Satoshi Scoop Weekly, 28 Mar 2025
 Cryptape
CryptapeTable of contents
- Crypto Insights
- Proposal and Discussion on Introducing a New Bitcoin Script Opcode: OP_ISSUBSTR
- Discussion on Bitcoin’s Next Major Upgrade: Evaluating OP_CAT and OP_CTV
- Implementing Post-Signature Cross-Input Scripting in Bitcoin Using Taproot Annex
- Can Orphan Block Reporting Effectively Prevent Selfish Mining? A Complex Reality
- LND Introduces Rewritten Sweeper Subsystem to Optimize Batch Transactions and Fee Bumping
- Analysis of Invalid Mining by AntPool and Associated Pools
- Payjoin Roadmap: From a Two-Party Protocol to a Multi-Party Collaboration Model
- Embedding Sats into Memes and Emojis
- Complete Guide to Buying Bitcoin Anonymously
- Global Cryptocurrency Tax Map
- Binance Report: The Future of Bitcoin—DeFi
- Top Reads on Blockchain and Beyond
Crypto Insights
Proposal and Discussion on Introducing a New Bitcoin Script Opcode: OP_ISSUBSTR
This BIP proposes the introduction of two new opcodes: OP_ISSUBSTR and OP_ISSUBSTRVERIFY. Their relationship is similar to OP_EQUAL and OP_EQUALVERIFY used to determine whether one string is a substring of another. Bitcoin developers have mixed opinions on this.
Supporters:
Enhancing script functionality: Enables direct on-chain string operations, reducing reliance on off-chain processing and centralized dependencies.
Simplifies certain use cases: Some applications (e.g., verifying if a public key contains a specific substring) would be easier to implement with OP_ISSUBSTR.
OP_CAT is not a perfect substitute: Although OP_CAT can be used for string operations, it has security concerns and limitations, such as stack size limits.
Opponents:
Bitcoin Script is for validation, not computation: Peter Todd argues that substring searching can be achieved using concatenation (OP_CAT) and equality checks (OP_EQUAL), making OP_ISSUBSTR unnecessary.
Alternative script solutions exist: Some developers demonstrated that the proposed functionality can be emulated by having the script reconstruct the original string with known and unknown parts.
Potential stack management issues: Concerns exist regarding stack size limits and whether OP_ISSUBSTR offers sufficient benefits.
Discussion on Bitcoin’s Next Major Upgrade: Evaluating OP_CAT and OP_CTV
This analysis explores Bitcoin’s potential next major upgrade: OP_CAT (BIP 347) and OP_CTV (BIP 119). Both aim to enhance Bitcoin’s transaction programmability by enabling spending conditions on transaction outputs, improving script expressiveness.
The report explains how OP_CAT enables recursive contracts and trustless Bitcoin bridges, supporting BitVM development, while OP_CTV improves efficiency for vaults and rollup-based complex transactions.
It predicts that Bitcoin Core developers are expected to reach consensus on adding OP_CAT or OP_CTV this year, but due to the extensive activation process, actual implementation may take 1–2 years.
Implementing Post-Signature Cross-Input Scripting in Bitcoin Using Taproot Annex
A new method has been proposed to introduce cross-input scripting using Taproot annex. This allows users to commit to additional spending conditions when signing transactions, expanding Bitcoin scripting capabilities and transaction flexibility.
Can Orphan Block Reporting Effectively Prevent Selfish Mining? A Complex Reality
A common belief is that incorporating orphan block counts in Bitcoin’s Difficulty Adjustment Mechanism (DAM) can make selfish mining unprofitable. However, this study refutes that view by analyzing the time-averaged profit of selfish mining.
The research also introduces two improved DAM models considering both main-chain and orphaned blocks, along with two smart intermittent selfish mining strategies—one outperforming standard intermittent selfish mining and the other remaining profitable under the modified DAM.
Additionally, the study describes an "orphan exclusion attack," where attackers prevent honest miners from reporting orphan blocks. Using combinatorial tools, the research examines the profitability of selfish mining under the improved DAM when combined with orphan exclusion attacks. Results indicate that even with orphan block inclusion, selfish mining remains profitable. However, under the modifed DAM, profitability significantly decreases compared to Bitcoin's current DAM, suggesting that orphan block reporting can be an effective mitigation strategy against a payoff-maximizing selfish miner.
