📌Part 1 Streamlining AWS Infrastructure for Kubernetes: A Guide to Terraform & Ansible Setup
 Vikas Surve
Vikas Surve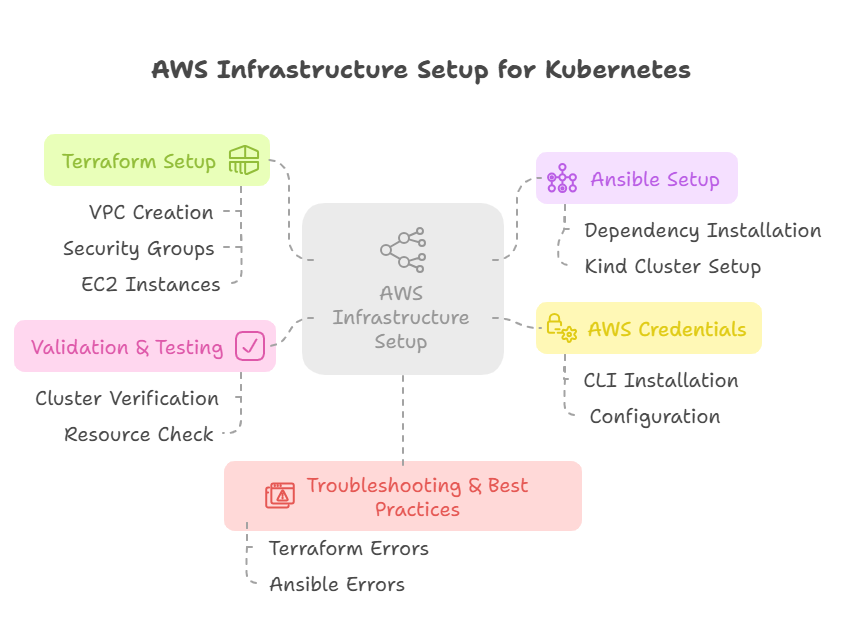
1️⃣ Overview
This section covers automating AWS infrastructure setup for Kubernetes using:
✅ Terraform Modules for AWS Infrastructure
✅ Ansible Roles for Configuring EC2 Instances
✅ IAM Roles, Security Enhancements, and System Optimizations
✅ Troubleshooting and Best Practices
By the end of this guide, you’ll have a production-ready AWS environment for Kubernetes.
2️⃣ AWS Credentials & Configuration
🔹 Why is this important?
AWS authentication is required for Terraform and Ansible to create and manage resources.
🔹 Step 1: Install AWS CLI
curl "https://awscli.amazonaws.com/AWSCLIV2.pkg" -o "AWSCLIV2.pkg"
sudo installer -pkg AWSCLIV2.pkg -target /
🔹 Step 2: Configure AWS Credentials
aws configure
Enter your credentials:
AWS Access Key ID [None]: AKIAXXXXXXXXXXXXX
AWS Secret Access Key [None]: XXXXXXXXXXXXXXXXXXXXXXXX
Default region name [None]: us-east-1
Default output format [None]: json
🔹 Step 3: Verify AWS Access
aws sts get-caller-identity
✅ Expected Output:
{
"UserId": "AIDAEXAMPLEID",
"Account": "123456789012",
"Arn": "arn:aws:iam::123456789012:user/Admin"
}
3️⃣ Terraform Setup for AWS Infrastructure
🔹 Why Use Terraform Modules?
Modular & Reusable: Allows different teams to manage VPC, EC2, Security Groups independently.
Scalability: Makes infrastructure modifications easy.
Consistency: Avoids manual setup errors.
