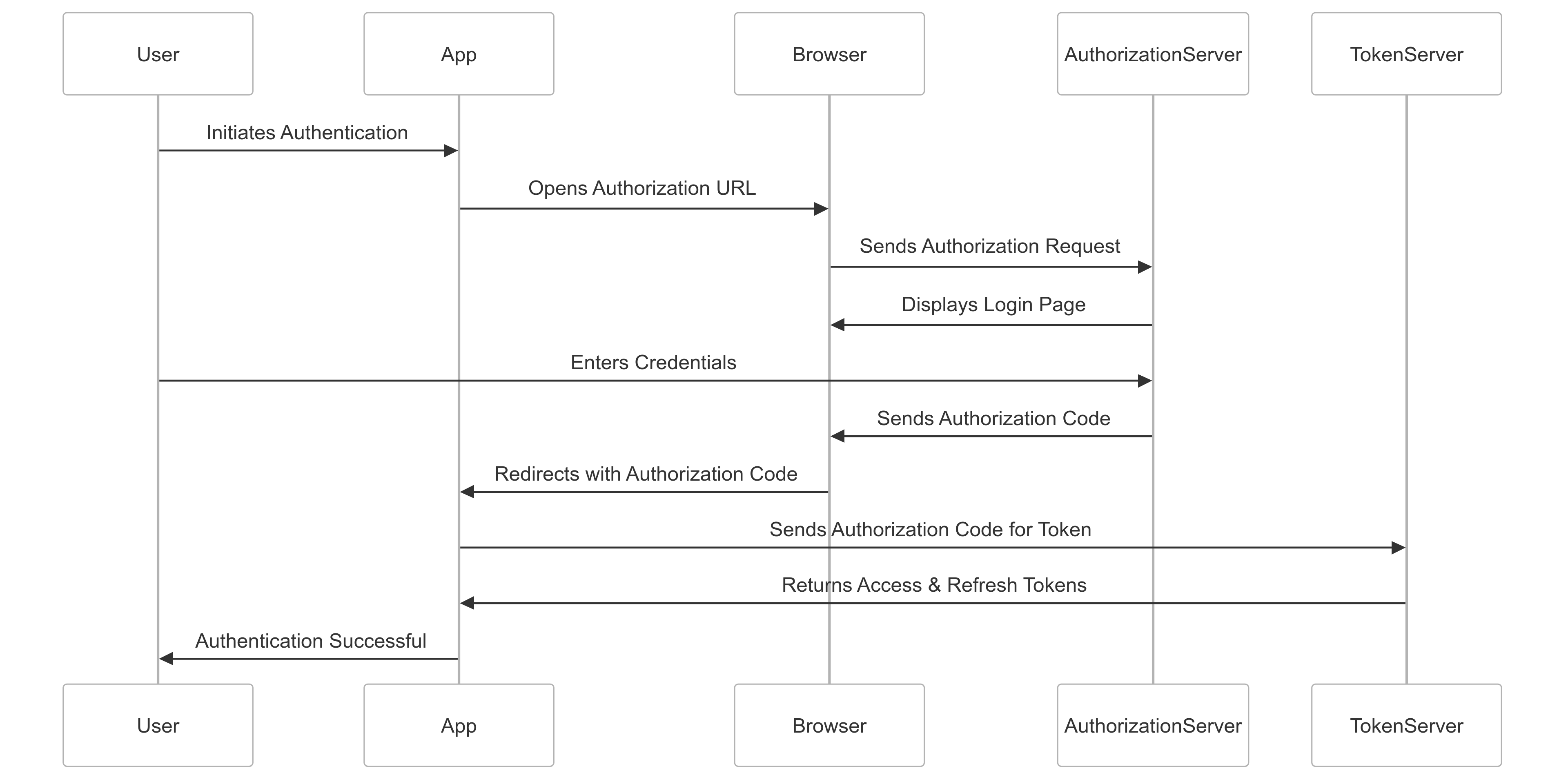
Steps to Implement OAuth 2.0 in React Native
1. Open the Authorization URL in the System Browser
Instead of using an embedded web view, open the authentication URL in the device’s default browser using React Native’s Linking API, as recommended by RFC 8252.
import { Linking } from 'react-native';
const authUrl = 'https://authorization-server.com/auth?client_id=YOUR_CLIENT_ID&redirect_uri=YOUR_REDIRECT_URI&response_type=code&scope=YOUR_SCOPES';
const initiateAuth = async () => {
const supported = await Linking.canOpenURL(authUrl);
if (supported) {
await Linking.openURL(authUrl);
} else {
console.error('Unable to open URL:', authUrl);
}
};
2. Handle Authorization Response
Once authentication is complete, the authorization server redirects the user back to the app using a custom scheme or a universal link, aligning with RFC 8252's recommendations.
Using a Custom URI Scheme
Register a deep link (e.g., myapp://oauth) in your app and use React Native’s Linking API to handle incoming authorization responses.
import { useEffect } from 'react';
import { Linking } from 'react-native';
useEffect(() => {
const handleUrl = (event) => {
const { url } = event;
// Extract authorization code from the URL
};
Linking.addEventListener('url', handleUrl);
return () => {
Linking.removeEventListener('url', handleUrl);
};
}, []);
3. Exchange Authorization Code for Tokens
Once you receive the authorization code, send it to the authorization server to obtain an access token securely.
import axios from 'axios';
const exchangeCodeForToken = async (code) => {
const tokenUrl = 'https://authorization-server.com/token';
const params = new URLSearchParams();
params.append('grant_type', 'authorization_code');
params.append('code', code);
params.append('redirect_uri', 'YOUR_REDIRECT_URI');
params.append('client_id', 'YOUR_CLIENT_ID');
params.append('code_verifier', 'YOUR_CODE_VERIFIER'); // If using PKCE
try {
const response = await axios.post(tokenUrl, params);
const { access_token, refresh_token } = response.data;
// Store tokens securely
} catch (error) {
console.error('Token exchange failed:', error);
}
};
4. Implement PKCE for Enhanced Security
Proof Key for Code Exchange (PKCE) prevents attackers from intercepting authorization codes. RFC 8252 strongly recommends PKCE for public clients, including mobile apps. Generate a code verifier and code challenge before making the authentication request.
import { encode as base64Encode } from 'base-64';
import { sha256 } from 'js-sha256';
const generateCodeVerifier = () => {
return [...Array(128)].map(() => Math.random().toString(36)[2]).join('');
};
const generateCodeChallenge = (codeVerifier) => {
const hashed = sha256.arrayBuffer(codeVerifier);
return base64Encode(String.fromCharCode.apply(null, new Uint8Array(hashed)))
.replace(/\+/g, '-')
.replace(/\//g, '_')
.replace(/=+$/, '');
};
const codeVerifier = generateCodeVerifier();
const codeChallenge = generateCodeChallenge(codeVerifier);
Conclusion
By following RFC 8252, your React Native app ensures secure authentication without compromising user experience. Using the system browser for OAuth 2.0 authentication, handling redirect URIs correctly, and implementing PKCE significantly improve security.
Would you like to see additional enhancements? Let me know in the comments!
Subscribe to my newsletter
Read articles from Pawan Gangwani directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Pawan Gangwani
Pawan Gangwani
I’m Pawan Gangwani, a passionate Full Stack Developer with over 12 years of experience in web development. Currently serving as a Lead Software Engineer at Lowes India, I specialize in modern web applications, particularly in React and performance optimization. I’m dedicated to best practices in coding, testing, and Agile methodologies. Outside of work, I enjoy table tennis, exploring new cuisines, and spending quality time with my family.