AWS VPC Peering Made Easy — A Real-World Problem Solving Guide
 Soumo Sarkar
Soumo Sarkar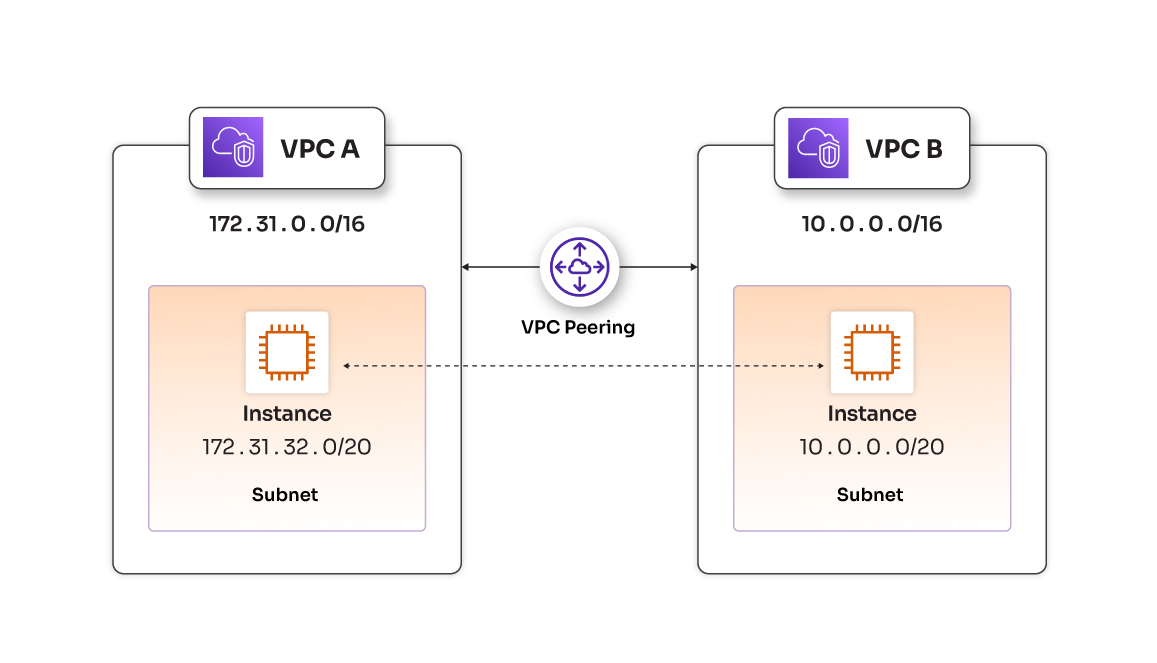
"How do I connect two different AWS VPCs securely and privately?"
If you've ever wondered about this, VPC Peering is the superhero you’ve been waiting for. In this article, let's break it down using a real-life scenario so you’ll never forget it!
A Real-World Scenario
Imagine you’re the DevOps lead at CloudFizz Inc., a fast-growing startup running two AWS environments:
Production VPC (172.31.0.0/16): Hosts customer-facing apps.
Testing VPC (10.0.0.0/16): Used for pre-release testing.
The Problem:
Your testing team needs to access a PostgreSQL database in the Production VPC to validate data migrations. But exposing the database to the public internet via a VPN or Elastic IP is a security nightmare. How do you connect these two VPCs securely and cost-effectively without rearchitecting everything?
Here comes VPC Peering – Your Private Highway Between AWS Networks.
What is VPC Peering? (In Layman's terms)
Think of VPCs as private gated communities in the cloud. VPC Peering is like building a direct, secure tunnel between two such communities. No traffic goes over the public internet, and AWS handles the encryption.
VPC Peering allows private, secure communication between two VPCs without using public IPs or VPN.
Think of it like creating a "private bridge" between two isolated cities (VPCs).
Key Features
Private connectivity: Traffic stays within AWS’s network.
No Single Point of Failure: Unlike VPNs, no hardware to manage.