🔹 Terraform Directory Structure
terraform-setup/
│── modules/
│ │── vpc/
│ │ ├── main.tf
│ │ ├── variables.tf
│ │ ├── outputs.tf
│ │── ec2/
│ │ ├── main.tf
│ │ ├── variables.tf
│ │ ├── outputs.tf
│── main.tf
│── variables.tf
│── outputs.tf
│── terraform.tfvars
🔹 Module 1: VPC (modules/vpc/main.tf)
Creates a VPC and Subnet for Kubernetes networking.
resource "aws_vpc" "main" {
cidr_block = var.vpc_cidr
enable_dns_support = true
enable_dns_hostnames = true
}
resource "aws_subnet" "public_subnet" {
vpc_id = aws_vpc.main.id
cidr_block = var.subnet_cidr
map_public_ip_on_launch = true
}
Variables (modules/vpc/variables.tf)
variable "vpc_cidr" { default = "10.0.0.0/16" }
variable "subnet_cidr" { default = "10.0.1.0/24" }
🔹 Module 2: Security Groups (modules/security/main.tf)
Manages network security by restricting access.
resource "aws_security_group" "k8s_sg" {
vpc_id = var.vpc_id
ingress {
from_port = 22
to_port = 22
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
ingress {
from_port = 80
to_port = 80
protocol = "tcp"
cidr_blocks = ["0.0.0.0/0"]
}
egress {
from_port = 0
to_port = 0
protocol = "-1"
cidr_blocks = ["0.0.0.0/0"]
}
}
🔹 Module 3: IAM Role for EC2 (modules/iam/main.tf)
Allows EC2 to interact with AWS services.
resource "aws_iam_role" "ec2_role" {
name = "ec2-k8s-role"
assume_role_policy = <<EOF
{
"Version": "2012-10-17",
"Statement": [
{
"Effect": "Allow",
"Principal": {
"Service": "ec2.amazonaws.com"
},
"Action": "sts:AssumeRole"
}
]
}
EOF
}
🔹 Module 4: EC2 Instance (modules/ec2/main.tf)
Deploys an EC2 instance with Ubuntu.
resource "aws_instance" "ec2" {
ami = "ami-0c55b159cbfafe1f0"
instance_type = var.instance_type
subnet_id = var.subnet_id
key_name = var.key_name
iam_instance_profile = aws_iam_role.ec2_role.name
}
🔹 Deploy Terraform Configuration
terraform init
terraform apply -auto-approve
✅ Sample Output:
Apply complete! Resources: 5 added.
ec2_public_ip = "3.85.76.182"
4️⃣ Ansible Setup for Kubernetes Dependencies
🔹 Why Use Ansible?
Automates EC2 Configuration (installs Docker, Kind, kubectl).
Ensures Consistency across multiple instances.
🔹 Ansible Directory Structure
ansible-setup/
│── roles/
│ │── common/
│ │ ├── tasks/
│ │ │ ├── main.yml
│ │── kubernetes/
│ │ ├── tasks/
│ │ │ ├── main.yml
│── inventory.ini
│── setup.yml
🔹 Role: Install Dependencies (roles/common/tasks/main.yml)
- name: Install dependencies
apt:
name: ['docker.io', 'curl']
state: present
update_cache: yes
🔹 Role: Setup Kind Cluster (roles/kubernetes/tasks/main.yml)
- name: Install Kind
shell: |
curl -Lo ./kind https://kind.sigs.k8s.io/dl/v0.20.0/kind-linux-amd64
chmod +x ./kind
sudo mv ./kind /usr/local/bin/kind
- name: Create Kind Cluster
shell: kind create cluster --name easyshop
🔹 Ansible Playbook (setup.yml)
- name: Setup Kubernetes Cluster
hosts: servers
become: yes
roles:
- common
- kubernetes
5️⃣ Validation & Testing
Check if Kind Cluster is Running
kubectl get nodes
✅ Expected Output:
NAME STATUS ROLES AGE VERSION
kind-control-plane Ready master 2m v1.28.0
6️⃣ Troubleshooting & Best Practices
Common Terraform Errors
"IAM role does not exist" → Ensure the IAM role is created before EC2 starts.
"Security group not found" → Check that Security Groups are correctly referenced.
Common Ansible Errors
SSH Connection Issues → Ensure EC2 key pair matches the one defined in Terraform.
Permission Denied → Use
become: yesin Ansible tasks for elevated privileges.
🎯 Conclusion
🚀 AWS infrastructure is now production-ready!
