Service Principal vs. Managed Identity in Azure: A Quick Guide
 Iresh Ekanayaka
Iresh EkanayakaWhen working with Azure, managing authentication and access to resources securely is crucial. Two common approaches for enabling applications and services to authenticate without using user credentials are Service Principals and Managed Identities. Let’s break down their differences and use cases.
🔹 What is a Service Principal?
A Service Principal is an identity created in Azure Active Directory (Azure AD) to authenticate applications or automation processes. It enables fine-grained access control by assigning specific roles and permissions to a non-human identity.
How to Create a Service Principal (CLI Method):
az ad sp create-for-rbac --name "my-app" --role "Contributor" --scopes "/subscriptions/{subscription-id}"
After running the above command, you will receive output containing essential credentials:
{
"appId": "<client_id>",
"password": "<client_secret>",
"tenant": "<tenant_id>"
}
appId →
client_idpassword →
client_secrettenant →
tenant_id
How to Create a Service Principal (Portal Method):
Navigate to Azure Portal → Azure Active Directory.
Select App registrations → New registration.
Provide a name, select the supported account types, and register the application.
Go to Certificates & secrets to generate a client secret.
Assign necessary RBAC roles under Azure subscriptions.
Key Points:
✅ Requires manual management of secrets or certificates.
✅ Can be used for automation, scripts, or CI/CD pipelines.
✅ Supports role-based access control (RBAC).
✅ Needs explicit lifecycle management (creation, rotation, deletion).
🔹 What is a Managed Identity?
A Managed Identity is an Azure feature that eliminates the need for managing credentials. Azure automatically handles authentication when resources (like Virtual Machines, Functions, and App Services) need access to other Azure services.
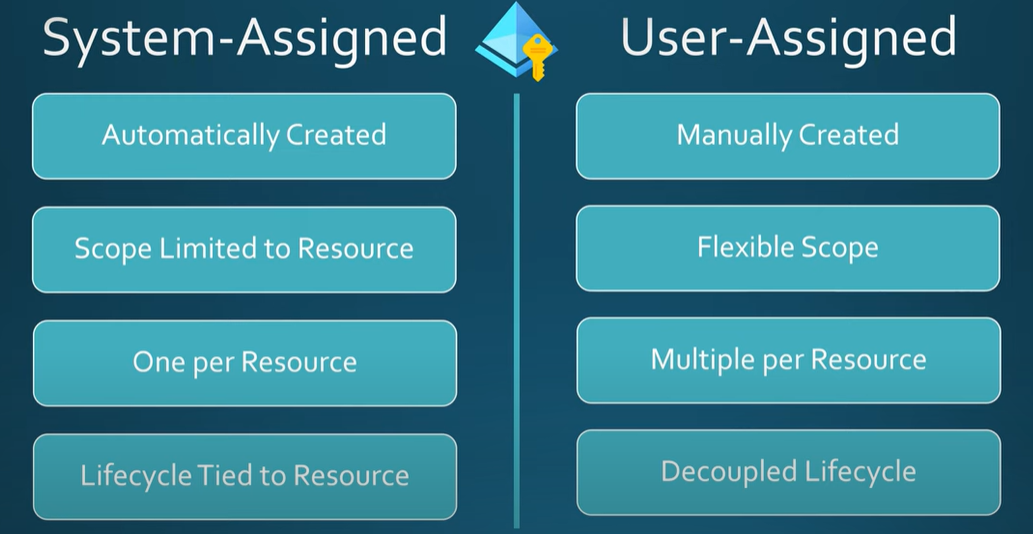
Types of Managed Identities:
System-assigned – Tied to a single Azure resource and deleted when the resource is deleted.
User-assigned – Created independently and can be assigned to multiple resources.
How to Enable a System-Assigned Managed Identity (CLI Method):
az vm identity assign --resource-group myResourceGroup --name myVM
How to Enable a Managed Identity (Portal Method):
Navigate to Azure Portal → Your Resource (VM, App Service, etc.).
Go to Identity under the settings.
Enable System-assigned or User-assigned identity.
Assign necessary RBAC roles under Azure subscriptions.
Key Points:
✅ No need to manage credentials manually.
✅ Seamless integration with Azure services.
✅ Automatically rotates credentials for security.
✅ System-assigned identities are tied to a specific resource, while user-assigned identities can be shared.
🔹 When to Use Which?
| Use Case | Service Principal | Managed Identity |
| CI/CD Pipelines | ✅ | ❌ |
| Cross-Cloud Authentication | ✅ | ❌ |
| VM to Azure Storage Authentication | ❌ | ✅ |
| Long-Term Secrets Management | ✅ | ❌ |
| Automatic Credential Rotation | ❌ | ✅ |
🔹 Final Thoughts
Both Service Principals and Managed Identities serve specific purposes. If you need a reusable identity for automation, Service Principals are the way to go. If you want a secure and hassle-free authentication method for Azure resources, Managed Identities are the best choice.
Which one do you use the most? Let me know in the comments! 🚀
Subscribe to my newsletter
Read articles from Iresh Ekanayaka directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
