SUID Binaries: A Double-Edged Sword in Linux Security
 Victor Ukoha
Victor Ukoha
PREREQUISITE
Before diving into SUID binaries, readers should have a basic understanding of:
Linux file permissions
Command-line usage
User roles and privilege escalation
INTRODUCTION
In Linux and Unix-based systems, the permission character set represents the basic access control and authorization level. Files, directories, scripts, etc., have permissions defining who and what actions are allowed on these. Like every other file, binaries and executables also have permissions set, which can be modified. Some of these binaries are over-privileged and result in being targeted by threat actors to escalate privileges, horizontally and vertically.

WHAT ARE SUID BINARIES?
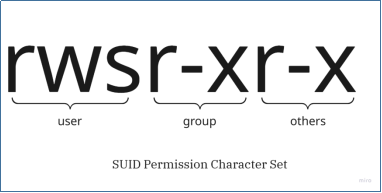
The Set User ID (SUID) binaries are a type of executable file with permissions slightly different from the common permission character set. These are binaries with a special character, s, in the permissions character set (I.e. they have a special permission bit set). These binaries are executed as the owner’s privileges rather than the privileges of the user executing it. This feature enables users to perform functions such as changing passwords, accessing restricted resources, etc., without having full and extended privileges (in this case, root privileges).

The SUID bit is set in the file permission with an s in the user’s permissions as shown above.
HOW TO SET SUID BITS
The chmod command is used to set SUID bits in files and binaries. Either of the following methods can be used to set these bits:
Using the symbolic method:
chmod u+s filename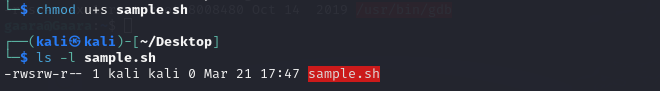
Using the octal method:
chmod 4755 filename
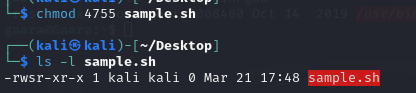
You can verify the updated permission with the command ls -l filename
EXPLOITING SUID BINARIES
Attackers find SUID binaries in systems to exploit as the following are common risks associated with these binaries:
Unintended privilege escalation.
Unauthorized access to sensitive files or system resources.
Potential for buffer overflow or other code execution vulnerabilities.
To exploit these binaries there are no hard and fast rules to doing so. However, the following steps outlined can serve as a guide and template:
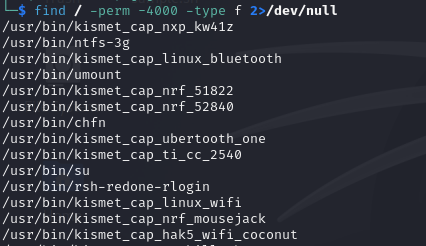
- First, find all SUID binaries using the command:
find / -perm -4000 -type f 2>/dev/null
This command will search the entire filesystem for files (-type f) with the SUID bit set (-perm -4000), beginning with the root directory (/). The 2>/dev/null section redirects any error messages (such as "permission denied") to /dev/null, thus removing them from the output.
- The next step is to identify exploitable binaries. Once a SUID binary has been identified, the following can be done to check if it is exploitable or not via:
Researching for known vulnerabilities such as buffer flow, etc.
Checking if it allows command execution,
Searching GTFOBins for potential exploits.
SUID SECURITY IMPLEMENTATION AND MONITORING
As a consequence of the security risks associated with SUID binaries, certain measures can be implemented to mitigate these risks:
Minimize SUID Usage:
It is important to only allow SUID on essential binaries. If elevated privileges are not required in binaries, remove or disable the SUID bits on them. Using the command below, remove SUID bit on a binary:
chmod u-s filename
Restrict Executions:
Use AppArmor or SELinux to limit which users and processes can execute SUID binaries.
Regular Audits and Monitoring:
Regular checks on the system to identify unnecessary or newly introduced SUID binaries help to identify suspicious behaviour. Also, monitoring these binaries and their executions provides for identifying SUID binaries abuse. Either of the following techniques can be used to audit and monitor SUID binaries:
- Auditing using Linux Audit Daemon (auditd): Utilities associated with audits, such as ausearch, auditctl, etc., can be used to monitor and track the execution of specified SUID binaries as shown below:
auditctl -a always,exit -F path=/path/to/suid_binary -F perm=x -k suid_exec
Check system logs: Monior /var/log/auth.log and /var/log/syslog for unusal activity.
Use Intrusion Detection Systems(IDS): Tools like AIDE or OSSEC can alert administrators when new SUID binaries appear.
CONCLUSION
SUID binaries serve an essential function in Linux and Unix-based systems; however, they pose serious security risks if misconfigured. Understanding their operation, exploitation and how to secure them is crucial for maintaining a secure system. Regular audit, proper access controls, and continuous monitoring are key techniques employed in mitigating SUID-related threats.
REFERENCES
Subscribe to my newsletter
Read articles from Victor Ukoha directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by