✅ Terraform Modules for VPC, Security, IAM, EC2
✅ Ansible Roles for Configuring Kubernetes Dependencies
Subscribe to my newsletter
Read articles from Vikas Surve directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Vikas Surve
Vikas Surve
I am an 𝗠𝗦 𝗖𝗲𝗿𝘁𝗶𝗳𝗶𝗲𝗱 𝗗𝗲𝘃𝗢𝗽𝘀 𝗘𝗻𝗴𝗶𝗻𝗲𝗲𝗿 𝗘𝘅𝗽𝗲𝗿𝘁 and 𝗔𝘇𝘂𝗿𝗲 𝗔𝗱𝗺𝗶𝗻𝗶𝘀𝘁𝗿𝗮𝘁𝗼𝗿 𝗔𝘀𝘀𝗼𝗰𝗶𝗮𝘁𝗲 with over 𝟭𝟬 𝘆𝗲𝗮𝗿𝘀 𝗼𝗳 𝗲𝘅𝗽𝗲𝗿𝗶𝗲𝗻𝗰𝗲 in designing, implementing, and optimizing DevOps solutions. My expertise includes 𝗖𝗜/𝗖𝗗 𝗮𝘂𝘁𝗼𝗺𝗮𝘁𝗶𝗼𝗻 𝘂𝘀𝗶𝗻𝗴 𝗚𝗶𝘁𝗟𝗮𝗯, 𝗝𝗲𝗻𝗸𝗶𝗻𝘀, 𝗮𝗻𝗱 𝗔𝘇𝘂𝗿𝗲 𝗗𝗲𝘃𝗢𝗽𝘀, as well as 𝗖𝗼𝗻𝘁𝗮𝗶𝗻𝗲𝗿 𝗼𝗿𝗰𝗵𝗲𝘀𝘁𝗿𝗮𝘁𝗶𝗼𝗻 𝘄𝗶𝘁𝗵 𝗗𝗼𝗰𝗸𝗲𝗿 𝗮𝗻𝗱 𝗞𝘂𝗯𝗲𝗿𝗻𝗲𝘁𝗲𝘀. 🔹 𝗘𝘅𝗽𝗲𝗿𝘁 𝗶𝗻 𝗱𝗲𝘀𝗶𝗴𝗻𝗶𝗻𝗴 𝗮𝗻𝗱 𝗺𝗮𝗻𝗮𝗴𝗶𝗻𝗴 𝗲𝗻𝗱-𝘁𝗼-𝗲𝗻𝗱 𝗖𝗜/𝗖𝗗 𝗽𝗶𝗽𝗲𝗹𝗶𝗻𝗲𝘀 🔹 𝗛𝗮𝗻𝗱𝘀-𝗼𝗻 𝗲𝘅𝗽𝗲𝗿𝗶𝗲𝗻𝗰𝗲 𝘄𝗶𝘁𝗵 𝗔𝘇𝘂𝗿𝗲, 𝗞𝘂𝗯𝗲𝗿𝗻𝗲𝘁𝗲𝘀 (𝗔𝗞𝗦), 𝗮𝗻𝗱 𝗧𝗲𝗿𝗿𝗮𝗳𝗼𝗿𝗺 𝗳𝗼𝗿 𝘀𝗰𝗮𝗹𝗮𝗯𝗹𝗲 𝗱𝗲𝗽𝗹𝗼𝘆𝗺𝗲𝗻𝘁𝘀 🔹 𝗣𝗮𝘀𝘀𝗶𝗼𝗻𝗮𝘁𝗲 𝗮𝗯𝗼𝘂𝘁 𝗮𝘂𝘁𝗼𝗺𝗮𝘁𝗶𝗼𝗻, 𝘀𝗲𝗰𝘂𝗿𝗶𝘁𝘆, 𝗮𝗻𝗱 𝗰𝗹𝗼𝘂𝗱-𝗻𝗮𝘁𝗶𝘃𝗲 𝘁𝗲𝗰𝗵𝗻𝗼𝗹𝗼𝗴𝗶𝗲𝘀 🛠 𝗦𝗸𝗶𝗹𝗹𝘀 & 𝗧𝗼𝗼𝗹𝘀 ✅ 𝗗𝗲𝘃𝗢𝗽𝘀 & 𝗖𝗜/𝗖𝗗: Azure DevOps, GitLab, Jenkins ✅ 𝗖𝗹𝗼𝘂𝗱 & 𝗜𝗻𝗳𝗿𝗮𝘀𝘁𝗿𝘂𝗰𝘁𝘂𝗿𝗲: Azure, AWS ✅ 