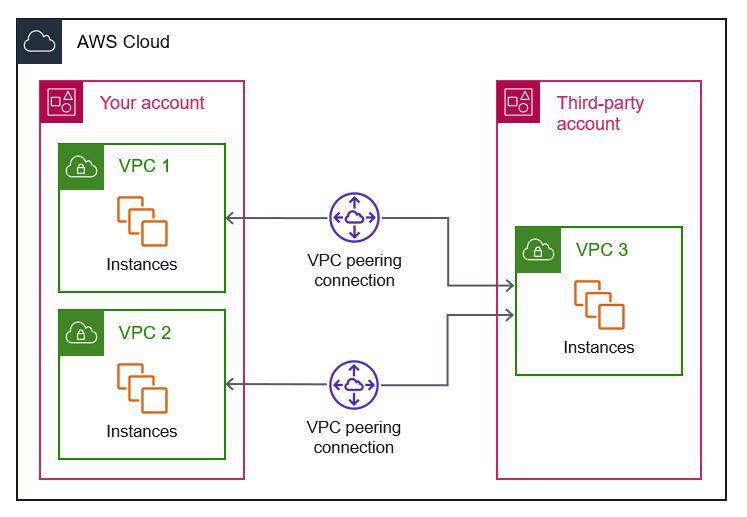
Cross-Account/Region Support: Connect VPCs across accounts or regions.
Step-by-Step: Solving CloudFizz’s Problem with VPC Peering
Step 1: Understand the Pre-requisites
Both VPCs are in the same AWS region (for simplicity, but cross-region is also possible!).
You have CIDR blocks that don’t overlap (e.g., VPC-A:
172.31.0.0/16, VPC-B:10.0.0.0/16).IAM permissions to create and accept peering connections.
Step 2: Create the Peering Connection
Go to AWS VPC Console → Peering Connections → Create Peering Connection.
Name it
Prod-To-Test-Peering.Select Production VPC as the requester and Testing VPC as the acceptor.
Step 3: Accept VPC Peering Connection
Go to VPC Dashboard → Peering Connections.
Find the
Prod-To-Test-Peeringpeering request.Click Actions → Accept Request.
🎉 Now, VPC Peering is active!
Step 2: Update Route Tables
Why? Peering alone isn’t enough. You need to define traffic rules.
Production VPC Route Table:
Add a route for10.0.0.0/16(Testing VPC) pointing to the peering connection.Testing VPC Route Table:
Add a route for172.31.0.0/16(Production VPC) pointing to the peering connection.
Step 3: Allow Access in Security Groups
Ensure the PostgreSQL database’s security group in Production VPC allows inbound traffic from the Testing VPC’s CIDR (10.0.0.0/16) on port 5432.
Step 4: Test Connectivity
From a Testing VPC EC2 instance, run:
psql -h <production-db-private-ip> -U db_user
If connected, you’re all set!
🚩 Common Real-Time Challenges & Fixes
Overlapping CIDR Blocks:
Problem: Both VPCs use
10.0.0.0/16.Fix: Recreate one VPC with a non-overlapping range (e.g.,
192.168.0.0/16&172.31.0.0/16).
Forgotten Route Table Updates:
Symptom: “Why can’t I ping the other VPC?!”
Fix: Double-check route tables for both VPCs.
Security Group Misconfigurations:
Symptom: Connection timeout.
Fix: Verify SG rules for the target resource (e.g., PostgreSQL).
🔑 Key Takeaways
VPC Peering = Private, secure communication between two VPCs.
Needs:
Non-overlapping CIDRs.
Peering Connection created and accepted.
Route tables updated for both sides.
Security Groups allowing traffic.
No public IPs, NAT, or VPN needed.
Why VPC Peering Over VPN or Transit Gateway?
Cost: No hourly VPN fees. Only data transfer costs ($0.01/GB).
Simplicity: No VPN hardware or complex BGP setups.
Speed: Low-latency AWS backbone.
🌐 Real-World Use Cases
Multi-Tier Applications: Connect frontend (public subnet) to backend (private DB subnet).
Shared Services: Centralize logging/audit tools in a “shared services VPC”.
Cross-Account Analytics: Let your data team query production data without direct access.
Connect Different Environments: Testing in Dev environment, securely calling Prod APIs.
Isolated Microservices: Microservice A in VPC-1 talks to Microservice B in VPC-2.
🔔 Conclusion
VPC Peering is your go-to for secure, simple, and scalable AWS network connectivity. For CloudFizz, it meant faster testing cycles without compromising security.
If you’ve ever struggled with VPC isolation and wanted a seamless way to connect workloads, VPC Peering is your go-to solution.
VPC Peering is one of the easiest and cost-effective ways to securely connect two VPCs for private communication — without exposing resources to the public internet.
Need help? Drop a comment below or ping me on LinkedIn. Happy peering! 🚀
Further Reading:
Subscribe to my newsletter
Read articles from Soumo Sarkar directly inside your inbox. Subscribe to the newsletter, and don't miss out.
Written by

Soumo Sarkar
Soumo Sarkar
Aspiring DevOps Engineer