Read the full paper.
LND Introduces Rewritten Sweeper Subsystem to Optimize Batch Transactions and Fee Bumping
According to the author, starting from v0.18.0, Lightning Network Daemon (LND) will completely revamp its sweeper subsystem for managing transaction batching and fee bumping.
The new sweeper integrates HTLC deadlines and fee budgets to compute a fee rate curve, dynamically adjusting fees based on transaction urgency. This new fee bumping strategy provides security benefits that other Lightning Network implementations may find valuable to adopt.
Analysis of Invalid Mining by AntPool and Associated Pools
boerst observed unusual block templates submitted at height 885797 by Antpool, CloverPool, Ultimus, Rawpool, and Poolin. The anomalies suggest possible selfish mining or template code issues. Suspicious signs include:
Empty Merkle branches, yet the coinbase output total exceeds the subsidy, implying fees are being collected for non-existent transactions.
The previous block hash for these is different from the rest of the pools and points to a block that seems to have never made it into the chain.
b10c's analysis suggests this may be a bug in AntPool’s coinbase transaction creation process. The findings indicate these pools may be operated by the same entity. It might be time to refer to AntPool and its associated pools (Braiins, Poolin, Binance Pool, and Ultimus, among others) collectively as "AntPool & Friends."
Payjoin Roadmap: From a Two-Party Protocol to a Multi-Party Collaboration Model
The Payjoin Dev Kit (PDK) team outlined the evolution of Payjoin from a two-party protocol to a multi-party framework. Payjoin V3 will address the limitations of the two-party model by introducing a collaboration model. The final goal is a "coalition formation protocol" that allows unconnected Bitcoin users to contribute to batch transactions.
The four development stages are:
Stage 0: Multi-sender, single-receiver (current stage)
Stage 1: Multi-sender, multi-receiver
Stage 2: Privacy optimization
Stage 3: Decentralized market mechanism—developing a coalition formation protocol to enable unconnected Bitcoin users to contribute to batch transactions
Embedding Sats into Memes and Emojis
This article explores how memeamigo.lol encodes Bitcoin-based Cashu into memes, embedding sats into emojis and memes like this and this.
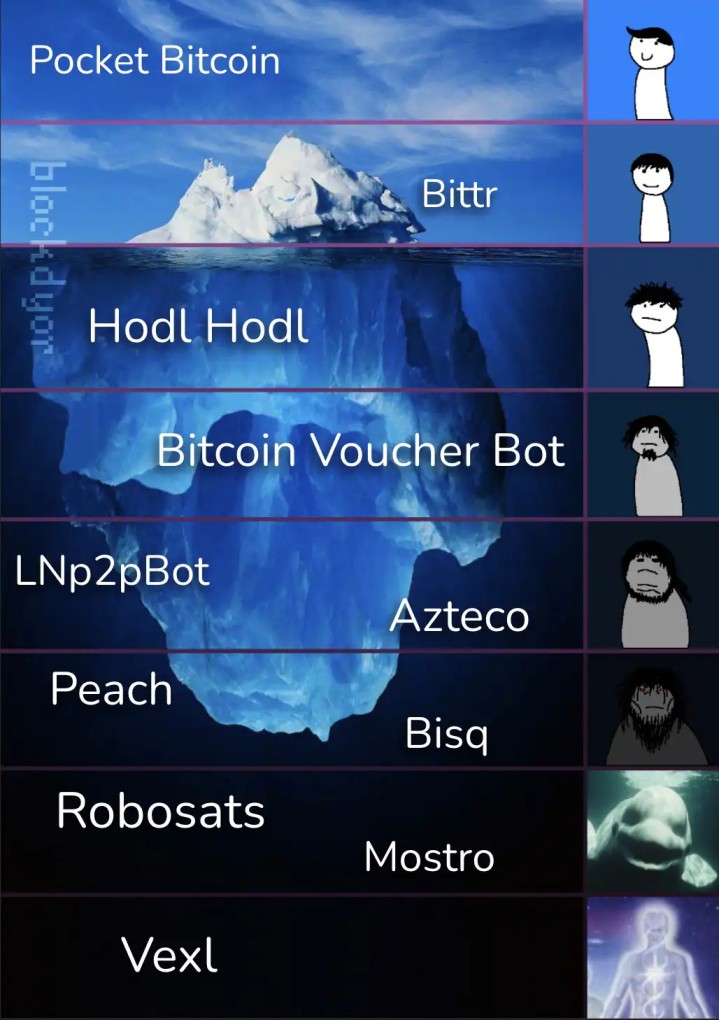
Complete Guide to Buying Bitcoin Anonymously
The author compares several Bitcoin exchanges, categorizing them based on decentralization and peer-to-peer features:
Decentralized & P2P
Centralized & P2P
Centralized & non-P2P (light KYC)
Each type has its own advantages and drawbacks, and the best choice depends on the user’s priorities regarding privacy, ease of use, and legal compliance.