𝗜𝗻𝗳𝗿𝗮𝘀𝘁𝗿𝘂𝗰𝘁𝘂𝗿𝗲 𝗮𝘀 𝗖𝗼𝗱𝗲 (𝗜𝗮𝗖): Terraform, Bicep ✅ 𝗖𝗼𝗻𝘁𝗮𝗶𝗻𝗲𝗿𝘀 & 𝗢𝗿𝗰𝗵𝗲𝘀𝘁𝗿𝗮𝘁𝗶𝗼𝗻: Docker, Kubernetes (AKS) ✅ 𝗖𝗼𝗻𝗳𝗶𝗴 𝗠𝗮𝗻𝗮𝗴𝗲𝗺𝗲𝗻𝘁: PowerShell, Shell Scripting ✅ 𝗠𝗼𝗻𝗶𝘁𝗼𝗿𝗶𝗻𝗴 & 𝗢𝗯𝘀𝗲𝗿𝘃𝗮𝗯𝗶𝗹𝗶𝘁𝘆: Grafana, Prometheus, Azure Monitor ✅ 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 & 𝗡𝗲𝘁𝘄𝗼𝗿𝗸𝗶𝗻𝗴: Load Balancers, Firewalls, ClusterIP ✅ 𝗢𝗽𝗲𝗿𝗮𝘁𝗶𝗻𝗴 𝗦𝘆𝘀𝘁𝗲𝗺𝘀: Linux, Mac 💡 𝗞𝗲𝘆 𝗦𝘁𝗿𝗲𝗻𝗴𝘁𝗵𝘀 ✔ 𝗖𝗹𝗼𝘂𝗱 𝗔𝗿𝗰𝗵𝗶𝘁𝗲𝗰𝘁𝘂𝗿𝗲 & 𝗔𝘂𝘁𝗼𝗺𝗮𝘁𝗶𝗼𝗻 – Designing and managing scalable cloud solutions ✔ 𝗖𝗜/𝗖𝗗 & 𝗗𝗲𝘃𝗢𝗽𝘀 𝗟𝗲𝗮𝗱𝗲𝗿𝘀𝗵𝗶𝗽 – Implementing robust and automated software delivery pipelines ✔ 𝗧𝗲𝗮𝗺 𝗟𝗲𝗮𝗱𝗲𝗿𝘀𝗵𝗶𝗽 & 𝗠𝗲𝗻𝘁𝗼𝗿𝘀𝗵𝗶𝗽 – Leading a 5-member team, fostering collaboration and growth ✔ 𝗦𝗲𝗰𝘂𝗿𝗶𝘁𝘆 & 𝗖𝗼𝗺𝗽𝗹𝗶𝗮𝗻𝗰𝗲 – Ensuring cloud security, compliance, and best practices ✔ 𝗣𝗿𝗼𝗯𝗹𝗲𝗺 𝗦𝗼𝗹𝘃𝗶𝗻𝗴 & 𝗢𝗽𝘁𝗶𝗺𝗶𝘇𝗮𝘁𝗶𝗼𝗻 – Driving efficiency through automation and DevOps practices ✔ 𝗖𝗼𝗻𝘁𝗶𝗻𝘂𝗼𝘂𝘀 𝗟𝗲𝗮𝗿𝗻𝗶𝗻𝗴 & 𝗜𝗻𝗻𝗼𝘃𝗮𝘁𝗶𝗼𝗻 – Exploring emerging technologies and best practices