Global Cryptocurrency Tax Map
Hellosafe.ca provides a global crypto tax map, offering an overview of different tax policies worldwide.
Binance Report: The Future of Bitcoin—DeFi
Binance released a report on Bitcoin DeFi. Key takeaways include:
Security Budget & the Role of BTCFi: With Bitcoin’s block rewards continuously halving, its security model faces long-term sustainability challenges. BTCFi helps sustain miner incentives by increasing on-chain transaction fees, thereby strengthening Bitcoin’s long-term security budget.
Infrastructure as a Bottleneck: Bitcoin L2s are still in their early stages and require further development, adoption, and liquidity incentives to scale effectively.
Liquidity & Institutional Interest: Bitcoin investors have traditionally been long-term holders, posing challenges for liquidity provisioning. New incentive mechanisms are needed to activate idle BTC funds. While institutional investors have shown initial interest, large-scale adoption depends on regulatory clarity and user-friendly solutions.
Cross-Chain Interoperability is Crucial: Most Bitcoin used in DeFi currently exists as Wrapped BTC on Ethereum and other chains. BTCFi needs secure cross-chain solutions to bridge liquidity and attract users from existing DeFi ecosystems.
BTCFi Needs Its Own Path: Unlike Ethereum’s DeFi ecosystem, BTCFi cannot simply replicate existing models. Its success may rely on tailored solutions that align with Bitcoin holders' needs, particularly in yield generation, payments, and institutional-grade products.
Top Reads on Blockchain and Beyond
Infinite Recursion of Trust: Reflections on Trust
In Reflections on Trusting Trust, Ken Thompson reveals the fragility of software trust. By describing a potential "Trojan horse" attack, he highlights a philosophical and technical dilemma: verifying a system’s trustworthiness requires a trusted tool, but that tool itself needs another tool for verification—leading to infinite recursion. Ultimately, trust must be placed in a foundational layer, which may itself be unverifiable.
Contextual Trust Networks and Privacy: A Critical Analysis of Metadata, Surveillance, and Routing Dynamics in Decentralized Systems
This article critically examines contextual trust networks as an alternative to traditional privacy protection techniques in decentralized systems like Bitcoin and P2P networks. It first highlights inherent privacy limitations in popular anonymity-enhancing methods:
CoinJoin and Mixnets: Rely on anonymity sets but remain vulnerable to metadata correlation at ingress and egress points, providing surveillance opportunities for adversaries.
Onion Routing (Tor): Tor reduces direct metadata exposure but is still susceptible to persistent statistical traffic analysis at entry and exit nodes, compromising anonymity over time.
Distributed Hash Tables (DHTs): Broadcast metadata widely, inherently increasing visibility and surveillance risks.
The author then contrasts these with the contextual trust concept introduced by the Atomicity protocol. The analysis suggests that witness-generated metadata is a primary privacy risk and argues that contextual trust channels can enhance privacy by controlling witness selection and excluding irrelevant nodes during transaction routing.
Subscribe to my newsletter
Read articles from Cryptape directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
